MetaDefender IT-OT Access can be enhanced by using Omnissa Unified Access Gateway (UAG) to check device compliance before letting a user access to a VDI. Learn more about this integration.
By integrating MetaDefender IT-OT Access into Omnissa Unified Access Gateway solutions, administrators are able to check remote devices for:
- Vulnerabilities - Detect vulnerabilities on endpoints through installed applications and operating systems.
- Enhanced Compliance - Get greater visibility into the status of installed security applications such as hard disk encryption and system information, or such as password protection, to ensure devices are compliant with existing policies.
- Unwanted Applications - Detect and remove non-compliant or unwanted applications such as peer-to-peer applications from a remote device.
- Advanced Threat Detection - Utilizing two methods of advanced threat detection, MetaDefender IT-OT Access helps identify potential threats that existing anti-malware software might not protect against.
- Portable media scanning and access control - Protect organizations against threats from portable media on the endpoints, a common attack vector for malware.
- Anti-screen capture - Prevent keyloggers and advanced malware from accessing sensitive data.
- Screen capture protection - Prevent unauthorized or accidental screenshots and recording by users, VDI, web collaboration tools, and malicious applications.
Documents:
You can set up a MetaAccess account to manage up to 50 devices with free of charge. Start Trial Now
Frequently Asked Questions
1. Why does a user can access VDIs even their device is non-compliance through web access?
The Horizon Endpoint Compliance feature with OPSWAT MetaDefender IT-OT Access is currently supported for Omnissa native Horizon clients. With HTML Access, no policy check is made. However, you can turn on or off the disable HTML access setting on Omnissa UAG to either fully deny or allow access.
To deny all HTML access, you can follow the below steps:
- Log into Omnissa UAG console admin
- Open Edge Service Settings > Horizon Settings

- Turn on "Disable HTML Access" setting
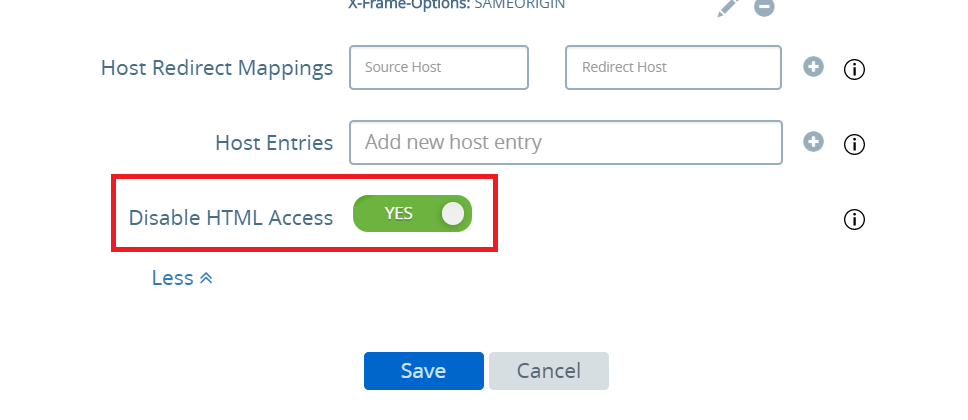
- Click SAVE
2. Does this integration support Android users?
This integration may work on some Android devices if the Omnissa Horizon app and OPSWAT Mobile app can retrieve a device's MAC address. This requires the device to install OPSWAT Mobile app and be enrolled it to the MetaDefender IT-OT Access account.
3. Does this integration support iOS users?
From Omnissa UAG version 3.8+, it now supports iOS users. The user experience will be different compared with the user experience on PCs.
4. What domains and IP addresses should I allowlist on my firewall/proxy?
If your devices or your UAG sits behind a firewall or a proxy, you need to allowlist domains to allow UAG and devices talk to OPSWAT MetaDefender IT-OT Access. See more details at How do I configure MetaDefender Endpoint to work with a proxy or outbound firewall?
You need to configure UAG outbound connection to Internet which is on the Internet facing NIC to able to contact the OPSWAT MetaDefender IT-OT Access servers, please refer Omnissa documents for more details. Please note that the domain gears.opswat.com is not assigned static IP addresses. If you need static IP addresses to configure on UAG/firewall, we have domain dapi.opswat.com as an alternative domain for gears.opswat.com and it's assigned static IP addresses.
