The Malware Events page displays files that were triggered either by InQuest MultiAV, VirusTotal, or OPSWAT MetaDefender Core.
Malware Events Details
Click Analysis > Malware Events. The right pane on the user interface displays sessions with basic file, virus, and supplier details in a tabular form. These basic details include the instance of the files triggered, source IP address from where the file originated, destination IP address, file hash, filename, virus name, supplier that detected the virus, and a link to click and view the detailed report of the malware events session.
Note: For information on using available tips and options on the Sessions page, refer the Other Options in the Analysis Pages section.
Note: Quick search does not search for vendor name or virus name, only file name. If you wish to search for vendor name or virus name, use the advanced search.
Advanced Search
Columns available in the Advanced Search menu for the Malware Events page are:
- Destination IP
- Destination Port
- Filename
- Hash List
- MD5
- SHA1
- SHA256
- SHA512
- Signature Name
- Source IP
- Source Port
- Vendor Name
- Virus Name
Select the column(s) and specify their criteria. You can also specify the session time from the Time Interval drop-down menu or select a date range from the built-in calendars by clicking the From/To option. Click Search to view the basic session details matching your specified columns and criteria on the right pane in a tabular form.
Advanced Search Usage- An Example
Consider an example where you want to do an advanced search to display events that included files containing the term "php" in the filename and source IP address contains "222" since June 20, 2016 to June 22, 2016.
- Click Analysis > Malware Events > Advanced Search.
- From the Add Column drop-down menu, select Filename. This column gets added below with an option to select its criteria.
- Specify its criteria below by selecting Contains and type php in its corresponding textbox.
- From the Add Column drop-down menu, select Source IP as the next column and select its criteria as Contains and type 222 in its corresponding textbox.
- In Time Interval, click From/To and using the calendar, select the From time to be 2016-06-20 00:00 and the To time as 2016-06-22 00:00 as highlighted in the following screen.
- Click Search. Malware event sessions matching the above search columns and criteria for the specified time interval are displayed on the right pane with their basic details.
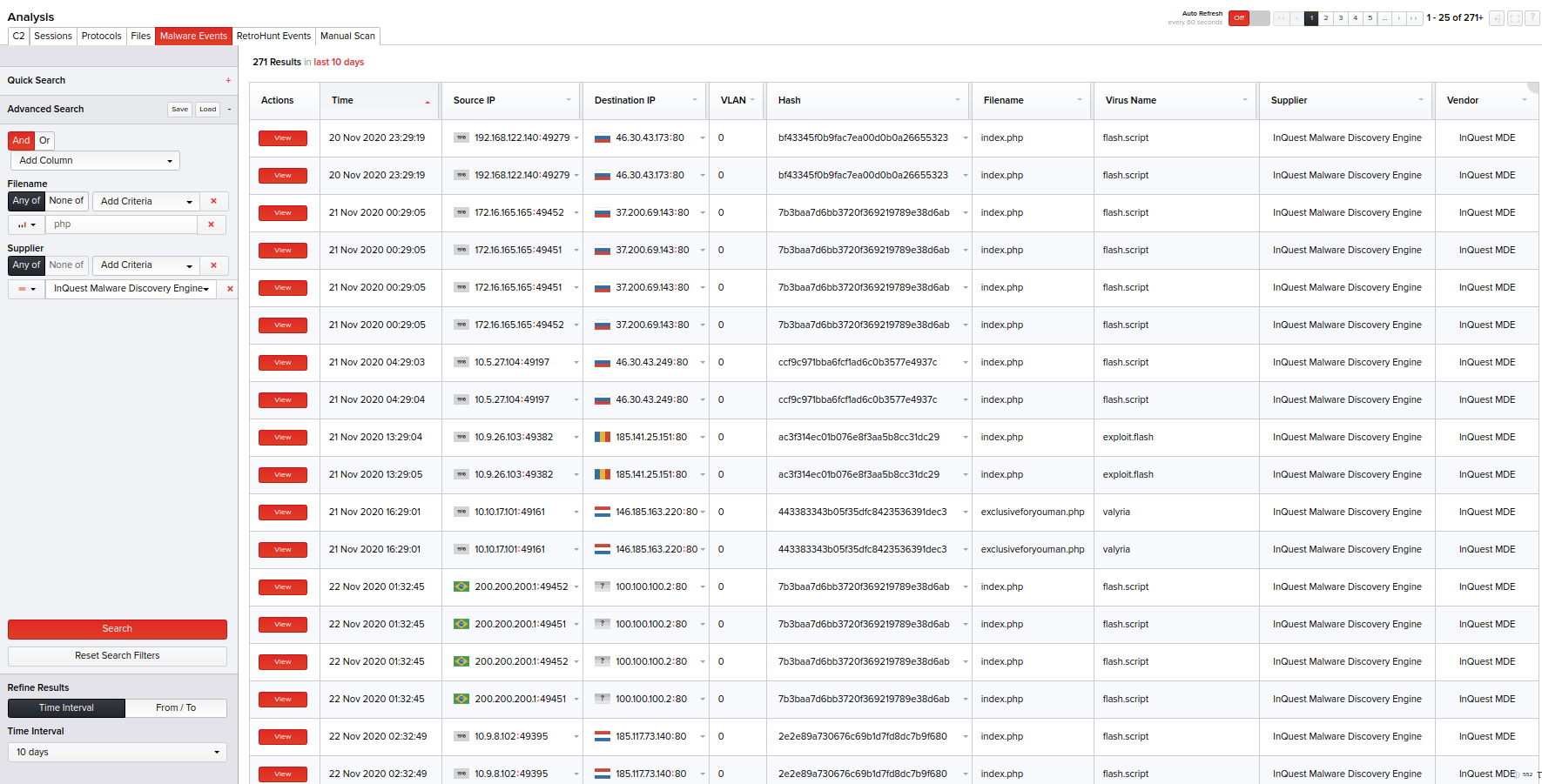
To view further details of the infected file, click View in the Actions column corresponding to that file. For more information, refer the Viewing Further Details of the File section.

