Title
Create new category
Edit page index title
Edit category
Edit link
OKTA - SAML Integration
MetaDefender ICAP Server has already tested and verified with following IDP for both SAML and OIDC integrations:
- OKTA
- AZure
- One Login
- Ping Identity
In this article, we selected OKTA (https://www.okta.com/) as a supported IDP to demonstrate OIDC and SAML integration with MetaDefender ICAP Server.
SAML Connect Integration
Create a new application on the IDP site for MetaDefender ICAP
- Sign in Okta site
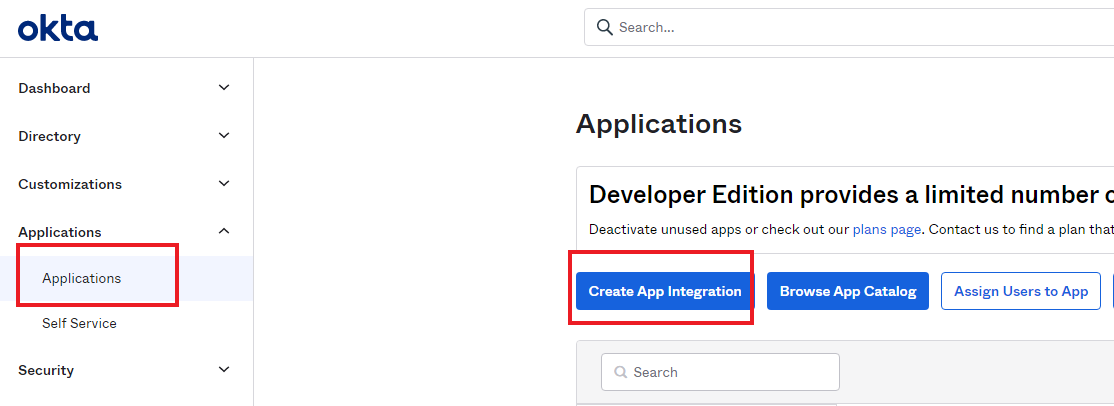
- Add an application, select “Web” application type, and choose “SAML 2.0” for Sign on method
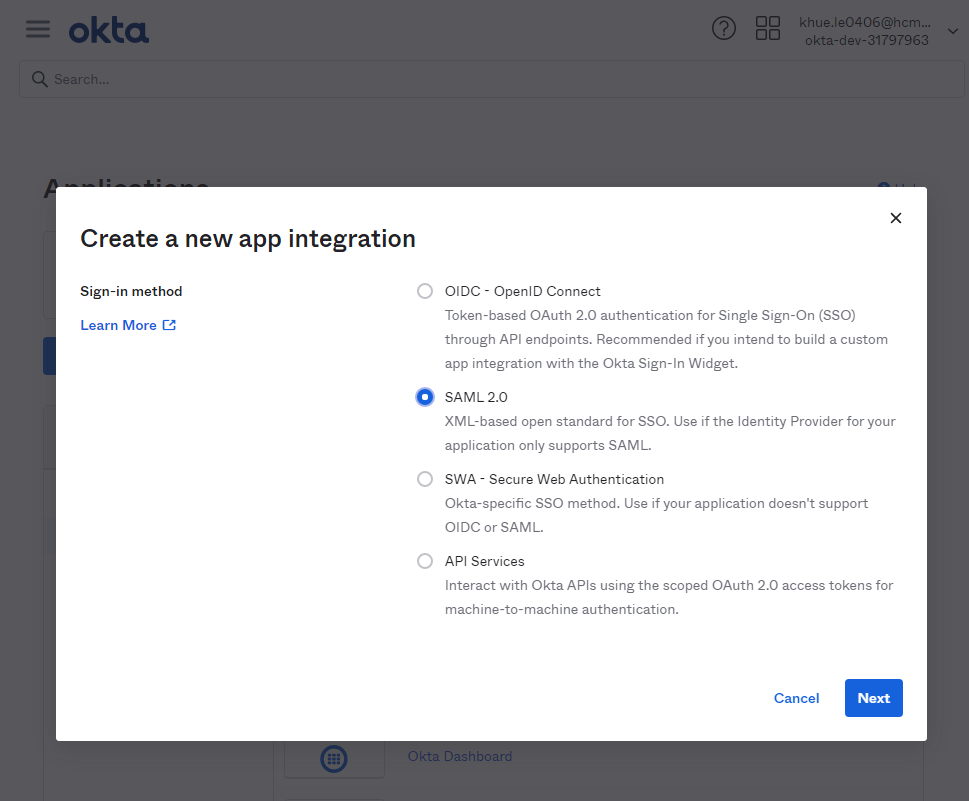
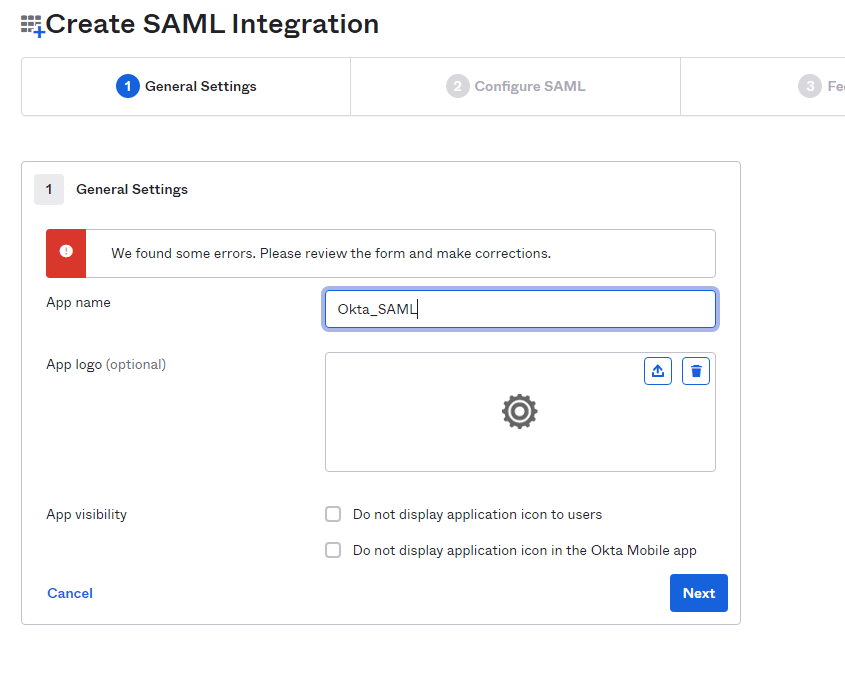
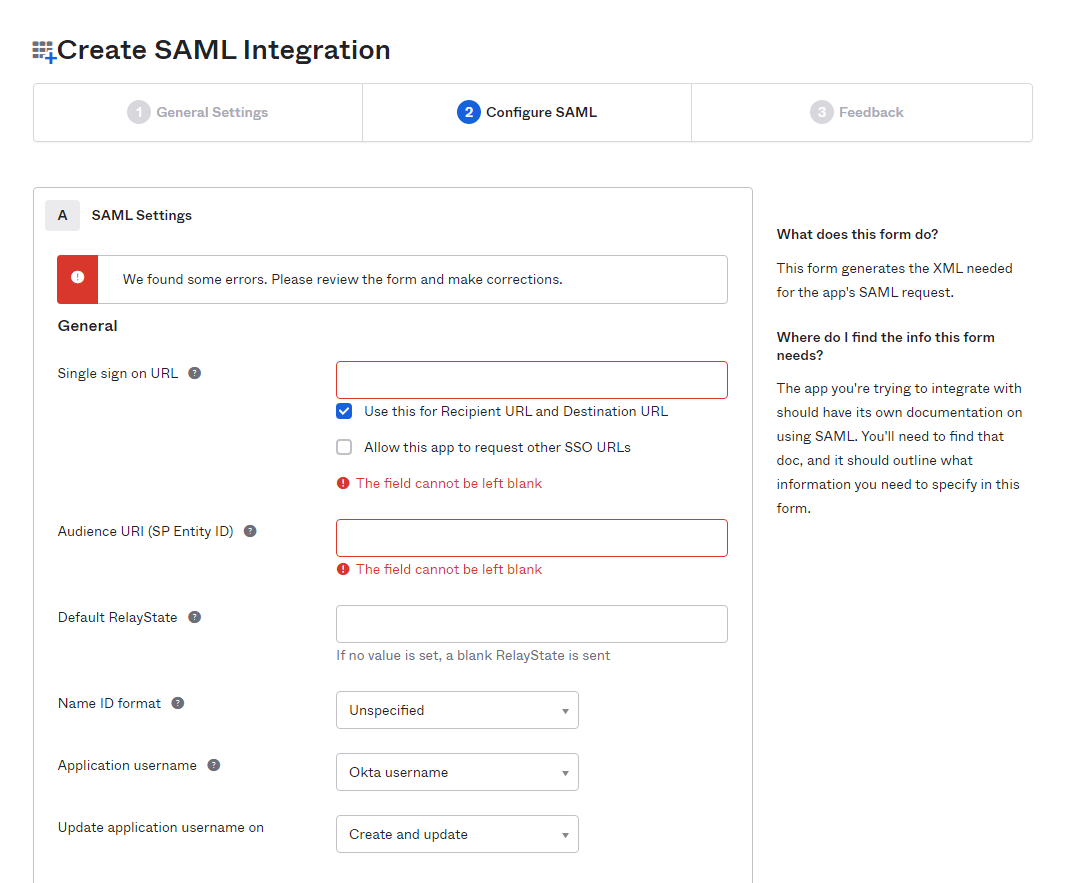
Proceeding to the “Configure SAML” step on SAML integration configuration, and filling these required fields by any valid value, we need to generate some data from the MetaDefender ICAP management console before getting back to this page later.
