Advanced Deployment
v4.8.0
Search this version
Advanced Deployment
Advanced Deployment
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Microsoft Entra ID Integration (OIDC)
Copy Markdown
Open in ChatGPT
Open in Claude
This section provides instructions for administrator to configure Microsoft Entra ID with SSO OIDC for authenticating to KIOSK UI.
Prerequisites
- Kiosk version 4.7.5 or later
- Microsoft Entra ID with pre-configured app to use OpenID Connect (OIDC) and users have been assigned to the application
- If the Application hasn't been created, please refer to Step 1 and 2 in this Microsoft Entra ID Integration - MetaDefender Kiosk Windows
To streamline the SSO-login process between Kiosk and MFT (3.9.0 or later), please ensure both are connecting to the same Entra ID application and protocol (OIDC)
Kiosk version 4.7.6 (and older) does not support domain name with hyphen "-", e.g User@domain-abc.com
Instruction
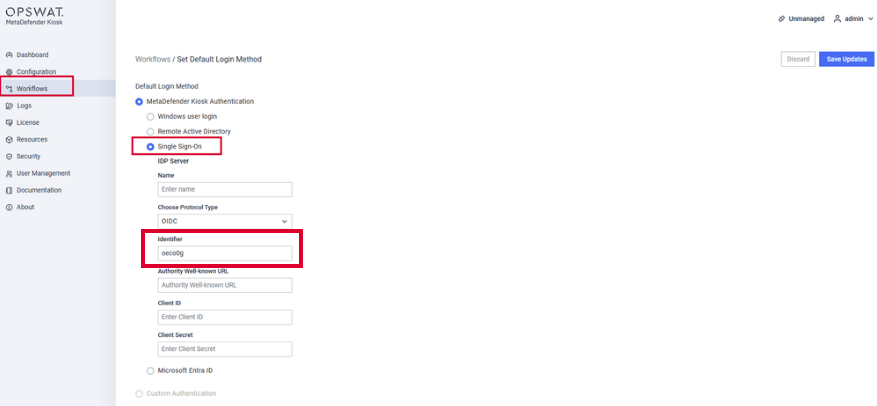
In order to authenticate with Entra ID (OIDC) in Kiosk UI, we need to configure the SSO settings under Kiosk Console, navigate to Workflows > Employee Workflow > Set Default Login Method > Single Sign-On > Select OIDC
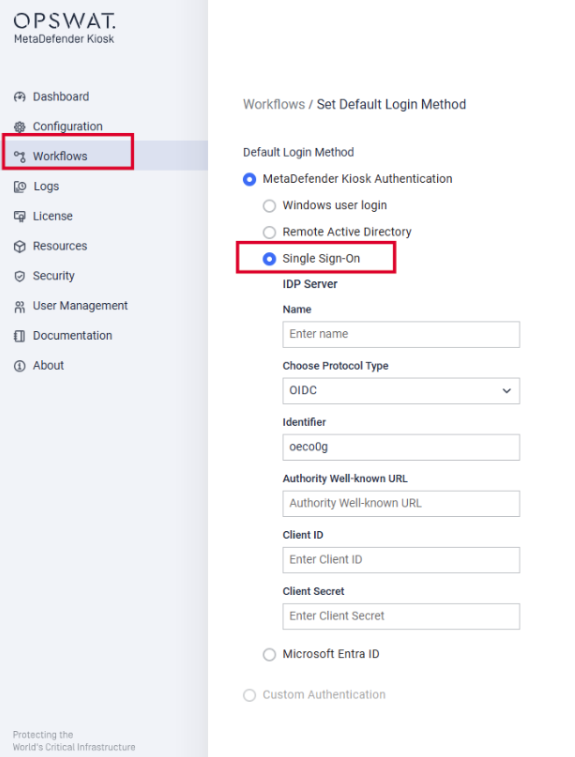
