Scenario: wireless device access to SSID which configured 802.1X authentication method. After authentication, client device will be transferred to compliant vlan (or ACL). Basic configuration is below:
- AAA Server Profile
- Configure NAC to return vlan to client (or ACL)
1- Secure Wireless
1.1 - Access Control Profile
Click on Wireless -> Access Control
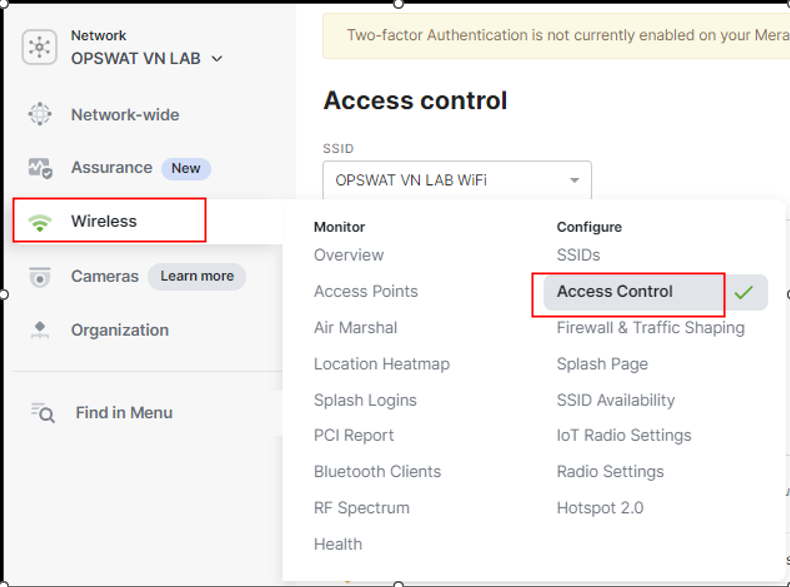
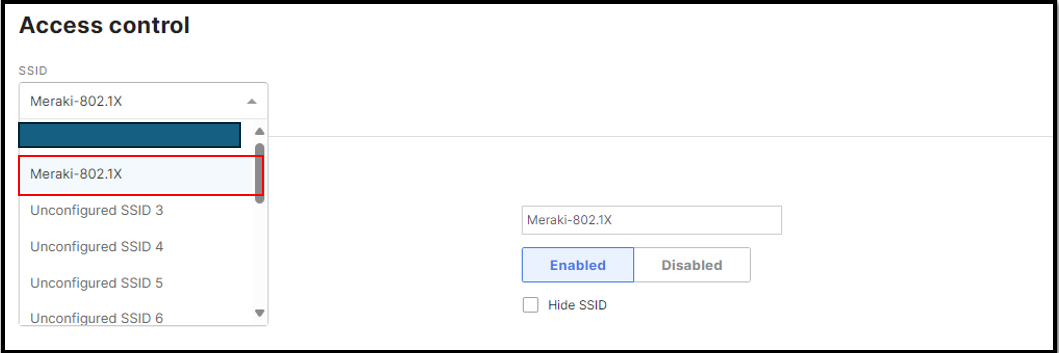
Choose SSID Name
Choose Security -> Enterprise with my Radius server
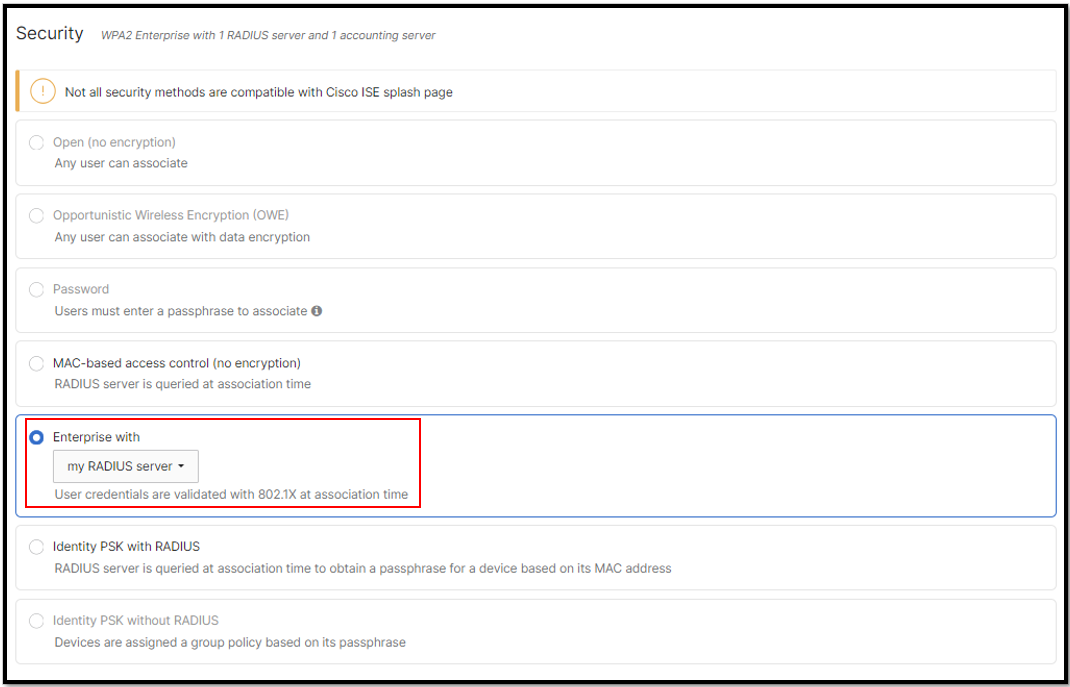
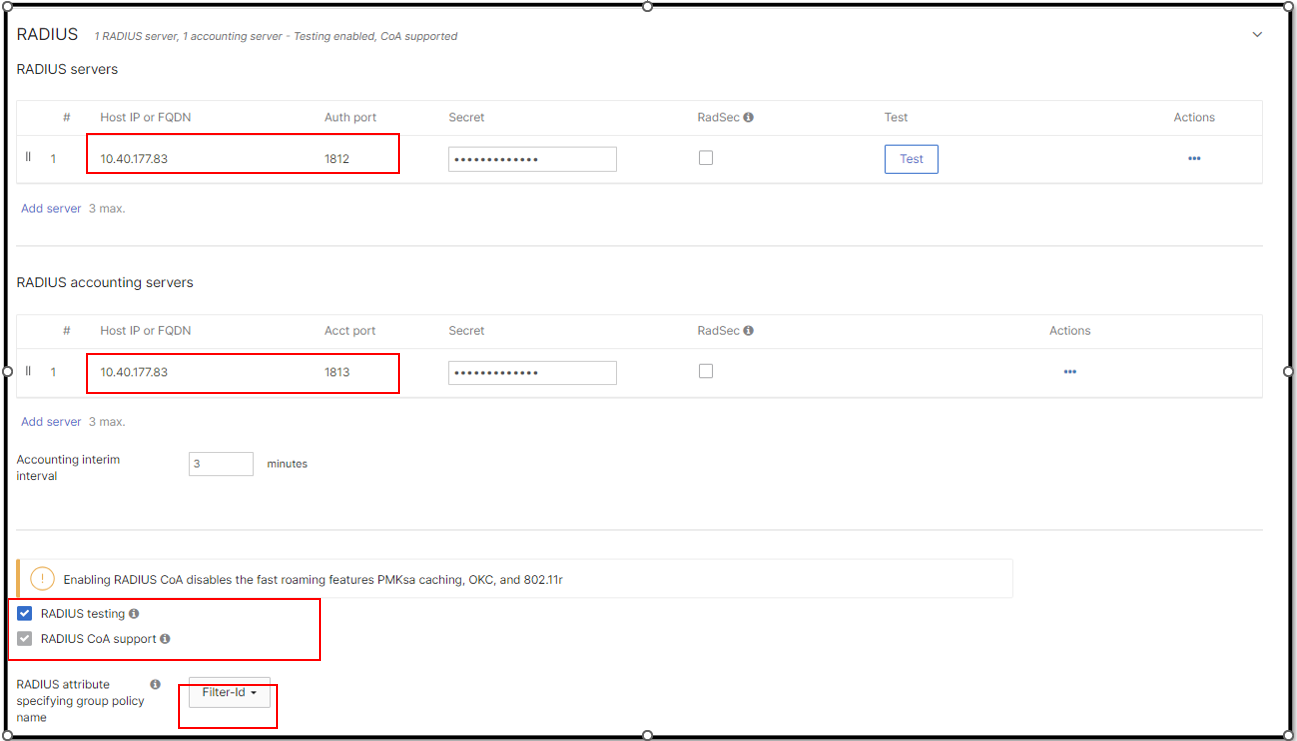
Create Radius Authentication and Accounting Servers
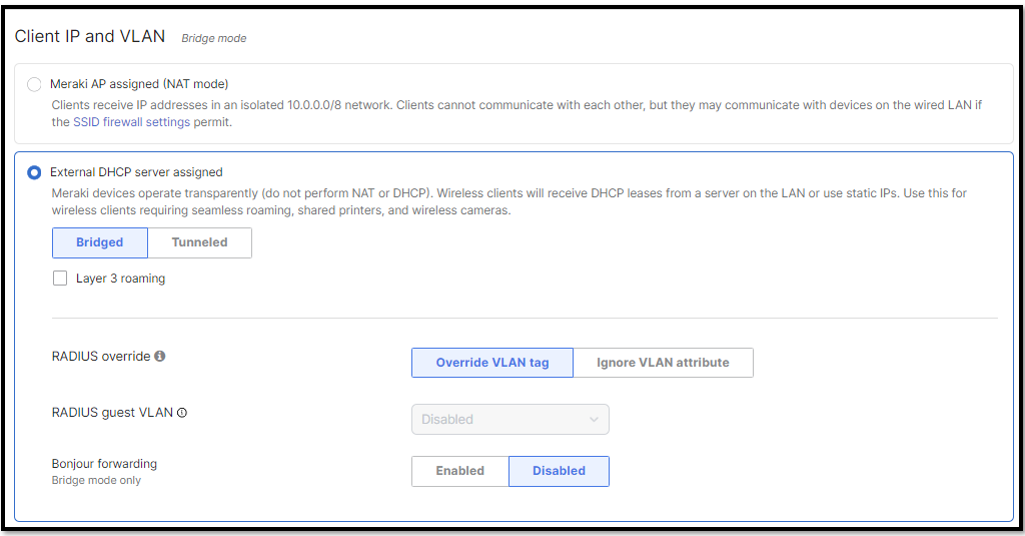
Client IP and Vlan (Bridge Mode)
1.2 - Configure NAC to return vlan to client
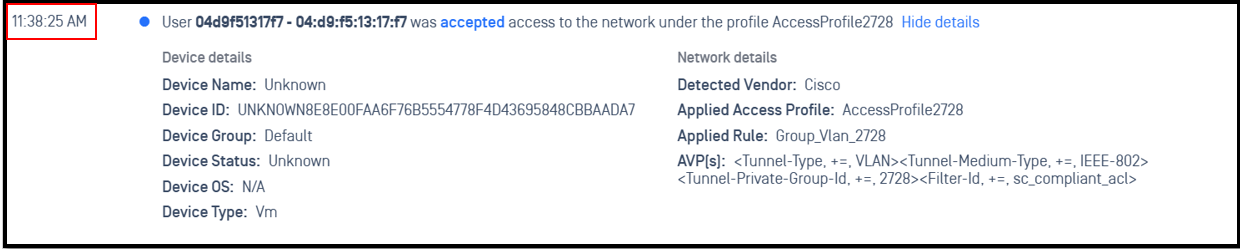
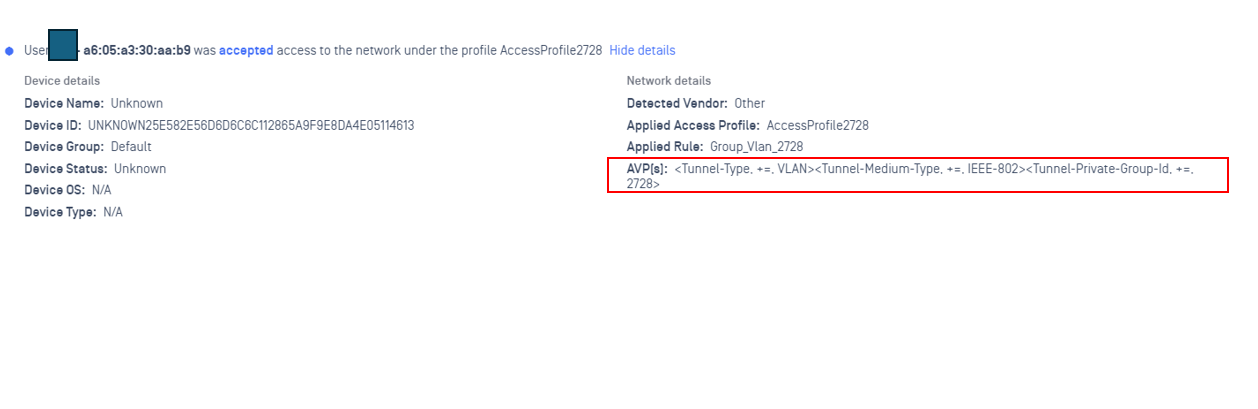
In this scenario, we will return vlan 2728 to this client
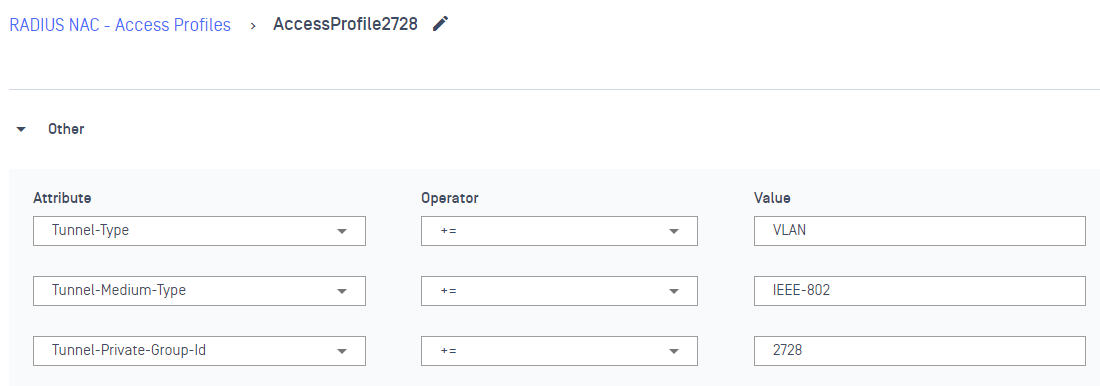
In case we want to return ACL, we can use Filter-ID := "Name of ACL" which predefined in Meraki Dashboard.
After device was authenticated successfully, we will see it was transferred to vlan 2728
2 - Open Wireless
Scenario: A wireless device connects to an open SSID (no Layer 2 PSK required). This SSID is associated with a quarantine VLAN. In this VLAN, all traffic is redirected to the NAC Edge IP address, except for DHCP and DNS traffic. When a wireless device connects, it is presented with a Cloud NAC Portal where the user must enter their credentials. Once authentication is successful, the device is reassigned to a new VLAN with access to the internet.
The configuration will involve the following sections.
- ACL
- Access Control Profile
- New DNS record
- Access Profile and Rule on Cloud NAC Dashboard
2.1 - Configure ACL
Access to Meraki Dashboard -> Network-wide -> Group Policy
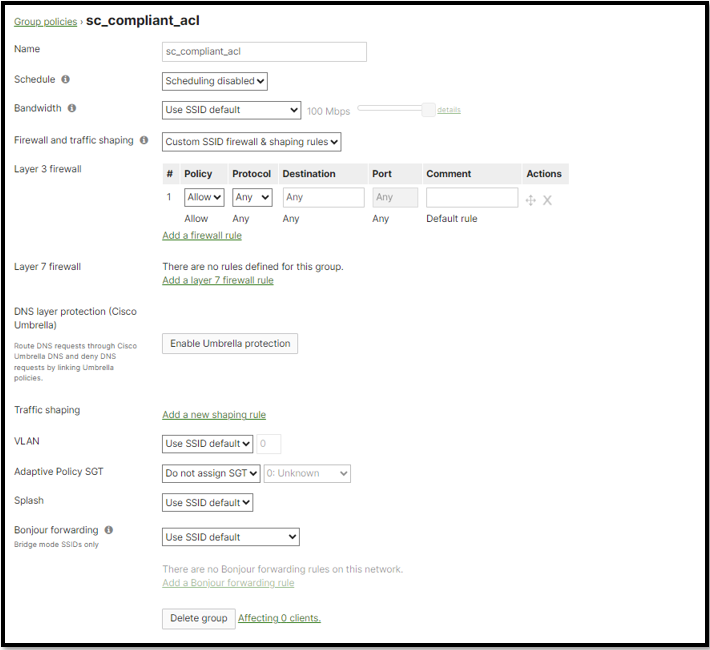
Create ACL and named it sc_compliant_acl. In this ACL, we can create some of custom ACLs which deny or permit certain type of traffic. In this example, we just simply create allow all ACL
2.2 - Access Control Profile
Click on Wireless -> Access Control
Choose SSID
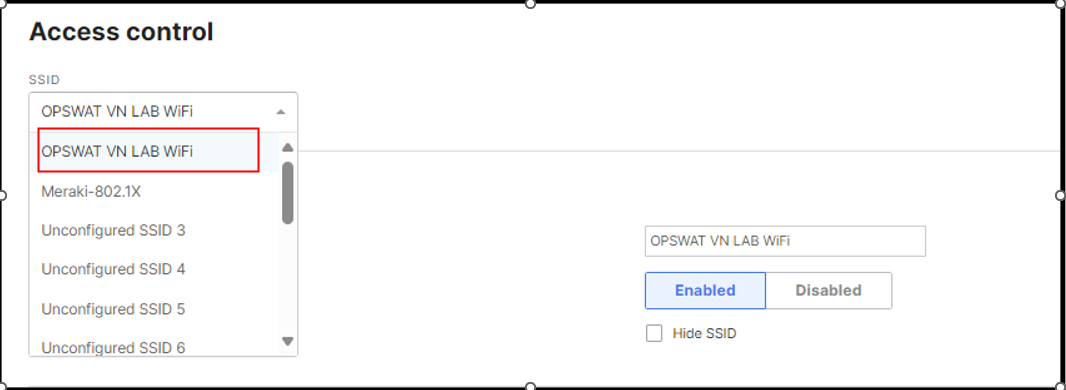
Choose Security -> Mac-based access control (no encryption)
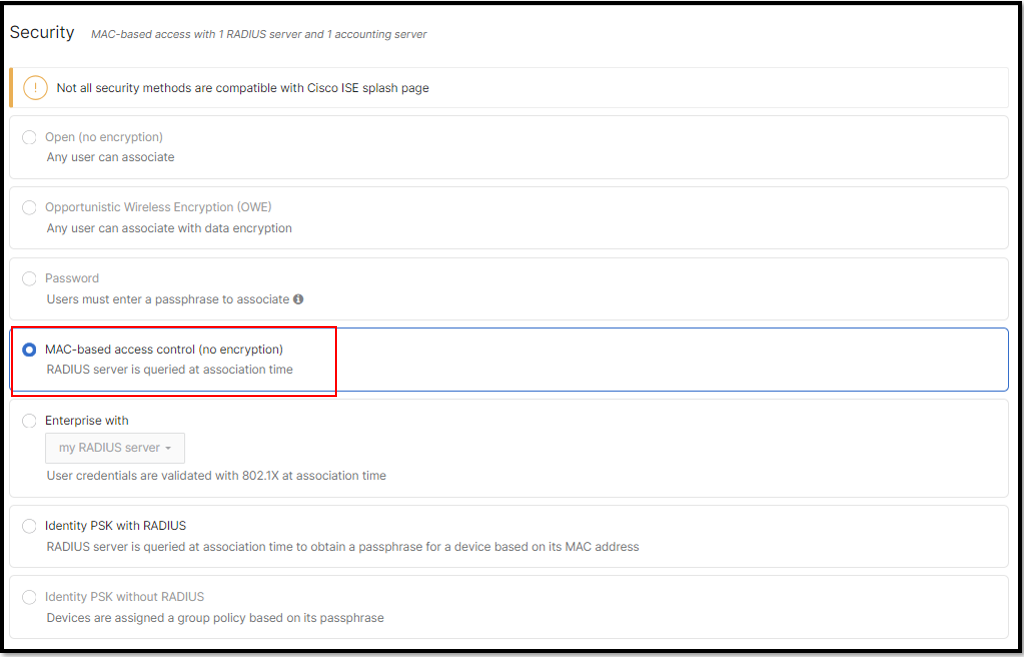
Choose Splash page -> Cisco Indentity Services Engine (ISE) Authentication
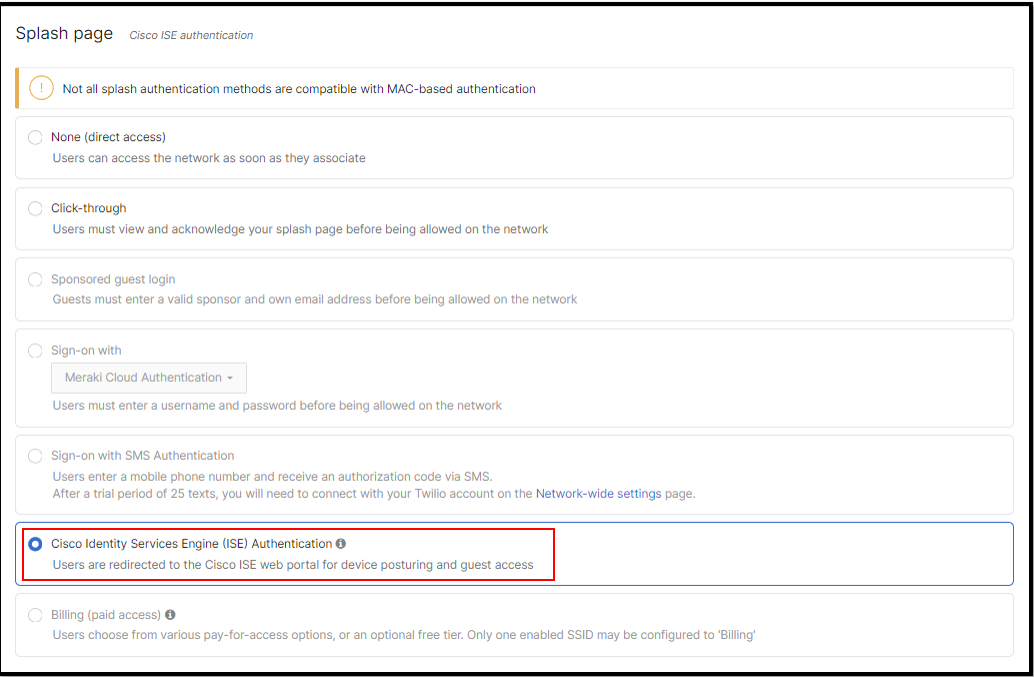
Choose Radius -> Setting configurations as below picture
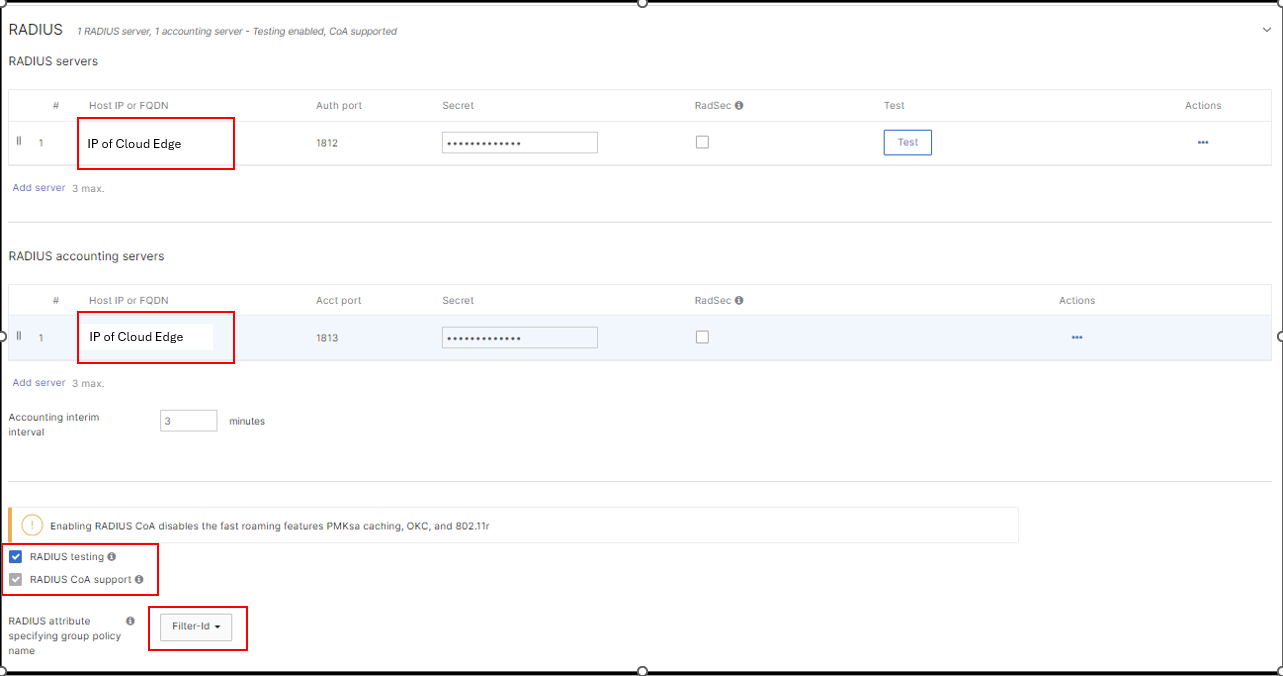
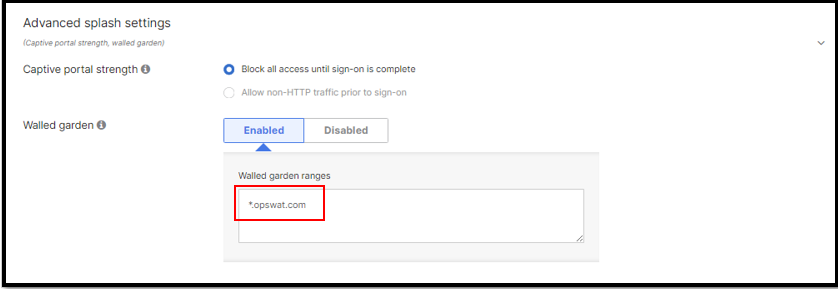
Choose Advanced splash settings
In this setting we will fill *.opswat.com domain name in
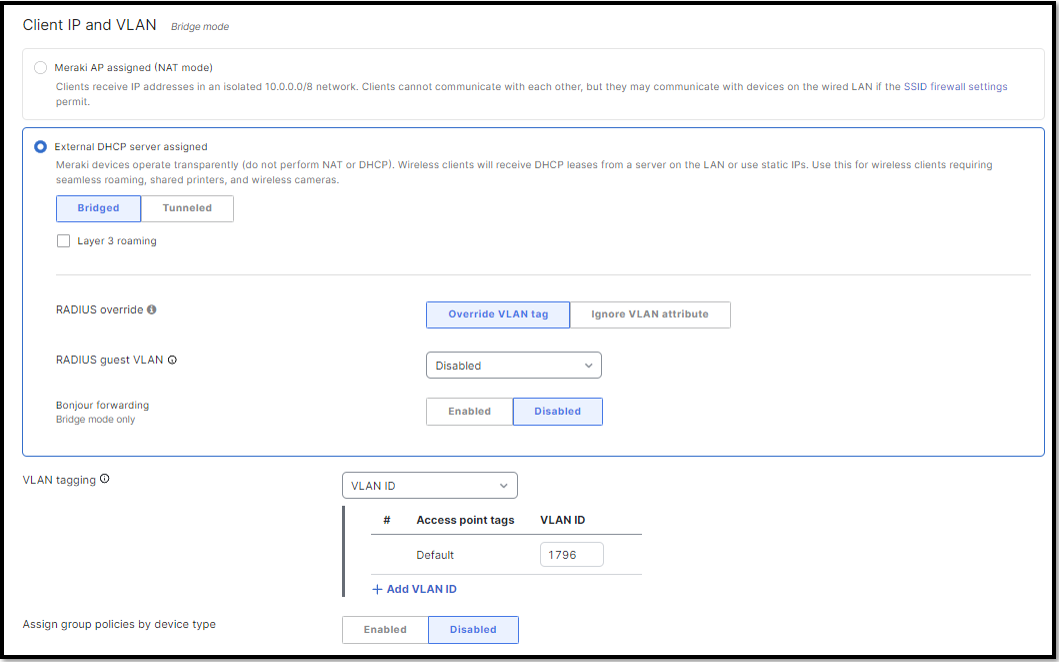
Choose IP and VLAN -> External DHCP server assigned
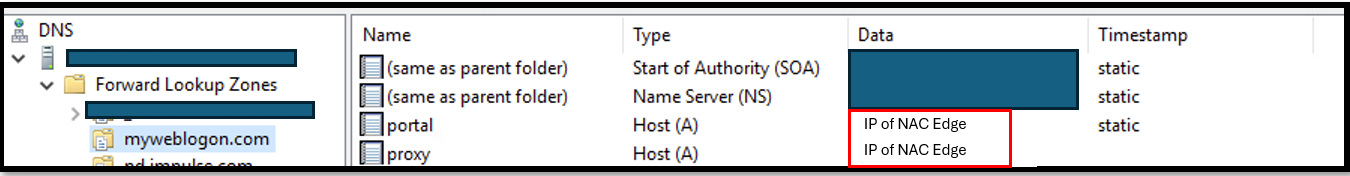
2.3 - New DNS Record
In this scenario, we will need to create one more DNS record, for example, give it a name proxy.myweblogon.com. We created it in DNS Windows Server
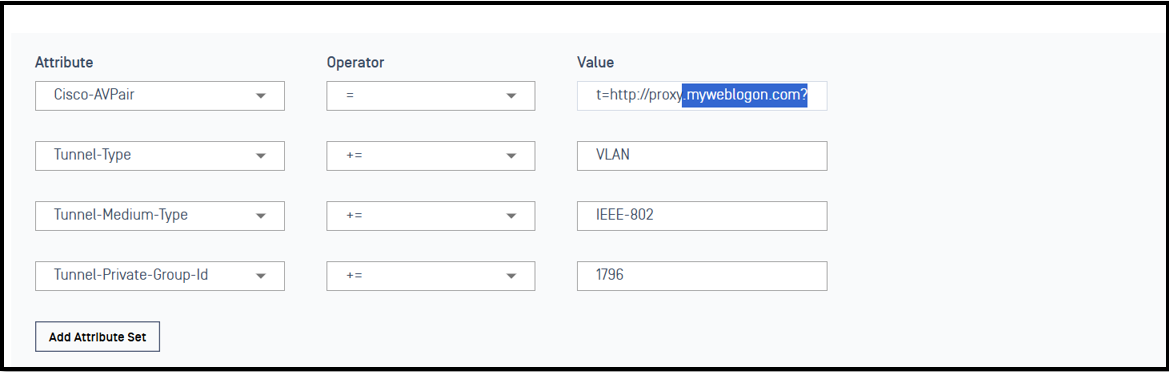
2.4 - Access Profile and Rule on Cloud NAC Dashboard
Create Access Profile
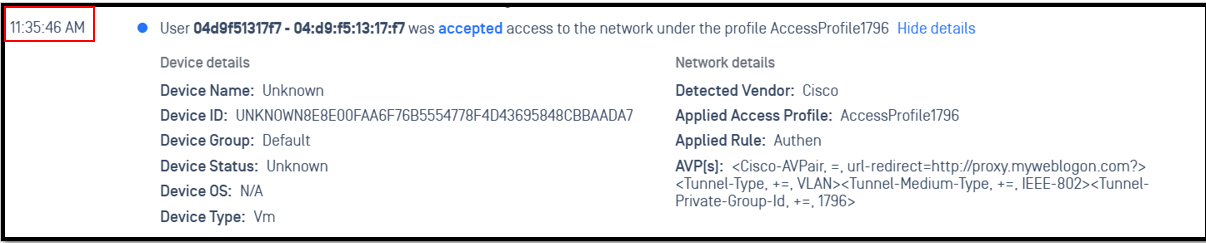
We will create the AccessProfile1796, it will return URL redirect to proxy.myweblogon.com and vlan 1796 to client. This proxy will force client to be authenticated with Cloud NAC portal
Cisco-AVPair=url-redirect=http://proxy.myweblogon.com? #Please note that we need "?" at the end of sentence
Tunnel-Type+=VLAN
Tunnel-Medium-Type+=IEEE-802
Tunnel-Private-Group-Id+=1796
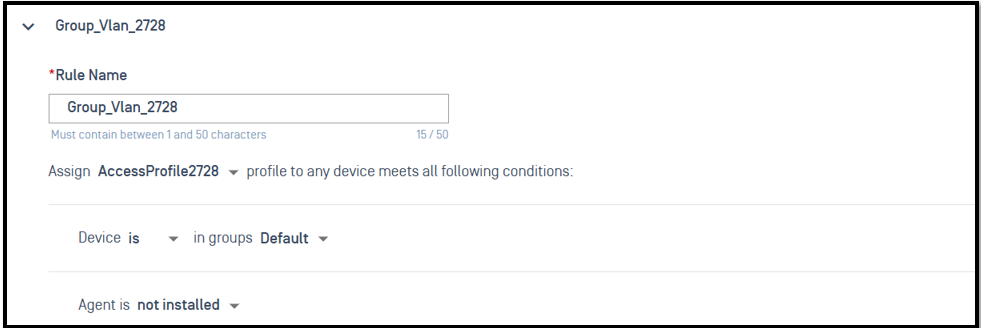
The next AccessProfile2728 will return client device in vlan 2728 and ACL sc_compliant _acl
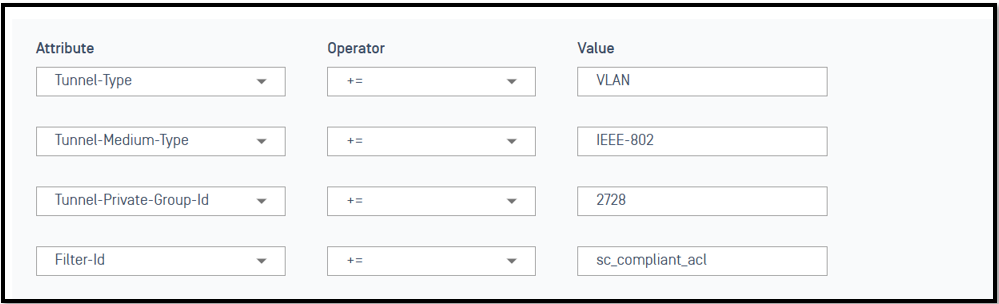
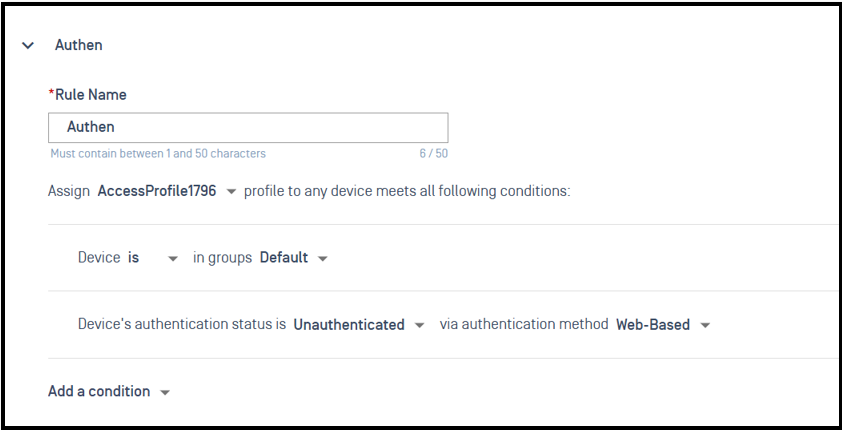
Create Rule : Client device will be assigned profile when they access to network
After successfully authenticated, client device will be changed vlan and acl with another rule
Check log Radius Event on Cloud NAC Portal