Create SAML directory on MDCore
- Login to MDCore
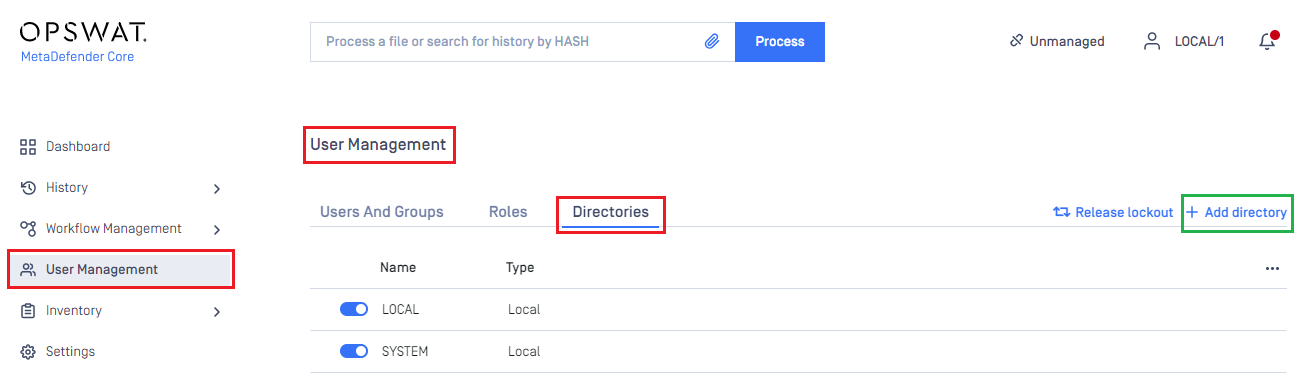
- At dashboard, hit
User Managementin sidebar - Under
User Managementpage, chooseDirectoriestab and hitAdd directoryon the top right
- In
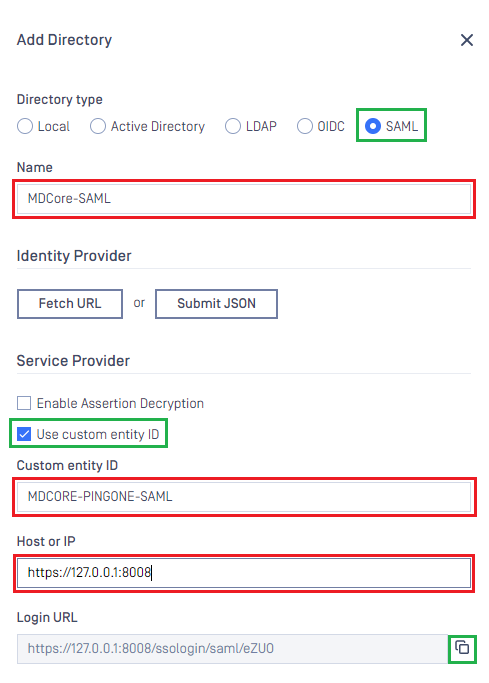
Add Directorypage, chooseSAMLinDirectory Type, fillNamefor the new directory, MDCore-SAML for example - Under
Service Providersection, enable optionUse custom entity IDand fill out the ID, MDCORE-PINGONE-SAML for example, then store it in entity_id - Fill
Host or IPwhere MDCore is hosting, https://127.0.0.1:8008 for this example - Copy string generated under
Login URLand store to reply_uri
Create and configure SAML application in PingOne
- In the PingOne Overview page, navigate
Applicationson sidebar
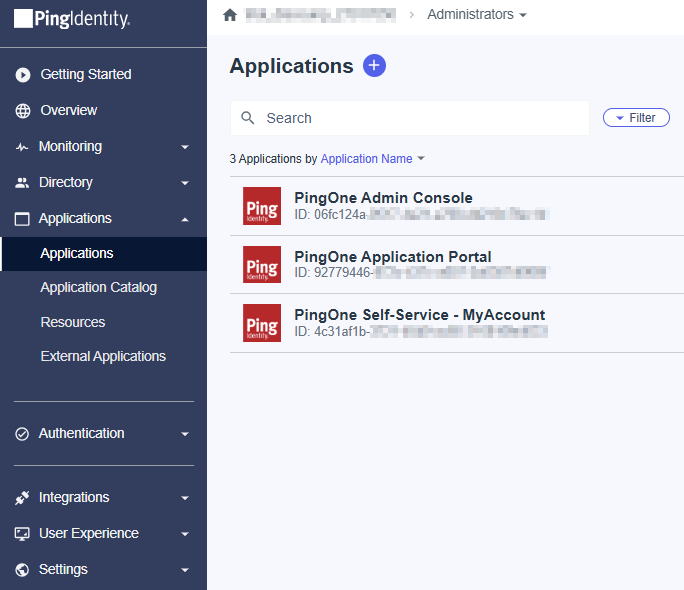
- Hit on plus button to add new application

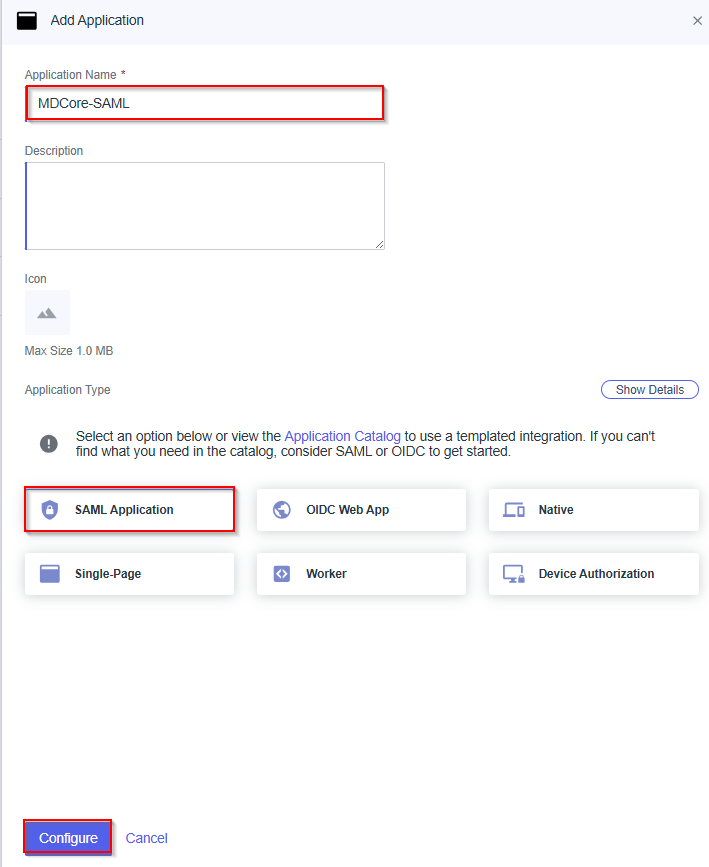
