Title
Create new category
Edit page index title
Edit category
Edit link
Ruckus-Integration Document
Scenario: wireless device access to SSID which configured 802.1X authentication method. After authentication, client device will be transferred to compliant vlan (or ACL). Basic configuration is below:
- AAA Server Profile
- WLAN Profile
- Configure NAC to return vlan to client (or ACL)
1- Secure Wireless
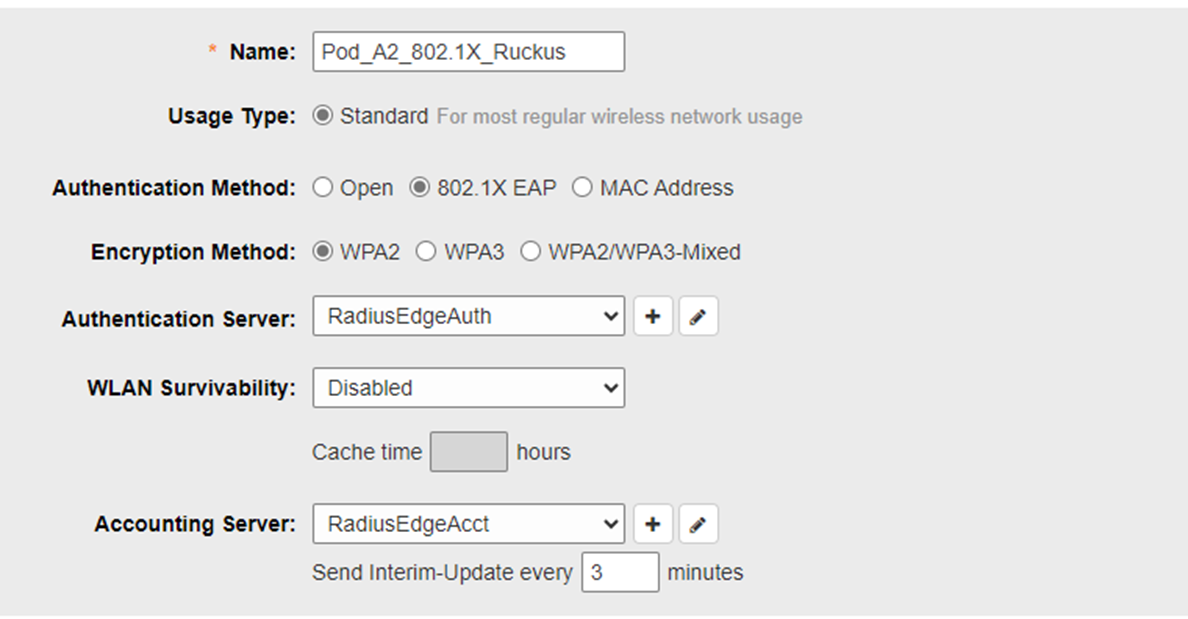
1.1 - AAA Server Profile
Click on Services -> AAA Servers. Create Authentication and Accounting Server
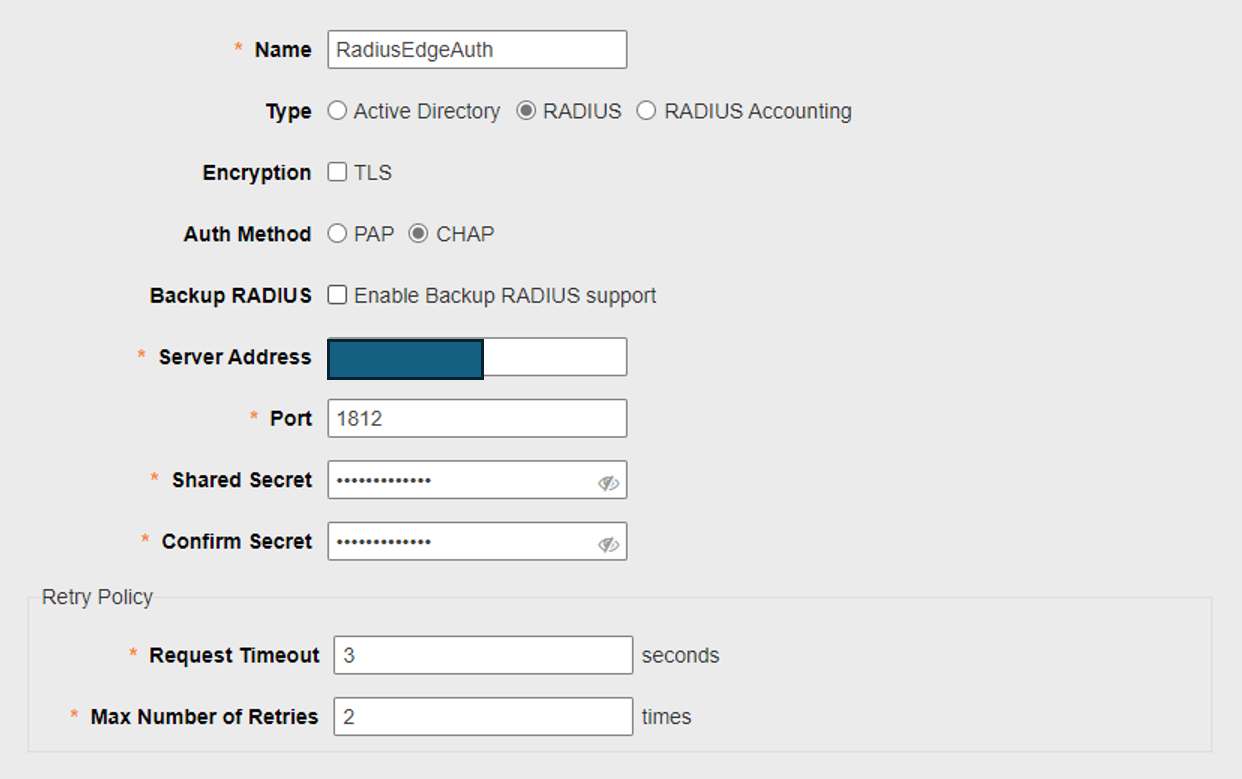
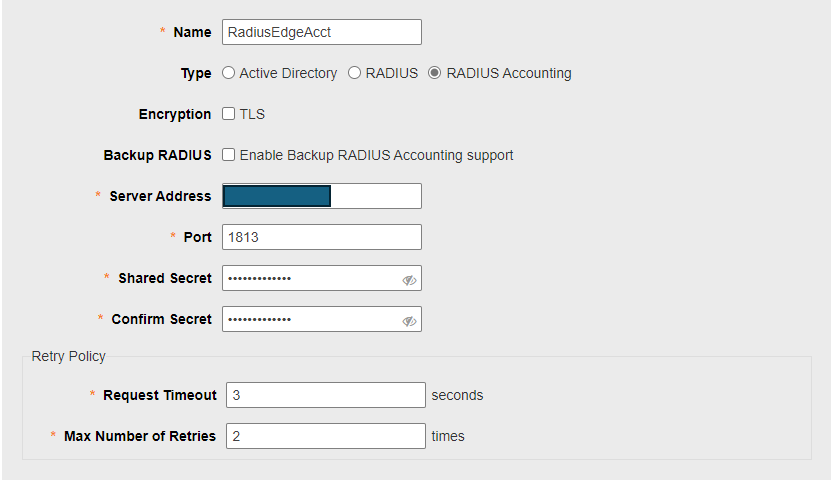
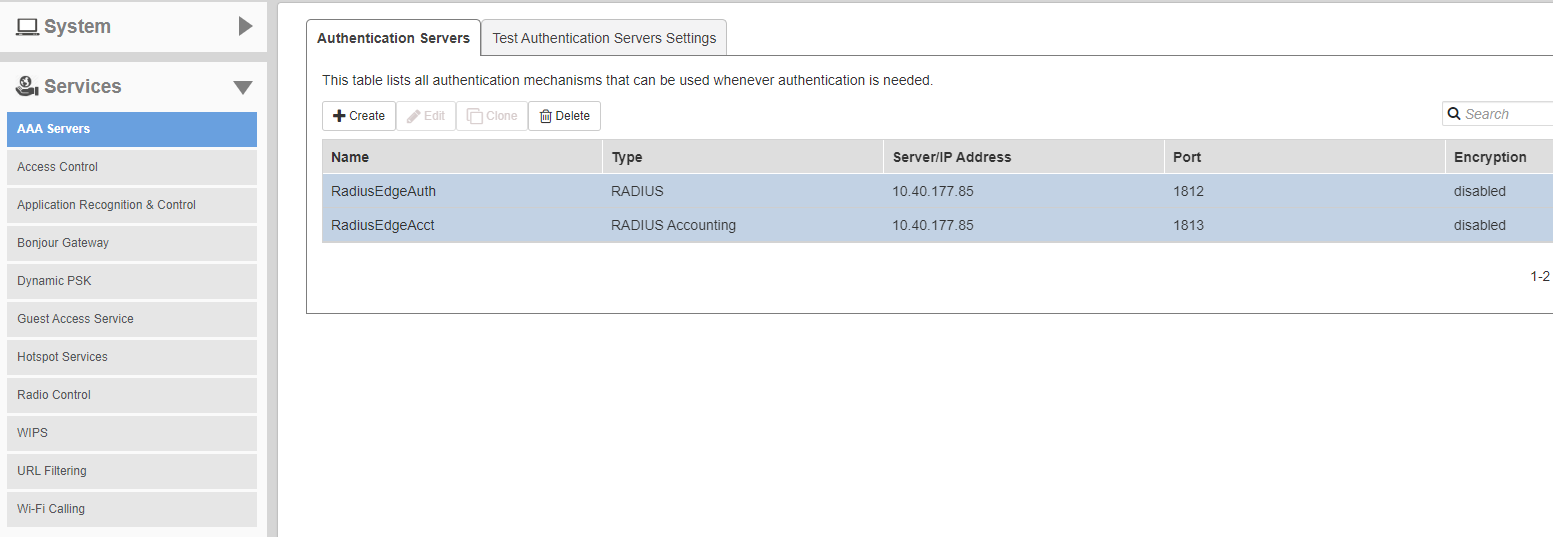
###
1.2 - WLAN Profile
Click on Wi-Fi Networks and click on Create
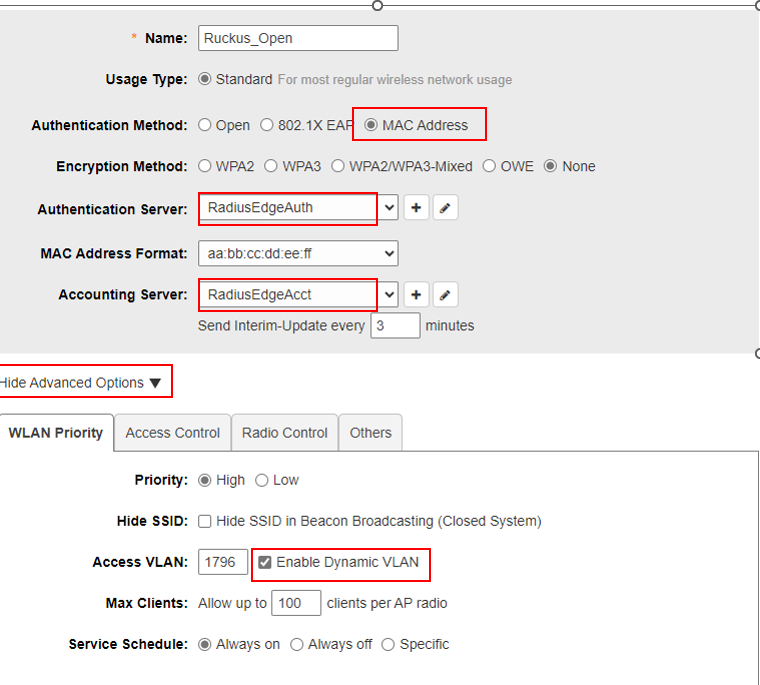
