Title
Create new category
Edit page index title
Edit category
Edit link
FortiGate
This documentation is based on FortiGate 5.4.3 documentation using web-based manager and CLI. For different version of FortiGate or missing information, refer to FortiGate user guides.

Configuration via Web-Based Manager
Enabling ICAP feature
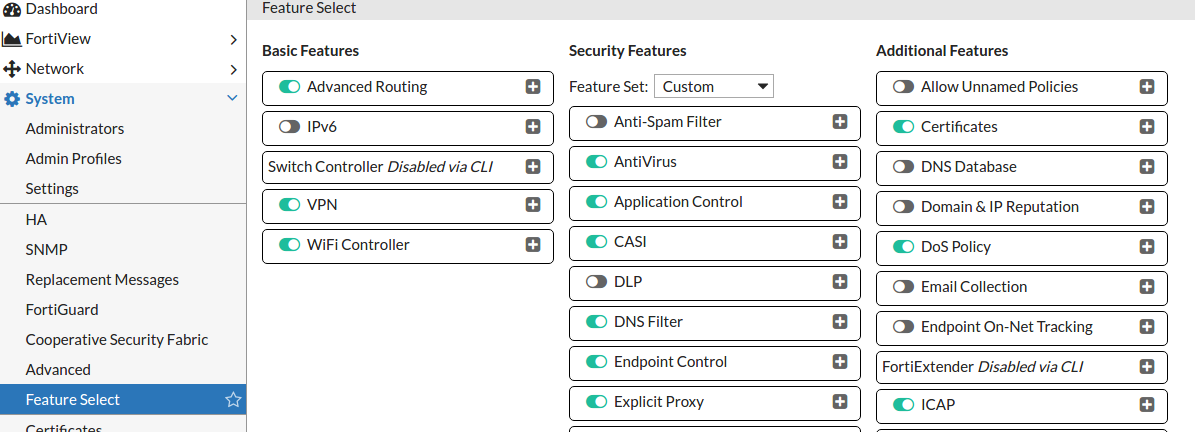
ICAP does not appear by default in the web-based manager, it has to be enabled by going to System → Feature Select and enabling ICAP. You may need to refresh the page in order to see the changes.
Adding ICAP server and profile
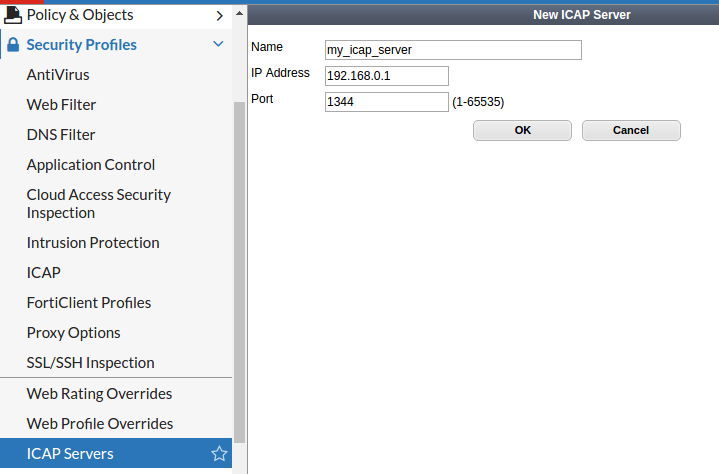
- Add ICAP server
- Select Security Profiles → ICAP Servers.
- Create new or edit an existing entry.
- The IP address and port should be the ones used by MetaDefender ICAP Server
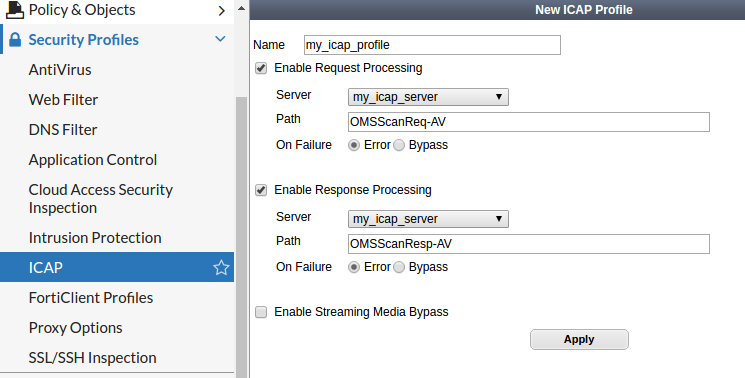
- Add ICAP profile
- Select Security Profiles → ICAP.
- Create new or edit an existing entry.
- Select the 'Enable Request Processing' check-box, select your server's name from the drop-down list and in the 'Path' field, type in 'OMSScanReq-AV'.
- Select the 'Enable Response Processing' check-box, select your server's name from the drop-down list and in the 'Path' field, type in 'OMSScanResp-AV'.
- Apply the changes.
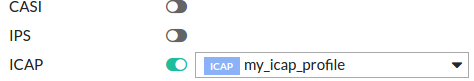
- Apply the ICAP profile in your policy/policies
- Select Policy&Objects → IPv4 Policy | Explicit Proxy Policy.
