Sessions refer to the TCP stream between the source IP address and destination IP address and between the same source port and destination port. The default Sessions page in the Analysis menu displays attributes associated with the latest TCP sessions recorded by MetaDefender NDR.
Session Details
The right pane on the user interface displays sessions with their basic details in a tabular form. Basic details of these sessions include:
- Time – Session time when the PCAPs were captured off the network sessions.
- Source – Source IP address from where the threat originated.
- Destination – Destination IP address.
- Protocol – HTTP or SMTP protocol involved in the file transmission.
- VLAN – Virtual local area network ID of the collector.
- Collector – Collector hostname.
- Actions – A link to click and view the detailed analysis report of the session.
Note: For information on using available tips and options on the Sessions page, refer the Other Options in the Analysis Pages section.
Quick Search Rules
Quick search in the Sessions page appears on the left pane of the user interface and supports simple search text to be typed, which includes the IP addresses, IP address subnets, and hashes to search the desired sessions. Rules to be followed while using these items include:
- Regular expression for IP address pattern must be at least two ‘dot-separated’ IP address octets. For example: 8.8.
- Regular expression for IP subnets must be full IPv4 subnets in CIDR notation. For example: 192.168.0.0/24.
- Regular expression for hashes must contain 6 and more subsequent 0-9a-f characters or strings.
On clicking Search, if your search request did not match any of the above patterns, the search text will be transformed into a new pattern where all space characters are replaced with an underscore, and all wildcards * with [a-z0-9_]*. InQuest API then matches the signature names in its database against the resulting new text pattern, and searches and returns session results related to the matched signature.
If your search request further didn’t match any patterns, the search is applied to any chunks having at least first three characters of a word. Also, the search engine makes characters (. / : & ? = % - @) as both word separators and parts of words. This means whenever you have signature containing 'qwer:tyui', you can match it with the text 'qwer', 'qwer:ty' as well as 'tyu'.
Quick Search Usage - An Example