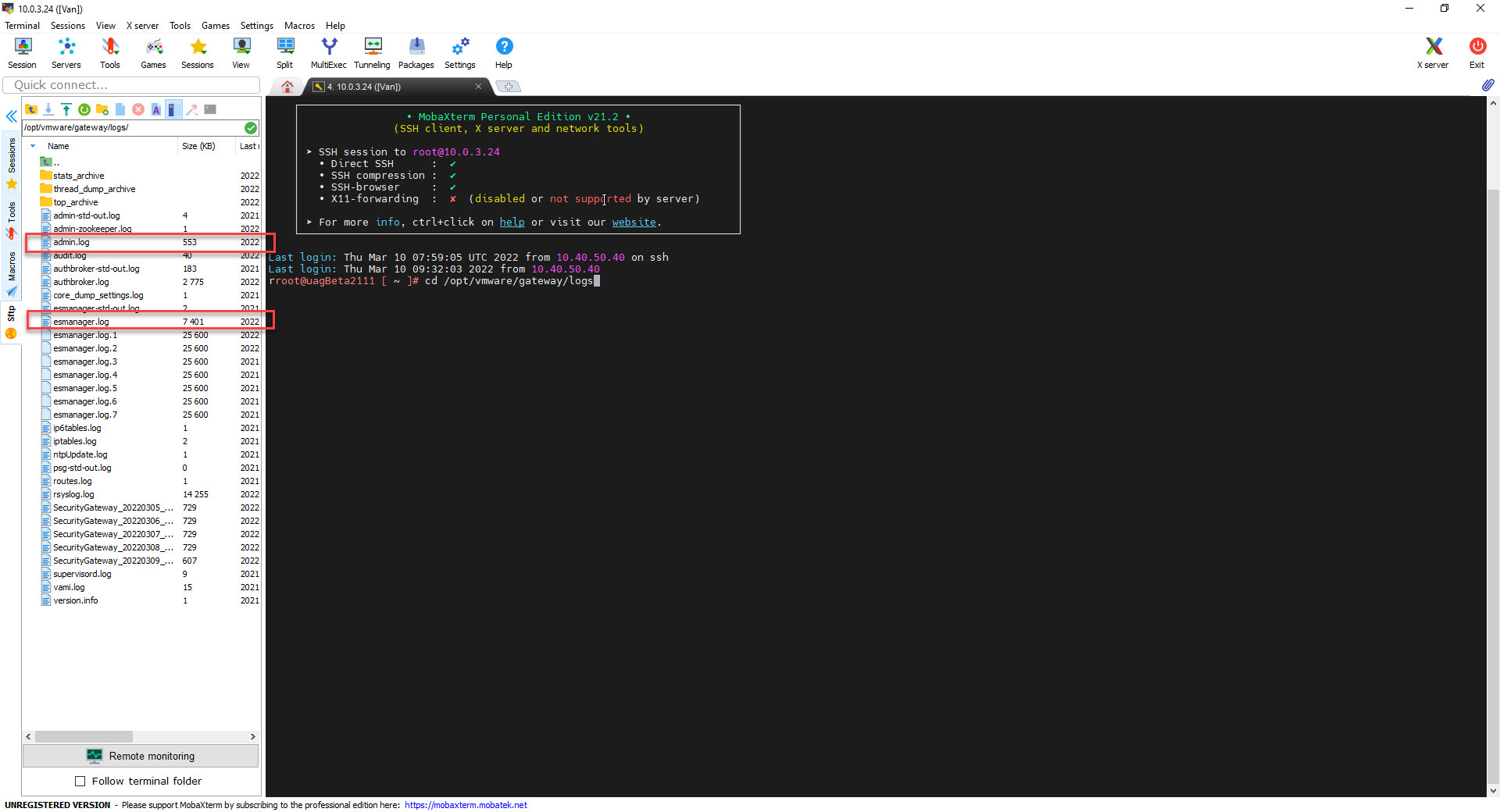
5. Where can I find On-Demand MetaDefender Endpoint's log when it's triggered from Horizon Client?
You can find On-Demand MetaDefender Endpoint's log at:
- Windows: C :\Users<username>\AppData\Local\VMware\VMware Horizon View Client\Code Cache<uuid>\ while Horizon Client session is still on.
