Title
Create new category
Edit page index title
Edit category
Edit link
Processing History
The "Processing History" page allows users with specific roles to view files that have been uploaded to MetaDefender Managed File Transfer™.
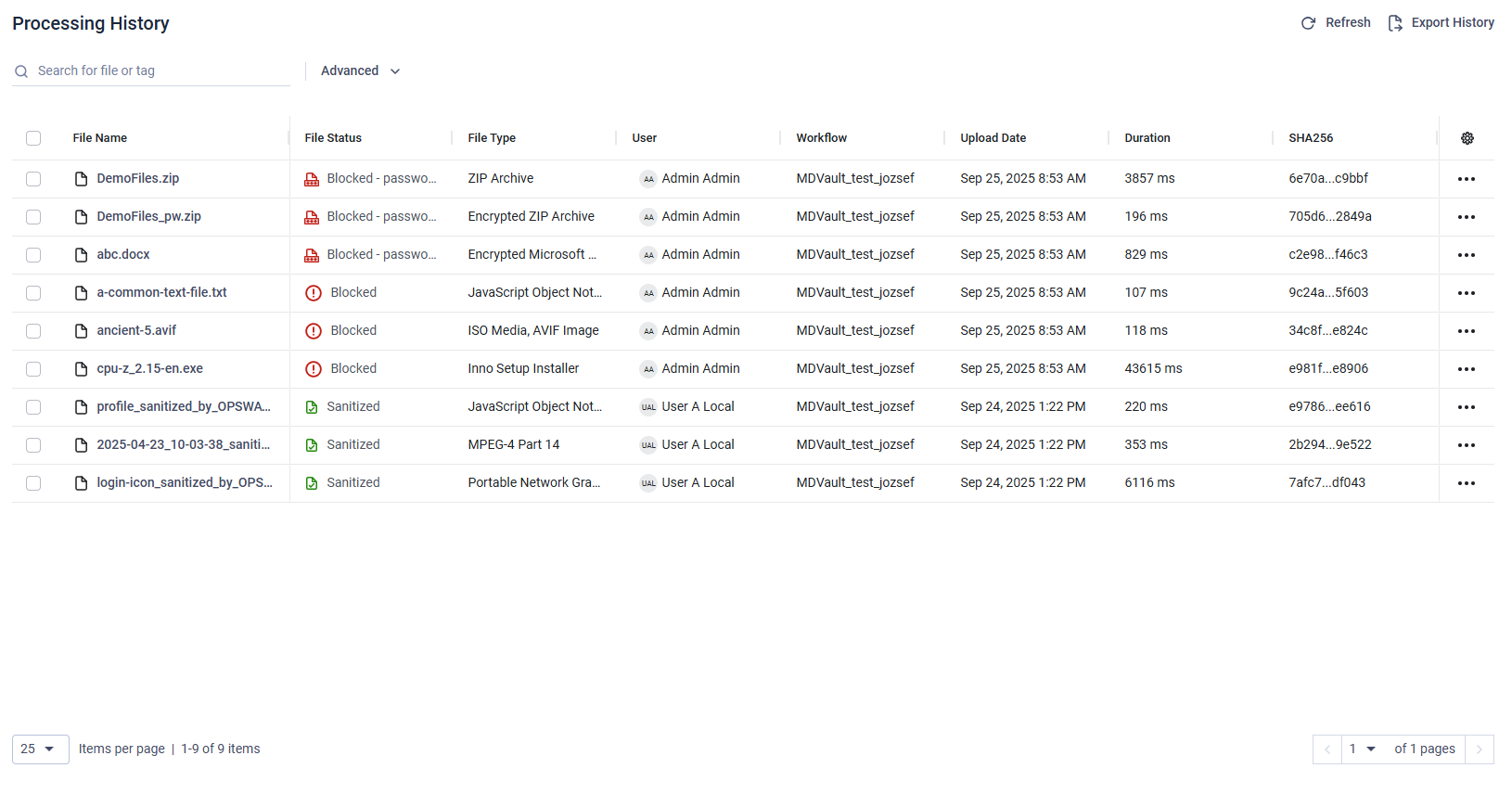
Hide / Show Columns
To toggle the visibility of a column, click the cogwheel icon located in the last column and select which columns you want to show or hide. The desired layout can be stored by clicking on the "Save View" button.