Consider an example where you want to search and display sessions related to the IP subnet 169.222.218.238 since March 03, 2018 till date.
- Click Analysis.
- In the default Sessions page, in the Quick Search textbox, type the complete IP subnet 169.222.218.238.
- Select 50 from the options below meaning your quick search must return at least 50 session results on the right pane.
- In Time Interval, click From/To and using the calendar, select the From time to be 2018-03-01 00:00 and retain the To time as the default Now.
- Click Search. Sessions matching the above search text for the specified time interval are displayed on the right pane with their basic details.
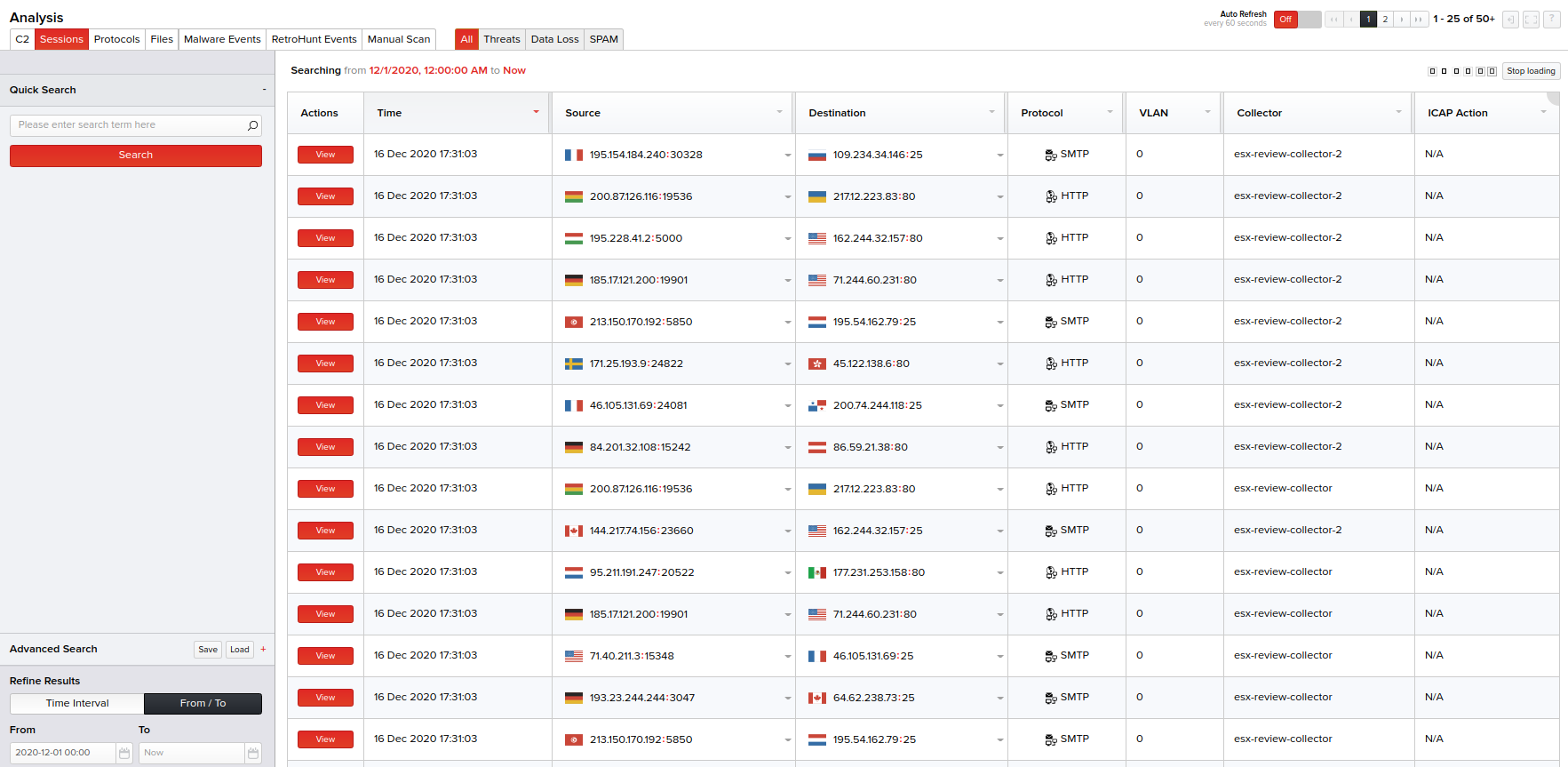
Advanced Search
Columns available in the Advanced Search menu for the Sessions page are:
- Collector
- Creator ID
- Destination ASN Number
- Destination ASN Reputation
- Destination IP
- Destination IP Cloud Threat Score
- Destination IP Country
- Destination Port
- File: Event ID
- File: MD5
- File: SHA1
- File: SHA256
- File: SHA512
- File: Signature Category
- Fire: Signature Name
- File: Ssdeep
- Hash List
- Header: Event ID
- Header: Signature Category
- Header: Signature Name
- Is In Blacklist
- Protocol
- Protocol Headers (HTTP)
- Protocol Headers (SMTP)
- Session ID
- Source ASN Description
- Source ASN Number
- Source ASN Reputation
- Source IP
- Source IP Cloud Threat Score
- Source IP Country
- Source Port
- VLAN ID
- Workflow
Note__: Advanced searches for the columns "Protocol Headers (HTTP)" or "Protocol Headers (SMTP)" are case sensitive.
Select the column(s) and specify their respective criteria. You can also specify the session time from the Time Interval drop-down menu or select a date range from the built-in calendars by clicking the From/To option. Click Search to view the basic session details matching your specified columns and criteria on the right pane in a tabular form.
Advanced Search Usage - An Example
Consider an example where you want to do an advanced search to display sessions that has the destination IP address in the "United States of America" starting from March 01, 2018 till date.
- Click Analysis.
- In the default Sessions page, click Advanced Search.
- From the Add Column drop-down menu, select Destination IP Country. This column gets added below with an option to select its criteria.
- Specify its criteria below by selecting Equal and United States.