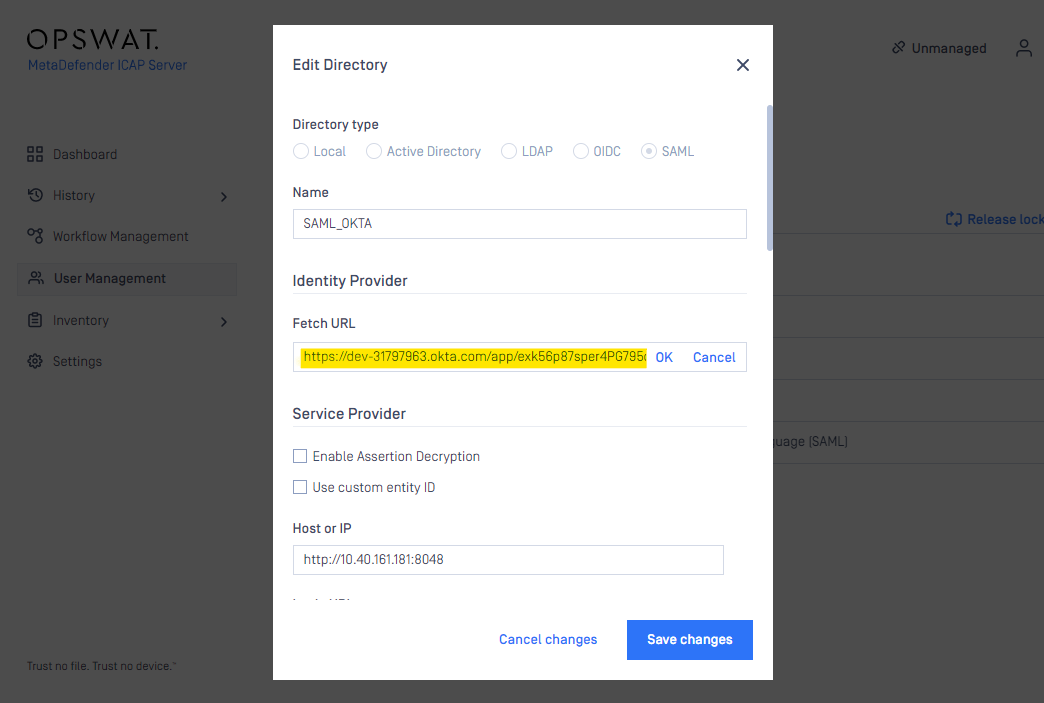
- On the MetaDefender ICAP management console, create a new user directory for SSO
- Navigate to Settings > User Management
- On “USER DIRECTORIES” tab, hit “ADD NEW USER DIRECTORY” button
- Choose “Security Assertion Markup Language (SAML)” option for “USER DIRECTORY TYPE”
- Type the directory name of your choice
- In “IDENTIFY PROVIDER” section, hit “FETCH” button to input IDP’s SAML designated metadata API URL (e.g. Okta could be found at Enterprise Identity Provider | Okta Developer )