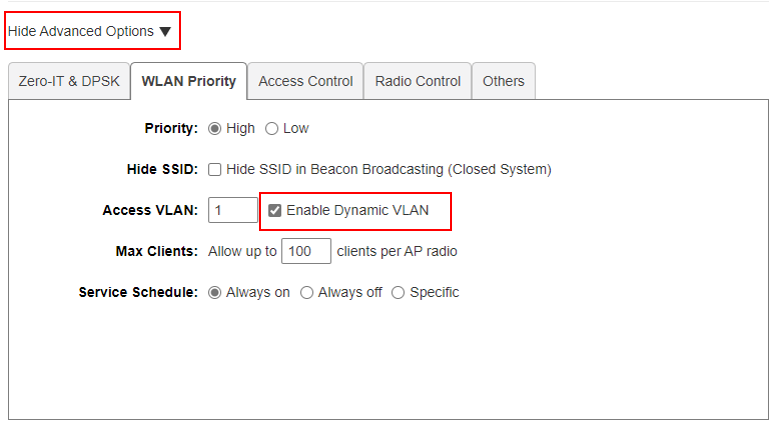
Click Hide Advanced Options to show more configuration and stick Enable Dynamic VLAN
1.3 - Configure NAC to return vlan to client
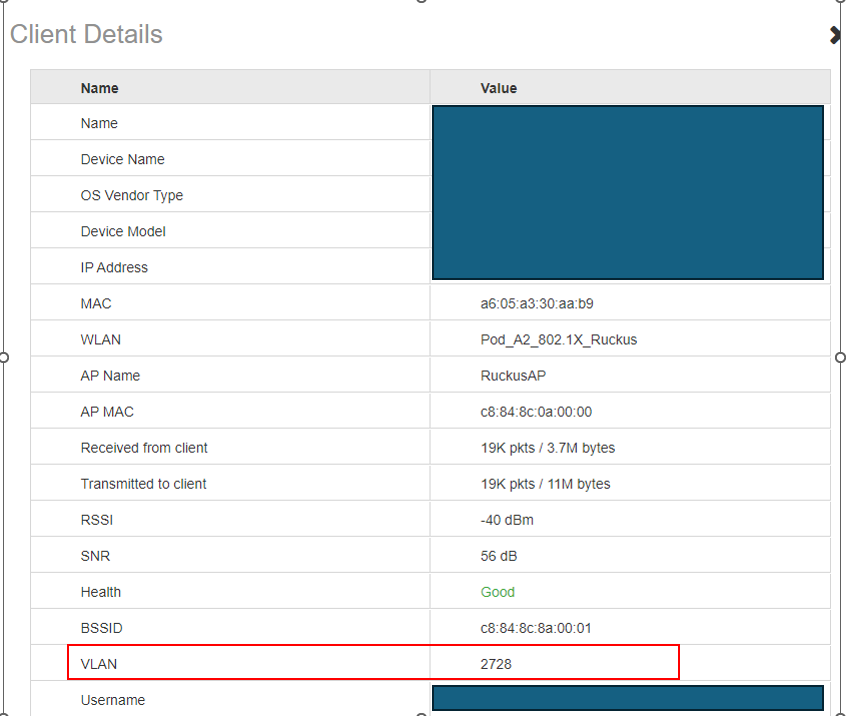
In this scenario, we will return vlan 2728 to this client
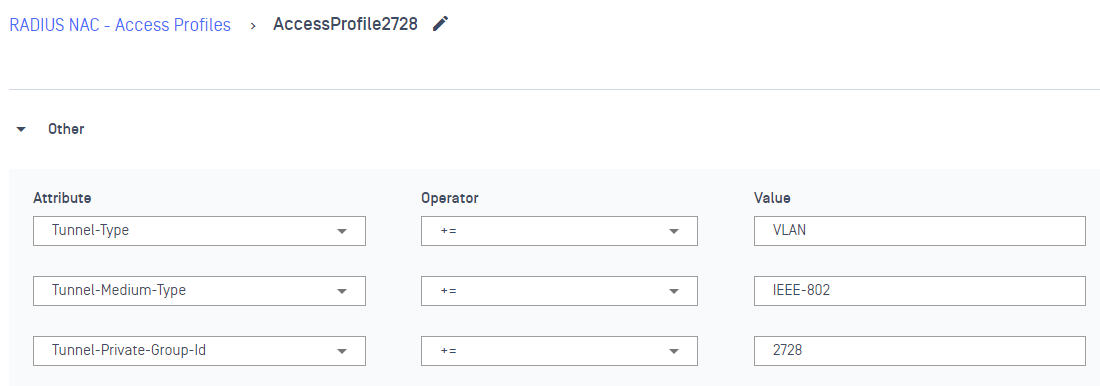
In case we want to return ACL, we can use Filter-ID := "Name of ACL" which predefined in AP