- In Time Interval, click From/To and using the calendar, select the From time to be 2018-03-01 00:00 and retain the To time as the default Now as highlighted in the following screen.
- Click Search. Sessions matching the above search columns and criteria for the specified time interval are displayed on the right pane with their basic details.
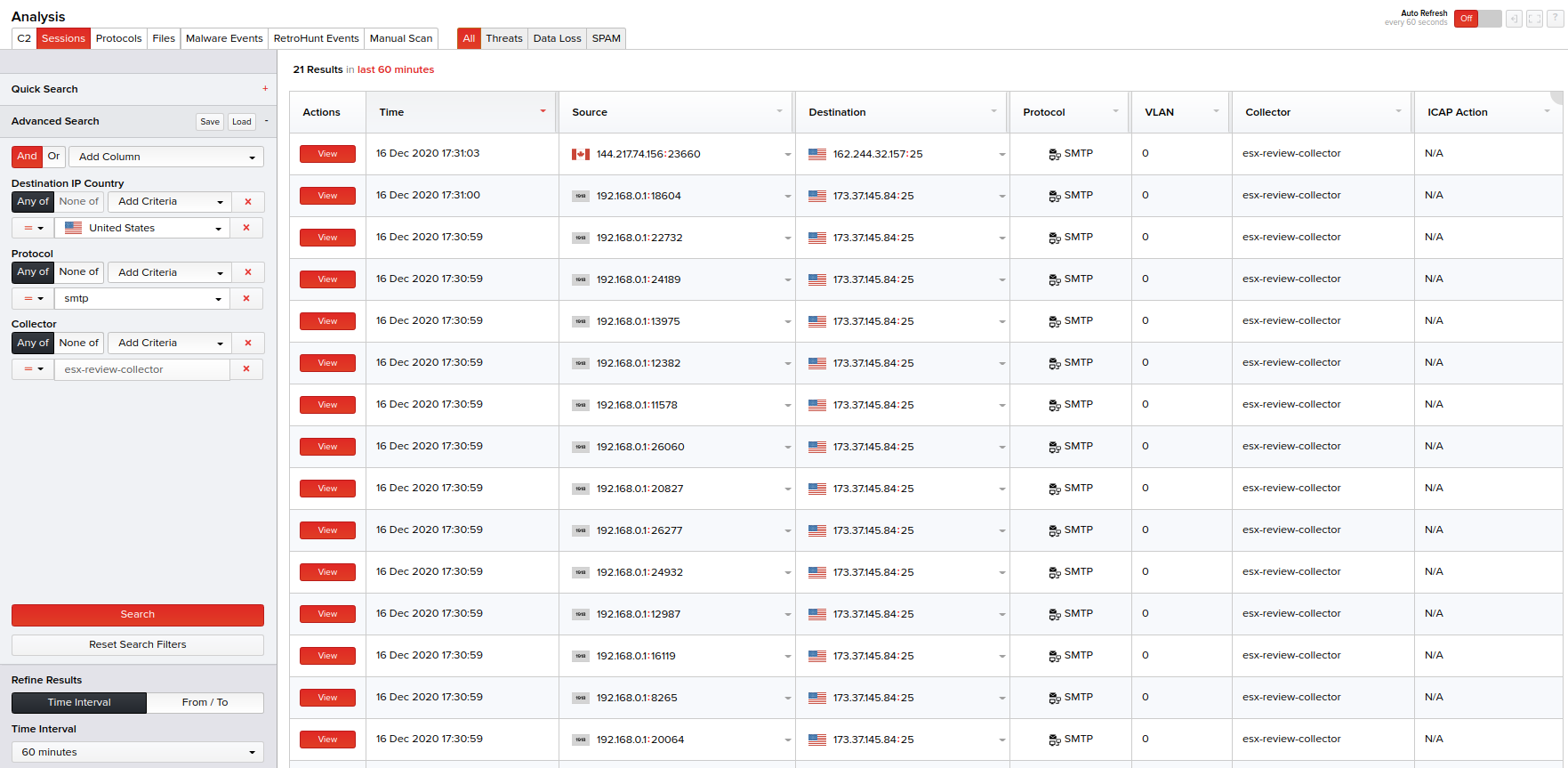
Basic details of each session displayed (for both the Quick Search or Advanced Search methods) include the session time when the PCAPs were captured off the sessions, source and destination IP addresses, protocol, VLAN, collector host name and a link to view the session details.