- In “SERVICE PROVIDER” section:
- On MetaDefender Console current display, type your MetaDefender ICAP address in “HOST OR IP” field
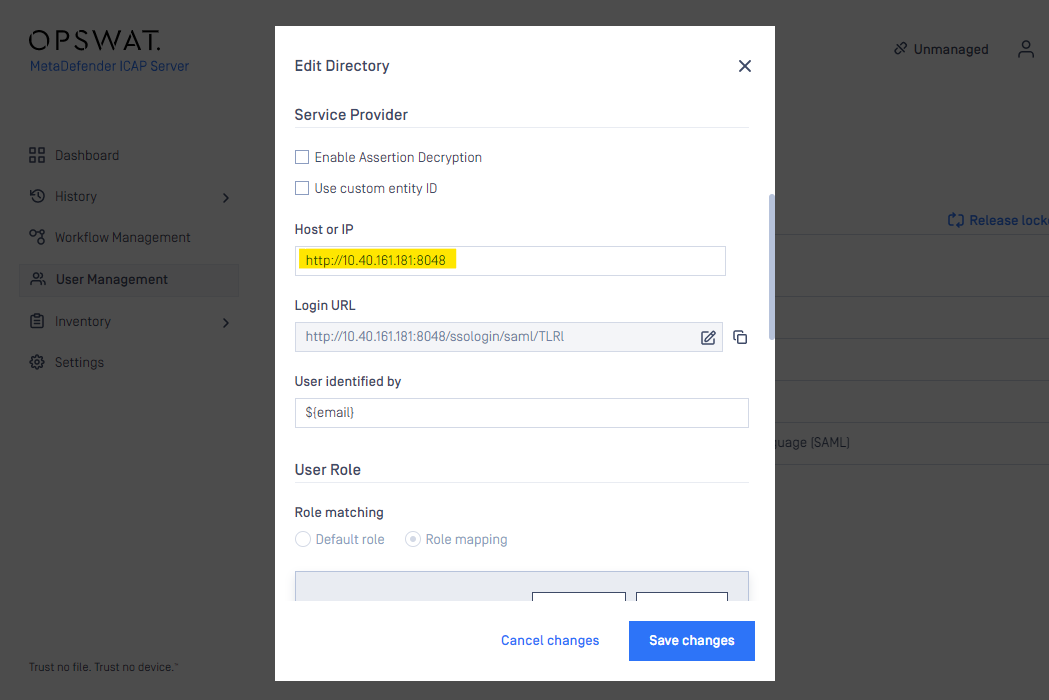
and a login redirect URL will be auto-generated by MetaDefender ICAP, you will want to copy the full link to proceed:
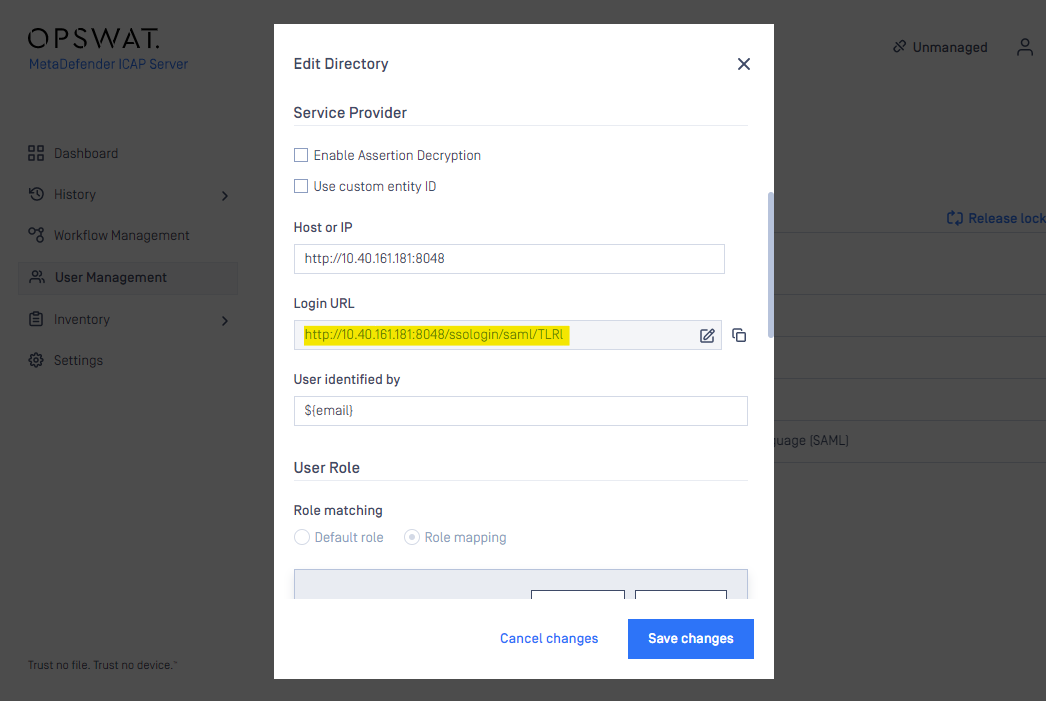
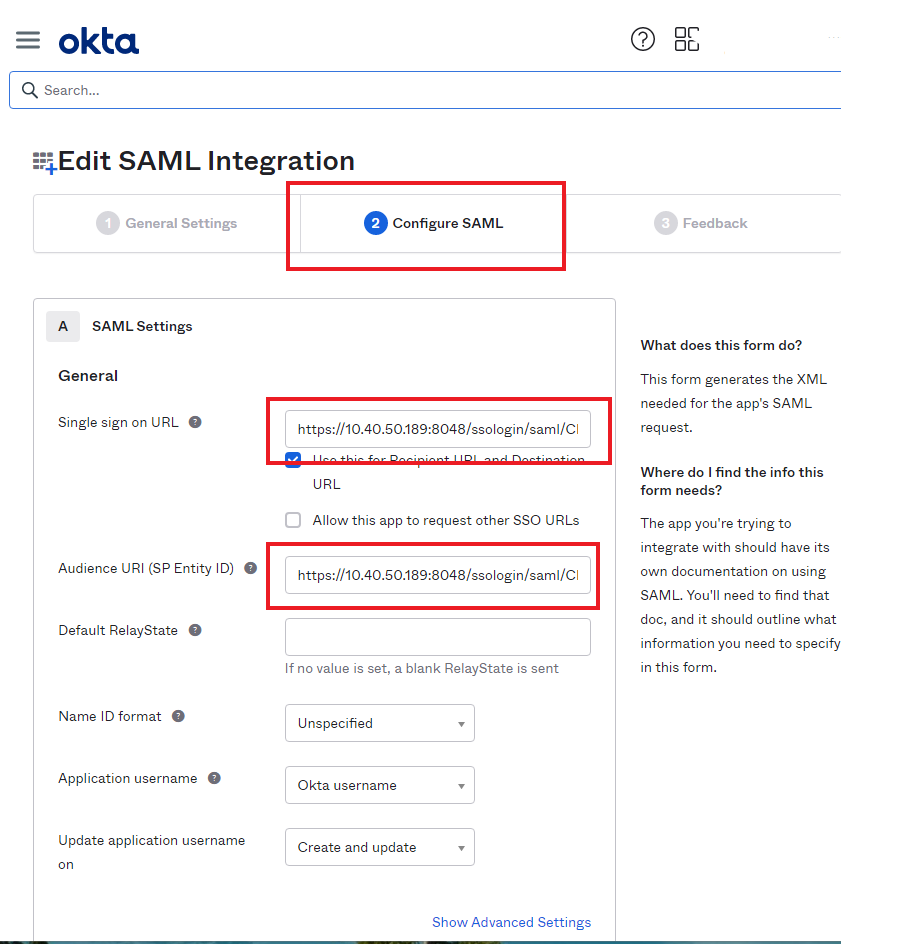
