Configuration
v5.12.0
Search this version
Configuration
Configuration
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
OKTA - OpenID Connect Integration
Copy Markdown
Open in ChatGPT
Open in Claude
MetaDefender ICAP Server has already tested and verified with following IDP for both SAML and OIDC integrations:
- OKTA
- AZure
- One Login
- Ping Identity
In this article, we selected OKTA (https://www.okta.com/) as a supported IDP to demonstrate OIDC and SAML integration with MetaDefender ICAP Server.
OpenID Connect Integration
Create a new application on the IDP site for MetaDefender ICAP Server
- Sign in Okta site Okta Developer

- Add an application, select “Web” application type, and choose “OpenID Connect” for Sign on method

- Make sure the newly created application is in ACTIVE list (e.g. Okta_OpenId)

- Access the newly created application (e.g. Okta_OpenId), navigate to the “General” tab, and create a new secret if not exist:
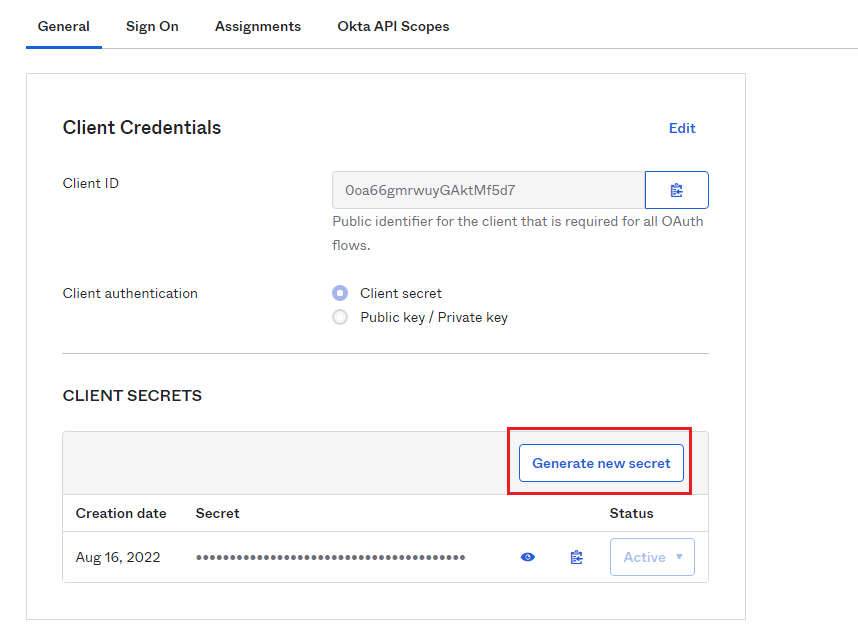
- On the MetaDefender ICAP Server management console, create a new user directory for SSO
- Navigate to Settings > User Management