Note__: For viewing the detailed analysis report of a session on a new screen, click the View link corresponding to that session in the Actions column.
Viewing Detailed Session Reports
Details of a session can be viewed by clicking View in the Actions column corresponding to a session for a selected Analysis page.
Session Details
The Session Details page gives an overview of the session details that include the threat score for the session, TCP session ID, instance when the PCAPs were captured off the sessions, source and destination IP address of the session, protocol involved, VLAN id, number of files transferred, file name, number of unique threat detection events out of the total events, details on the protocol header and the transferred files.
You have an option to view the file content and download them as raw or encrypted files as shown in the following screen.
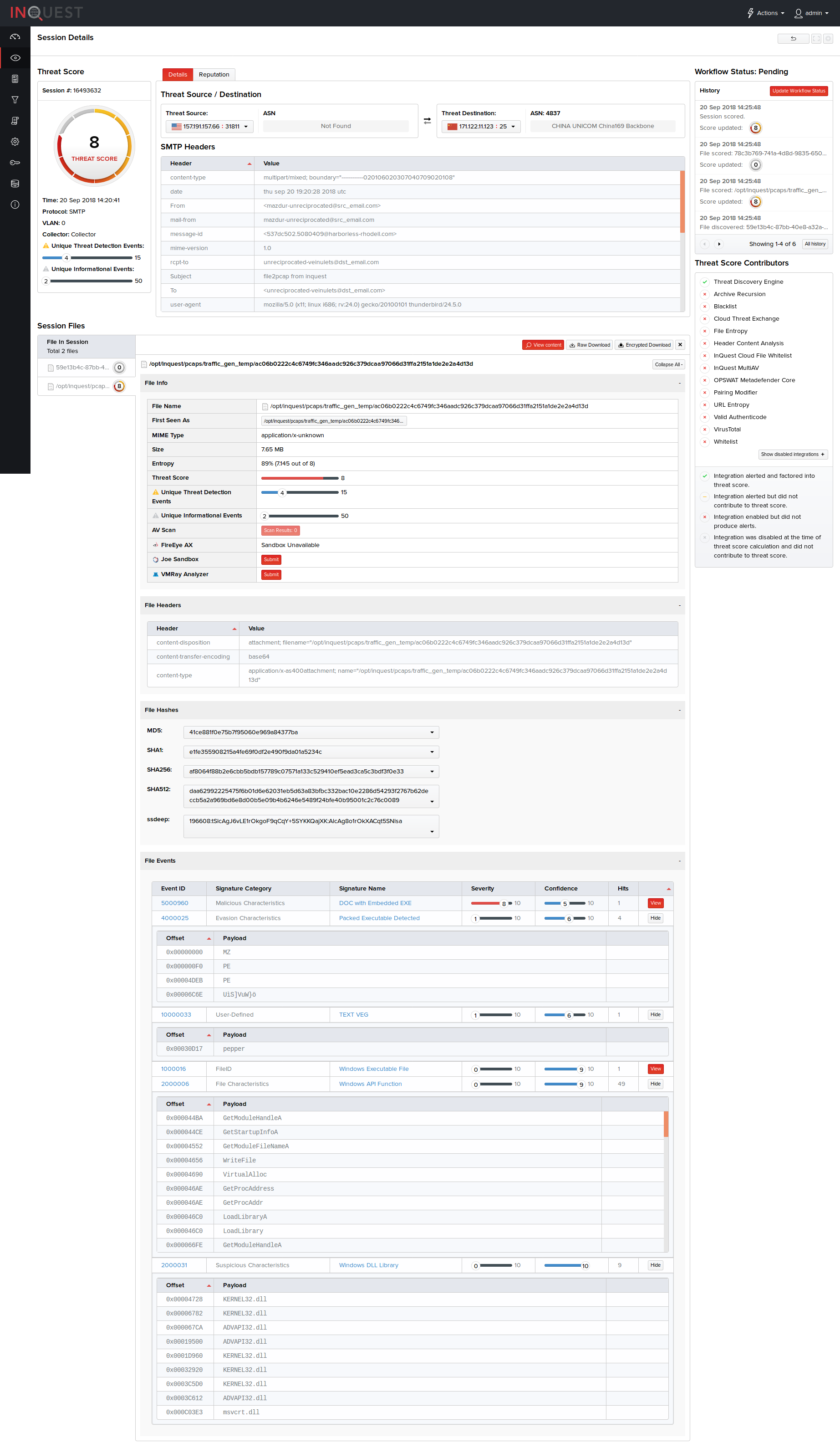
The contents of each file within the session file tree can be viewed by clicking the "View Content" button.