- Switching to Okta IDP console, paste the single sign-on URL and also input Audience URI, check “Use this for Recipient URL and Destination URL” option
- “USER IDENTIFIED BY” field:
- Username can be constructed by attributes set by IDP, or
- Defined by the customer on the IDP site
Please review the IDP document for more details. For example, for Okta: https://help.okta.com/en/prod/Content/Topics/Apps/Apps_App_Integration_Wizard_SAML.htm
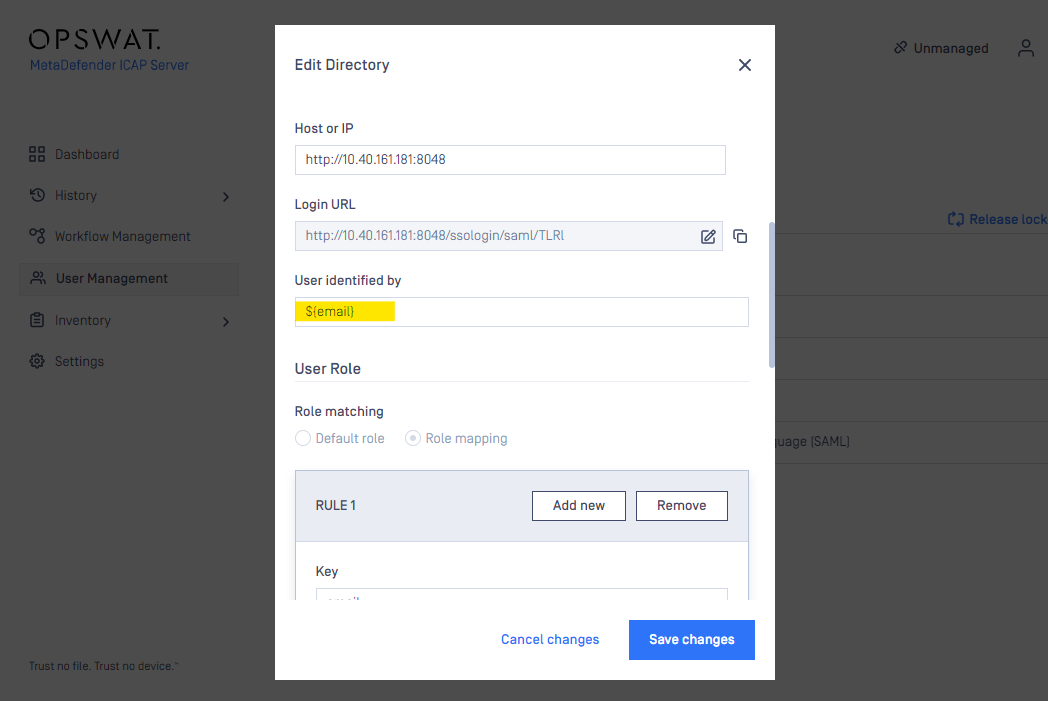
- In “USER ROLE” section
