Why is MetaDefender Core SSO failing when HTTPS is handled by an external NGINX proxy?
This article applies to MetaDefender Core 5 releases deployed on Windows, Linux.
Issue:
When SSO is enabled in MetaDefender Core, but HTTPS is terminated by an external NGINX proxy (and not directly by the Core application), SSO authentication may fail if NGINX does not forward the correct Host header.
By default, NGINX forwards the Host header without the server port. MetaDefender Core validates the Host and port to match its HTTPS configuration. Missing the port in the Host header causes SSO callbacks to be rejected due to mismatched redirect URLs.
Resolution:
To ensure MetaDefender Core receives the correct Host header including port, update your NGINX configuration:
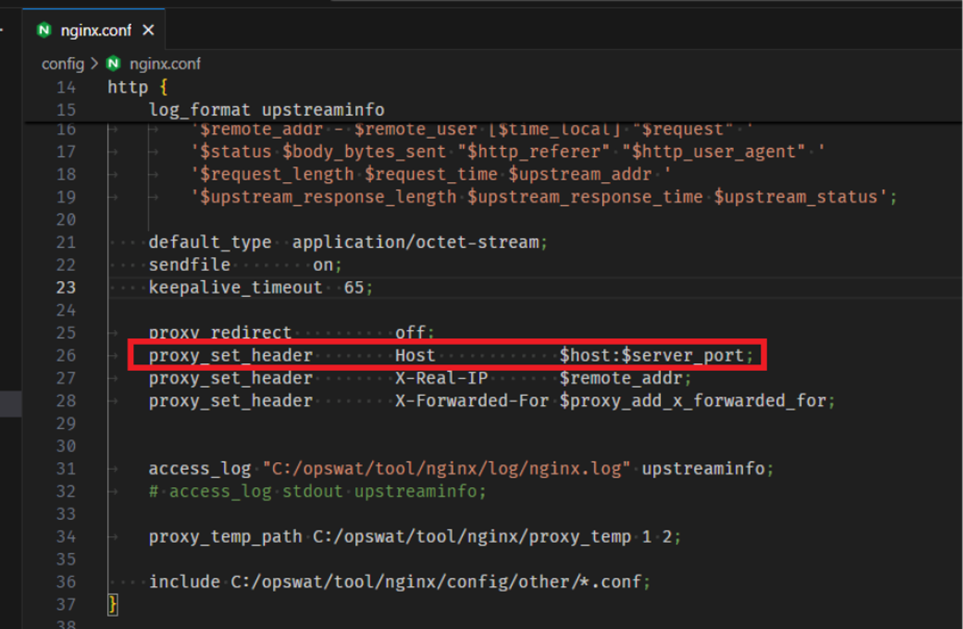
NGINX Configuration Update
In your nginx.conf (or in any included server block configuration file), locate the proxy_set_header directives and add or update the following line:
proxy_set_ header Host $host:$server_port; This ensures the Host header includes both the hostname and the port number, matching Core’s HTTPS endpoint.
Validation
Restart NGINX service after updating the configuration.
Clear browser cache or restart browser to ensure new headers are used.
Attempt SSO login to MetaDefender Core. Successful authentication should redirect to the correct HTTPS URL.
Steps to Reproduce:
Attempt SSO login to MetaDefender Core when HTTPS is handled by an external NGINX proxy without forwarding the correct Host header.
If Further Assistance is required, please proceed to log a support case or chatting with our support engineer.