- Fill application name, MDCore-SAML for an example, choose
SAML Applicationfor Application Type and hitConfigure
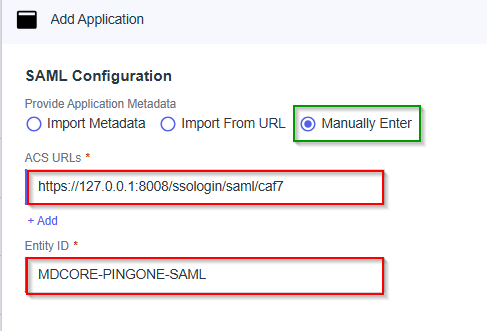
- Select
Manually Enterfor SAML Configuration, fillACS URLswith reply_uri, andEntity IDwith entity_id, and hitSave
- Select
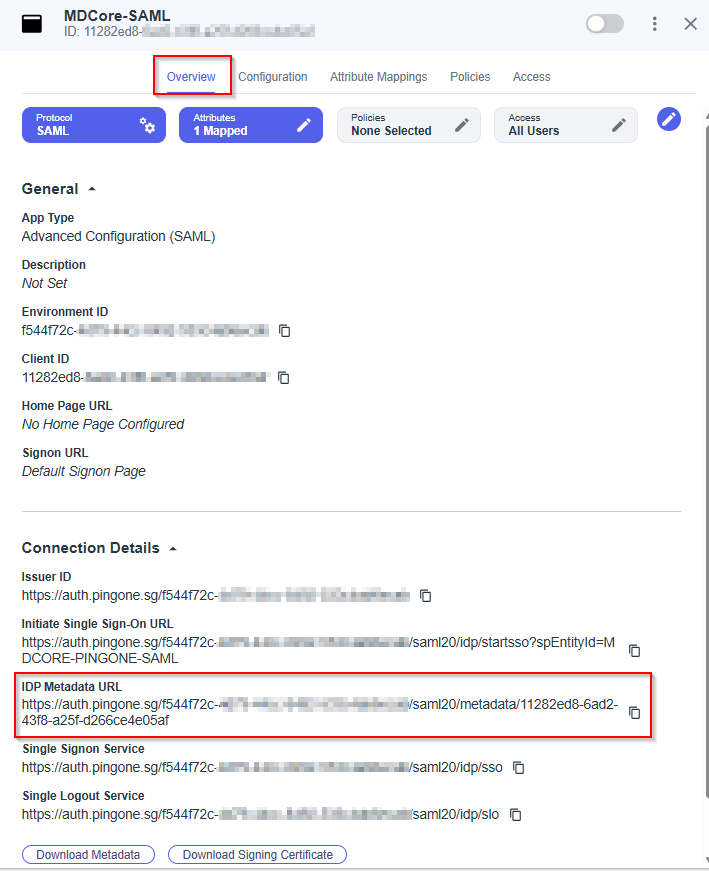
Overviewtab, navigate toIDP Metadata URL, copy the link below and store to metadata_url
__
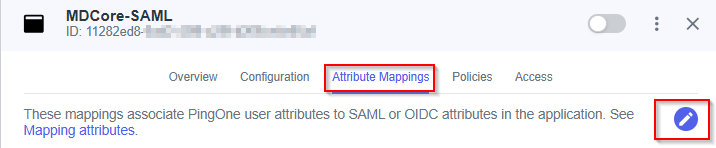
- Select
Attribute Mappingstab and click Edit button.
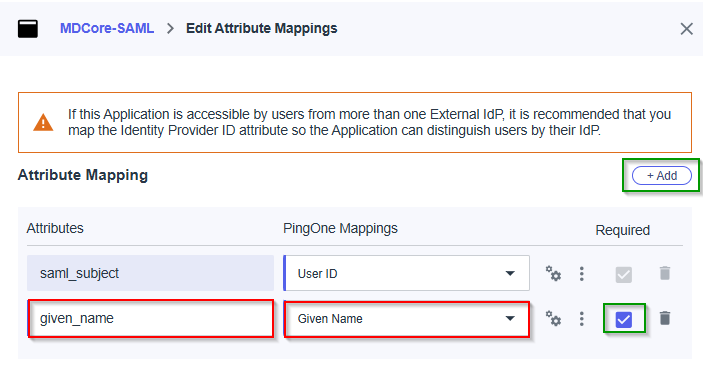
- In
Edit Attribute Mappingspage, hitAddto add new mapping
In this step, we make a mapping from the key name used by MDCore and the name exported by PingOne. For example, we set given_name mapped to Given Name exported by PingOne. Later on, given_name is used by MDCore to identify the login user
- Fill attribute name,
