Operating
v3.6.1
Search this version
Operating
Operating
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Threat Detection
Copy Markdown
Open in ChatGPT
Open in Claude
The Threat Detection is accessible under Policies → Asset Policies → Threat Detection.
The unauthorized asset page lists asset policies that are detection of duplication of a device’s identifiable property via network connections (e.g., MAC, IP, hostname) in network connections to identify spoofed or cloned devices, and network attacks.
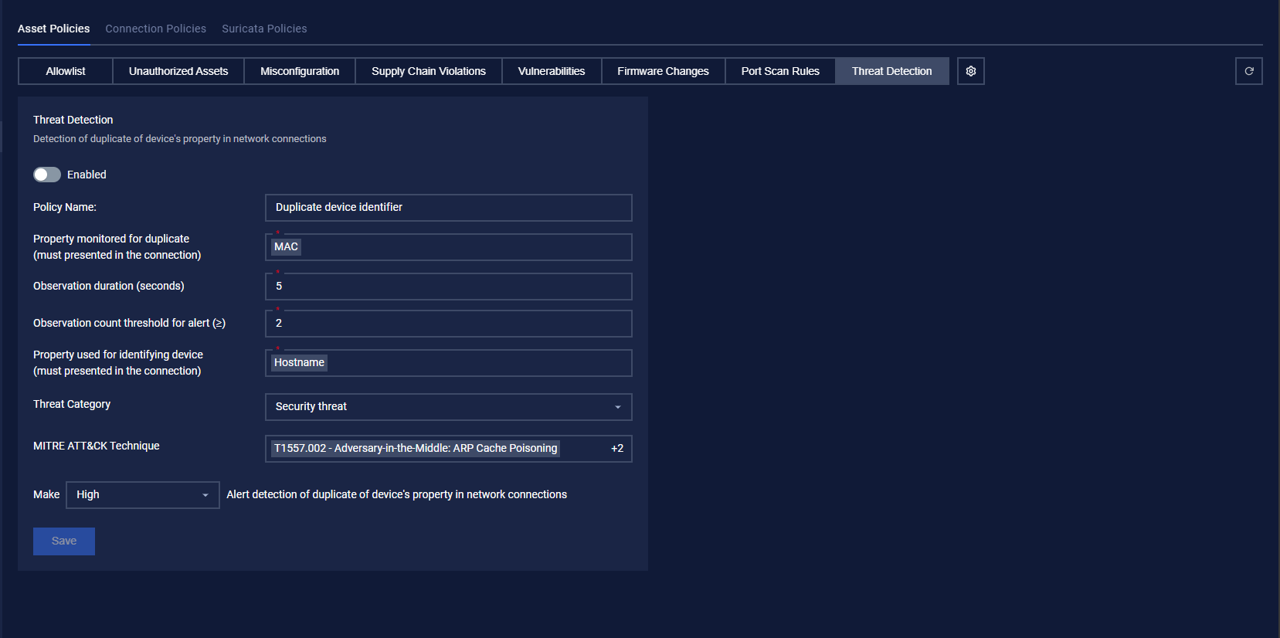
Actions on Threat Detection
1. View policy
Policies are displayed following the information:
- Policy Name
- Property monitored for duplicate (must be presented in the connection): MAC
- Observation duration (seconds)
- Observation count threshold for alert (≥)
- Property used for identifying device (must presented in the connection): Hostname
- Threat Category: Security threat
- MITRE ATT&CK Technique
- Criticality: Alert level (low/high/medium/critical).
2. Edit policy
You can edit a policy
You can see the detailed policy. You can edit by clicking on the field to be edited and performing input operations.
When finished editing, click “Save” to save the changes or “Cancel” to discard all.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Connection PoliciesDiscard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