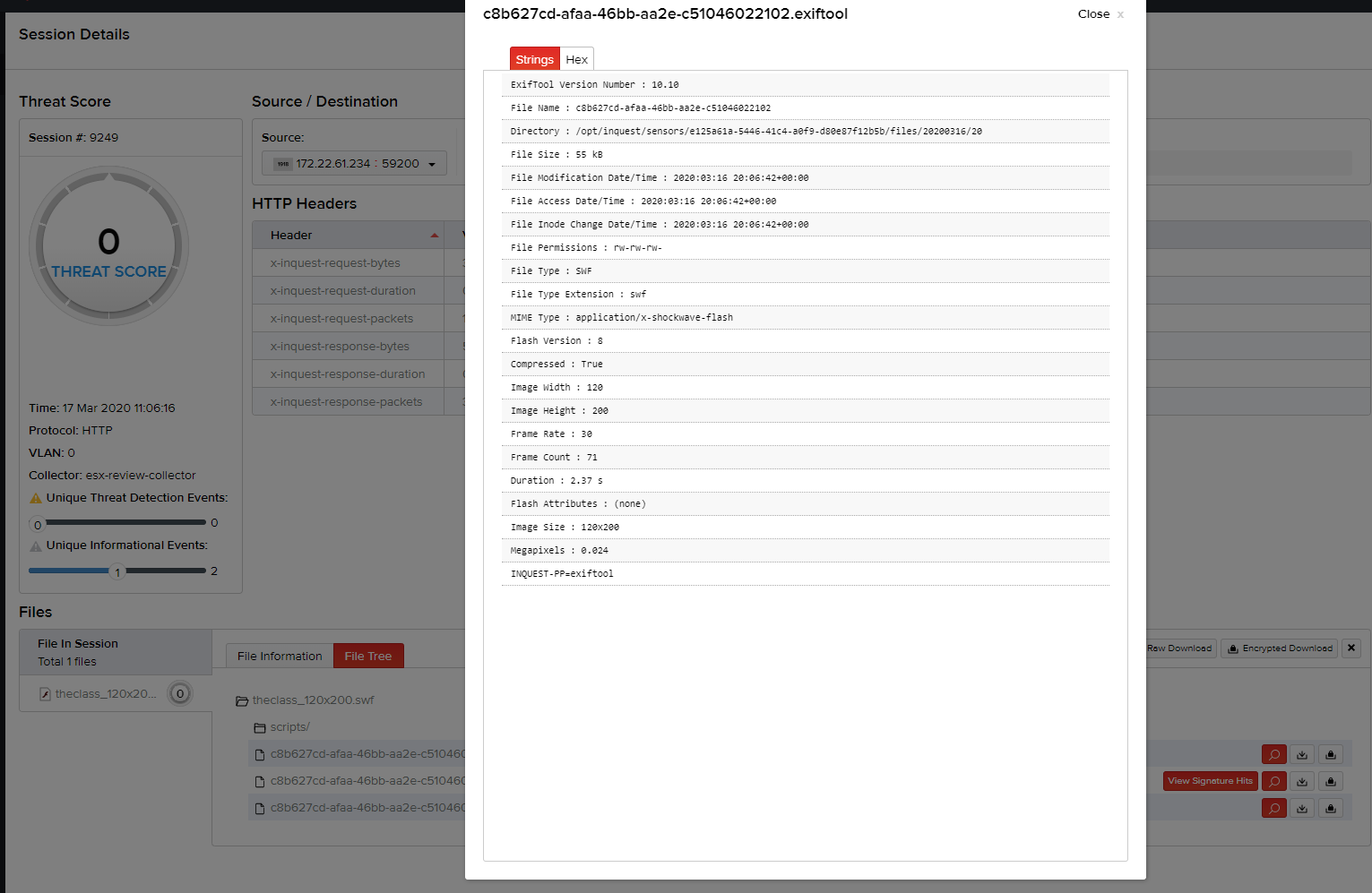
Image files (PNG, JPG, GIF) within the session file tree can also be viewed within the UI by clicking the "View Image" Button.
