Title
Create new category
Edit page index title
Edit category
Edit link
Inventory Management
Metadefender Core displays detailed information on scan nodes and the status of engine updates including anti-malware engines, archive engines, etc.
Certificates
On this page, path to certificates and private keys for signing scan batches or HTTPS configuration can be given.
- Certificate should be in a Base64-encoded X.509 certificate file (.crt, .cer) format.
- Private key should be a privacy-enhanced electronic mail file (.pem) format and it should not be locked by password.
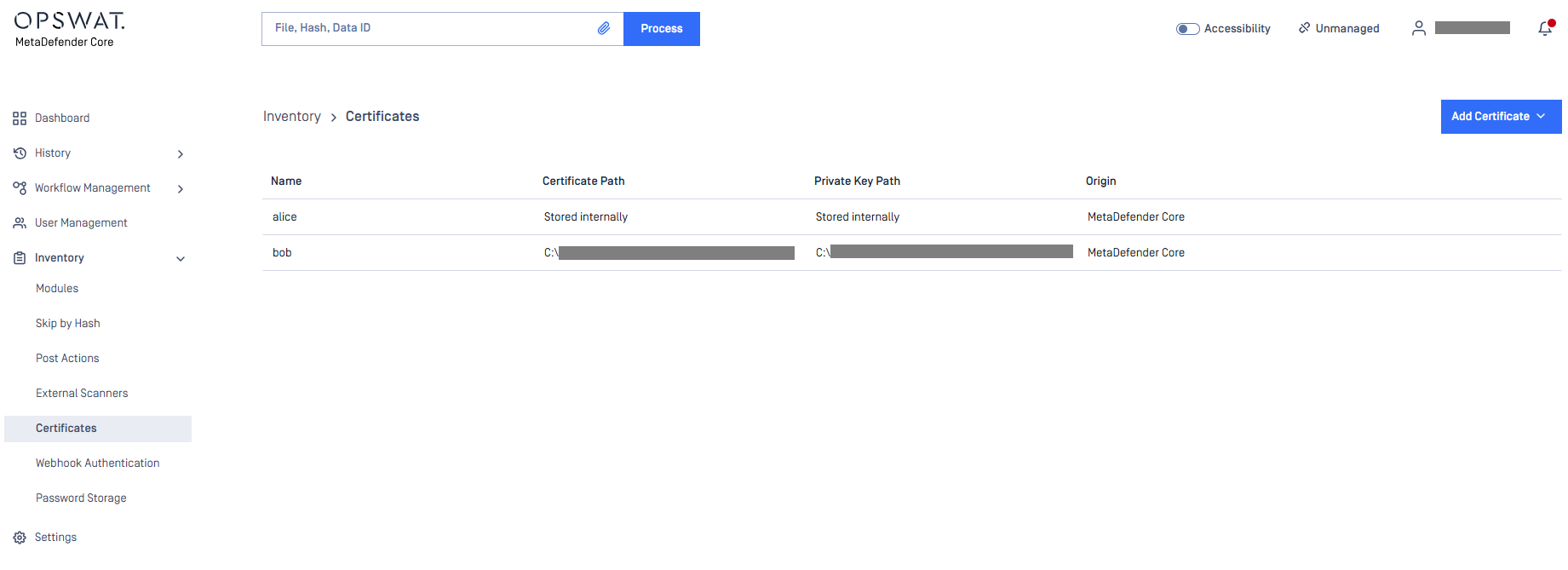
Adding certificate-key pair to the inventory
- Go to Inventory → Certificates page
- Click on Add Certificate button
- Fill out the Add new certificate form using one of the following methods:
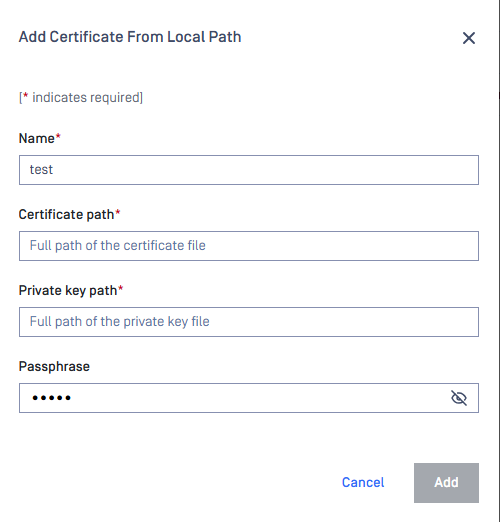
Method 1: Add From Local Path
- Name: Certificate name - Certificate Path: Absolute path to the certificate file - Private Key Path: Absolute path to the private key file - Passphrase: Enter the passphrase for the private key (if required)
Method 2: Add By Uploading File
- Name: Certificate name - Certificate: Upload the certificate file - Private Key: Upload the private key file - Passphrase: Enter the passphrase for the private key (if required)
- Click Add button

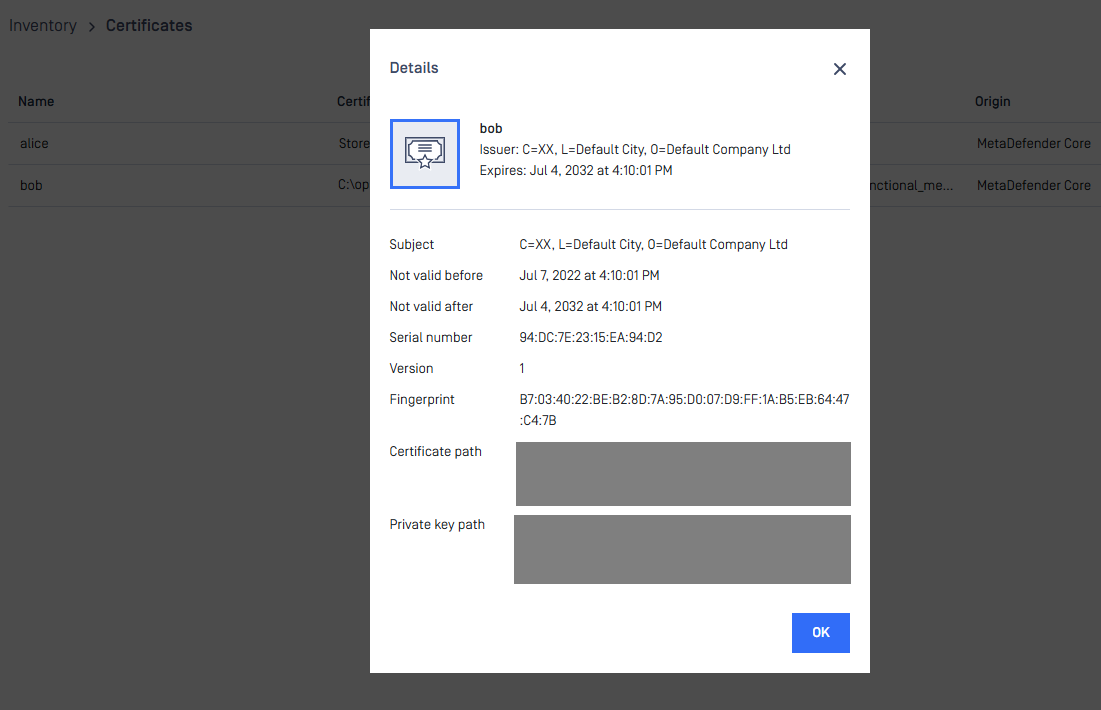
Checking the details of a certificate
By clicking the line of the certificate, the "Certificate viewer" pops up and shows the details of the certificate.
