Apart from supporting the local account authentication with user name and password, MetaDefender NDR enables remote authentication through multiple external integrations for users with Active Directory (including AD+SSL), LDAP (including LDAPS), RADIUS or TACACS+. It uses the remote authentication server name, IP address, and port that lets users authenticate their account with a username, password, and authentication mapping.
- Click Authentication > Authentication Configuration > New Mapping for the default AD tab.
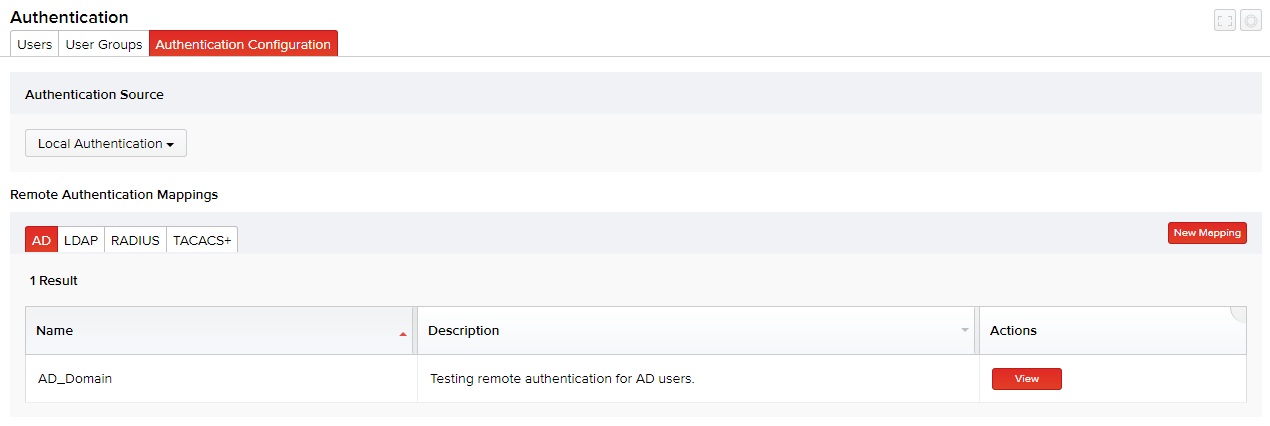
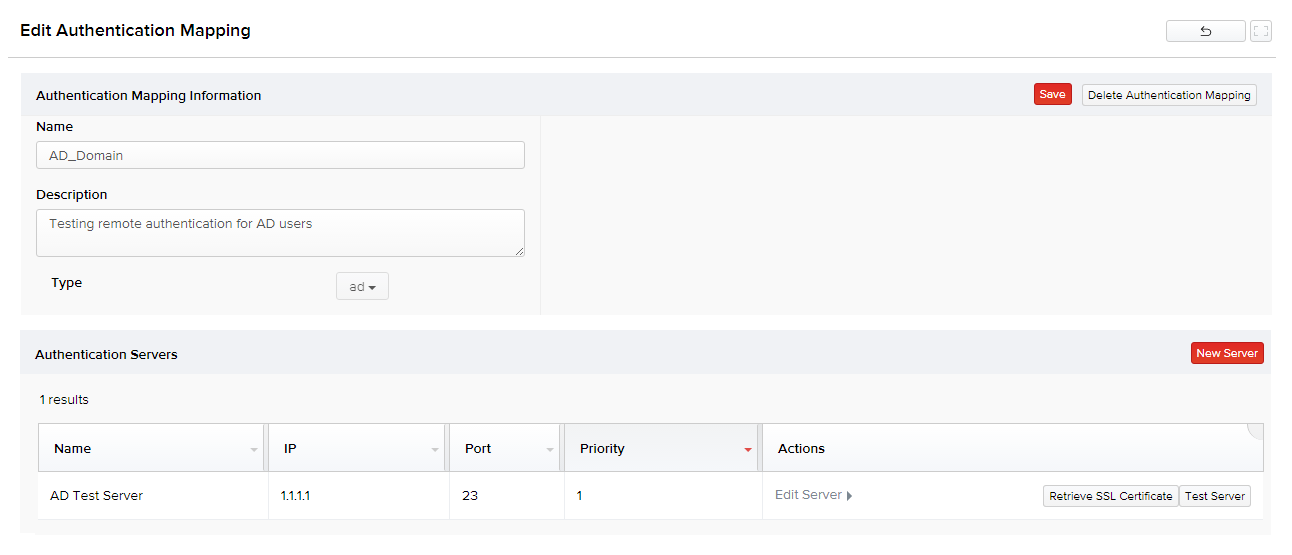
- Enter the name and description for the new authentication mapping, and click Save. Once the mapping is added, you get an option to add server(s) to your mapping.