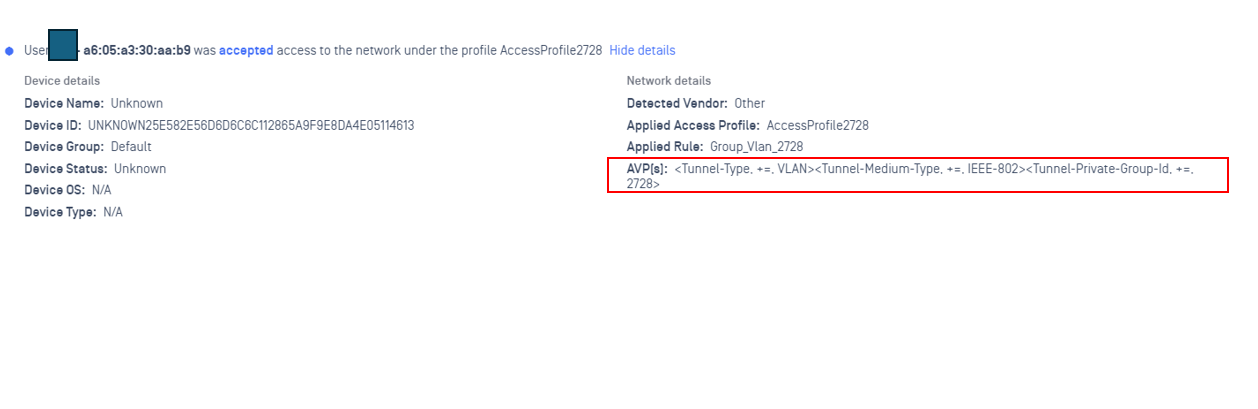
After device was authenticated successfully, we will see it was transfered to vlan 2728
2 - Open Wireless
Scenario: A wireless device connects to an open SSID (no Layer 2 PSK required). This SSID is associated with a quarantine VLAN. In this VLAN, all traffic is redirected to the NAC Edge IP address, except for DHCP and DNS traffic. When a wireless device connects, it is presented with a Cloud NAC Portal where the user must enter their credentials. Once authentication is successful, the device is reassigned to a new VLAN with access to the internet.
To implement this scenario, a Layer 3 router or switch with ACL (Access Control List) and Policy Routing capabilities is required. The configuration will involve the following sections.