Modifying the name, passphrase or the paths of a certification
Hover the mouse cursor over the line that is to be modified and click on the pen picto. The Modify certificate modal pops up and the fields can be edited.
The certificate file and the key file should be readable by the user who owns the ometascan process.
Webhook Authentication
While leveraging webhook on MetaDefender Core, the callback connection stays at un-secured by default. To harden the security, MetaDefender Core supports a mutual authentication mode between the server (MetaDefender Core) and client (where the callback is sent to), and prevents the man-in-the-middle attack (scan results could be possibly altered unauthorizedly).
How this security feature works
- Admin user to request MetaDefender Core to generate a private-public key pair (the private key is encrypted within the product, and could not be seen or readable by anyone)
- Admin user to download and keep that public key in their secret vault on the client side (where the callback is sent to).
- Admin user to configure MetaDefender Core to use the private key in a desired workflow rule, for each scan request:
- MetaDefender Core to calculate the signature of scan result using the selected private key.
- MetaDefender Core to include the calculated signature into the callback response header before sending back to client.
- Client side (where the callback is sent to) to use the stored public key to:
- Decrypt the signature included in the callback response header.
- Calculate SHA256 hash checksum from the callback reponse body (which is the entire scan result).
- Compare the calculated SHA256 hash checksum to the hash value decrypted from the callback response header.
MetaDefender Core also supports admin users to configure the user role for whom allowed to see and modify webhook authentication settings.
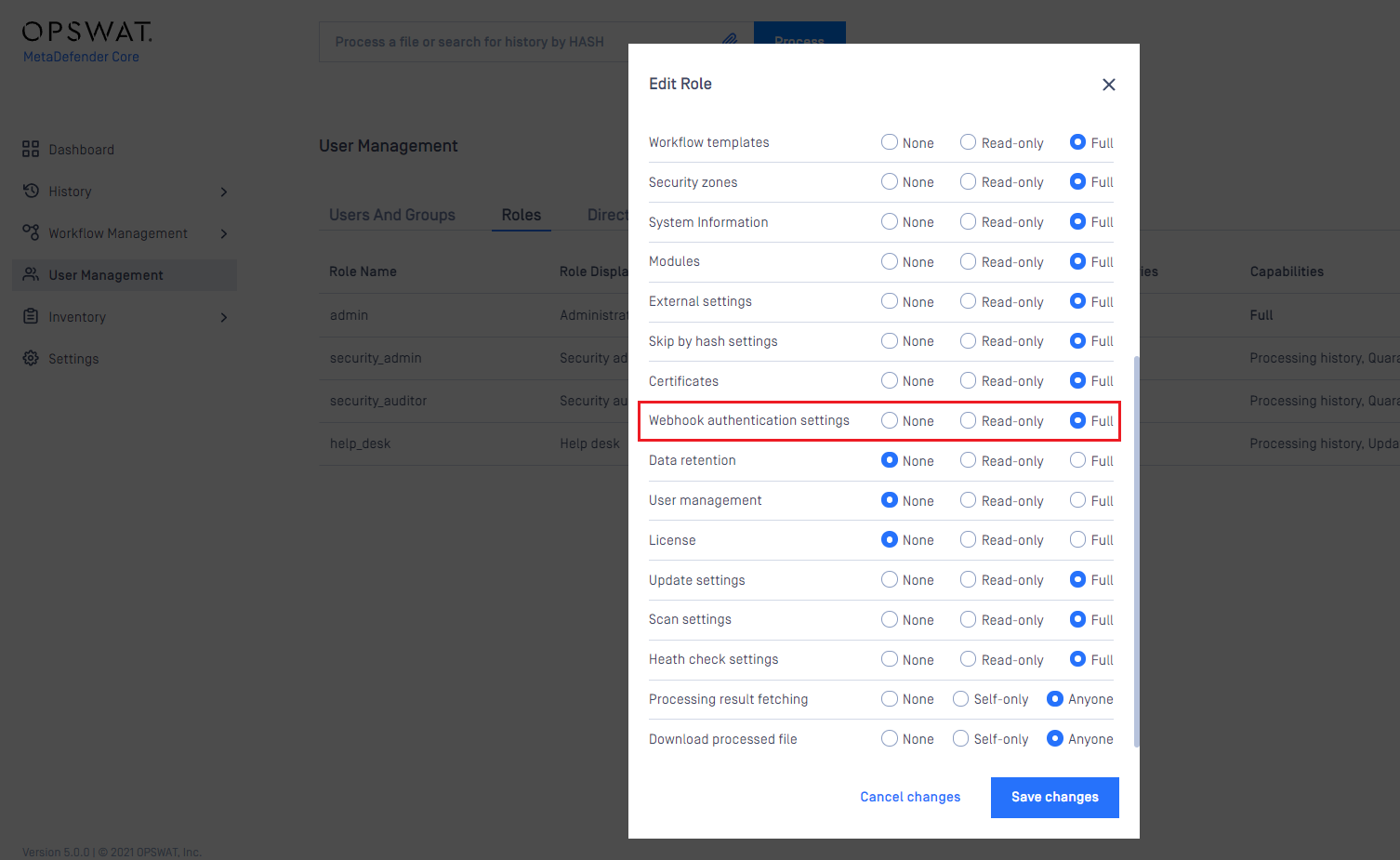
Create a new certificate-key pair for webhook authentication
- Go to Inventory→Webhook Authentication page
- Click on Add certificate button
Modules
Engine type details
Under the Modules menu all the installed engines are listed with their details such as
Type of engine. Possible types are
- Anti-malware engine
- Archive engine
- Proactive DLP engine
- Deep CDR engine
- Adaptive Sandbox engine
- Software Bill of Materials engine
- Filetype detection engine
- Reputation engine
- Country of Origin engine
- Utility engine
- Vulnerability detection engine
Elapsed time since last update
Proportion of active and non-active engines of a particular type
Engine version
Version of database the engine is currently using
Engine status (Active/Non-Active)
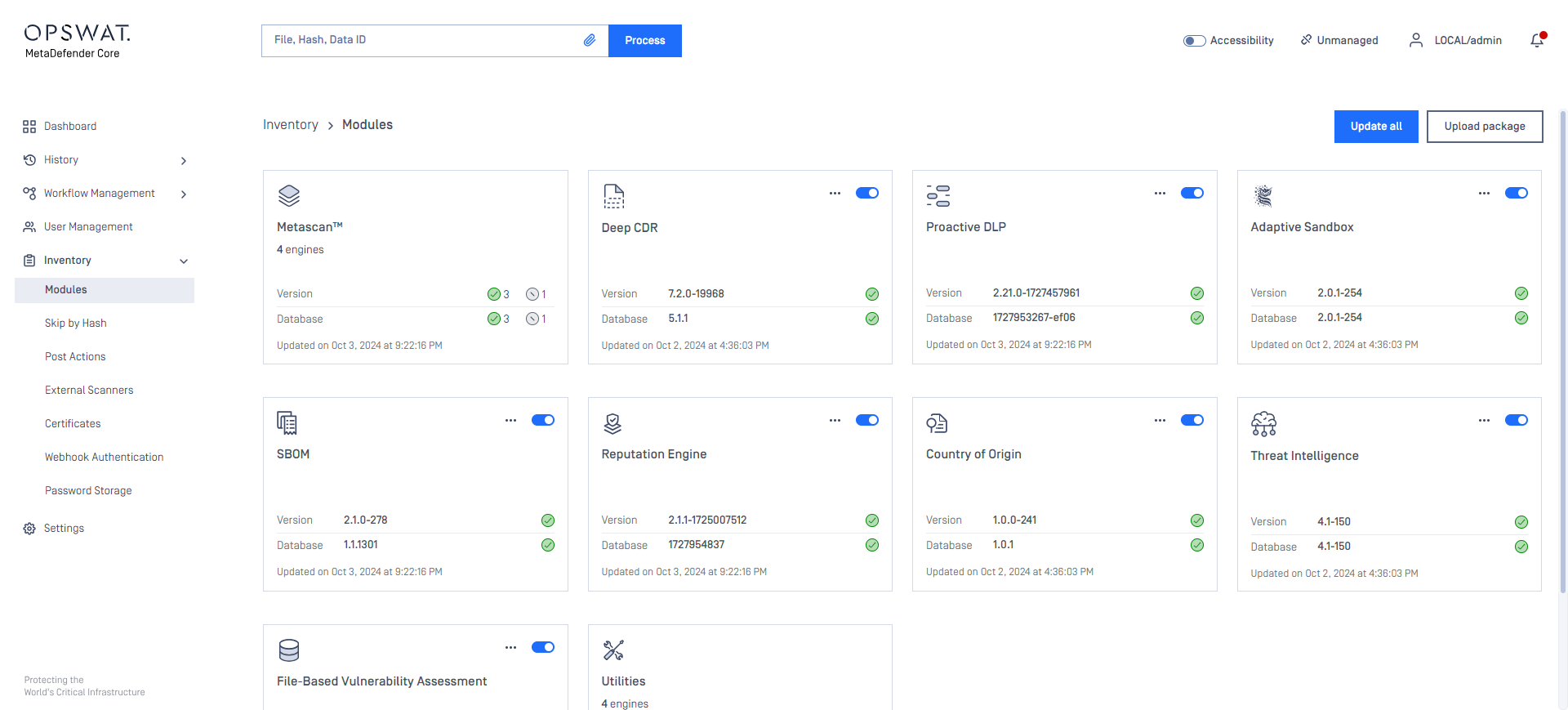
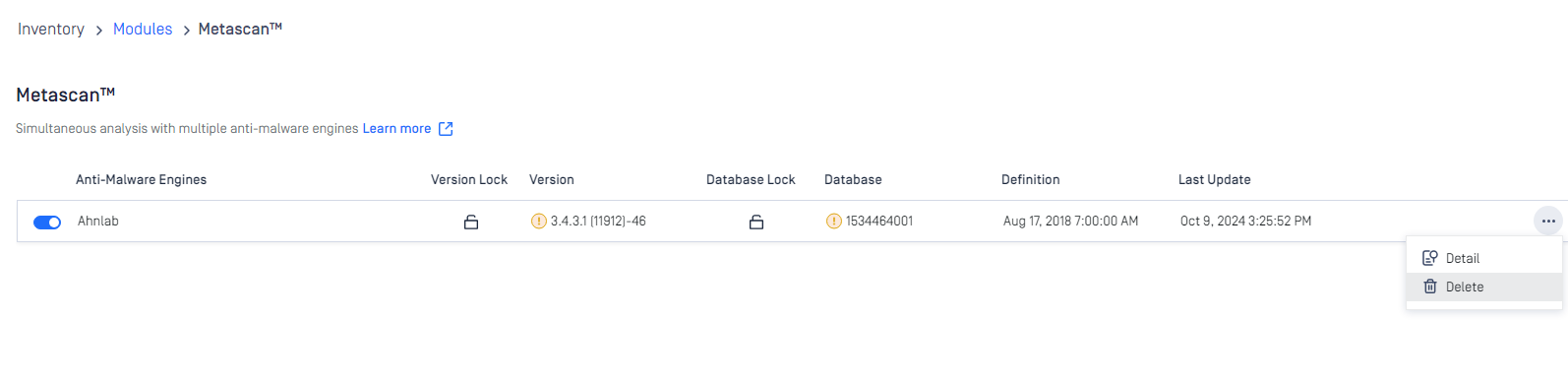
Engines can be disabled (and re-enabled afterwards) by clicking on the switch at the end of the line that belongs to that particular engine. When an engine is disabled neither the engine nor the corresponding database package is updated and it will be removed from every node.