- Specify the server configuration by clicking New Server. The Add Server page appears
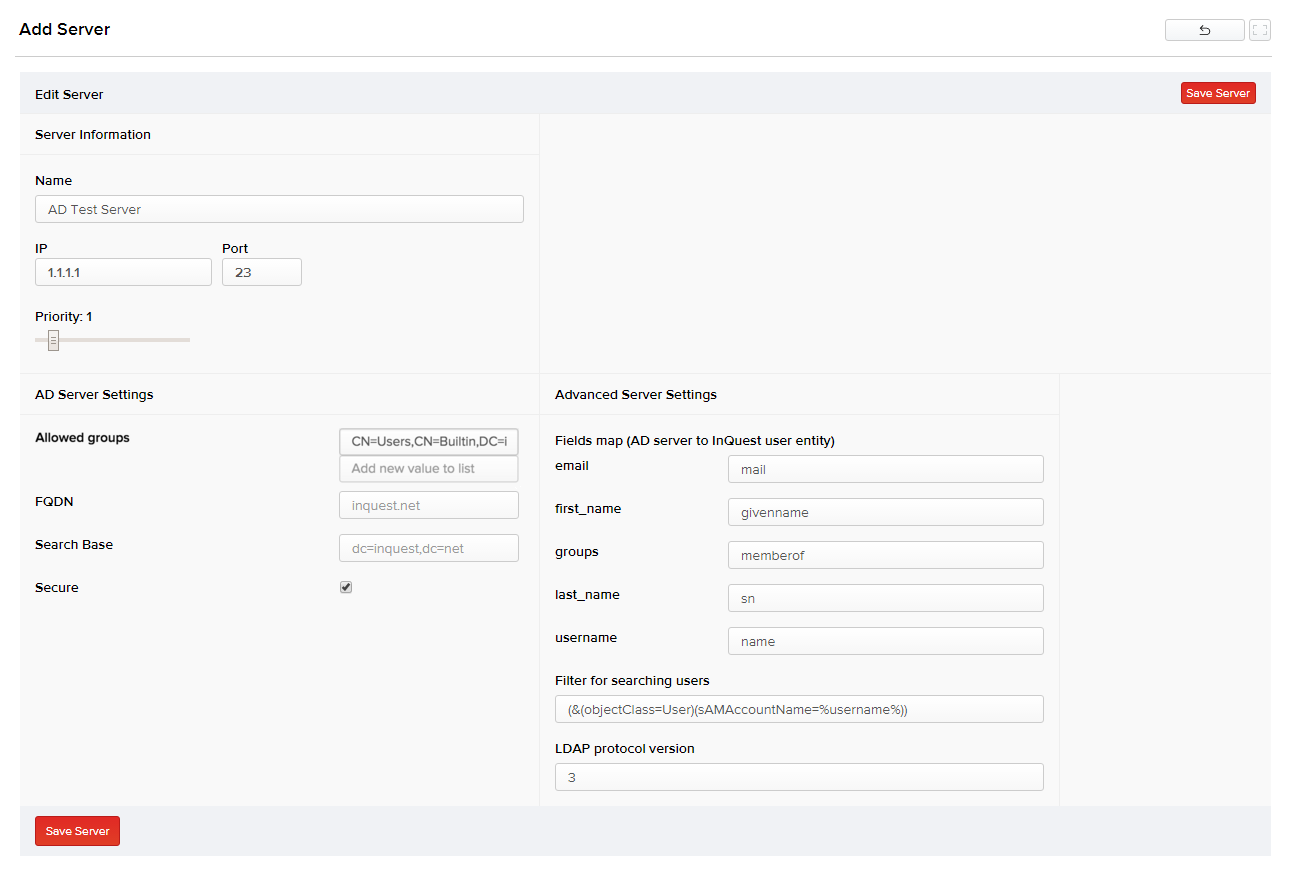
- Specify the server name, IP address, port, priority, server settings, advanced server settings (default advanced settings are mostly retained), and then click Save Server. The new server is added to the authentication server list below.
Allowed groups must be entered one by one in corresponding fields and must not be a comma-separated list in one field. Once the groups are added, the remote server group would be mapped to the local MetaDefender NDR Manager group, thus mapping all permissions of the local MetaDefender NDR group to the remote server groups too.
Users can add one or more servers to an authentication mapping. In such cases, they can act as fallbacks to one another without a sequence. Assigning priority to each server controls the sequence in which they are used. For instance, if server with priority 1 is down, server assigned with priority 2 is used and so on. Select the Secure checkbox if you want to authenticate to the server through a secured connection.