Scroll down to view further information pertaining to the protocol header and transferred files displayed in different segments; one below the other.
- In the File Info segment, you can view the file name, MIME type, file size, and entropy in terms of percentage. You can view the number of AV scan results with an option to click and view its further details, first seen name of the file that can be clicked to view further details of the file, and the option to view the file(s) content and download them as raw or encrypted file(s). Encrypted file downloads are password protected using the password inquest.
- Note*: Entropy is the randomness of the file. Files with structured data will have lower entropy percentage. Files with compressed or encrypted data will have a higher entropy percentage.
- In the File Headers segment, you can view the protocol header host, URI strings, method in the programming code that triggered the file, HTTP response status codes, file content type and the reference URL of the header.
- In the File Hashes segment, you can also view the MD5, SHA1, SHA256, SHA512 checksums and the ssdeep fuzzy hashes that detected the file(s).
- The File Events segment displays information on signatures that have fired on the file, such as signature category, severity, confidence, and the number of signature hits.
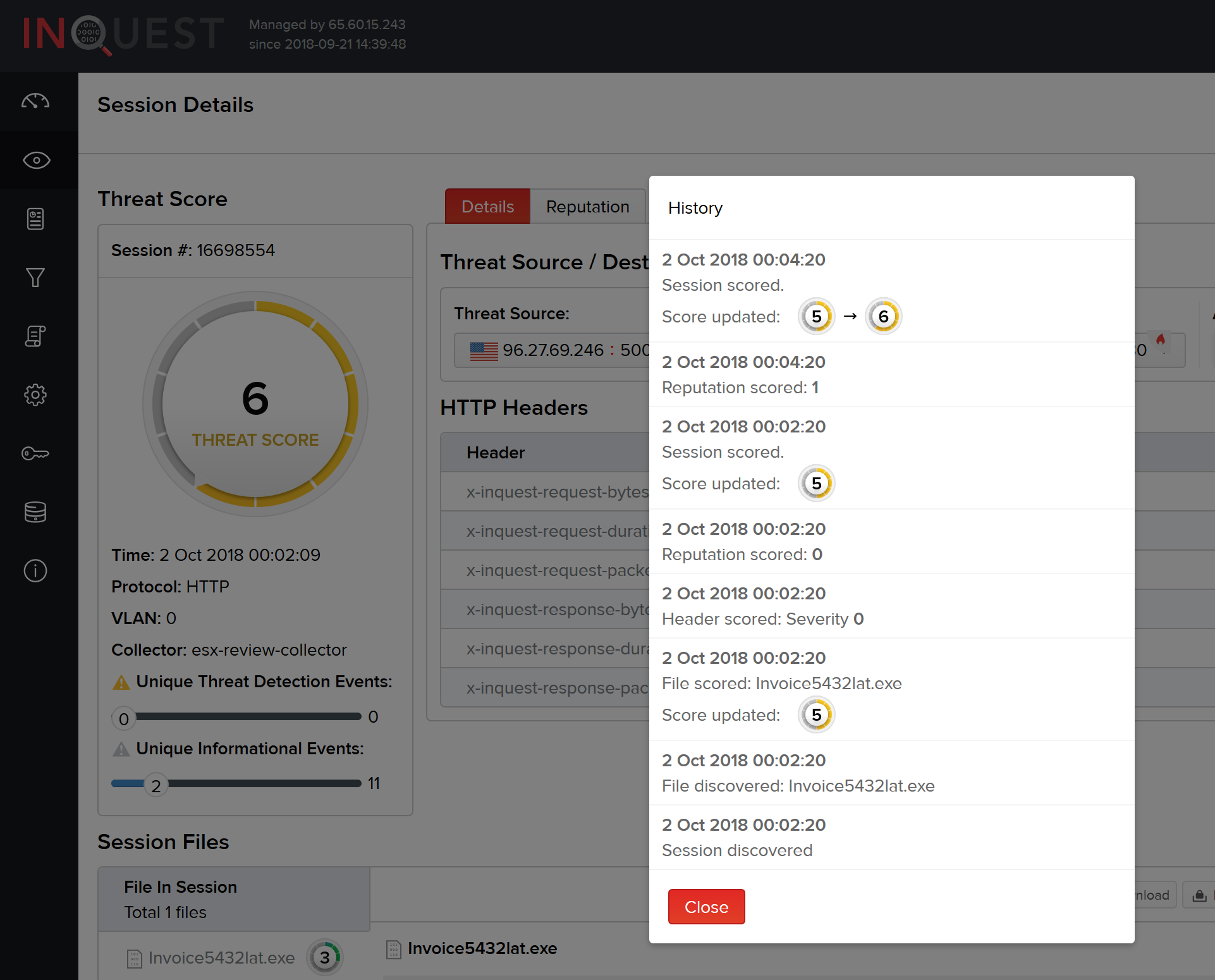
History
The history pane displays a timeline of session threat scores as well as workflow changes for this session. The preview shows the most recent updates on top.
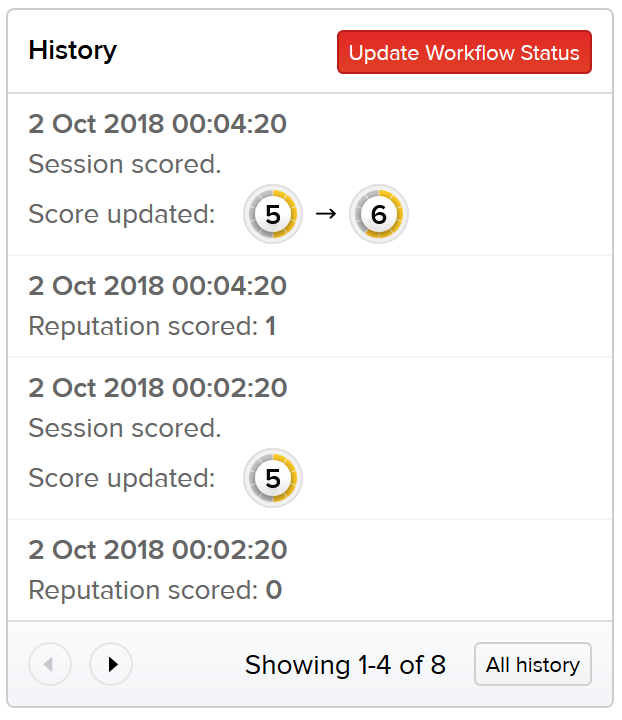
The full history can be viewed by clicking the All history button.
This history will include information like when the session or file was discovered, changes to the threat score of a file, header, reputation, or session, and any changes to the workflow. These details tell the history of the session and are listed in reverse order.
Threat Score Contributors
Apart from the common information pertaining to the protocol header and transferred files, the Threat Score Contributors column on this screen provides information on the subsystems contributing to the overall threat score of the content and alert generation. On the right pane, you can change the workflow status of the session as required by clicking Update Workflow Status, Note__: You can change the workflow status of the sessions provided you have been granted the permission for it. If not, this option is disabled.