Lock & Unlock engines (for auto-update prevention)
Engine and its database can be locked (previous called pin and unpin) to prevent it from being applied new updates when you allow auto update on Core.
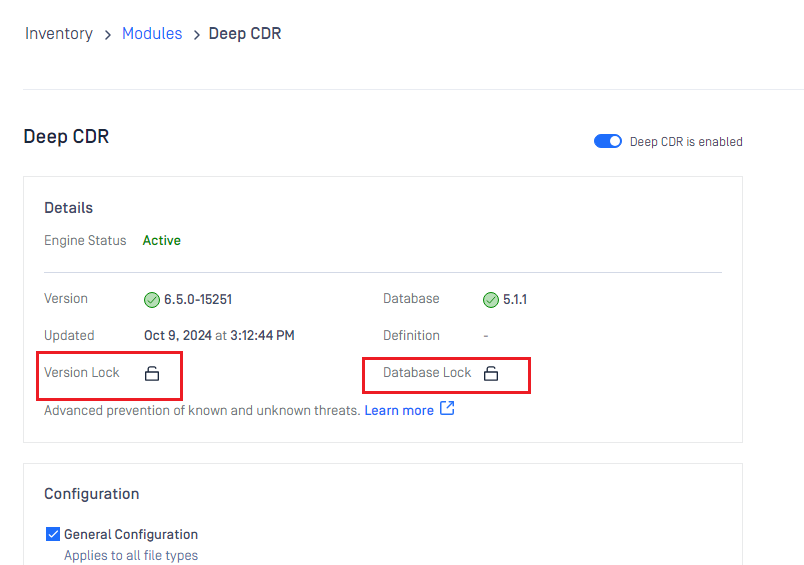
- You can lock engine and database individually on same engine
- When locked, that means no auto update can be applied on that part (engine / database), even when user triggers "Update All" button
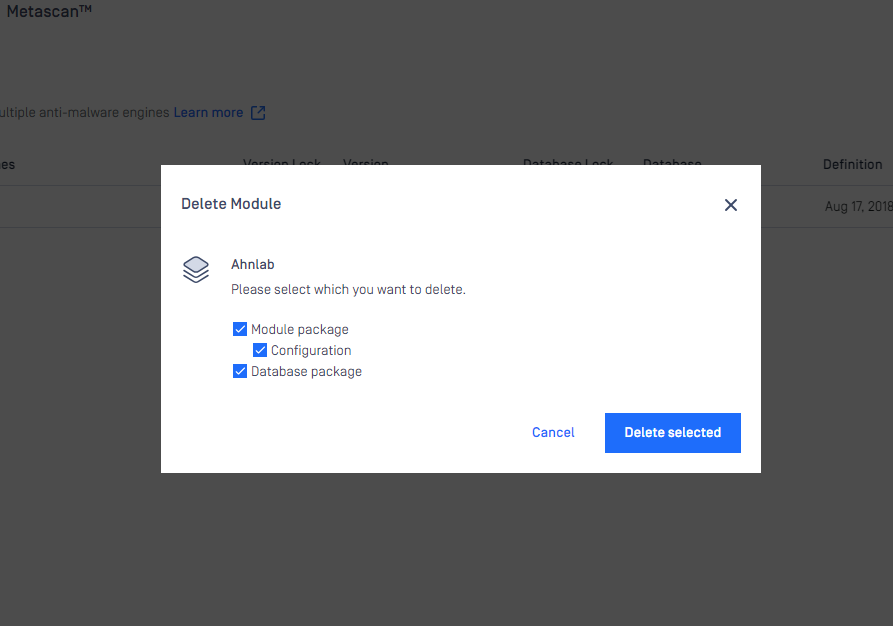
Remove engines (to start over engine download and deployment)
At some points, when engines become problematic and comes to the state of permanent failed, then you may need to remove engine.
Manual updates
To manually trigger update of scan engine and database packages, click on the Update now button.
To provide engine or database packages on your own, select the Upload package option.
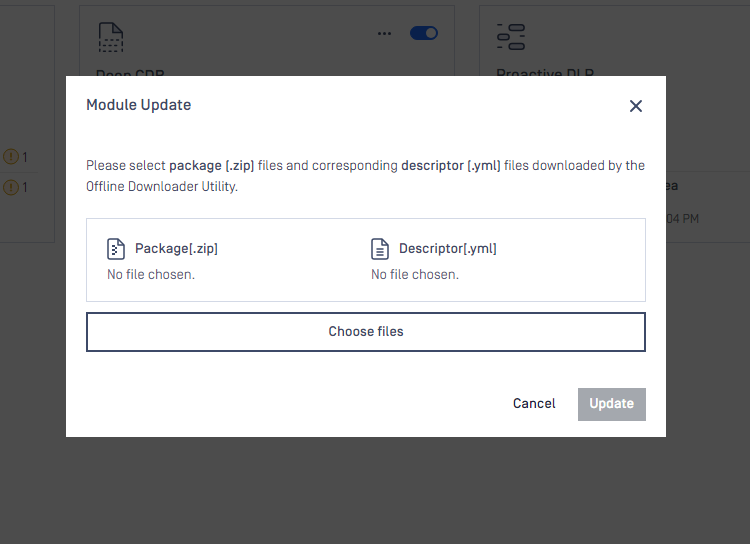
Upload packages
The package should be a ZIP and the descriptor YML file, which can be downloaded with the Update Downloader. Multiple files can be selected.
Engine or database versions that have ever been used on a system won't be accepted as updates.
