Introduction
MetaDefender ICAP Server can be installed in Kubernetes (K8S), the components that are defined in the MetaDefender ICAP Server helm chart stored in https://github.com/OPSWAT/metadefender-k8s/tree/main/helm_charts/icap
This guide explains the different components that we propose for MetaDefender ICAP Server to run in K8S properly.
K8S Component Architecture Options
There will be deployed different services depending on how the cluster is accessed, and will be used to work with MetaDefender ICAP Server.
These are the possible combinations:
MetaDefender ICAP Server Service + Ingress
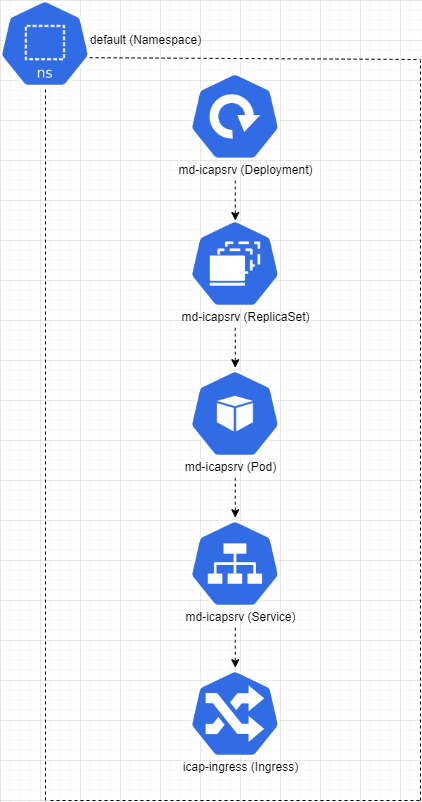
md-icapsrvserviceicap-ingressservice (Optional)
Overview Architecture of K8S Component
Components Table
| Component Type | Component Name | Description |
|---|---|---|
| Ingress | icap-ingress | Ingress component for accessing to the md-icapsrv service from outside of the cluster. In case you have an external load balancer, it is optional, as you can setup an ingress controller for any of the CSPs load balancers. |
| Deployment | md-icapsrv | Define what replicas and containers needed for md-icapsrv . |
| Service | md-icapsrv | Represent a single point to access to all the pods for md-icapsrv . |
| Pod | md-icapsrv | Contains all containers needed for running MetaDefender ICAP Server application. |
Diagram of Components
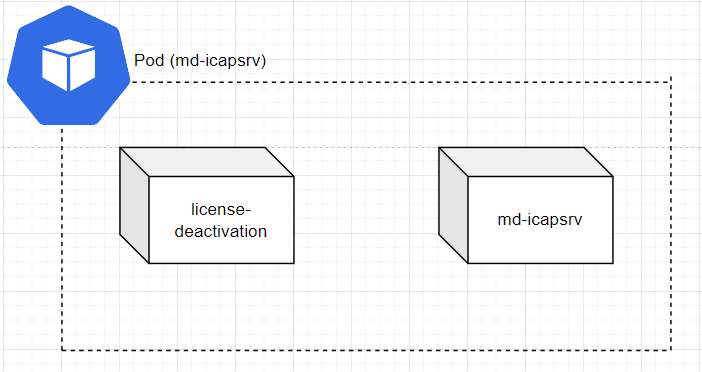
Containers Design
Containers Description
- App Container: Main container of the application that hosts all the logic to activate the service with the license.
- Sidecar Container: Will handle the deactivation of the license key in case there is any failure with that pod.
Secrets Configuration
- mdicapsrv-api-key: API key autogenerated in case it is not indicated in the helm chart
- mdicapsrv-cred: Admin user and password autogenerated in case it is not indicated in the helm chart
- mdicapsrv-license-key: MetaDefender ICAP Server activation key is needed to activate the pods.
TLS Configuration
When you enable TLS in file values of the helm chart, need to prepare two secrets on your Kubernetes cluster.