given_namein this example, select itemGiven Namein PingOne Mappings, enableRequiredoption and hitSaveto complete
- Enable the new application on PingOne
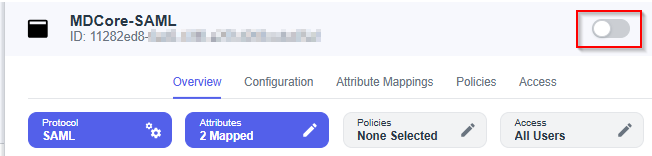
Complete configuration on MDCore
- Switch back to MDCore, under
Identity Provider, hitFetch URL, paste metadata_url to the box under, and then hitOK, which requests MDCore to check and set PingOne as its IDP if succeed

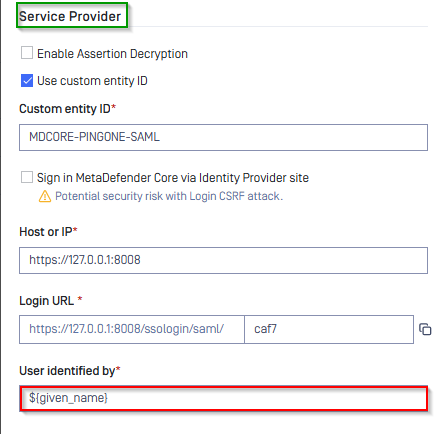
- Under
Service Provider, fill ${given_name} in the box underUser identified by
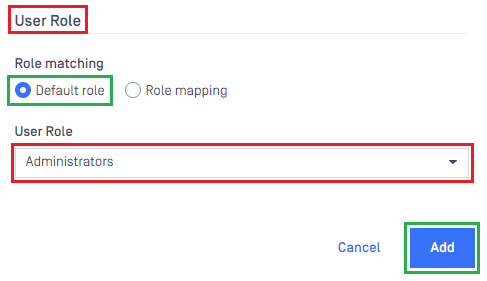
- Select
Default roleoption, choose the role to assign to login user underUser Roleand hitAddto complete setting on MDCore
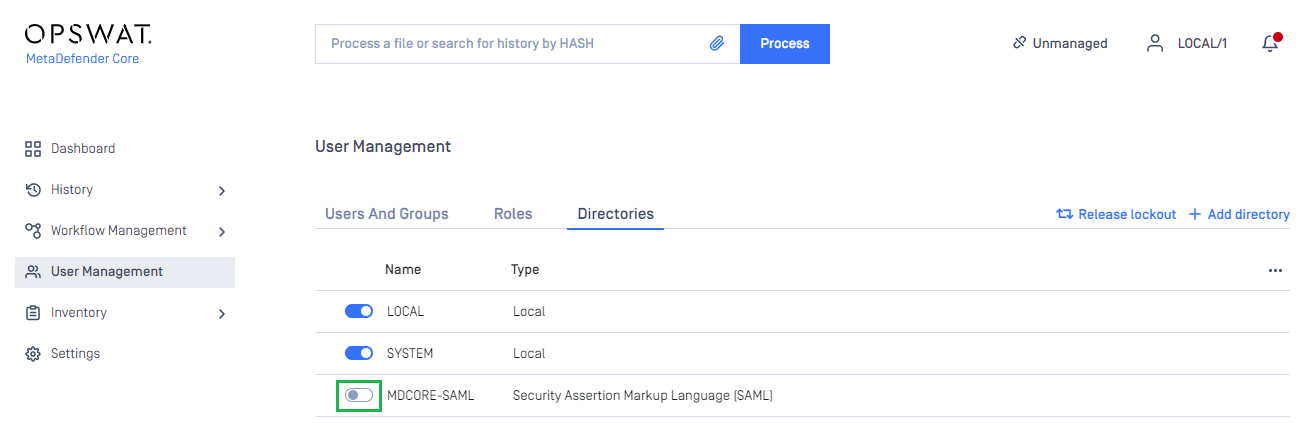
- In
User Managementpage, toggle the new directory, MDCORE-SAML in this example. A dialog box is shown to confirm the action. OnceEnableis hit, all sessions are expired immediately
Test the integration
- In home screen on MDCore, hit