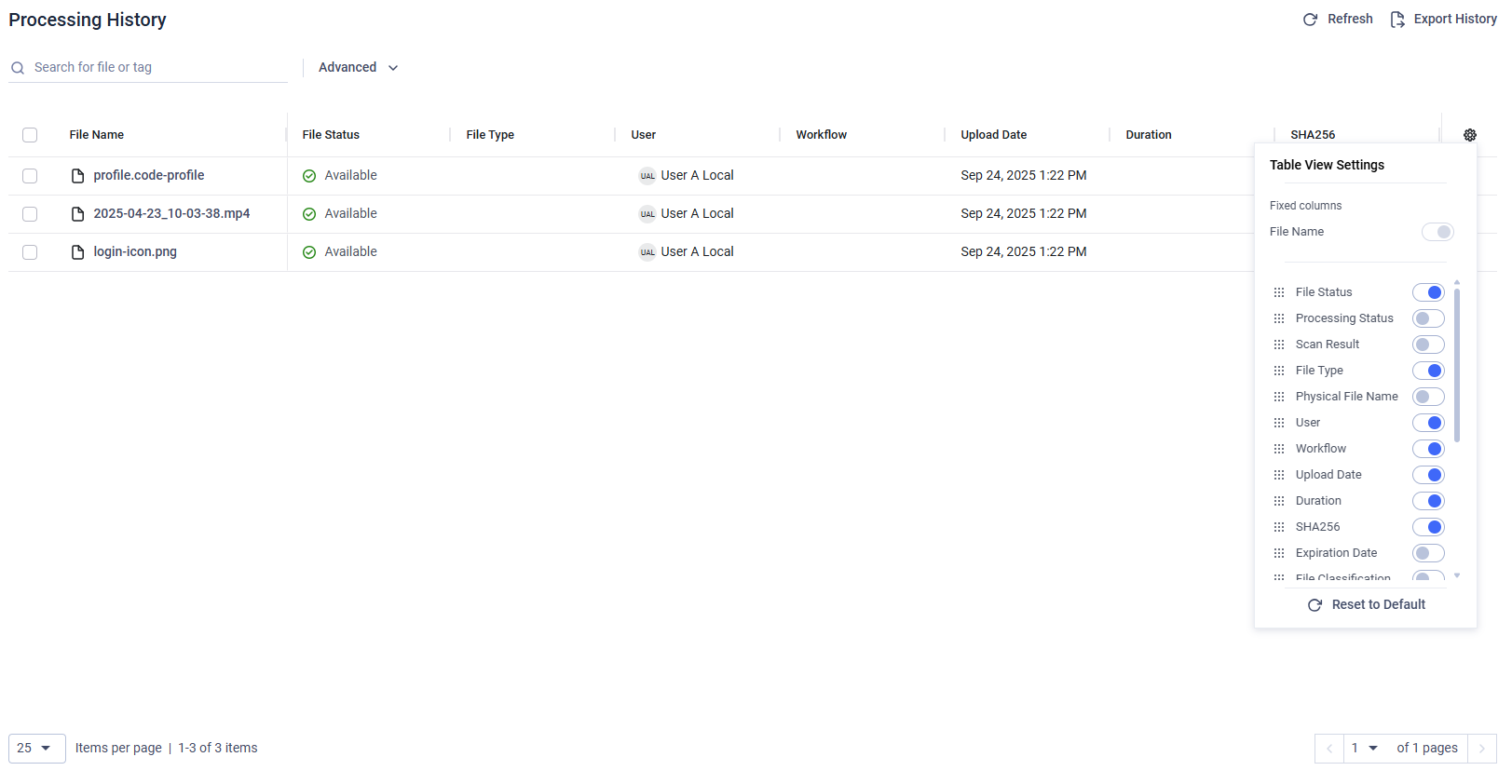
The "Last Time Downloaded" column displays the most recent download timestamp for files shared with users. Downloads by Administrators and Auditors do not affect the "Last Time Downloaded" record.
The "Physical File Name" column displays the actual file name on the associated storage device.