- macOS: /Users/<User name>/Library/Logs/Gears/<License Key>/GEARS-Ondemand.log
For MetaDefender Endpoint log:
- User login to machine User with admin role:
C:\Program Files (x86)\VMware\VMware Horizon View Client\Code Cache <License Key>\logs\gears-ondemand.log

- User login to machine User with user_user role:
C:\Users<user_admin>\AppData\Local\VMware\VMware Horizon View Client\Code Cache<License Key>\logs\gears-ondemand.log

Horizon: C:\Users\van.truong\AppData\Local\VMware\VDM\logs

For Omnissa UAG log: esmager.log and admin.log
6. Why couldn't Horizon Client distribute On-Demand MetaDefender Endpoint on devices?
The minimum version of Horizon Client that supports this feature is 5.4 and make sure you upload an on-demand client to Unified Access Gateway v3.9+.
If a user runs an older version, please upgrade Horizon Client to a version 5.4.
If a user already run Horizon Client 5.4.x, please contact Omnissa support to troubleshoot the issue.
To restrict minimum Horizon Client running on a device, you can refer this guideline on Omnissa.
7. Why couldn't Horizon Client distribute On-Demand MetaDefender Endpoint on macOS devices?
This is a known issue if you are running Horizon Client version 5.4.x and previous versions and your administrators do not add any parameters into CLI on UAG. As a workaround solution, you should add parameters to the CLI on UAG, such as /log 1 as the below screenshot to fix it.
For more information about parameters available on On-Demand MetaDefender Endpoint, you can visit On-Demand MetaDefender Endpoint CLI
8. How to know On-Demand MetaDefender Endpoint has been downloaded by Horizon Client?
First step: Please check the settings:
- Client Key and Client Secret
- Hostname
- Path To Executable
- For macOS: Please follow format: OPSWAT_GEARS_Client_<very_long_filename>.app/Contents/Resources/opswat-gears-od
- Example: OPSWAT_GEARS_Client_3445-a44 ***ba.app/Contents/Resources/opswat-gears-od
The second step: Check Horizon Client has successfully downloaded OPSWAT On-Demand MetaDefender Endpoint
For macOS:
