Title
Create new category
Edit page index title
Edit category
Edit link
Enabling HTTPS
MetaDefender Core supports accessing Web UI and REST interface via HTTPS. This feature is not enabled by default.
There are two ways to enable the feature:
- via Management Console or
- modifying MetaDefender Core server configuration via configuration files.
TLS v1.2 and v1.3 are supported HTTPS connection.
If HTTPS is configured via both: Web Management console and configuration file, only the settings made on Management Console will take effect. It is highly recommended not to use both configuration files and Management Console for HTTPS settings at the same time.
Enabling HTTPS via Management Console
- Go to Settings→Security page
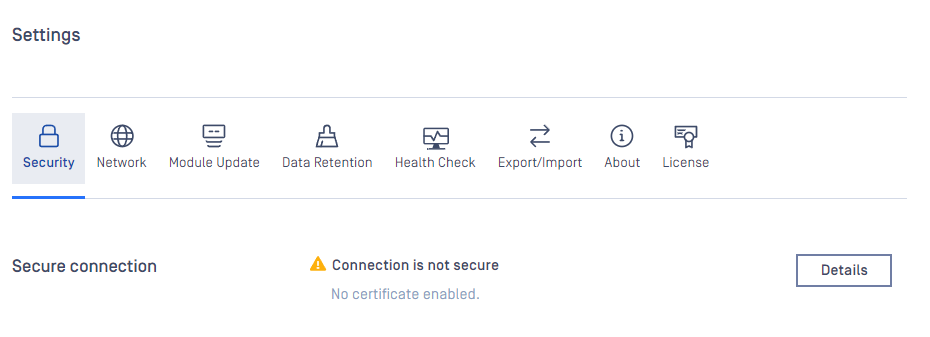
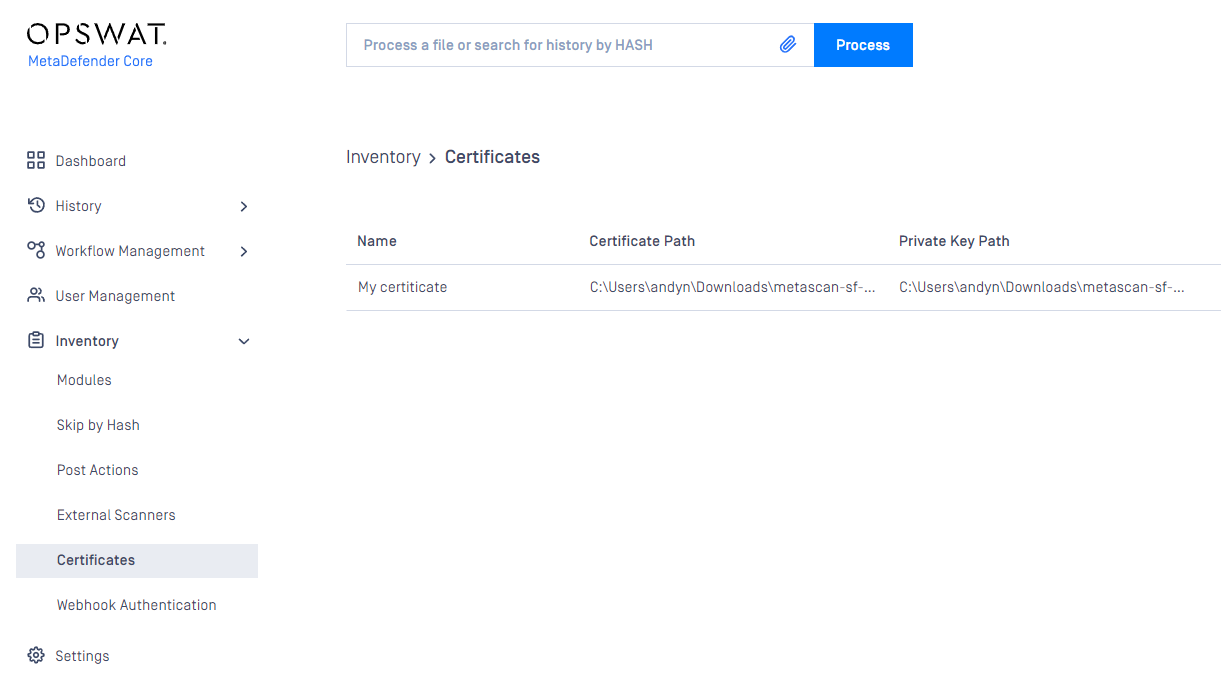
- If there's no certificate-key pair added to the inventory, please go to Inventory→Certificates add one that is desired to use for securing HTTP connections.
- Check Enable certificate connection button and choose a certificate-key pair.
- Users can define advanced SSL settings in the "Advanced SSL Settings" section. These settings follow Nginx syntax.
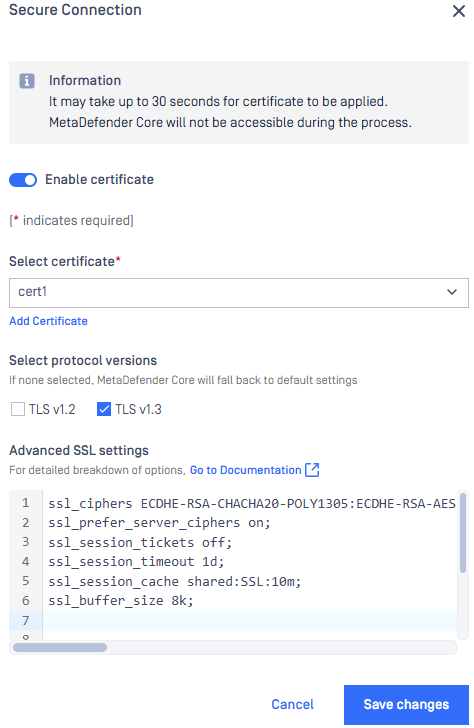
- As clicking on Save changes, you will be warned that Management Console is going to be restarted and this will take some time.
- Approximately 30 seconds after confirming saving of configuration the Management Console will be reloaded via HTTPS.
Enabling HTTPS via configuration files
Starting from version 5.14.0, advanced SSL settings can be configured directly through the UI. We highly recommend using the UI for SSL configuration to ensure better management and ease of use.
For config HTTPS via configuration file, please use this instruction: SSL Configurations