Sorting
On the "Processing History" page, you can sort the data by clicking on the respective column headers. The following fields are currently supported for sorting:
- File Name
- Expiration Date
- Upload Date
- File Size
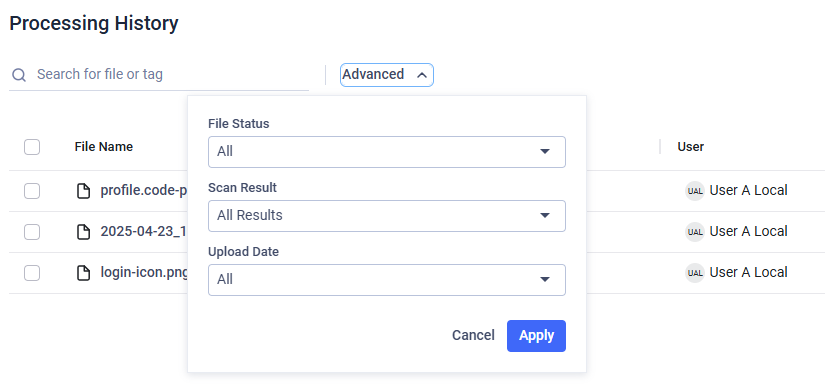
Filtering
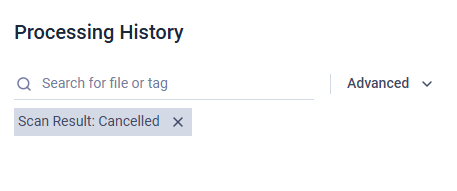
To access available filters, click the "Advanced" button. When a filter is active, you can remove it by clicking the "X" button.
Supported filters:
- State: Filter files based on whether they were Allowed or Blocked.
- Result: Filter files according to the MetaDefender Core's scanning result.
- Date and Time: Narrow down the processing history list using predefined time intervals or create a custom timeframe based on when the file was uploaded.
Exporting History
You can export processing history in CSV format. This export feature allows you to filter records by upload time, offering the option to choose between predefined intervals or custom timeframes. All available columns are included in the export, with localization applied where applicable.
Applied filters or selected columns at the "Processing History" page do not effect the Processing History Export.
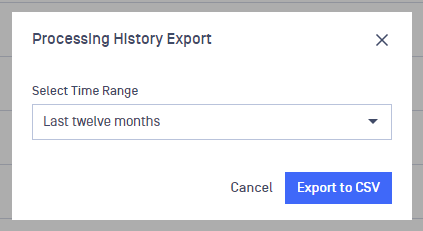
Processing History Export modal
To prevent formula injections (also known as CSV injections), the exported CSV may include additional apostrophe characters at the beginning of fields. This prevents spreadsheet applications from interpreting potentially malicious fields as formulas.
Override Blocked Status and Restore Blocked Status action