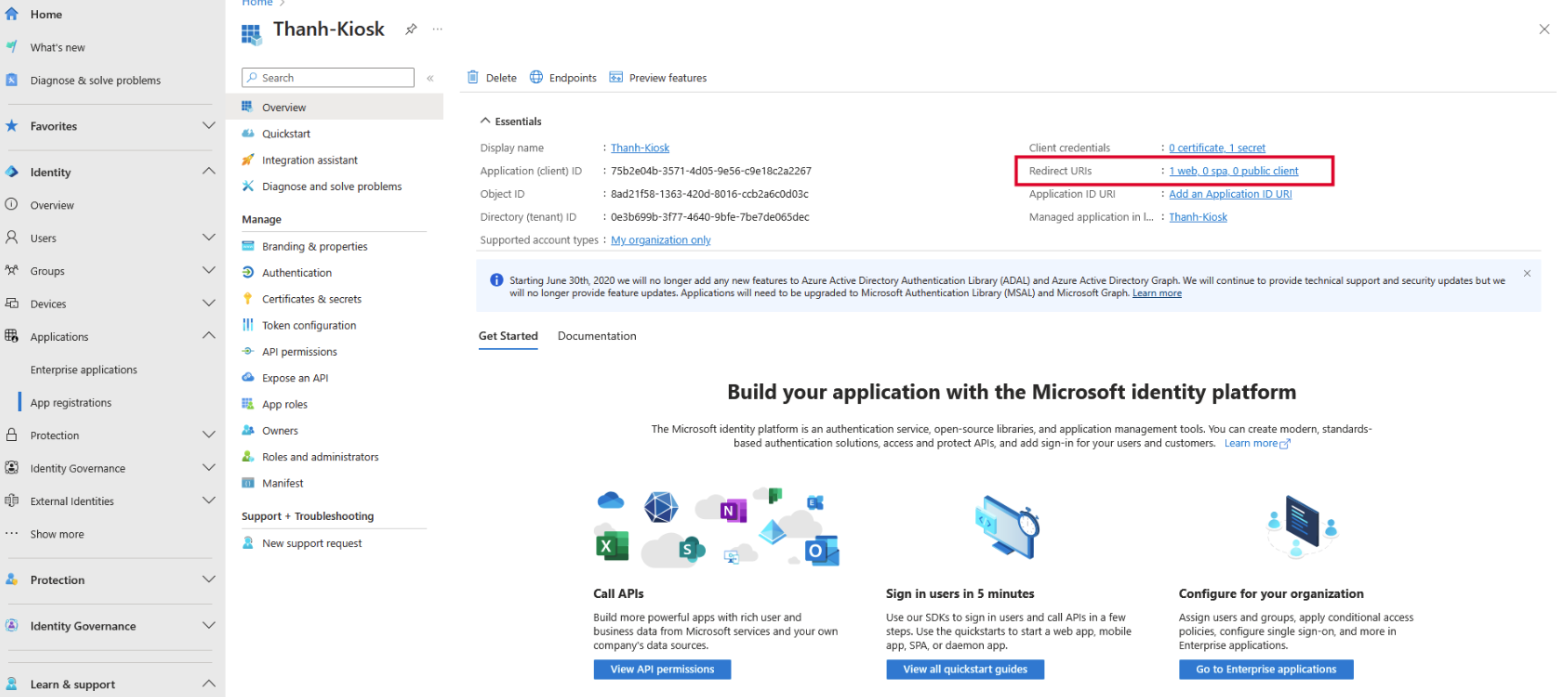
The 3 fields (Authority Well-known URL, Client ID, Client Secret) can be found in Entra ID App Registrations settings
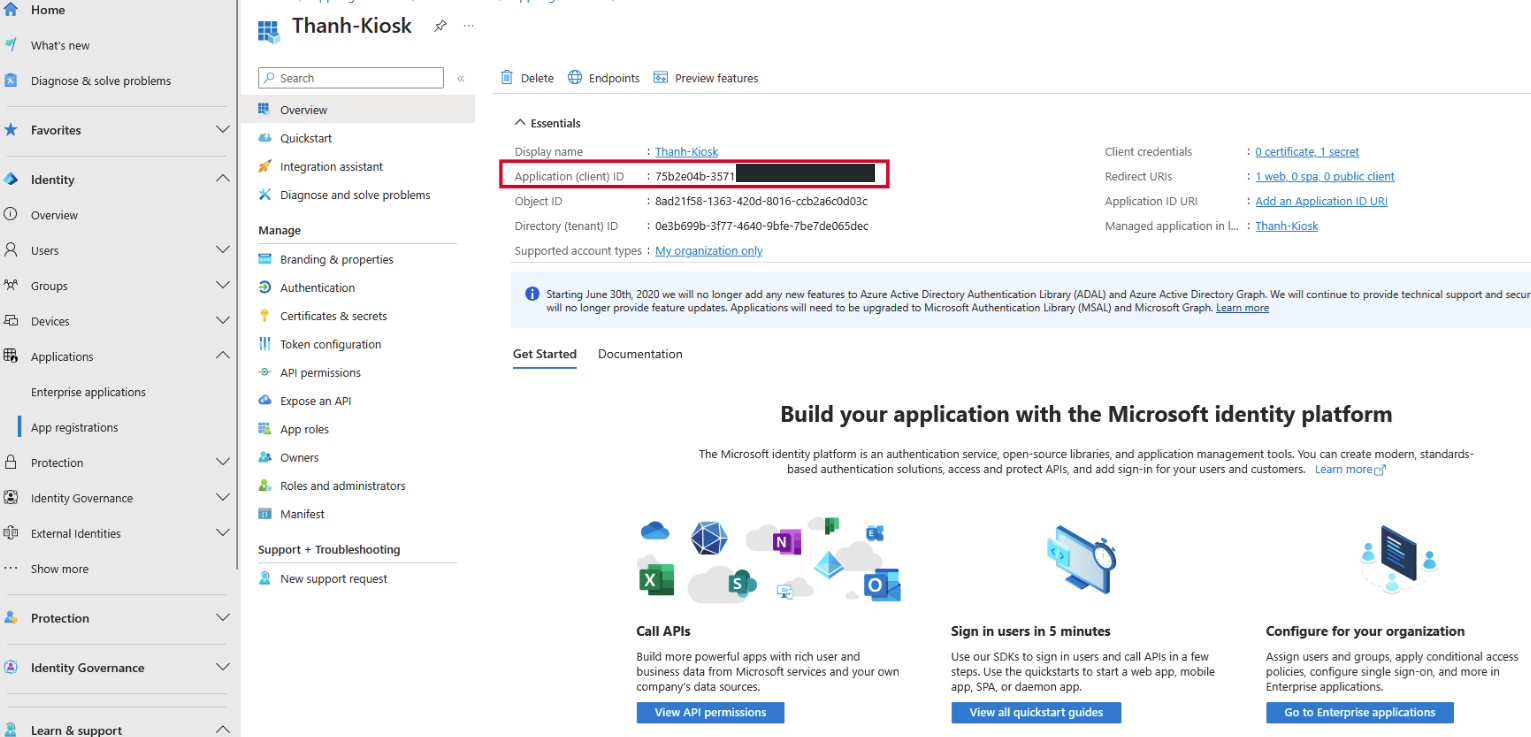
- Select the application that you have already created
- Within the Application, copy Client ID
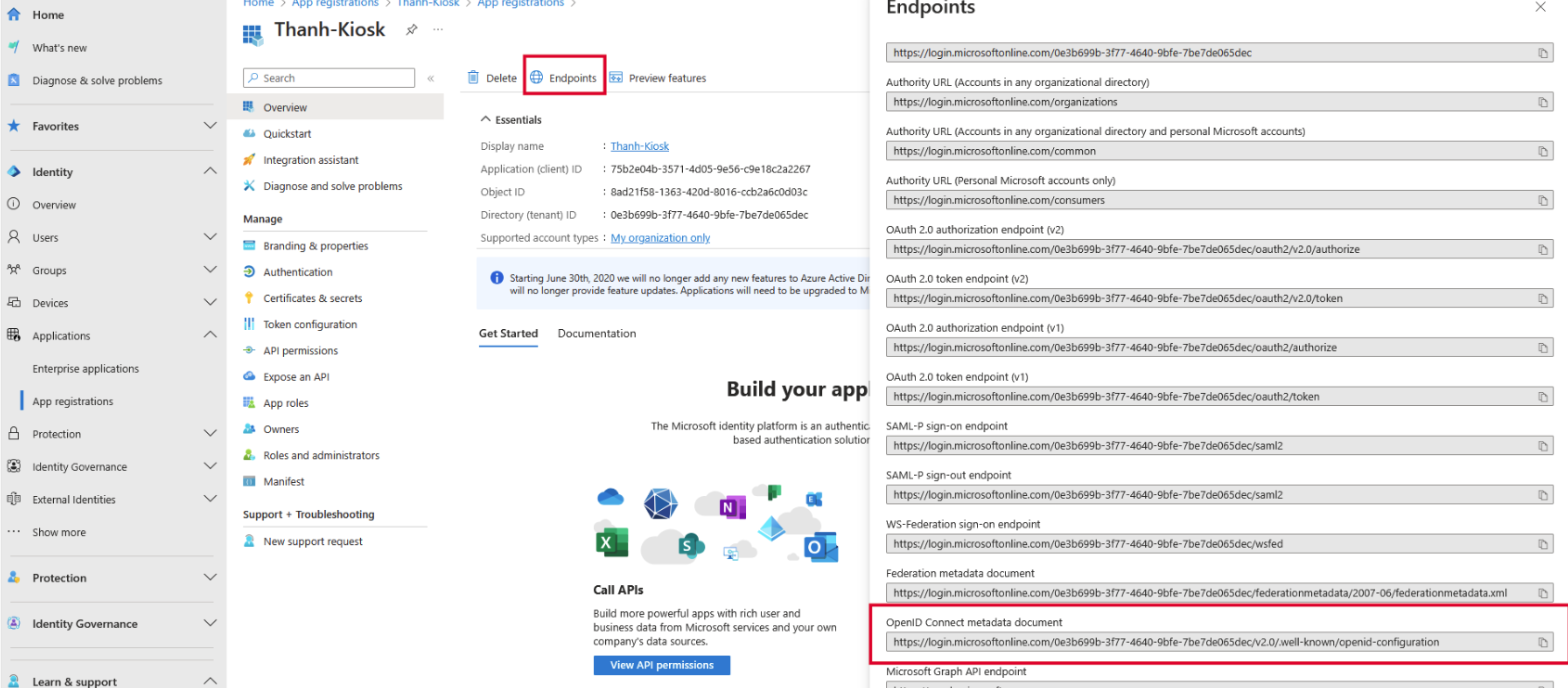
- Then click on Endpoints to get Authority Well-known URL
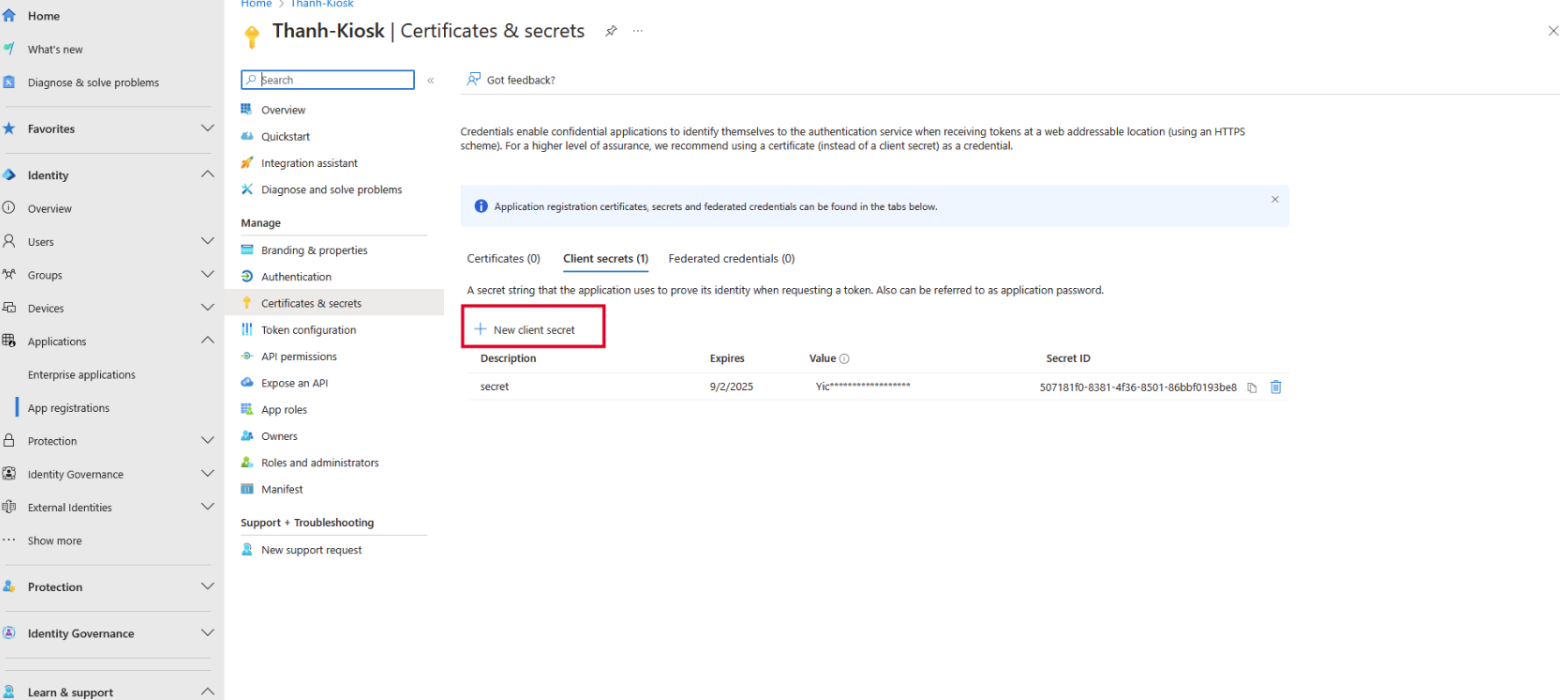
