Title
Create new category
Edit page index title
Edit category
Edit link
A10 SSL Insight (SSLi)
Using A10’s Thunder SSLi together with MetaDefender ICAP Server will help you scan your HTTP and decrypt SSL/TLS traffic flows for threats using all of the engines in MetaDefender Core. This guide describes the basic steps to get MetaDefender ICAP Server working with your A10 Thunder SSLi.
Sample Deployment Diagram

System Requirements
The following systems are required to set up MetaDefender ICAP Server with an A10 Thunder SSLi
- A10 SSL Insight appliance (Thunder SSLi or Thunder CFW)
- MetaDefender ICAP Server
- MetaDefender Core
Configuring MetaDefender ICAP Server
For installation and configuration quick guidelines see: 1. Quick Start with MetaDefender ICAP Server.
For detailed instructions see: 2. Installing or Upgrading MetaDefender ICAP Server and: 3. Configuring MetaDefender ICAP Server.
Note on MetaDefender ICAP Server Licensing
MetaDefender ICAP Server must have a valid license to function correctly. For license configuration details see 2.4. MetaDefender ICAP Server Licensing.
Configuring A10 Thunder SSLi
The steps below describe the minimum configuration required for MetaDefender ICAP Server integration with A10 Thunder SSLi and was created based on ACOS 4.1.4_GR1-P2.
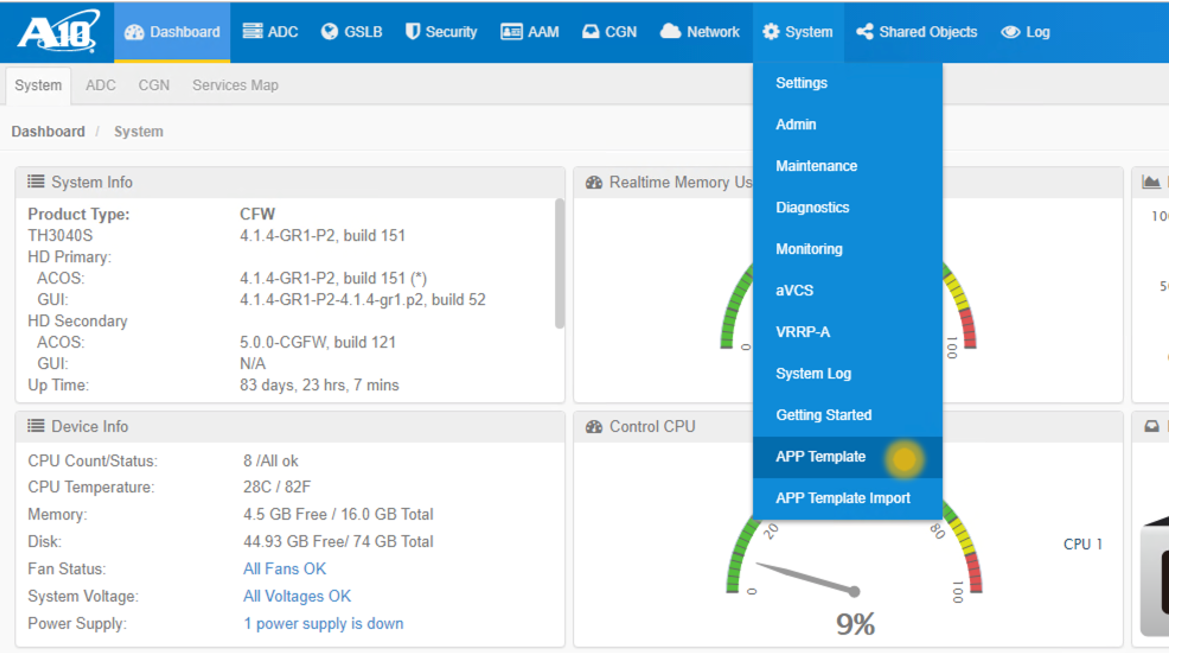
- Open a web browser and launch the Thunder SSLi ACOS Web GUI. (Please refer to the A10 documentation for details on how to open the ACOS Web GUI. This guide was written with a presumption that you have already completed the device management configuration on the Thunder SSLi.)
- Navigate to System > **App Template
*
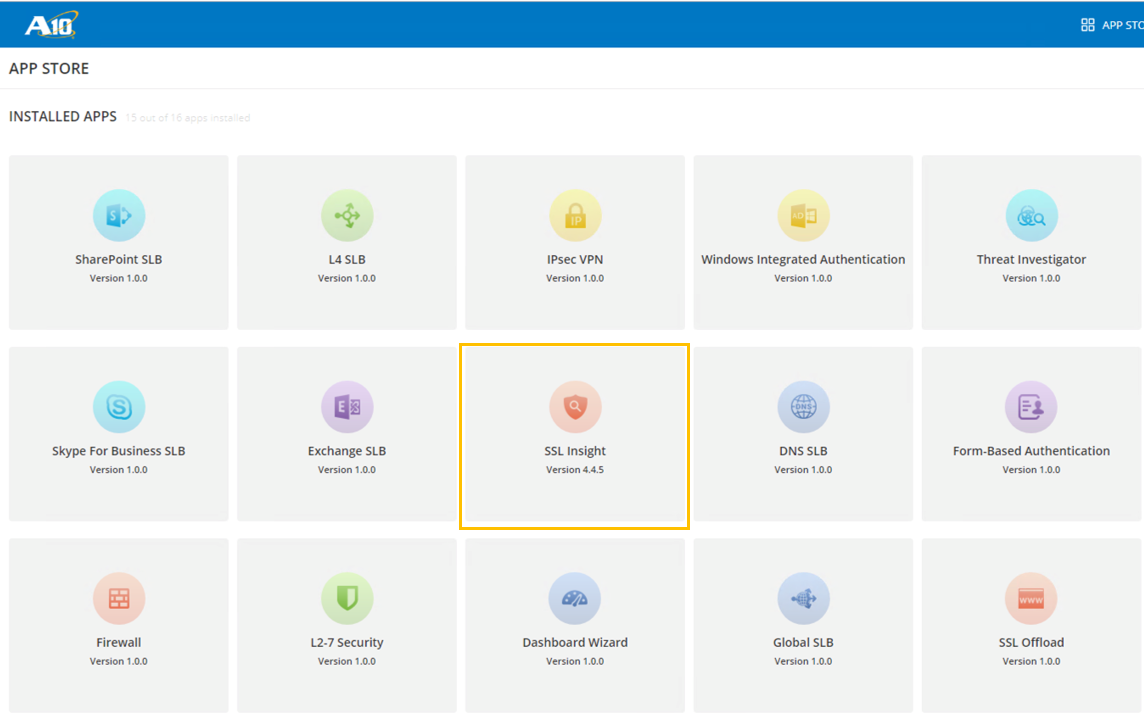
- Select SSL Insight to launch the SSLi App Centric Template (ACT)
- Navigate to the first tab, Wizard on the SSL Insight ACT (if not automatically directed to it).
- Select Custom under the Deployment sub-tab, since the topology would require advanced configuration that needs an IP address to be assigned on the Thunder SSLi appliance. Click NEXT when done.
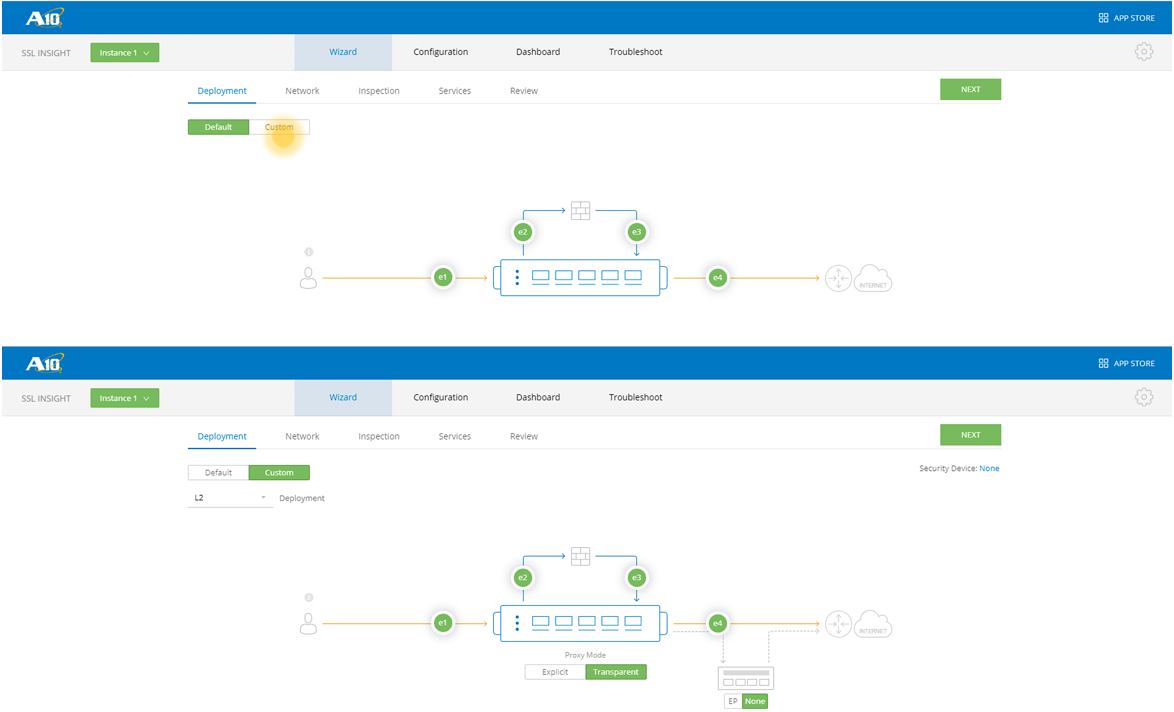
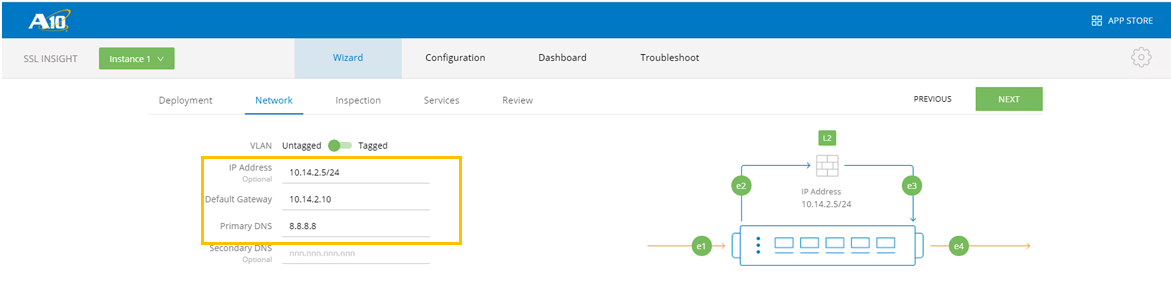
- Under Network, Assign the device IP Address and Default Gateway. Click NEXT when done.
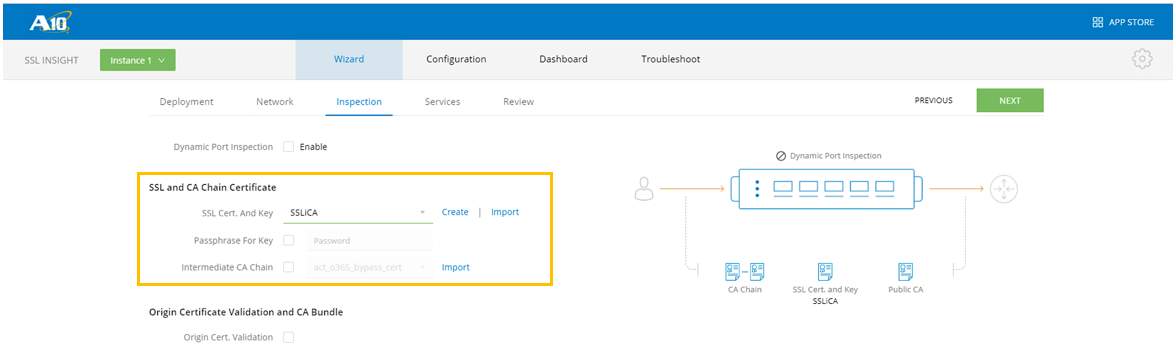
- Import and assign the SSL Cert. and Key. Click NEXT when done.
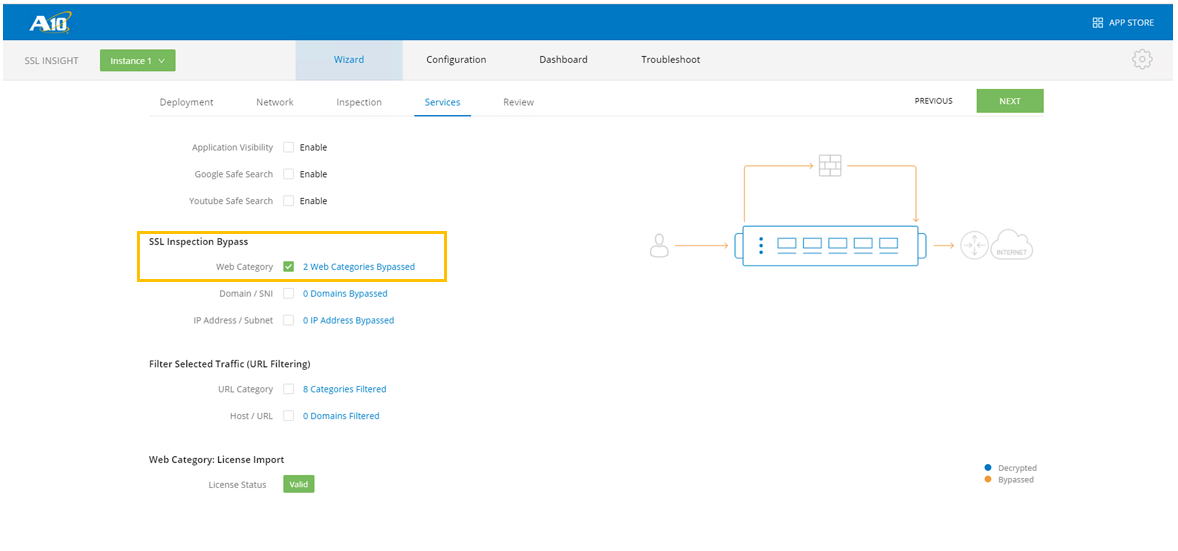
- Select traffic that needs to be bypassed from SSL inspection (for compliance), for e.g. Finance and Healthcare. Click NEXT when done.
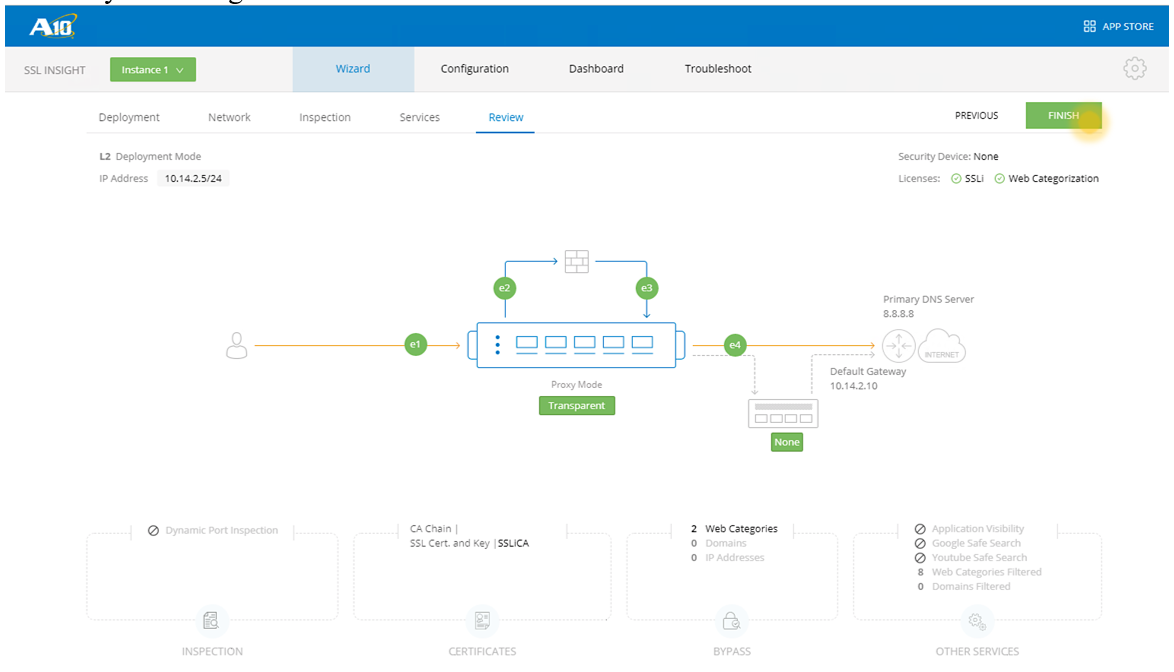
- Review your configuration and click FINISH when done.
- Select APPLY.
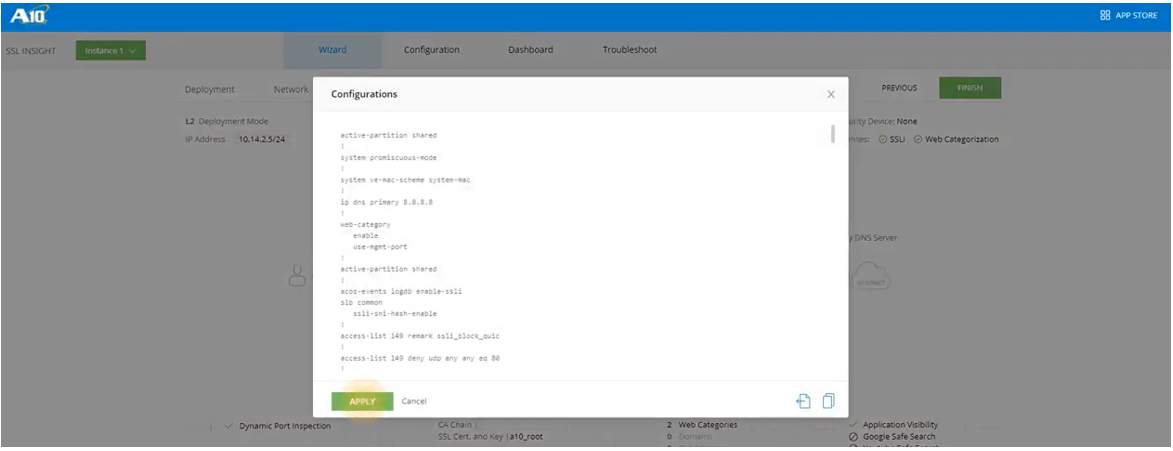
- The configuration will take a few seconds and a pop-up will indicate if the configuration was successful.
- Navigate to the Configuration tab on the SSL Insight ACT, to set up OPSWAT security features.
- Select Edit Services icon next to Configured Services on the right-hand side.
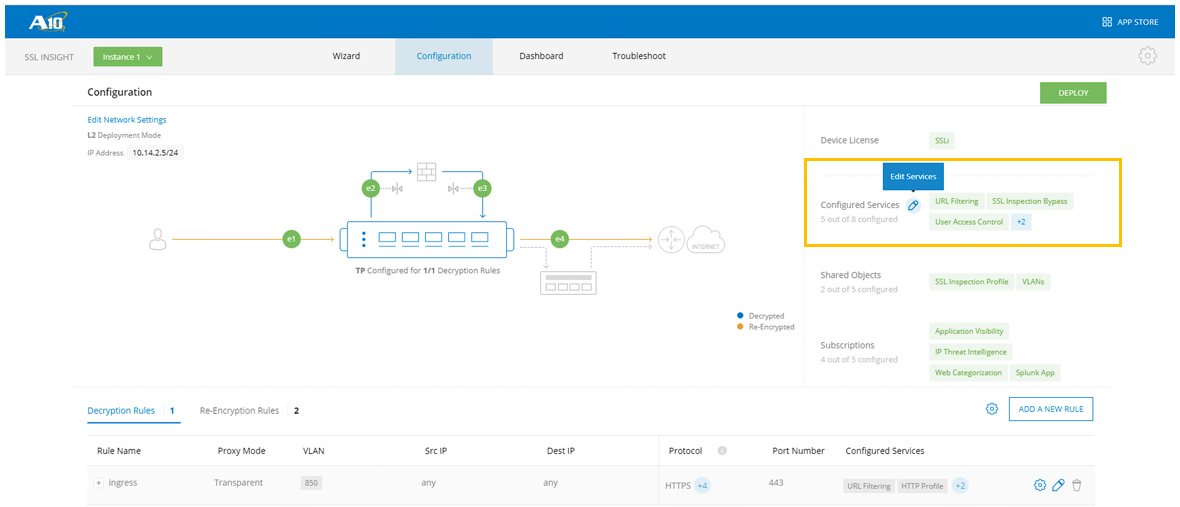
- Under Edit Services, find and select **ICAP Based DLP / AV.
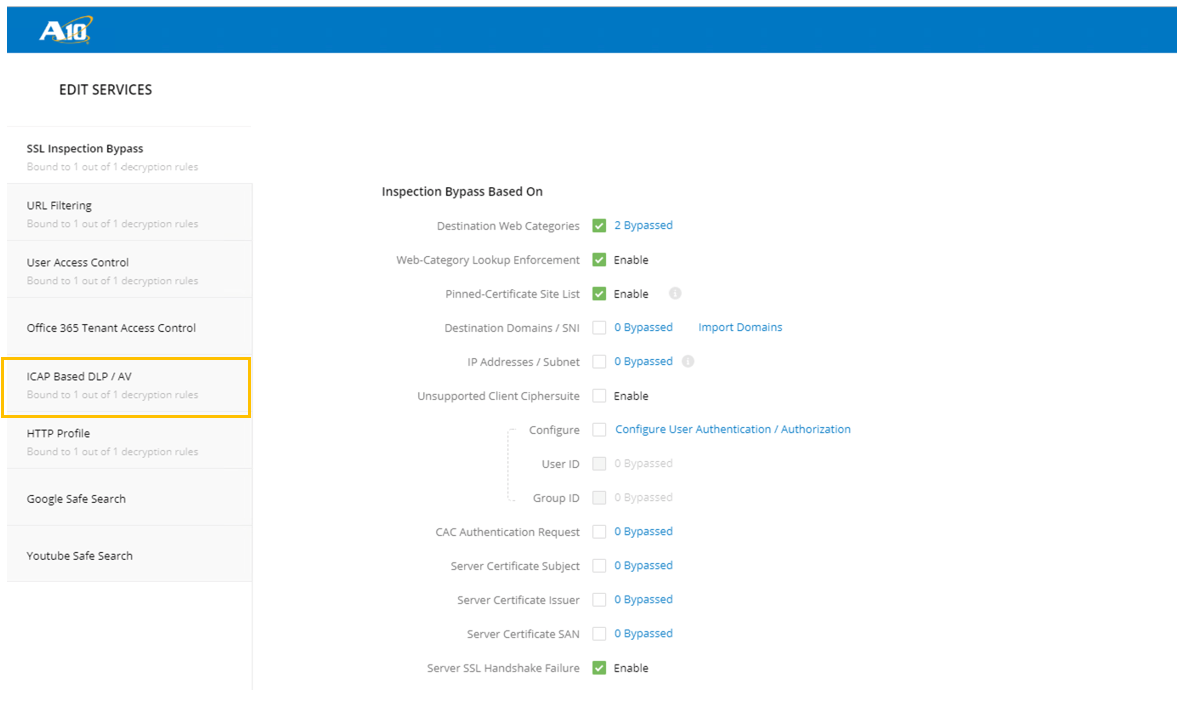
- Check Enable ICAP, then clarify the MD ICAP Server IP Address.
- The ICAP Operation contains a drop drown menu. The MD ICAP server can do REQMOD, RESPMOD, or both.
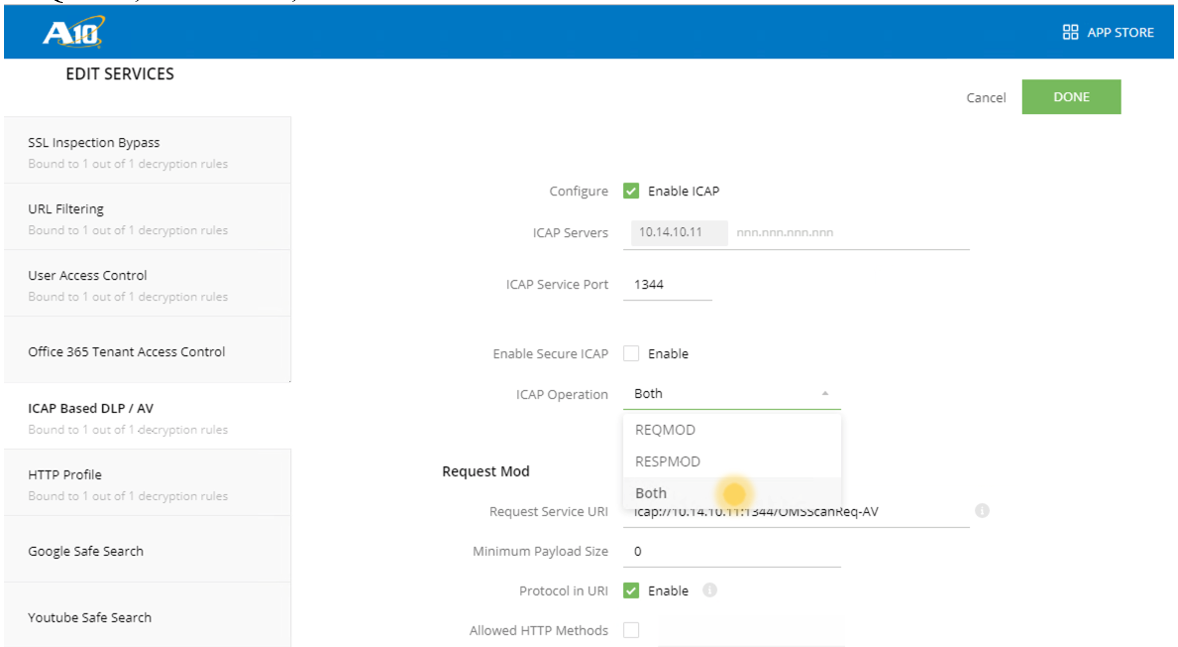
- Make sure to add, OMSScanReq-A or OMSScanResp-A, respectively on the URL on the Request Service URI.
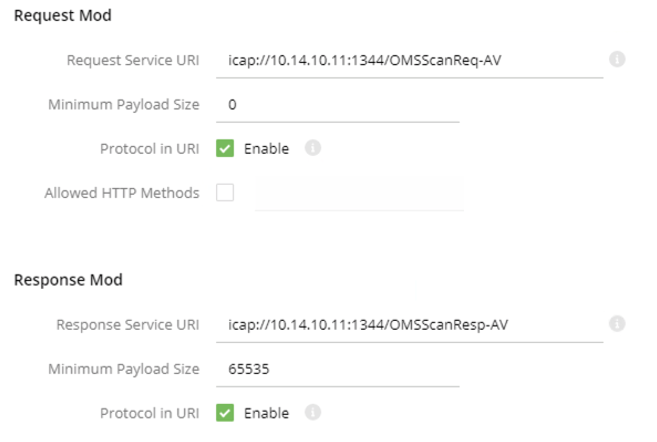
- Select Done on the top right.
- Finally, bind the ICAP policy to either the Decryption or Re-encryption Rule.
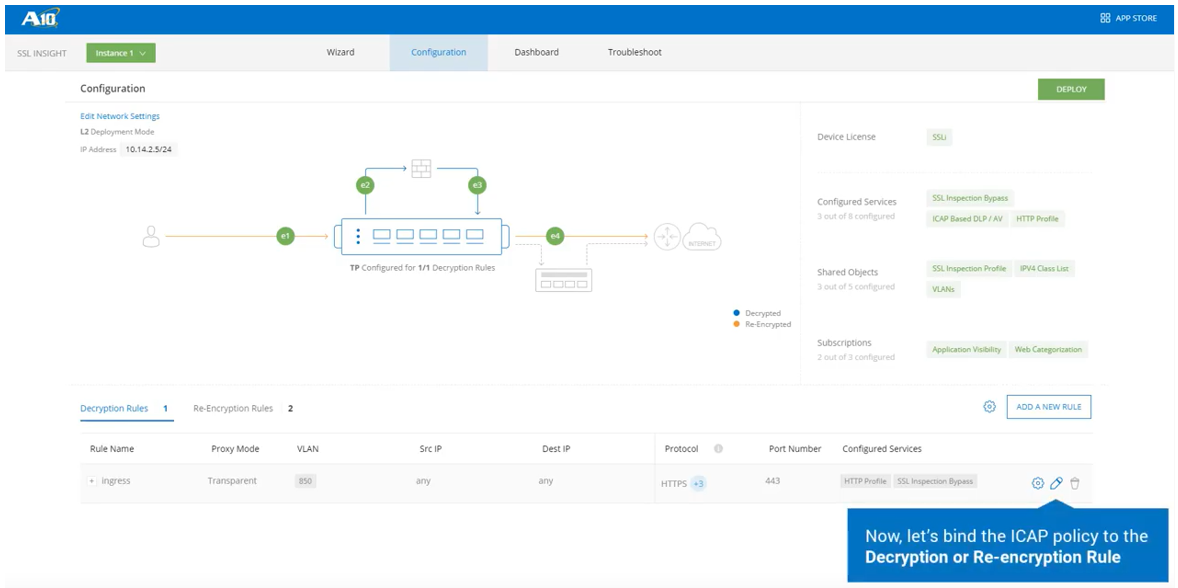
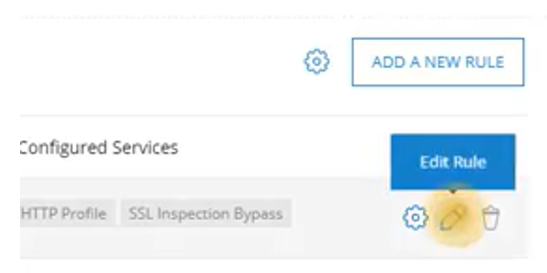
- Select the Edit Rule
- Under the Configured Services in the drop-down options, chose **ICAP Based DLP / AV.
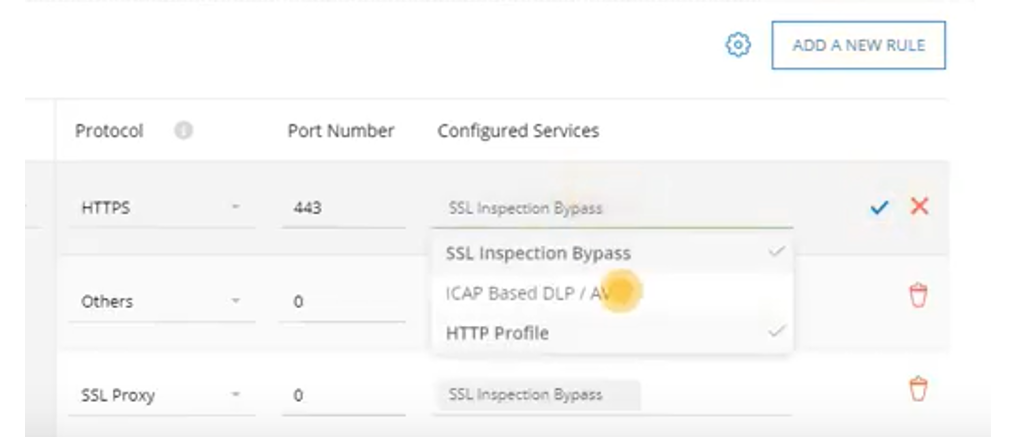
- Select Deploy on the to right.
