Title
Create new category
Edit page index title
Edit category
Edit link
F5 SSL Orchestrator
Sample Deployment Diagram
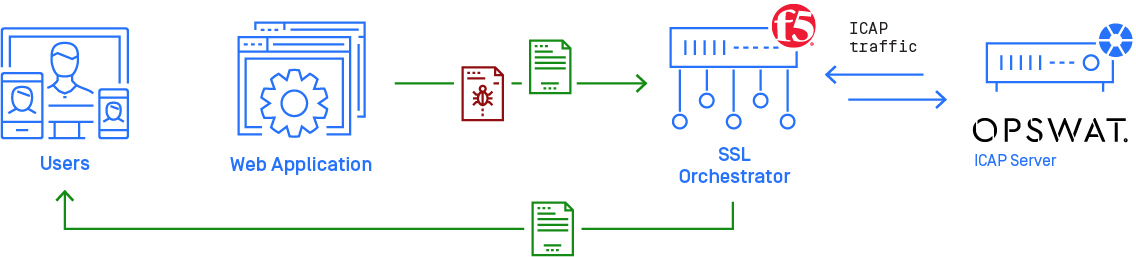
Using F5's SSL Orchestrator together with MetaDefender ICAP Server will help you scanning your non-SSL and decrypted SSL traffic flow for threats using all of the engines in MetaDefender Core. This guide describes the basic steps to getting MetaDefender ICAP Server working with your F5 SSL Orchestrator.
System Requirements
The following systems are required to set up MetaDefender ICAP Server with an F5 SSL Orchestrator
- F5 SSL Orchestrator
- MetaDefender ICAP Server
- MetaDefender Core
Configuring MetaDefender ICAP Server
For installation and configuration quick guidelines see: 1. Quick Start with MetaDefender ICAP Server.
For detailed instructions see 2. Installing or Upgrading MetaDefender ICAP Server and 3. Configuring MetaDefender ICAP Server.
Note on MetaDefender ICAP Server Licensing
MetaDefender ICAP Server must have a valid license to function correctly. For license configuration details see 2.4. MetaDefender ICAP Server Licensing.
Configuring F5 SSL Orchestrator
The following configuration steps should be done from the F5 SSL Orchestrator Management Console interface. The steps below describe the minimum configuration required for MetaDefender ICAP Server integration with F5 SSL Orchestrator and was created based on SSL Orchestrator v3.0.
Open a web browser and load the SSL Orchestrator Management Console. (Please refer to the SSL Orchestrator manual for details about how to open the BIG IP Management Console.)
This guide was written with a presumption that you have already completed the General Properties configuration in the SSL Orchestrator.
Configuring the ICAP service
- Navigate to SSL Orchestrator > **Configuration
- Select ICAP / SWG Services under the Services tab

- Click Add to add a new ICAP service
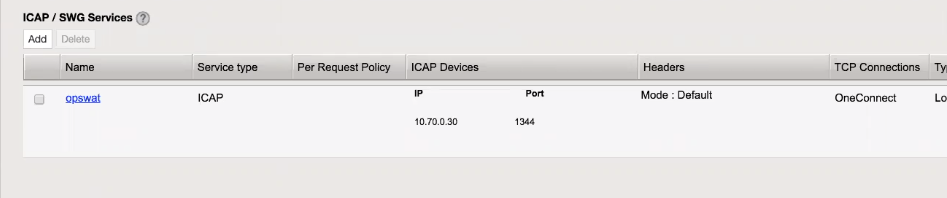
- In the Name field, type a name for your configuration
- Select ICAP as the Service type
- Add your MetaDefender ICAP Server's IP and port to the ICAP Devices
- Select the Headers mode. "Default" can be used.
- Select TCP Connections. OneConnect can be used if you enabled persistent connections in your MetaDefender ICAP Server (enabled by default) otherwise use Separate.
- Select "Load Balanced" as the Type. You can find more information about it here.
- You can use "reqmod" and "respmod" as the values for Request and Response fields
- Select your ICAP Policy if you have any
- Set 0 as the Preview Max. Length
- Select your preferred Server Failure Handling (Next Service Chain or Reset Connection)
- Select if you would like to send only HTTP/1.1 or both HTTP/1.0 and HTTP/1.1 requests to the ICAP service in Send HTTP/1.0 Requests to ICAP
- Set your Addition iRule if you have any
- Click Finished
- Click Save
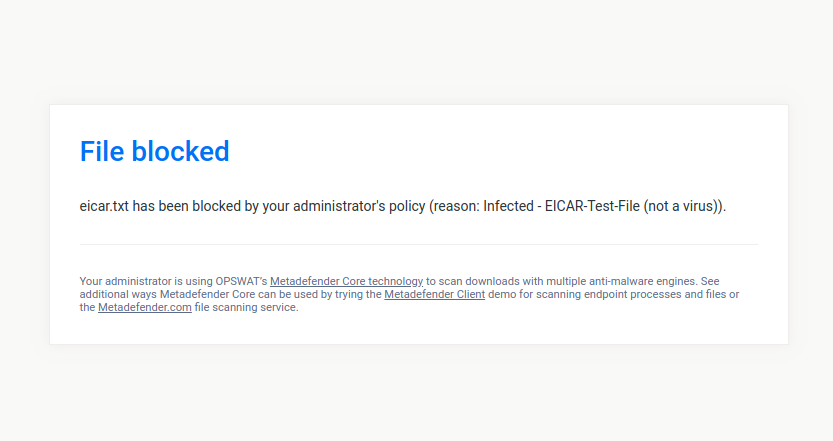
Testing the configuration
To check that you configuration is working as expected try to download an eicar testfile over HTTPS here. If everything was setup properly you should see a blocking page similar to this: