Knowledge Base
v5.16.1
Search this version
Knowledge Base
Knowledge Base
Configuration and Settings
Errors and Troubleshooting
Features and Functionality
Licensing, Setup and Deployment
Updates, Patches and Bug Fixes
Version Upgrades
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
What are the MetaDefender Core Security Policies and how do they work?
Copy Markdown
Open in ChatGPT
Open in Claude
As an overall simplified explanation of the topic, file processing on MetaDefender Core is orchestrated via workflow management.
- Any file processing request must be tied to a specific “workflow rule” whereas all product configurations and rules are defined.
- Each “workflow rule” must be tied to specific “template” and “security zones”:
- A “template” is literally a template that one or many “workflow rule” can be based on, which means, inherit all configurations' values that “template” defines to use for that “workflow rule”. Of course, you can customize configuration values for “workflow rule” after inheriting configurations' values from “template”. Similar relational concept like users & groups, or files & folders permission.
- A “security zones” is created as network filtering rule based IP address range for that corresponding “workflow rule”. That means, any client source’s address going out of that IP address range, that client is not allowed to use that “workflow rule” for file processing.
The term Security Policies refers to three highly configurable objects that work in combination to accomplish MetaDefender’s primary security function.
These objects are:
- Workflows
- Security Zones
- Templates
Workflows
The workflow is identified by its name.
- It defines eligibility parameters to use it (i.e. whether a client is in the proper Security Zone and/or the actual logged-in user is in the specified Role and/or the client has provided the required user_agent).
- It inherits processing characteristics (i.e. whether to scan files with the malware engines, if and how to use data sanitization, if and how to extract archives, etc.) from a Workflow that gets assigned to it.
- It also allows direct assignment of processing characteristics that override the characteristics of the Workflow.
You create a Workflow by giving it a name and assigning a Security Zone and a Template to it. You can also assign specific processing characteristics to it.
- A file's eligibility to be processed by the Workflow is determined by the filtering parameters under the General tab.
- If all the required parameters are matching, the processing actions performed on that file are then determined by the specific processing characteristics set on the Workflow such as:
- General tab
- Archive tab
- Filetype tab
- Metascan tab
- Deep CDR tab
- Proactive DLP tab
- Threat Intelligence tab
- Vulnerability tab
- Blocklist tab (as shown in the screenshot below)
- Allowlist tab
- Yara tab
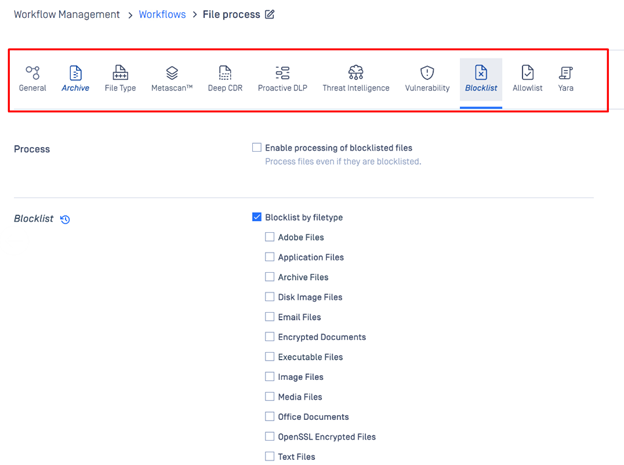
- Workflows can be reordered using drag & drop.
Security Zones
Templates
The Template can be thought of as a template of process settings.
- By assigning the Workflow to a Template, the Workflow inherits the Template settings for each field that has not been directly populated on the Workflow.
Templates that are included out-of-the-box with each MetaDefender Core V5 installation are:
- Default
- Skip Images
- Executables Only
- These Workflow Templates cannot be altered or deleted, but they can be copied to custom Workflows that can then be edited.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Is Metadefender Core compromised while scanning files?Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message