YARA Rule Package Generation
MetaDefender Core supports generating YARA packages from two types of sources:
- HTTP source
- Local directory
To generate a YARA package:
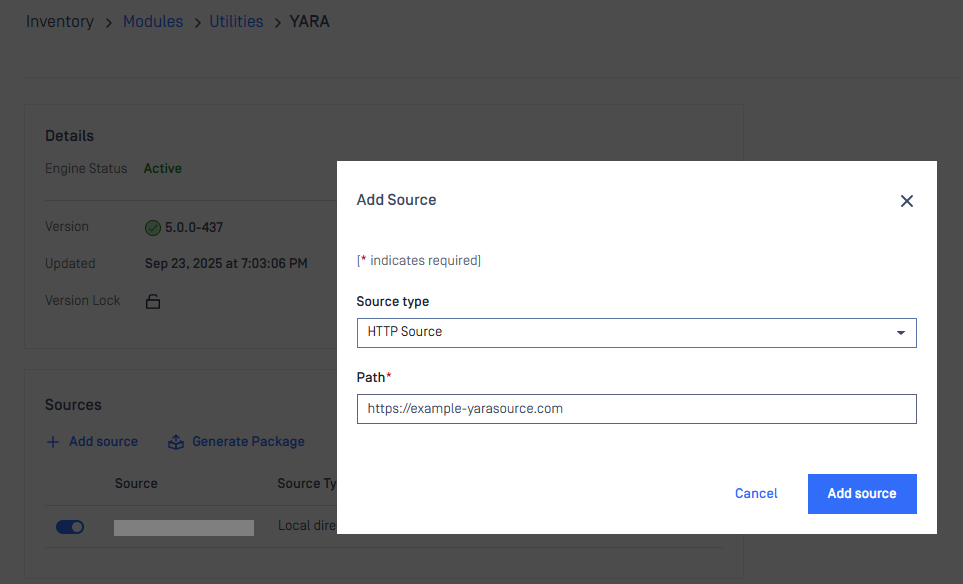
- Go to Inventory > Modules > Utilities > YARA.
- Click Add Source.
- Select the source type, enter the path, then click Add Source.
- Repeat step 3 if you need multiple sources.
- Click Generate Package.
You can also generate a YARA package via MD Core API endpoints: POST - Generate YARA packageAPI
For HTTP sources, to protect MD Core from several attack methods, YARA packages must meet certain constraints. Packages that violate these constraints are rejected. The required constraints include:
| Constraint | Limit | Description |
|---|---|---|
| Archive Size | 50 MB | Maximum size of the compressed YARA package file |
| File Entry Count | 1,000 files | Maximum number of individual files allowed within the archive |
| Nested Folder Depth | 50 levels | Maximum recursive depth for nested directories within the archive |
| File Path Length | 255 - engine DB path length | Maximum allowed path length for each file entry (calculated dynamically based on engine database folder location) |
| Extracted Content Size | 50 MB | Maximum total size of all files after extraction from the archive |
Configuring engine advanced settings
Some engines advanced settings can be configured.
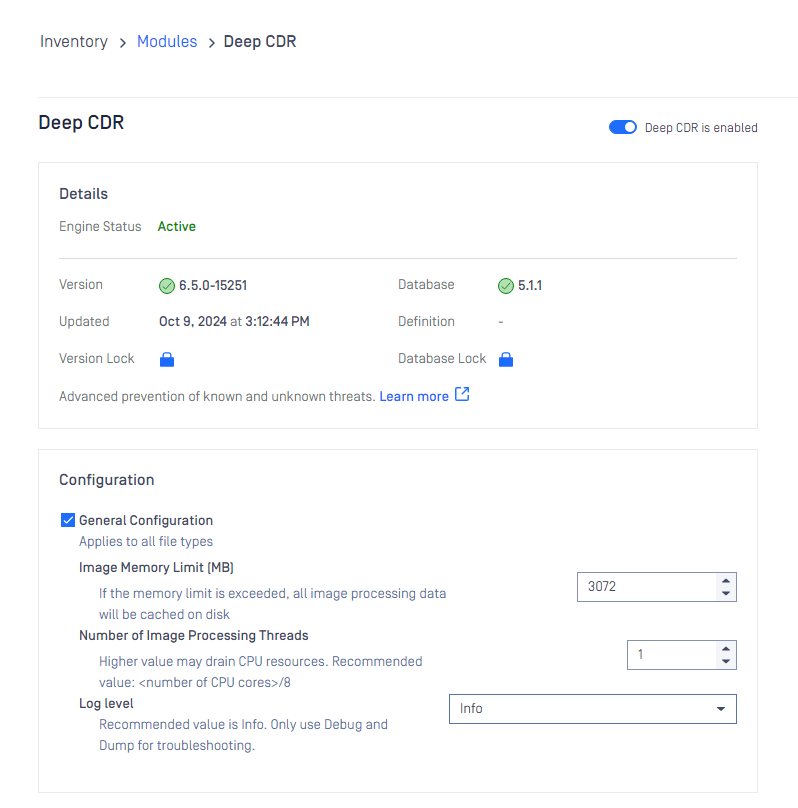
Choose your desired configurations and click Save changes, then Close.
Skip by hash
This page contains three lists which belong to similar but different features. Note that rules listed in these there features are globally applied, not per workflow.
Hash can be either MD5, SHA1, SHA256 or SHA512.
Skip engines
On this page, users can define rules on what files should be skipped by what engines. That is, a file with the given hash will not be processed by the listed engines.
Hash and at least one engine are mandatory to give, comment is optional.
Allowlist
Files whose hashes listed here will be globally allowlisted, so they won't be processed in any workflow and will be allowed.
Hash is mandatory to give, comment is optional.
Blocklist
Files whose hashes listed here will be globally blocklisted, so they won't be processed in any workflow and will be blocked.
Hash is mandatory to give, comment is optional.