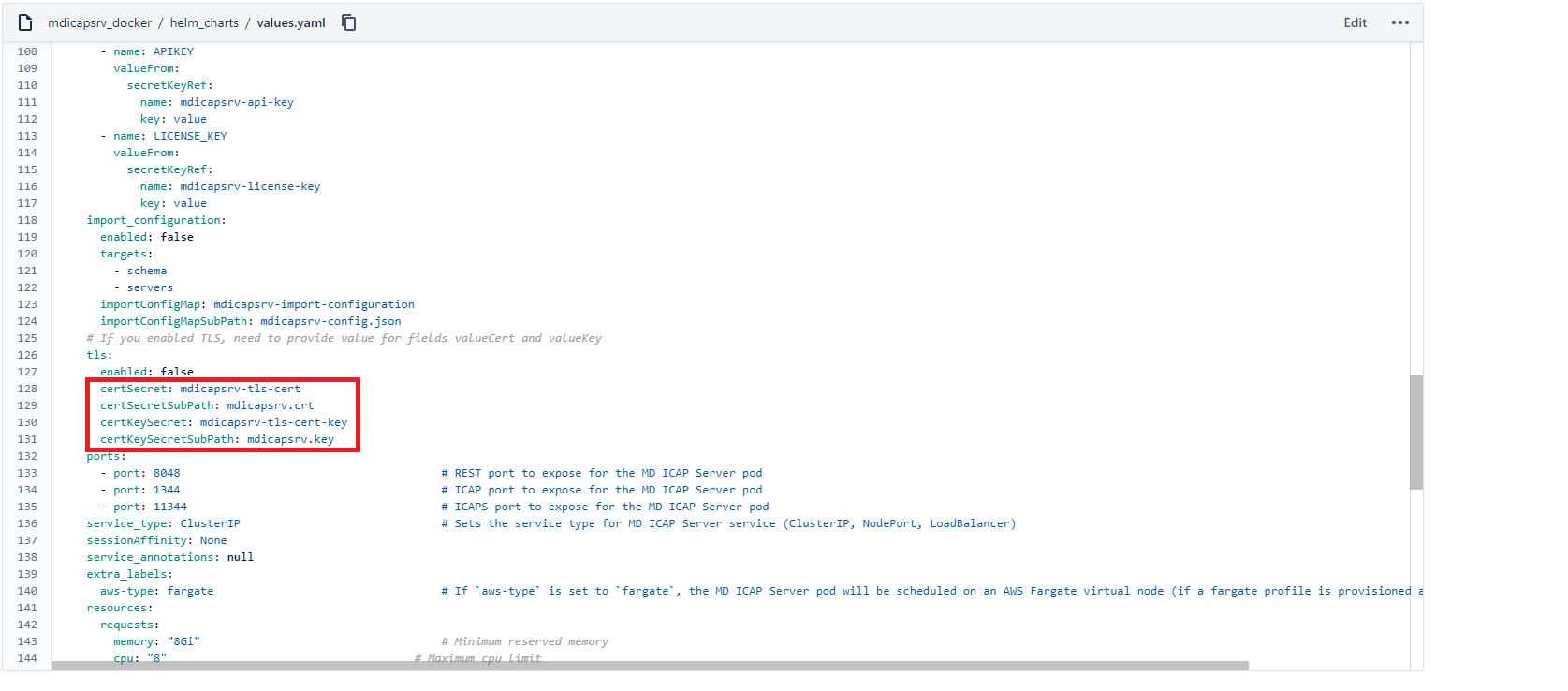
Override the secret name for your certificate and private key created on K8S.
Licensing Configuration
Every time a pod of md-icapsrv is created, it will create a deployment ID attached to that pod, so it is automatically activated. In case the pod anyhow goes down, it will be automatically deactivated thanks to a side container installed that will make a call to the OPSWAT Activation Server.
The md-icapsrv pods use the secrets mdicapsrv-license-key to generate a deployment id and activate that pod. In case of failure on activation the app container will restart until that secret is properly set up with a license key with enough activations.