- Create new or edit an existing policy
- In the section 'Security Profiles', switch on ICAP and select the previously created profile.
Configuration via CLI
- Add ICAP server
Add ICAP server via CLI config icap server edit <icap_server_name> set ip-version {4 | 6} [default: 4] set ip-address <server_ipv4> set ip6-address <server_ipv6> set max-connections <int> [default: 100] set port <port_int> [default: 1344] endThe example shown above in the web-based manager would look like this in the CLI:
Add concrate ICAP server via CLI config icap server edit my_icap_server set ip-address 172.16.201.36 end- Add ICAP profile
Add ICAP profile via CLI config icap profile edit <icap_profile_name> set replacemsg-group <grp_name> set request {enable | disable} [The following commands are enabled if request is set to 'enable'] set request-failure {error | bypass} set request-path <path> set request-server <icap_server> set response {enable | disable} [The following commands are enabled if response is set to 'enable'] set response-failure {error | bypass} set response-path <path> set response-server <icap_server> set streaming-content-bypass {enable | disable} endThe example shown above in the web-based manager would look like this in the CLI:
Add concrate ICAP profile via CLI config icap profile edit my_icap_profile set request enable set request-failure error set request-path OMSScanReq-AV set request-server my_icap_server set response enable set response-failure error set response-path OMSScanResp-AV set response-server my_icap_server set streaming-content-bypass disable end- Apply the ICAP profile policy (policy can be replaced by explicit-proxy-policy when setting ICAP for an Explicit Proxy Policy)
Apply ICAP profile via CLI config firewall policy [or policy6 if IPv6 is used] edit <index_int> set icap-profile <icap_profile_name> endThe example shown above in the web-based manager would look like this in the CLI:
Apply concrate ICAP profile via CLI config firewall policy edit 1 set icap-profile my_icap_profile endIf you want to disable the ICAP profile for a given policy you should write
Disable ICAP profile via CLI config firewall policy [or policy6 if IPv6 is used] edit <index_int> set icap-profile "" endScanning HTTPS content
To be able to inspect and scan SSL/SSH traffic you have to enable it in Fortigate. After enabling this option you should download the certificate used by Fortigate and install/import it to the browsers which communicate with Fortigate. Otherwise you might see SSL/security related notifications or errors, or even not working web pages.
The certificate can be downloaded under Security Profiles→ SSL/SSH Inspection
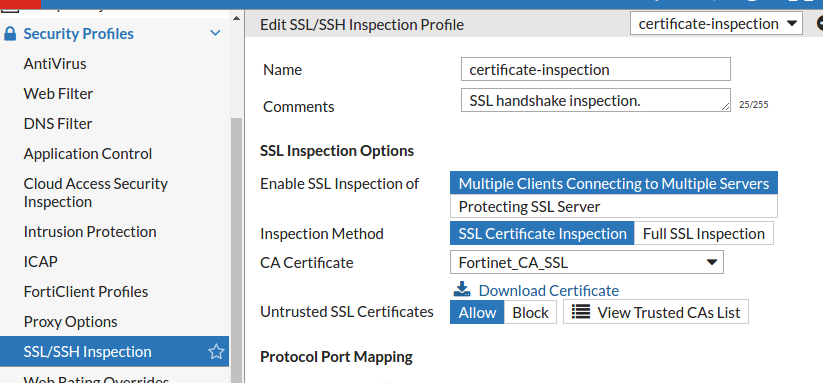
Enable SSL inception via GUI
- Navigate to Policy&Objects and select the policy you would like to enable SSL inception to (for example an Explicit Proxy Policy)
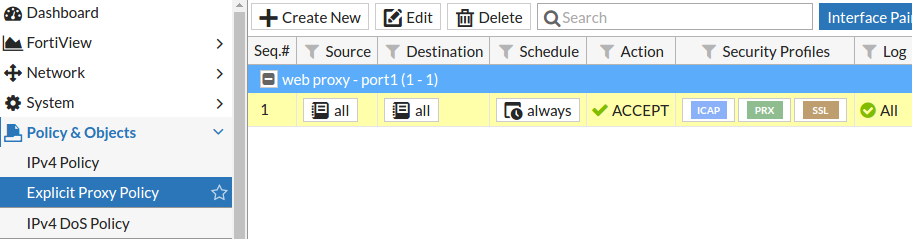
- In the Edit page of the selected policy locate the Security Profiles section
- Turn SSL/SSH Inspection on and set it to deep-inspection
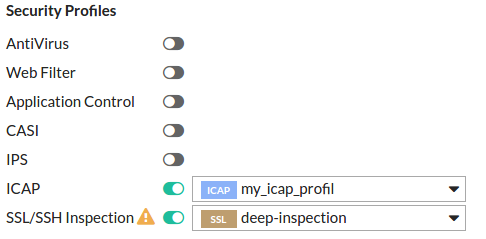
Enable SSL inspection via CLI
The steps shown above would like this via CLI:
Apply deep ssl inspection to an Explicit Proxy Policy config firewall explicit-proxy-policy edit 1 set ssl-ssh-profile deep-inspection end