- Then click on Client Credentials to create a new Client Secret

- Finally, click on Redirect URIs to register another endpoint represent the Kiosk
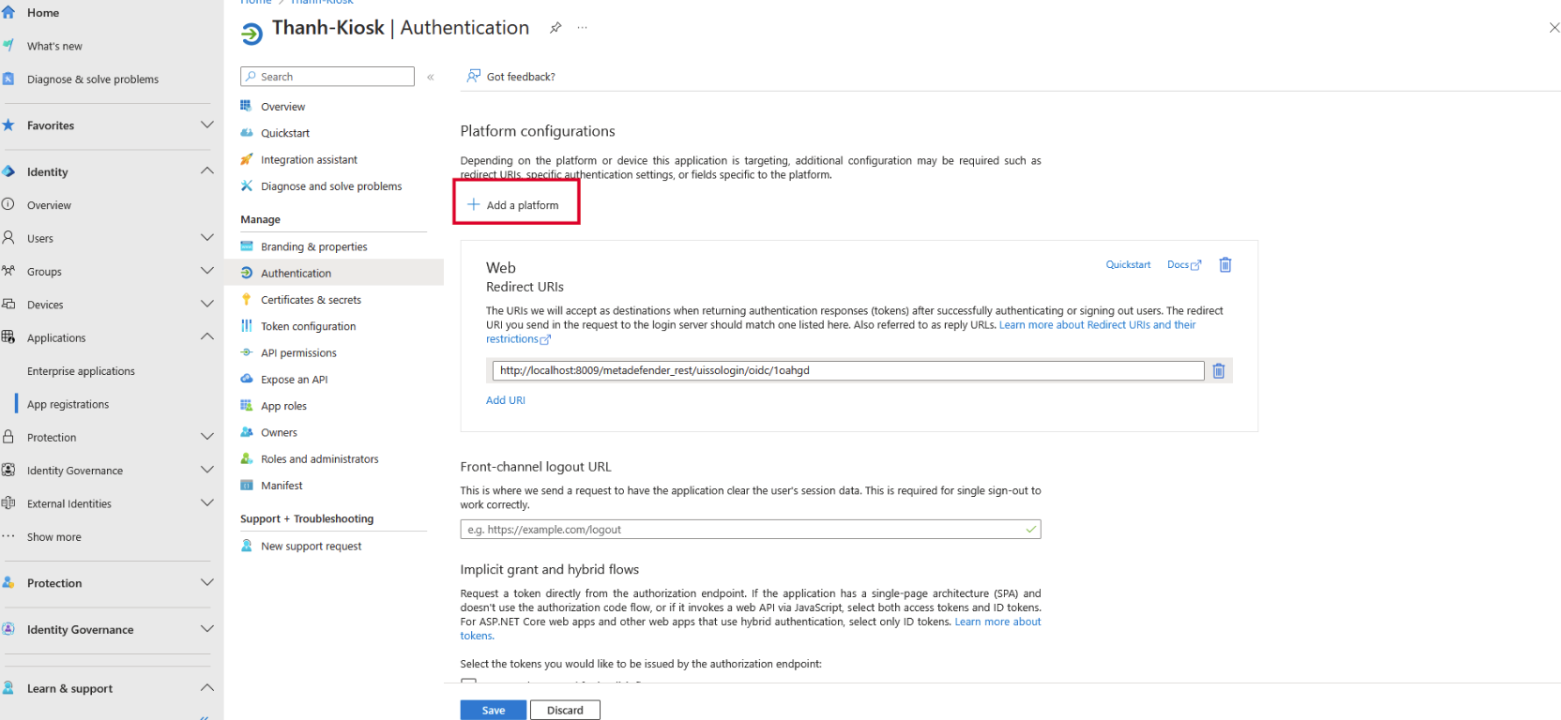
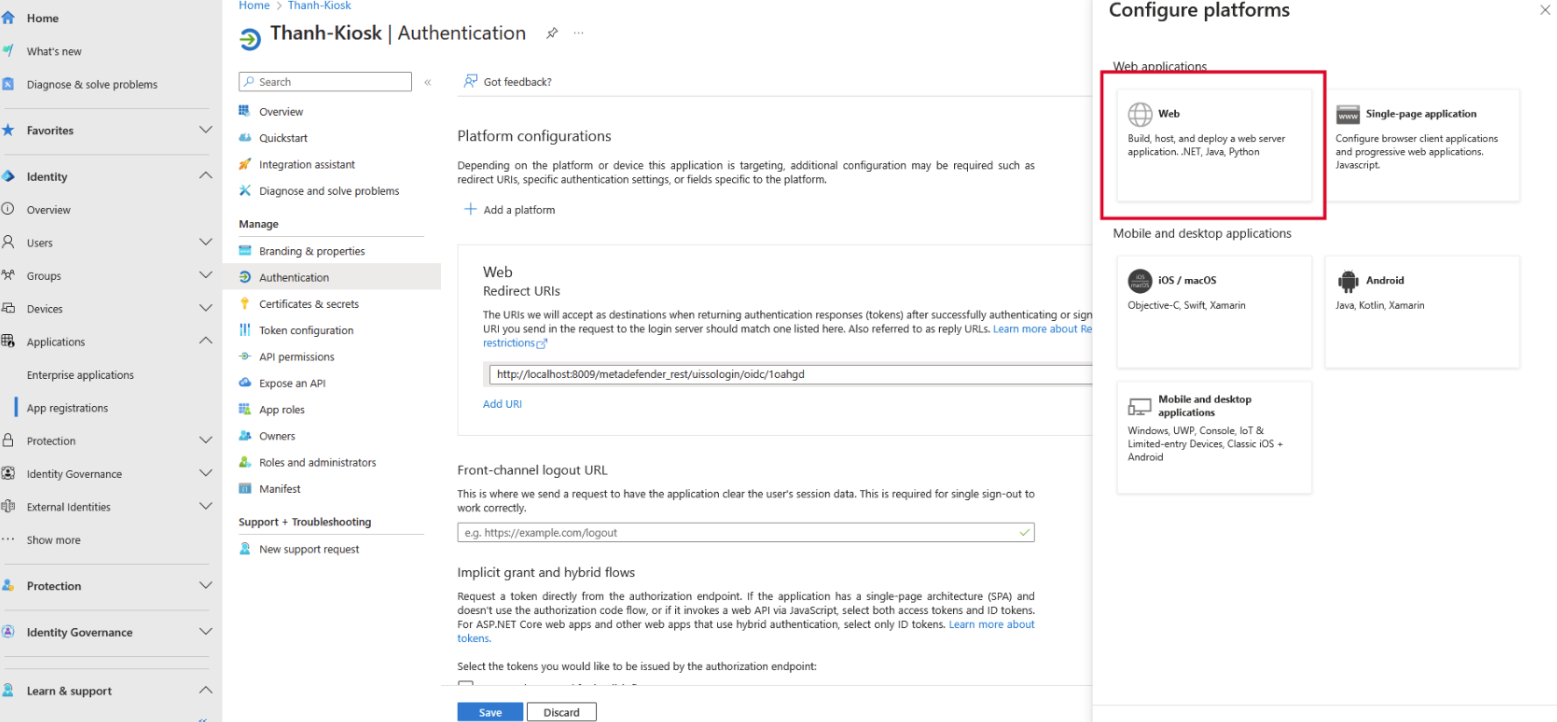
- In the Redirect URIs textbox, please enter the following format, replace all placeholders with the value reflecting your Kiosk system.
<http/https>://localhost:<port>/metadefender_rest/uissologin/oidc/<identifier>
- <http/https> : whether the Kiosk WebMC is running on http or https.
- <port> : the port number you are using to access the Kiosk WebMC (default to 8009).
- <identifier> : unique string you can get from the Kiosk WebMC
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Encrypted Device Verification And ApprovalDiscard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