- On “USER DIRECTORIES” tab, hit “ADD NEW USER DIRECTORY” button
- Choose “OpenID Connect (OIDC)” option for “USER DIRECTORY TYPE”
- Type the directory name of your choice
- In “IDENTIFY PROVIDER” section, hit “FETCH” button to input IDP’s designated metadata API URL (e.g. Okta could be found at OpenID Connect & OAuth 2.0 API | Okta Developer )

- When we successfully fetch, Scope default will be selected is OPENID
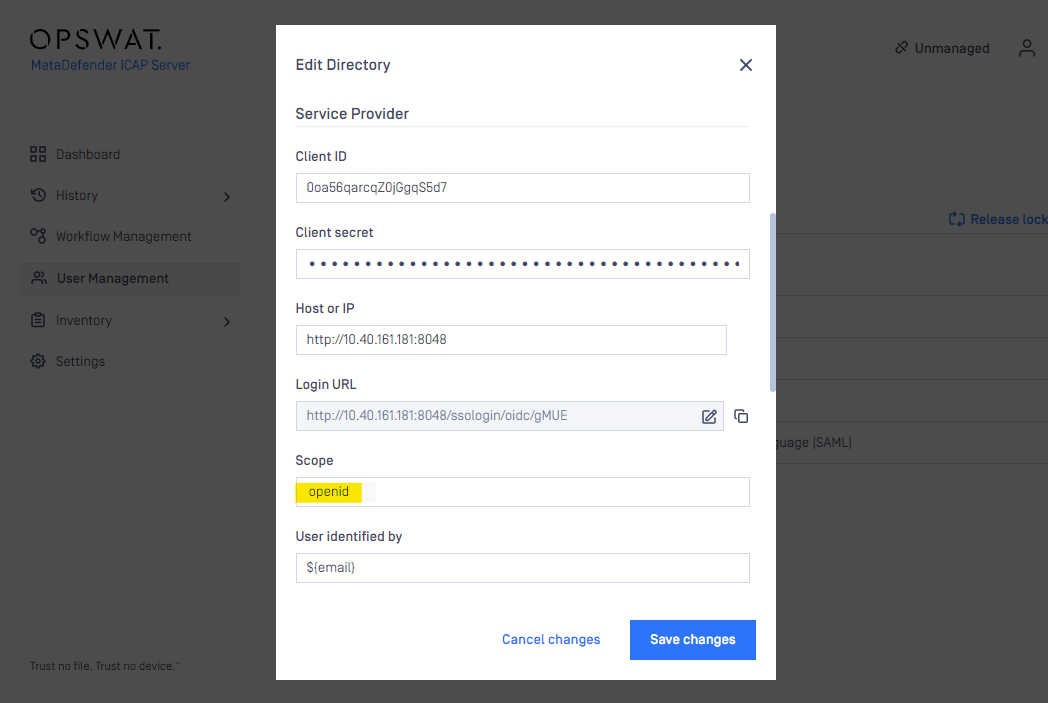
- In “SERVICE PROVIDER” section:
- Fill up “Client ID” and “Client Secret” matched to what generated in the IDP console:

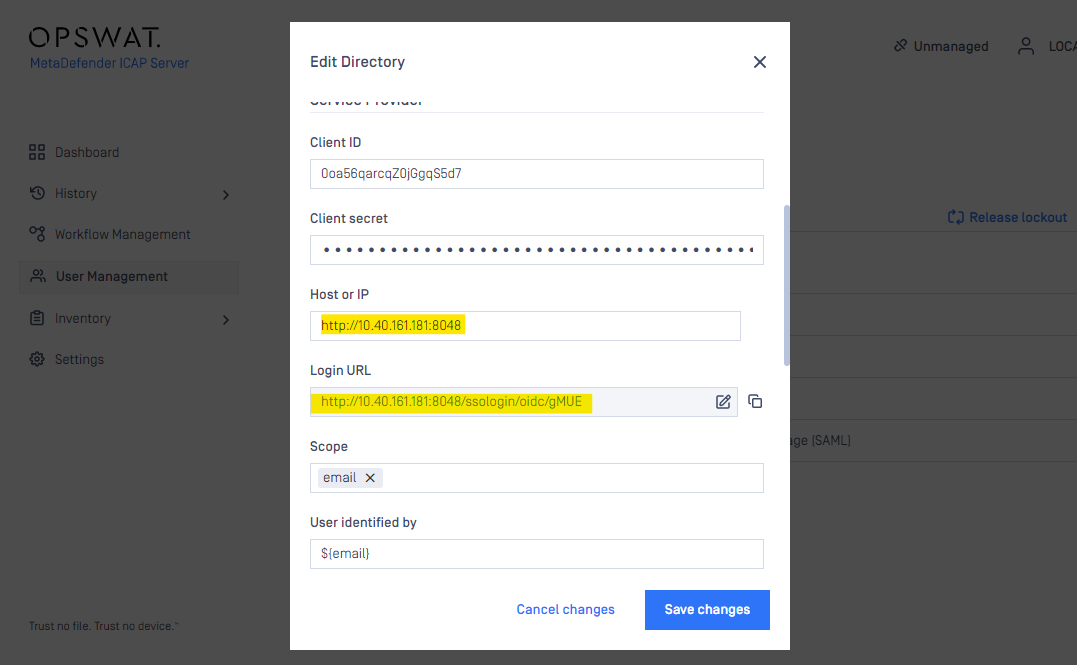
- On MetaDefender ICAP Server management console current display, type your MetaDefender ICAP address in “HOST OR IP” field
- and a login redirect URL will be auto-generated by MetaDefender ICAP, you will want to copy the full link to proceed
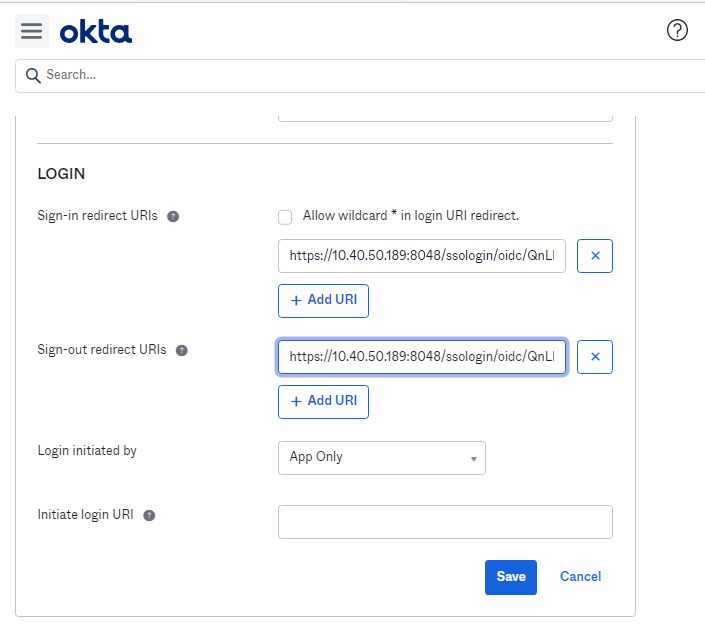
- Switching to the Okta IDP console, paste the login redirect URL and also input the Initiate login URI
- In “SCOPE” field:
- Able to select when fetching metadata above successfully.