Login, the user is redirected to login page from PingIdentity
- Login by the account registered to PingIdentity
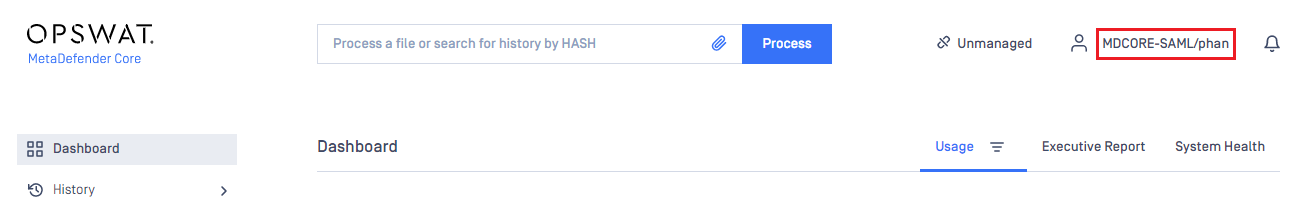
- If everything goes right, MDCore dashboard is shown with user identity set at the top right corner

- Otherwise, access back login page at
<mdcore-host>#/public/backuploginfor trouble shooting.
Test IdP-initiated login
- Login to PingOne management page.
- On the left sidebar, hit
Applications, thenApplications. - Select the SSO directory from which IdP-initiated login is enabled. MDCore-SAML in this example.

- On the right sidebar, hit tab
Overview. Copy the URL underInitiate Single Sign-On URL.

- Paste the URL into your browser and try to sign in.
- If everything goes right, MDCore dashboard is shown with user identity set at the top right corner
- Otherwise, access back login page at
<mdcore-host>#/public/backuploginfor troubleshooting.