- ACL and Policy Map on Router
- Configure WLAN Profile
- Configure Radius Profile on Unleased Portal
2.1 - ACL and Policy Map on Router
ip access-list extended Non_Redirect #create ip access extended
permit udp any any eq domain
permit udp any any eq bootps
route-map CloudNac_Quarantine deny 10 #create route map
match ip address Non_Redirect
route-map CloudNac_Quarantine permit 20
set ip next-hop 10.40.177.85 #IP Address of NAC Edge
#Apply route map into Router
interface GigabitEthernet0/0.1796
description Wireless Quarantine Subnet
encapsulation dot1Q 1796
ip address 10.40.179.65 255.255.255.240
ip helper-address 10.40.177.94 #DHCP Server in outside of this vlan
no ip route-cache
ip policy route-map CloudNac_Quarantine #Apply route map CloudNac_Quarantine
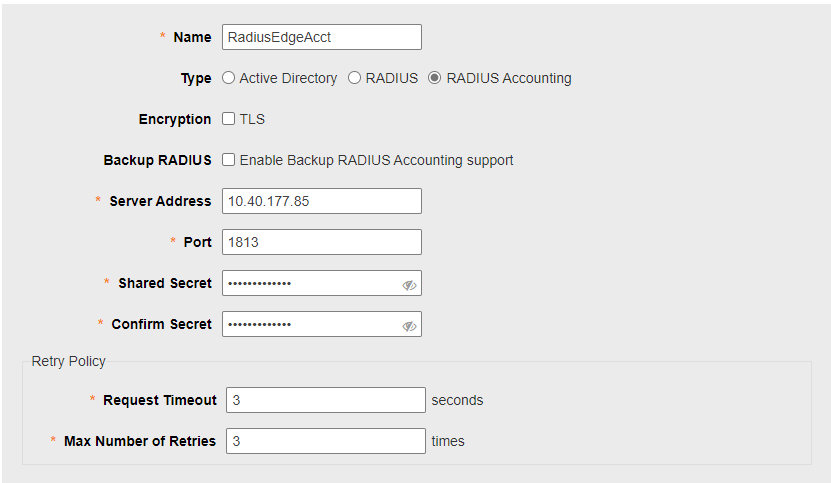
2.2 - Configure Radius Profile
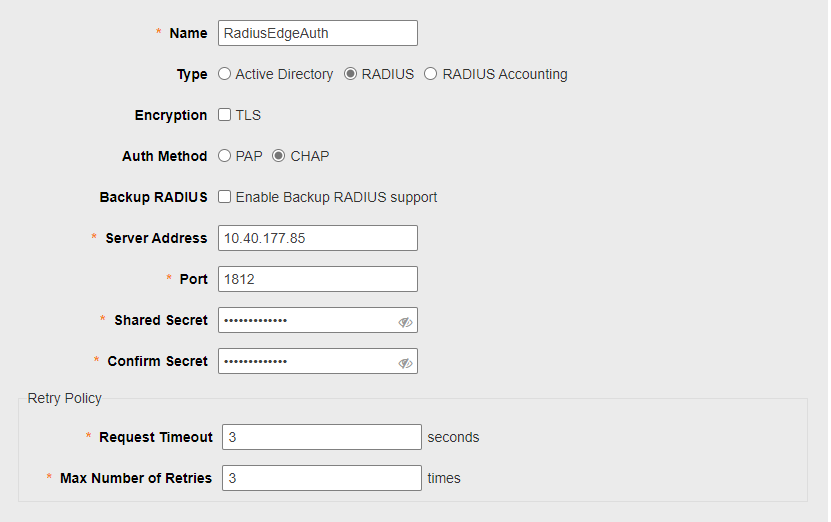
Access to Unleased Portal, choose System -> Servies -> AAA Servers
2.3 - Configure WLAN Profile
Access to Unleased Portal, choose Wi-Fi Networks and Create
Create Open SSID with Radius Server by MAC