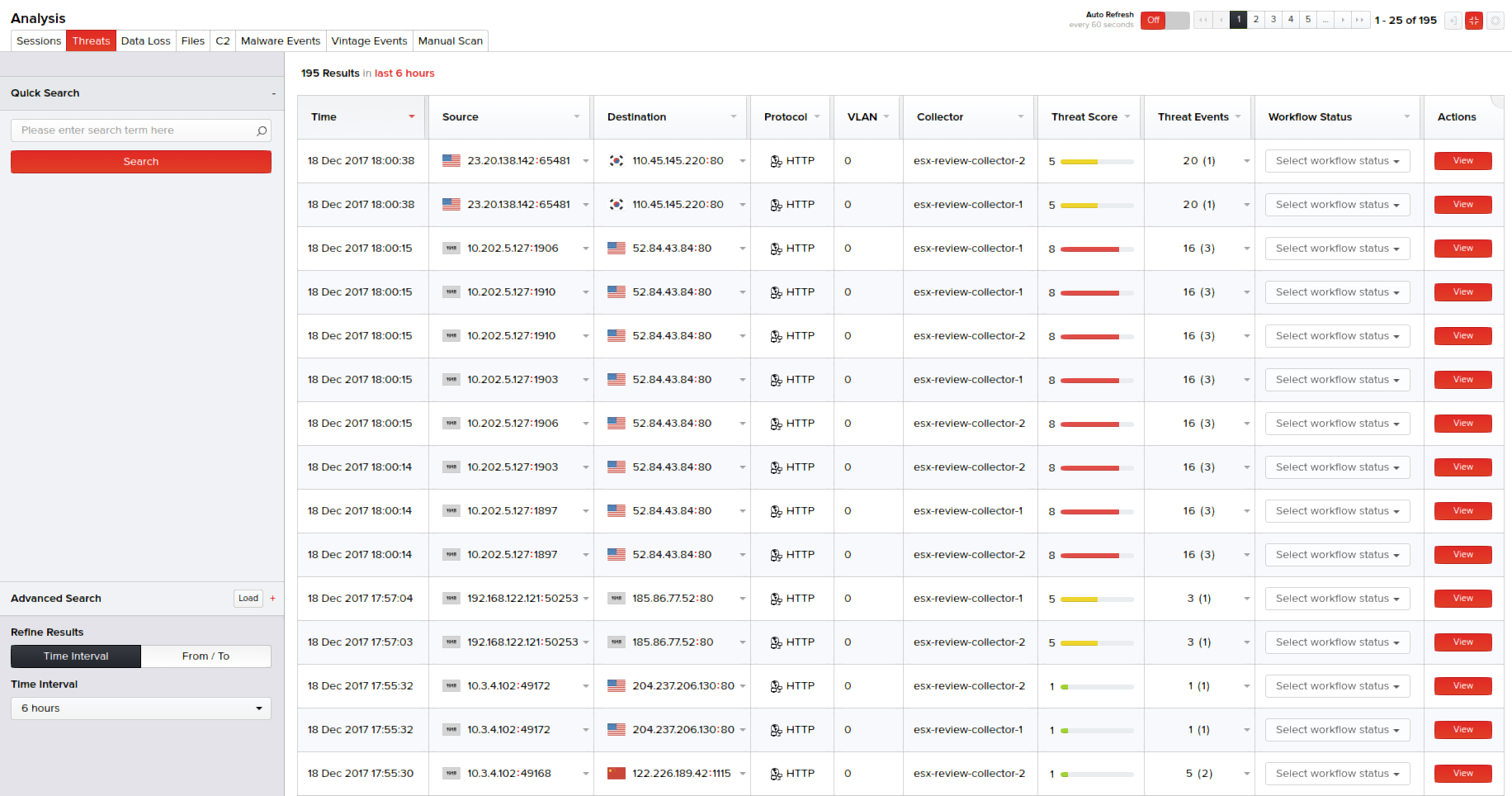
The Threats page displays a summarized list of sessions whose overall content and alerts have been assessed and given a threat score. The color-coded threat score given to the TCP sessions is based on severity and confidence of static analysis scans, cloud-based hash analysis, and file entropy.
Click Analysis > Threats. The right pane displays the basic session details in a tabular form; each session being assigned a threat score. The interface provides both Quick Search and Advanced Search features on the left pane.
Columns available in the Advanced Search menu for the Threats page are:
- Source IP
- Destination IP
- Source Port
- Destination Port
- Threat score
- Events count
- Events count (Unique)
- VLAN ID
- Workflow
- Collector
- Workflow Owner
- Protocol
- File: MD5
- File: SHA1
- File: SHA256
- File: SHA512
- File: Entropy
- File: Signature Name
Select the column(s) and specify their criteria. You can also specify the session time from the Time Interval drop-down menu or select a date range from the built-in calendars by clicking the From/To option. Click Search. Results appear in the right pane and display sessions with individual threat scores. Information on each session that includes the session time when the PCAPs were captured off the sessions, source and destination IP addresses, protocol, VLAN, collector host name, threat score, unique events of the total events, and a link to view the session details are displayed.
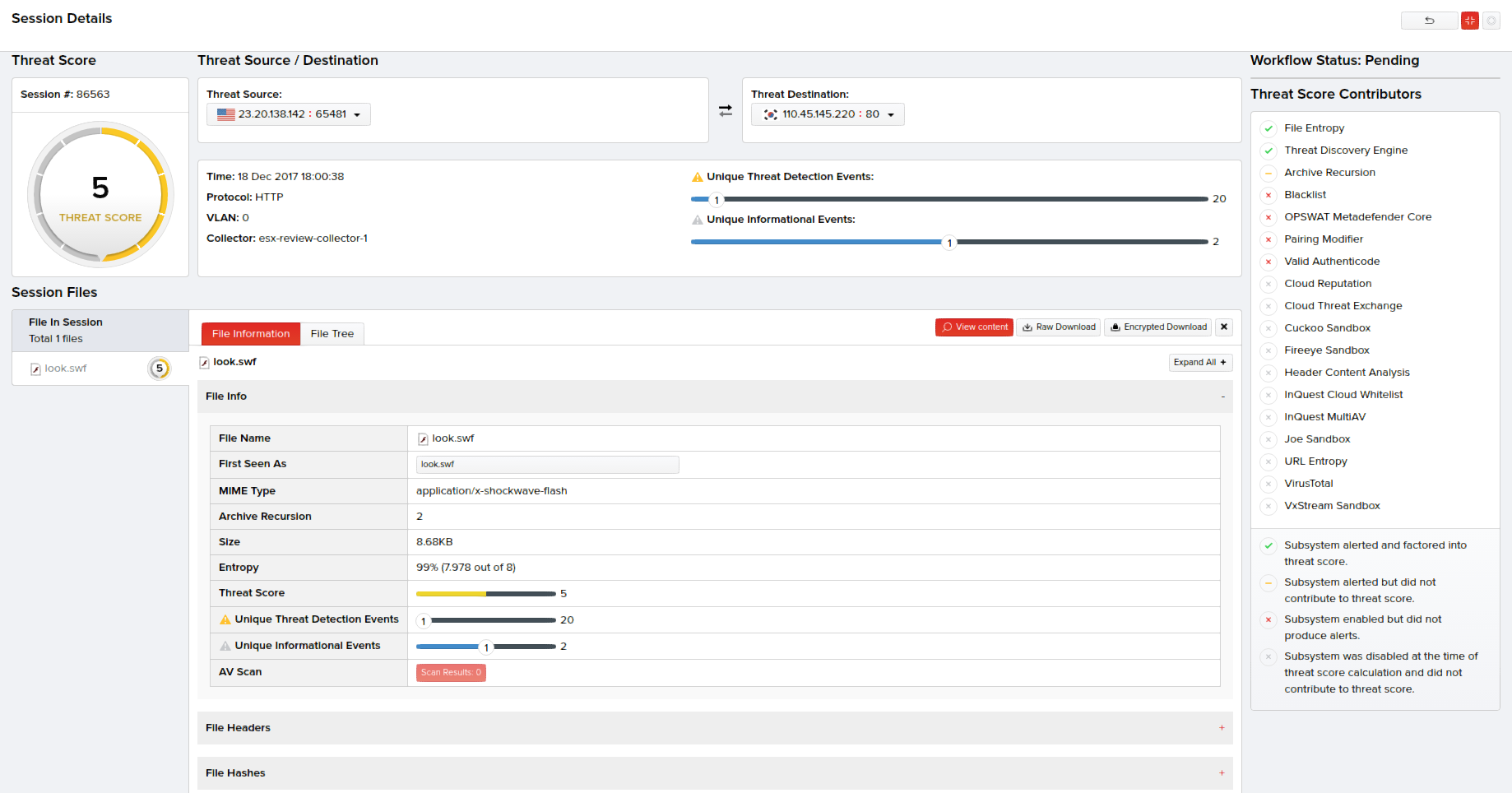
Viewing Session Details
Details of a session can be viewed by clicking View in the Actions column corresponding to that session. This page displays the TCP session ID, instance when the PCAPs were captured off the sessions, threat score, source and destination IP address of the session, protocol involved, VLAN, files transferred, details on the protocol header and the transferred files along with the option to view the file(s) content and download them as raw or encrypted file(s).
The Threat Score Contributors column on the right side of this screen provides information on the subsystems contributing to the overall threat score of the content and alert generation.