Installation
v5.17.1
Search this version
Installation
Installation
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
CIS Level 1 - Linux Guidelines
Copy Markdown
Open in ChatGPT
Open in Claude
Red Hat Enterprise Linux 9
For more details about Center for Internet Security (CIS) please refer to this document
Instruction steps
I. Install OpenSCAP
bash
yum install openscap-scanner scap-security-guideII. Generate a result file and a HTML report using OpenSCAP scanner tool
Bash
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_cis_server_l1 --results scan_results.xml --report scan_report.html /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xmlIII. Remediation of CIS Level 1 issues
Generate a remediation script based on the ssg-rhel9-ds.xml file:
Bash
oscap xccdf generate fix --profile xccdf_org.ssgproject.content_profile_cis_server_l1 --fix-type bash --output remediations.sh /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xmlAnd execute remediation script.
Bash
./remediations.shIV. Review the results after remediation
Bash
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_cis_server_l1 --results scan_results.xml --report scan_report.html /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xmlExample:
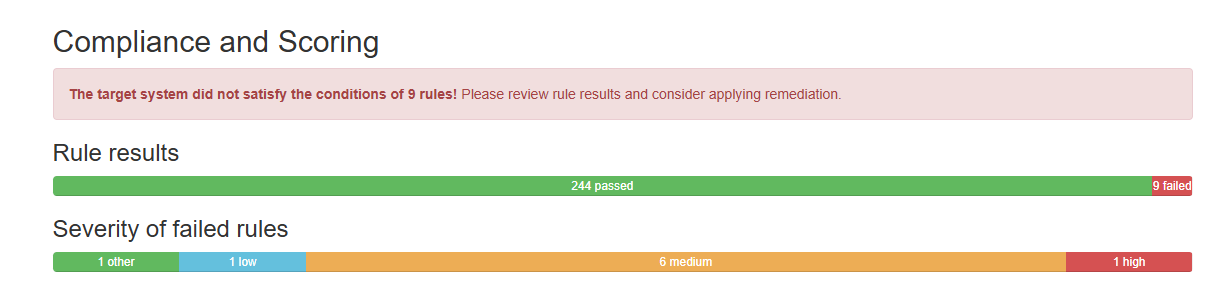
Ubuntu 22 Pro
Install the UA client
Bash
sudo apt updatesudo apt install ubuntu-advantage-toolsSet up the Ubuntu Security Guide
Bash
sudo ua enable usgsudo apt install usgCheck SCAP Content Overview (Security Content Automation Protocol)
Bash
sudo oscap info /usr/share/ubuntu-scap-security-guides/1/benchmarks/ssg-ubuntu2204-ds.xmlAuditing an Ubuntu System for DISA-STIG compliance
Bash
sudo usg audit cis_level1_serverThe report is generated in /var/lib/usg/
Applying the CIS rules to a set of systems
There are 2 ways that apply CIS rules
Method 1: directly using usg command - recommend
Bash
sudo usg fix cis_level2_serverMethod 2: using usg to generate script and then run the script
Bash
sudo usg generate-fix cis_level2_server --output fix.sh#And the run./fix.shA reboot is require to take the effect after apply the fix.
Notes
- CIS Level 1 requires
/tmpfolder to be mounted in a separate partition. Please ensure that that new partition have enough disk space for MetaDefender Core to run. - CIS Level 1 requires that "Ensure No World-Writable Files Exist".
- For now, when freshly installing MetaDefender Core, all its binary files meet the requirement.
- When installing/updating engines, some engines might create additional files for its operation, and it might violate this requirement. In this case, you need to again execute the remediation script in the step III.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
CIS Level 2 - Linux GuidelinesDiscard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message
On This Page
CIS Level 1 - Linux GuidelinesRed Hat Enterprise Linux 9Instruction stepsI. Install OpenSCAPII. Generate a result file and a HTML report using OpenSCAP scanner toolIII. Remediation of CIS Level 1 issuesIV. Review the results after remediationUbuntu 22 ProInstall the UA clientSet up the Ubuntu Security GuideCheck SCAP Content Overview (Security Content Automation Protocol)Auditing an Ubuntu System for DISA-STIG complianceApplying the CIS rules to a set of systemsA reboot is require to take the effect after apply the fix.Notes