- Review and select APPLY.
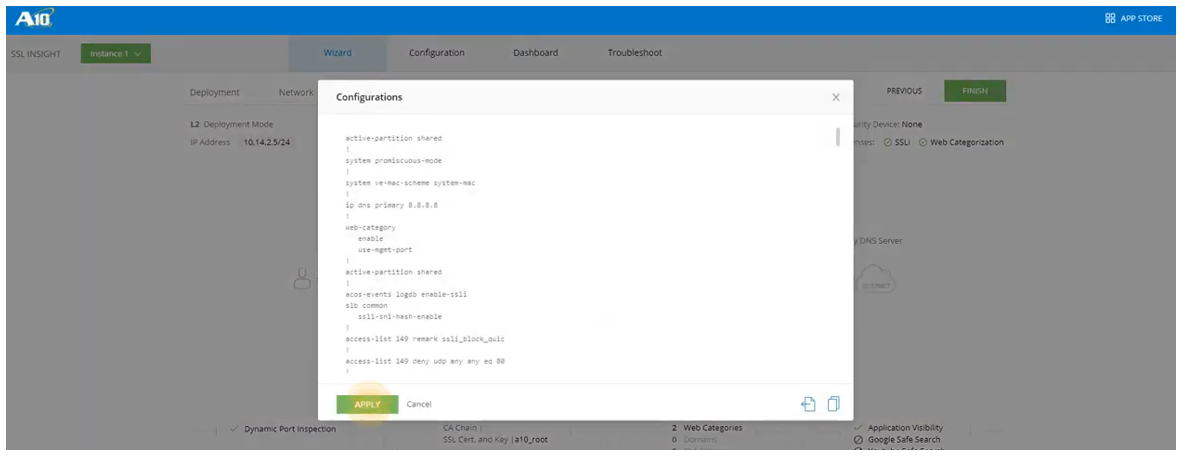
- Configurations will take a few seconds and a popup will indicate if the configuration was successful.
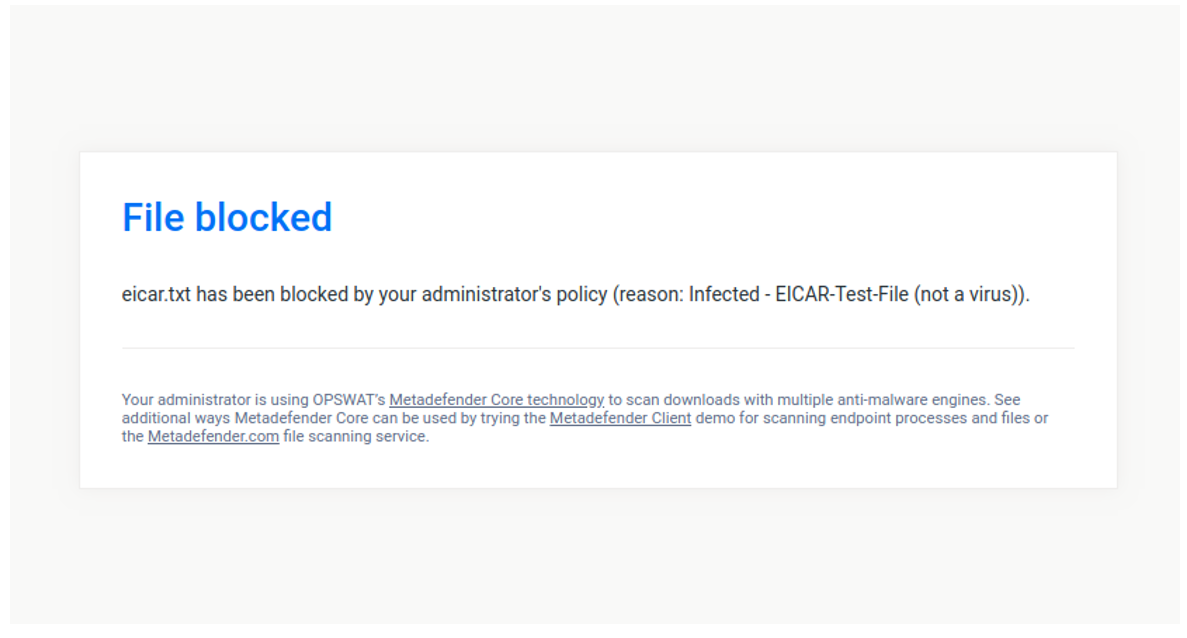
Testing the configuration
To check that you configuration is working as expected try to download an Eicar test file over HTTPS here. If everything was set up properly you should see a blocking page similar to this: