Title
Create new category
Edit page index title
Edit category
Edit link
Is MetaDefender Core able to extract, detect and block malicious embedded macros?
In short, yes! MetaDefender Core can extract and block files if malicious macros are embedded.
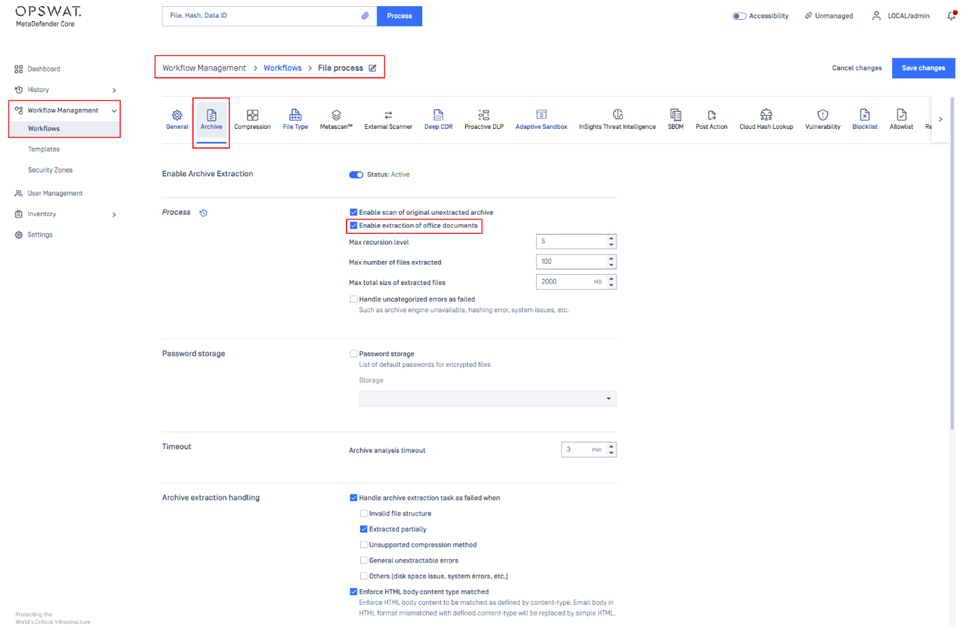
Macro objects are typically stored in Office Documents files such as xlsm, docm, pptm and so on, kindly make sure that the following option is enabled under your workflow, so that Core can extract Office Documents contents:
Workflow Management > Workflows > [any workflow] > Archive Tab > Enable extraction of office documents
Using the MetaScan Engines, it can detect the infected files and directly block them. For a more proactive approach, the DeepCDR Engine (What is CDR?) is able to deliver a clean version of the file by sanitizing/removing embedded data according to the configuration in place as per each file type, reconstructing the base file.
If Further Assistance is required, please proceed to log a support case or chatting with our support engineer.