Administrators and Restricted Administrators can unblock files that have been marked as blocked by MetaDefender Core™. During the unblock process, they must provide a reason, ensuring transparency since unblocking makes a potentially harmful file available for download to the uploading user. Once unblocked, the file status changes to Available – overridden.
Unblocking a file is a high-risk action, as it may allow malicious content to bypass security controls and become available for download. Administrators and Restricted Administrators must exercise extreme caution and verify the reason for the block before proceeding. This includes double-checking whether the file was blocked due to a false positive or an intentional security measure. Every unblock action requires a documented justification to ensure accountability and transparency.
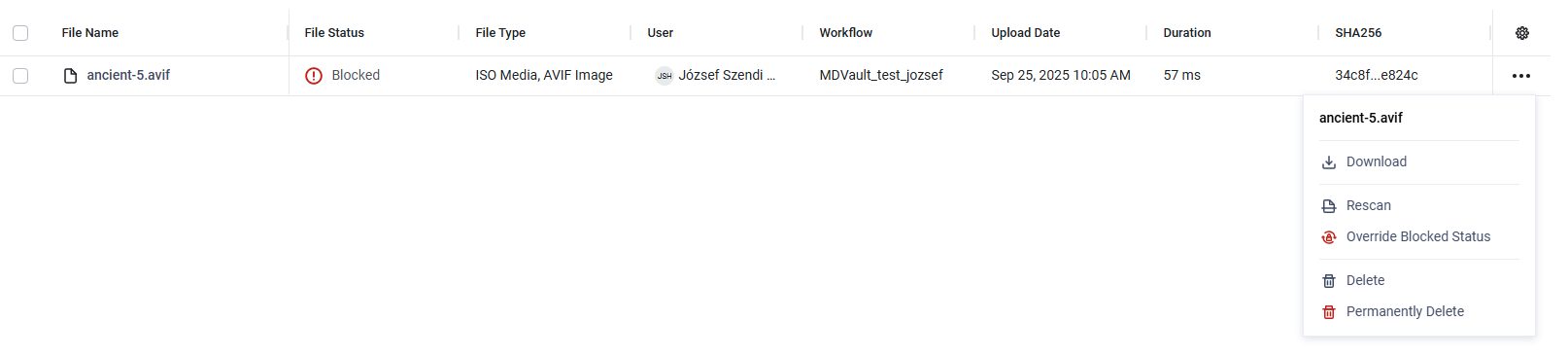
Override Blocked Status action available for Blocked files
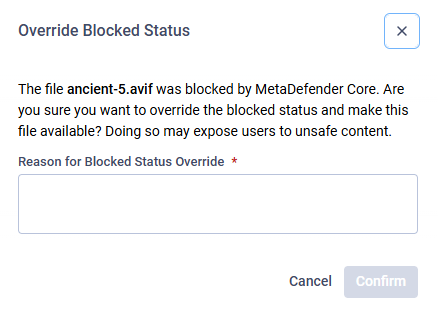
Admin has to provide a reason to Override Blocked Status
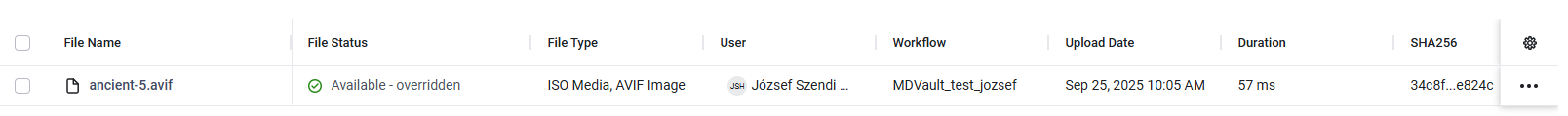
Overridden file status
An unblock action can be reverted by an Administrator or a Restricted Administrator. When reverting an unblock, they must provide a reason to maintain transparency. After the action is completed, the file status is changed back to Blocked.
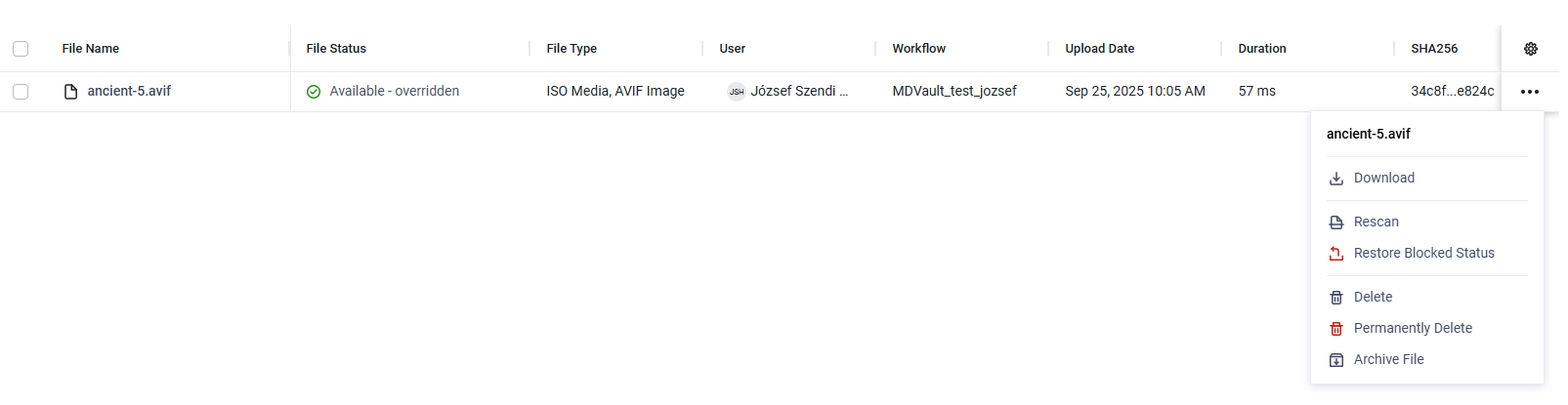
Restore Blocked status action for Overridden Files
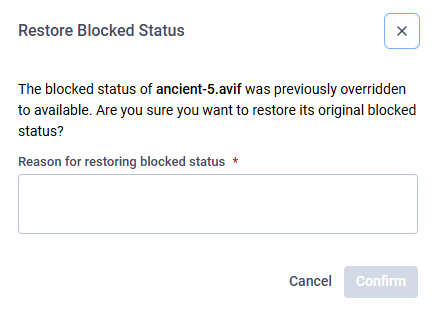
Admin has to provide a reason to Restore Blocked Status