- OpenID is the default scope.
- Select the scope that you will use claims in other fields ( USER IDENTIFIED BY and Role Mapping). Scope supported in Okta OpenID Connect & OAuth 2.0 API | Okta Developer

- In “USER IDENTIFIED BY” field:
- Username can be constructed by claims under email scope
- The claim variable is specified by syntax ${<claim-name>}
__ __
Notes: Supported claims under email scope are IDP specified. Please review the IDP document for more details.
For example: for OKTA (Identity, Claims, & Tokens – An OpenID Connect Primer, Part 1 of 3)
- “USER IDENTIFIED BY” field: Username can be constructed by claims under profile scope.
- The claim variable is specified by syntax ${<claim-name>}
Notes: Supported claims under profile scope are IDP specified. Please review the IDP document for more details.
For example, for OKTA (https://developer.okta.com/blog/2017/07/25/oidc-primer-part-1)
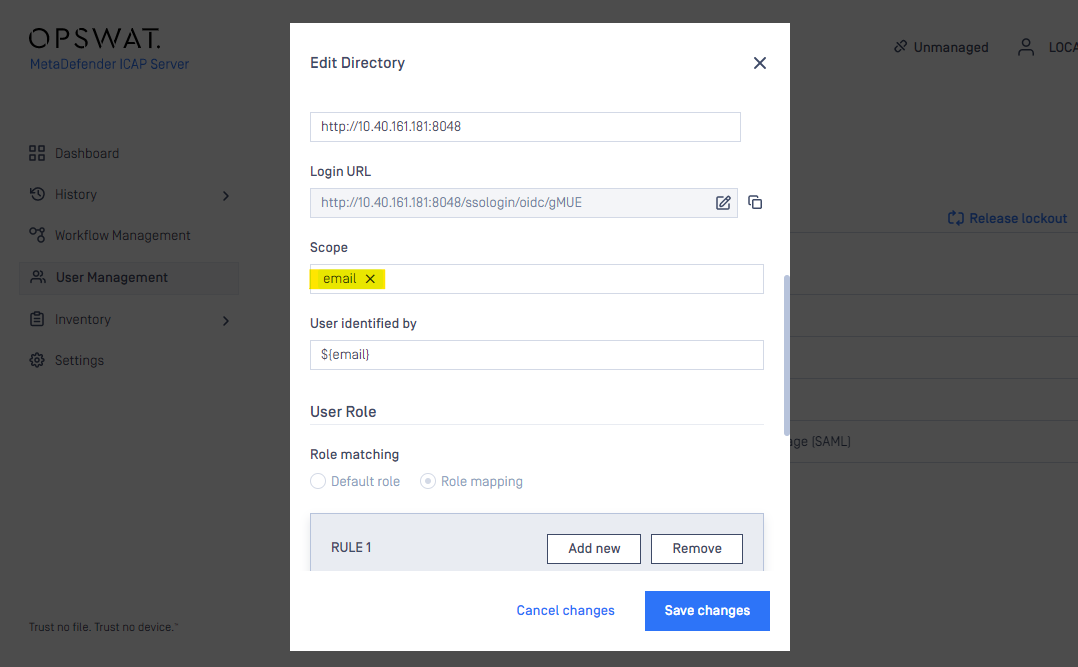
- In “USER ROLE” section, choose the default role to map an existing MetaDefender ICAP Server local role:
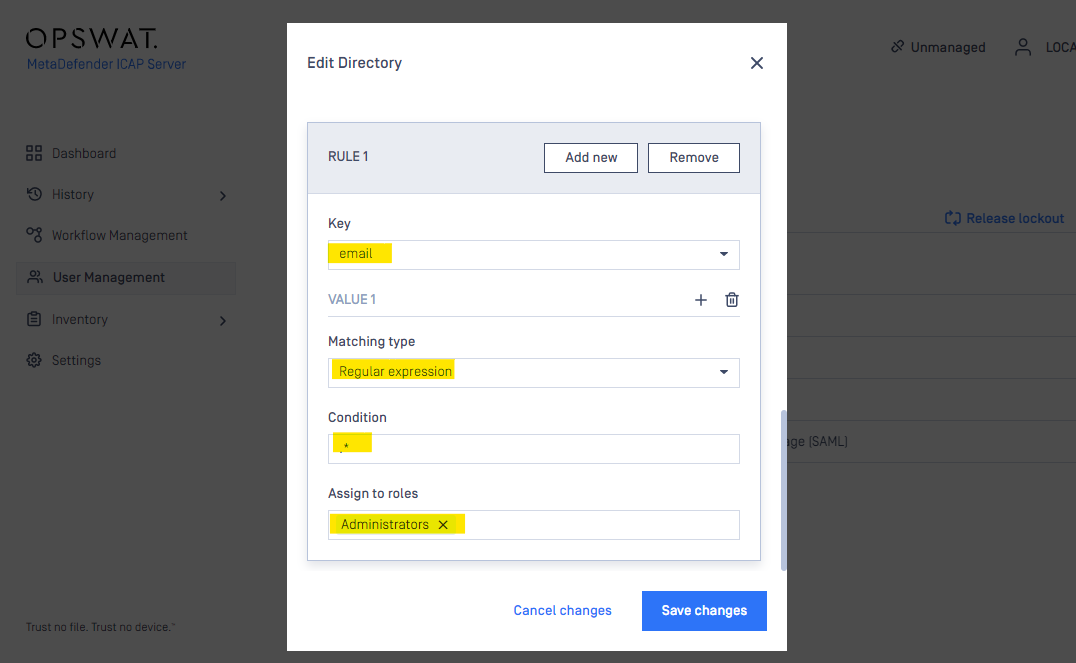
- Or create a custom role mapping based on RegEx:
- Hit “ADD” button to finish creating a new SSO user directory, by default the newly created user directory is disabled:
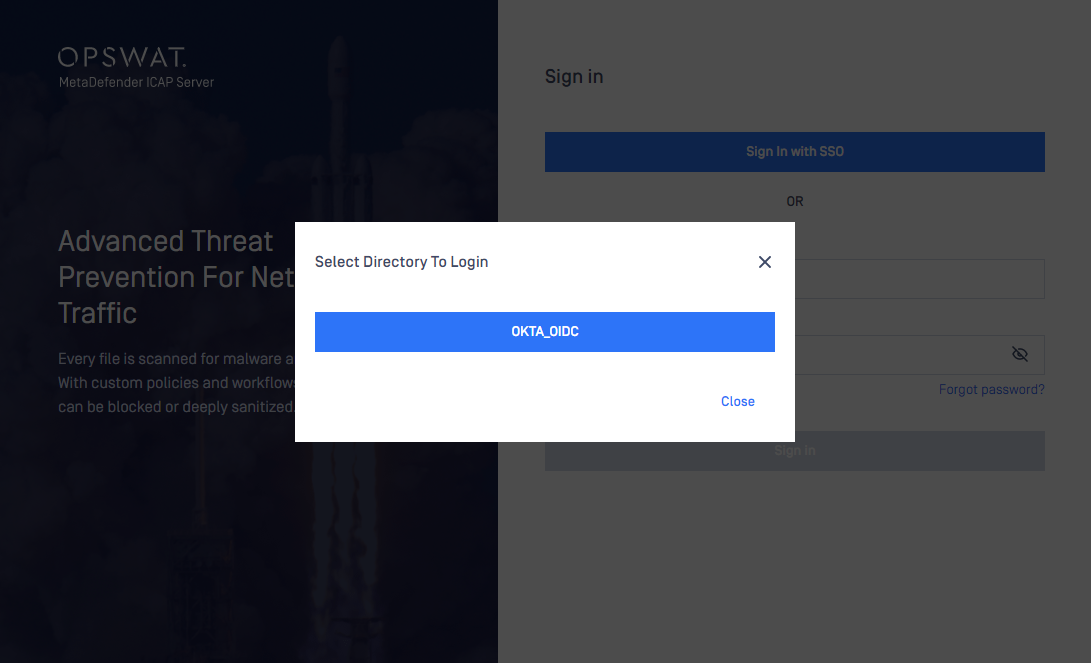
- Result Sign on using IDP authentication
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on Oct 10, 2022
Was this page helpful?
Next to read:
Configure OIDC SSO - Ping IdetityDiscard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