you are supported to choose the default role to map an existing MetaDefender ICAP local role
Or create a custom role mapping based on RegEx:
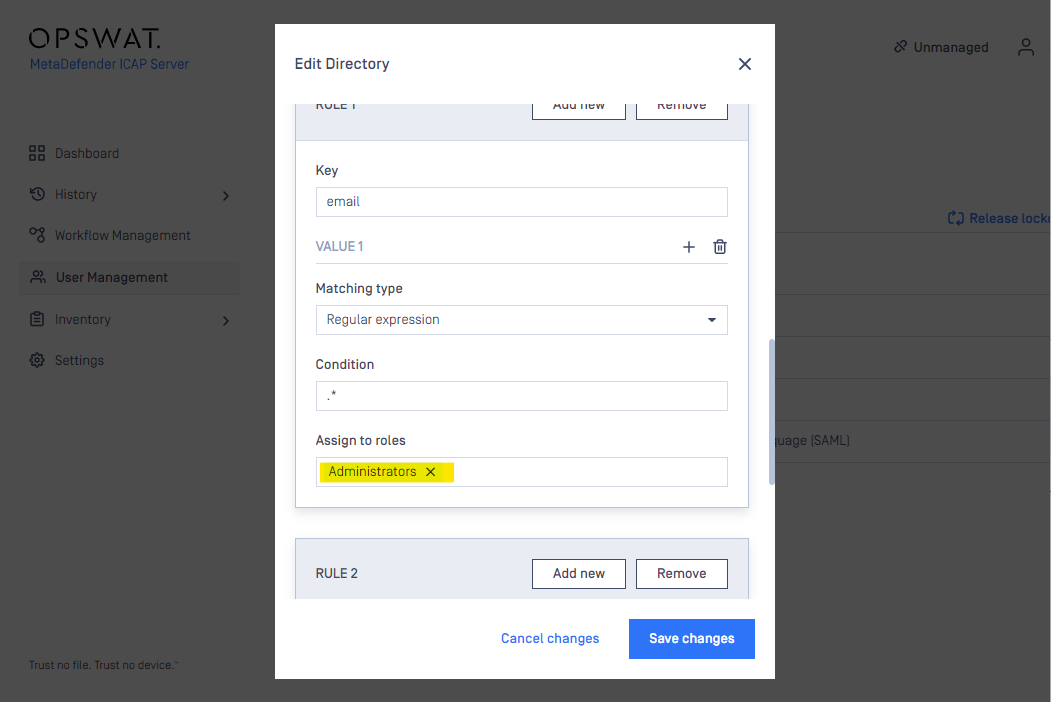
- Hit “ADD” button to finish creating a new SSO user directory, by default the newly created user directory is disabled:
- You may want to enable it for SSO login fashion
- Result
Logged in successfully will help you be redirected back to the MetaDefender ICAP Server management console.