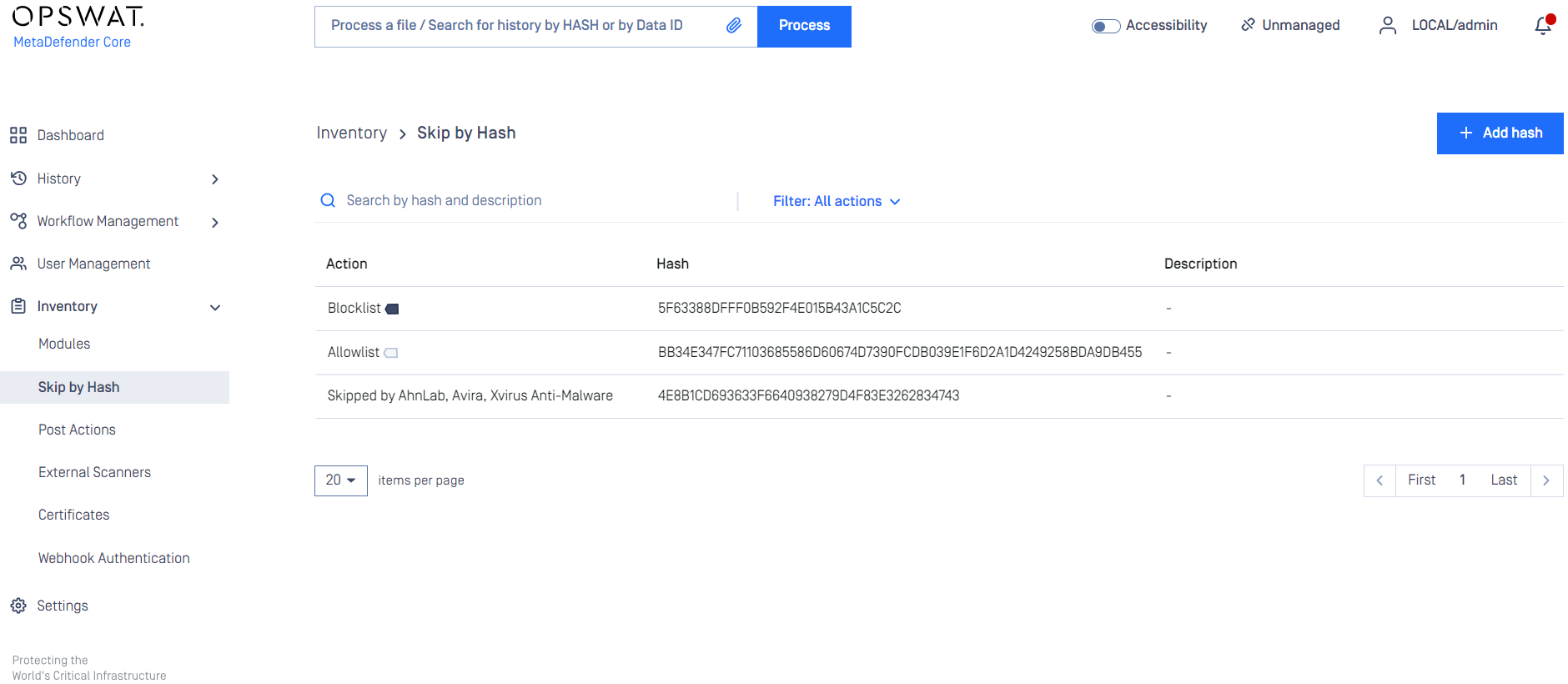
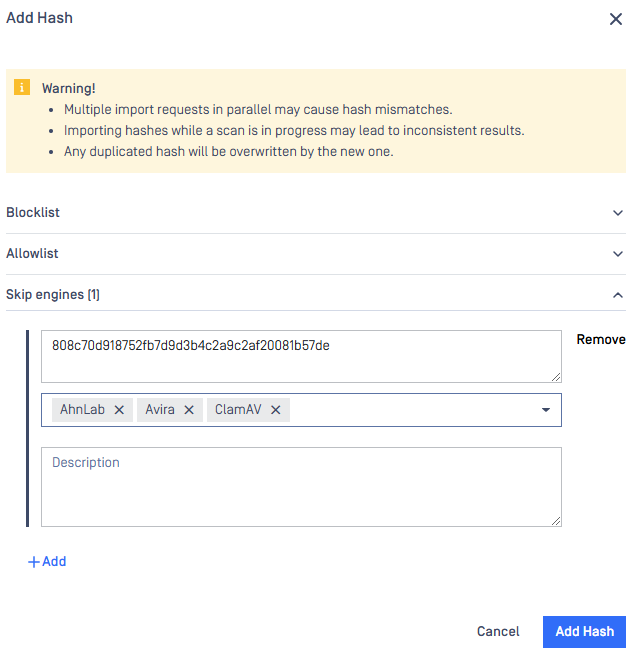
Adding a hash to skip list
On the Skip by Hash page click the "Add hash" button on the top right. There are 2 ways for Administrators to add hashes to the application.
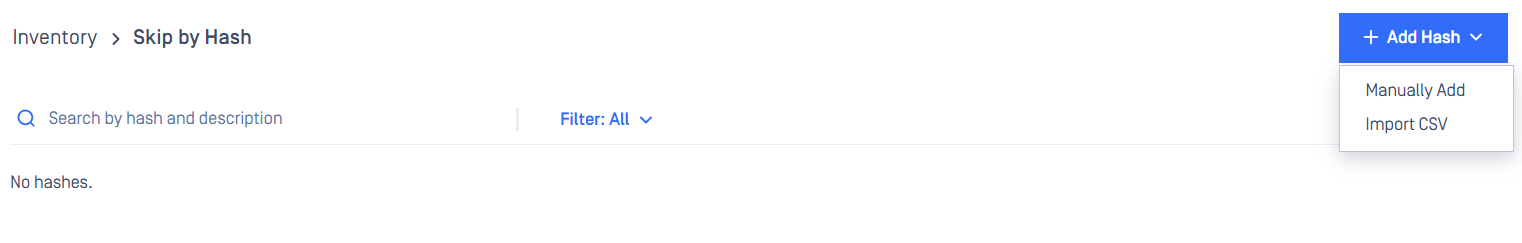
Manually Add:
- Allow you to input hashes and information manually.
Import CSV:
- Enable you to prepare a list of hashes and upload all at once to the application.
- A CSV template is downloadable for easy content input.
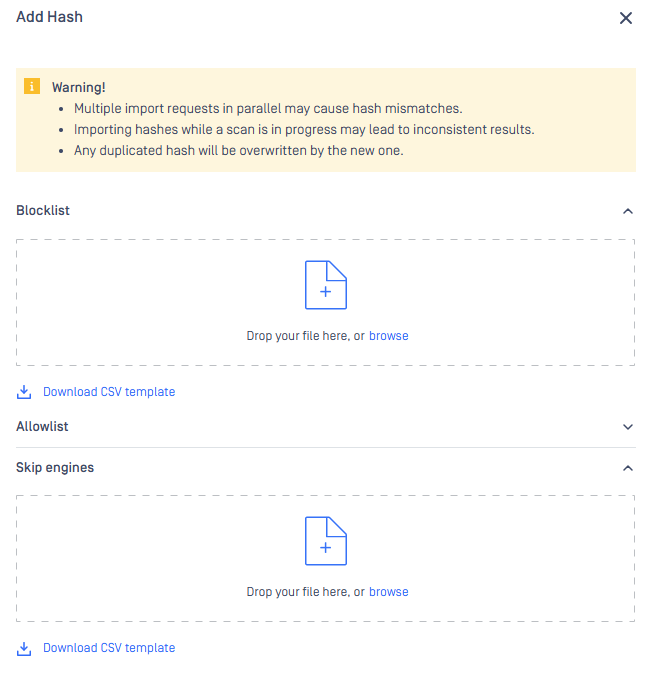
Select your desired way, then "Add hash" page appears.
After giving the necessary information, click on the Add button.
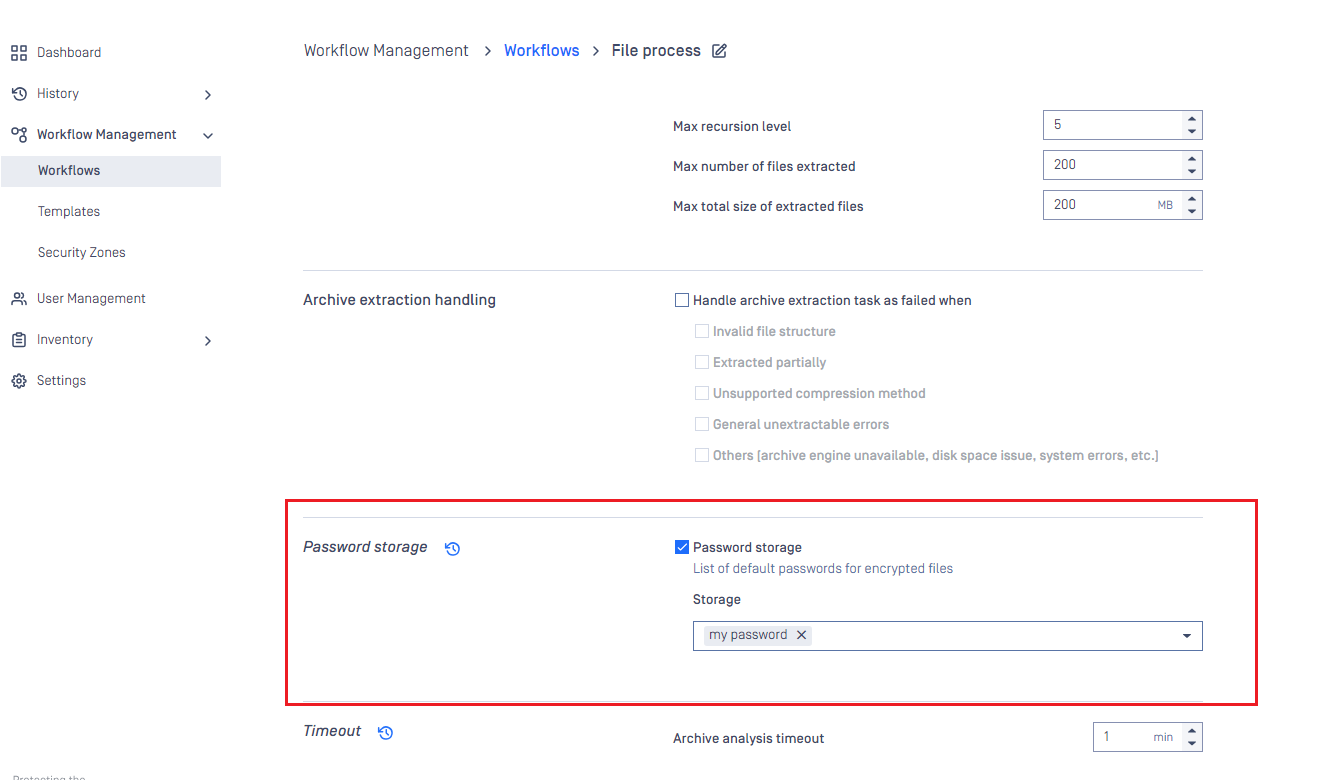
Password Storage
Users can define and manage lists of passwords used for file decryption, streamlining the process when handling encrypted or password-protected files.
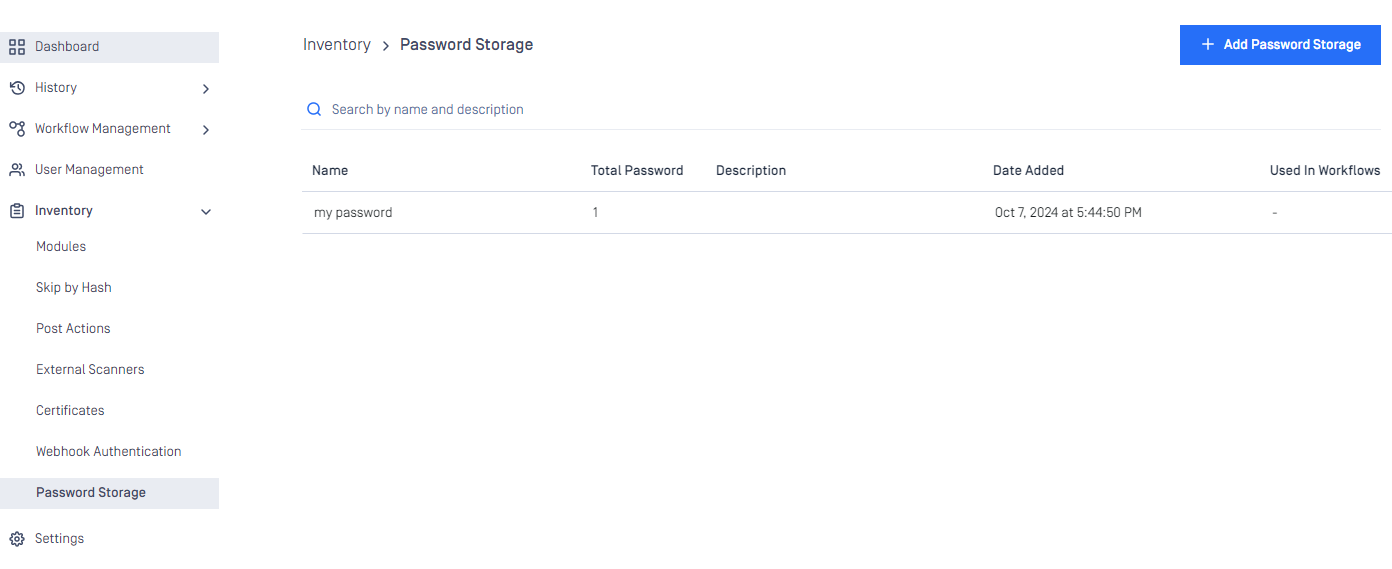
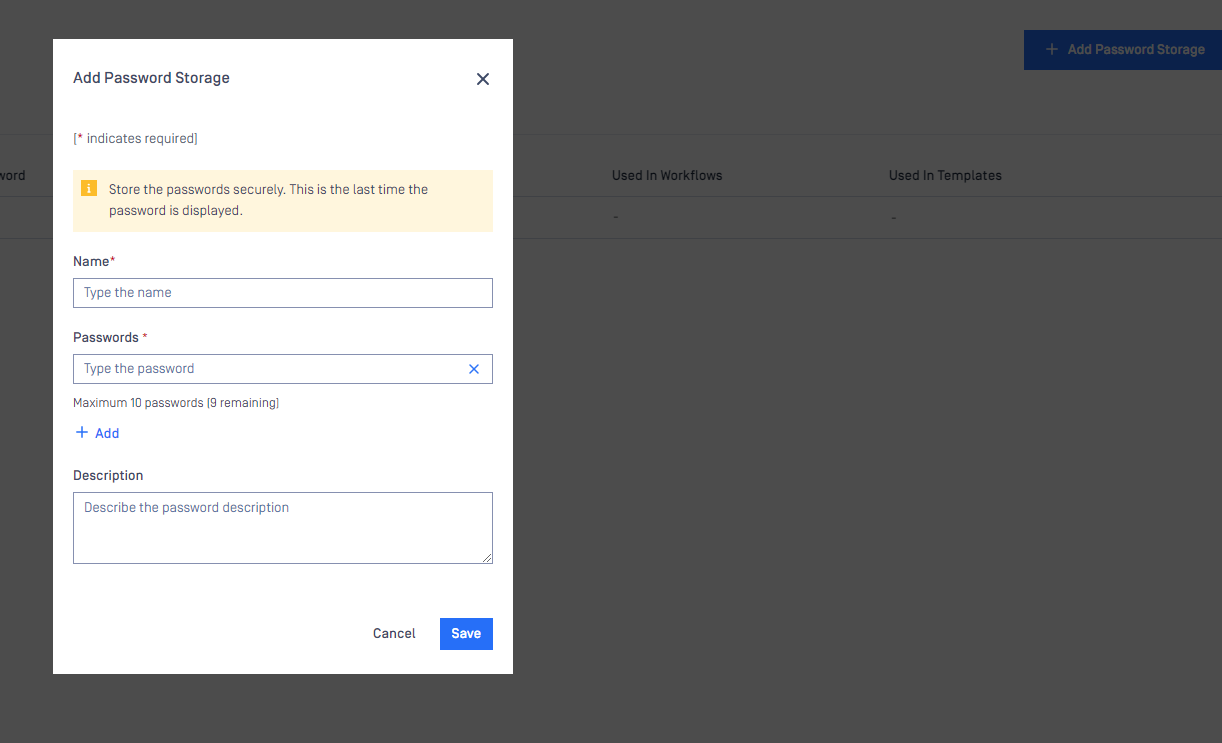
We can add up to 50 password storage and each password storage can contains up to 10 passwords
Click the button Add Password Storage for adding new password storage
We also can add more password in the list for later, click to any password storage to modify
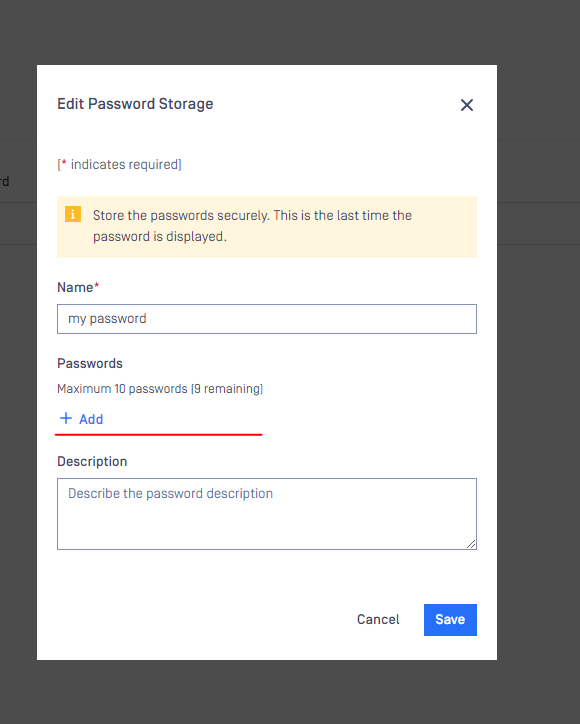
We can only add more password to the list, we cannot modify the old passwords or remove it from the list. To remove the password lists, we need remove the whole password storage.
After created the password storages, we need to go to workflow rule setting to select the password storages that we want to using for a specific workflow rule.
Workflow Management > Workflows > Select a workflow rule > Archive tab > Scroll down and check Password storage