- Check the folder: /Users/<Username>/Library/Application Support/VMware Horizon View Client/Code Cache/<uuid> there is a .zip file
- Check the .zip file to see the correct information such as server name, license key, agent version

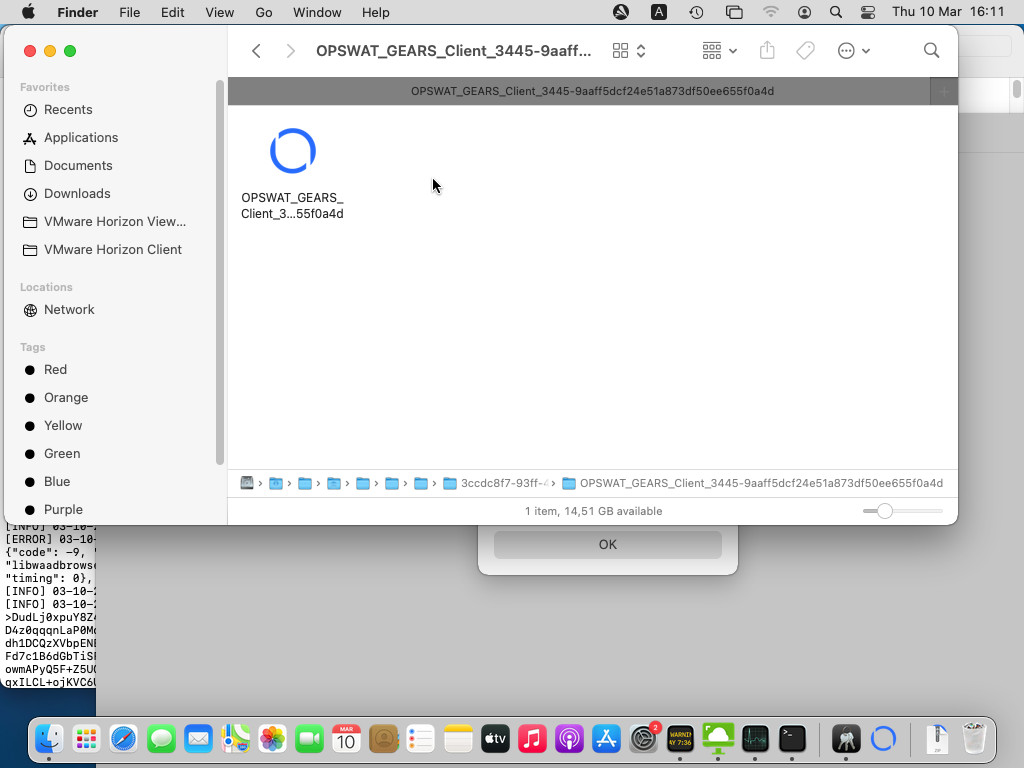
If failed: check in Endpoint Compliance Check Provider Settings and re-upload agent correctly
For Windows: check the On Demand file to see the correct information such as server name, license key, agent version
If user login to machine User with admin role, please check:
- C:\Program Files (x86)\VMware\VMware Horizon View Client\Code Cache
- C:\Users<user_admin>\AppData\Local\VMware\VMware Horizon View Client\Code Cache
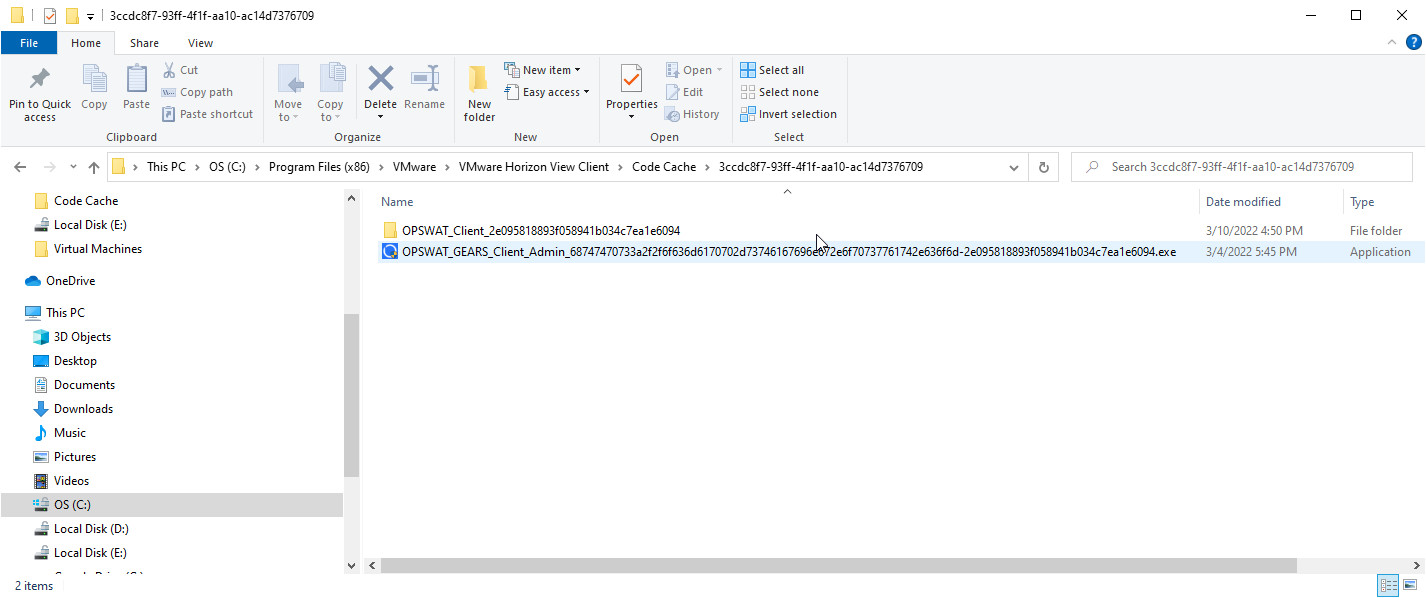

If user login to machine User with user_user role
- C:\Users<user_user>\AppData\Local\VMware\VMware Horizon View Client\Code Cache
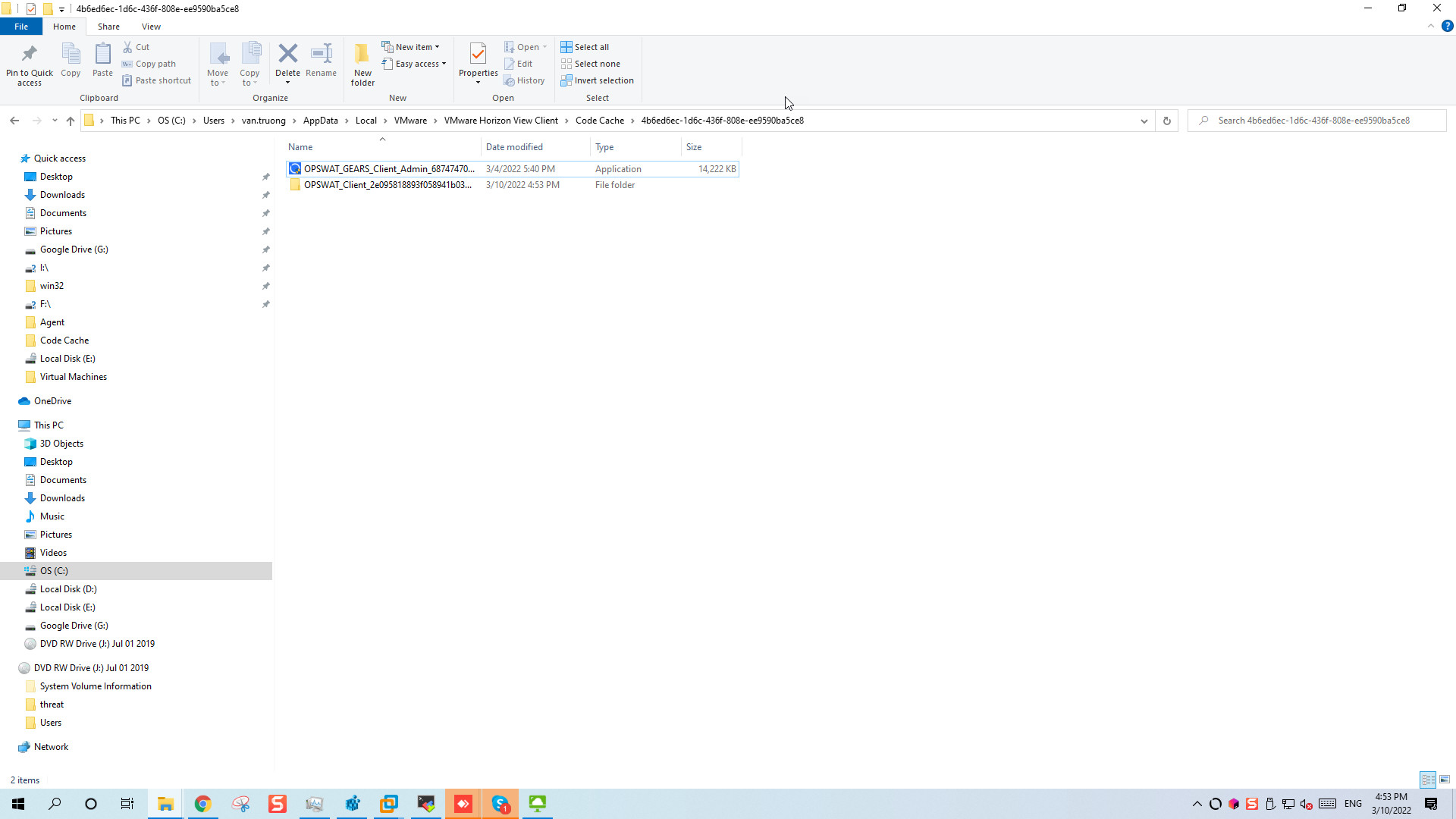
9. How to check Horizon Client start with On-Demand MetaDefender Endpoint?
For macOS:
Check in Activity Monitor for process opswat-gears-od when connecting to Horizon Client
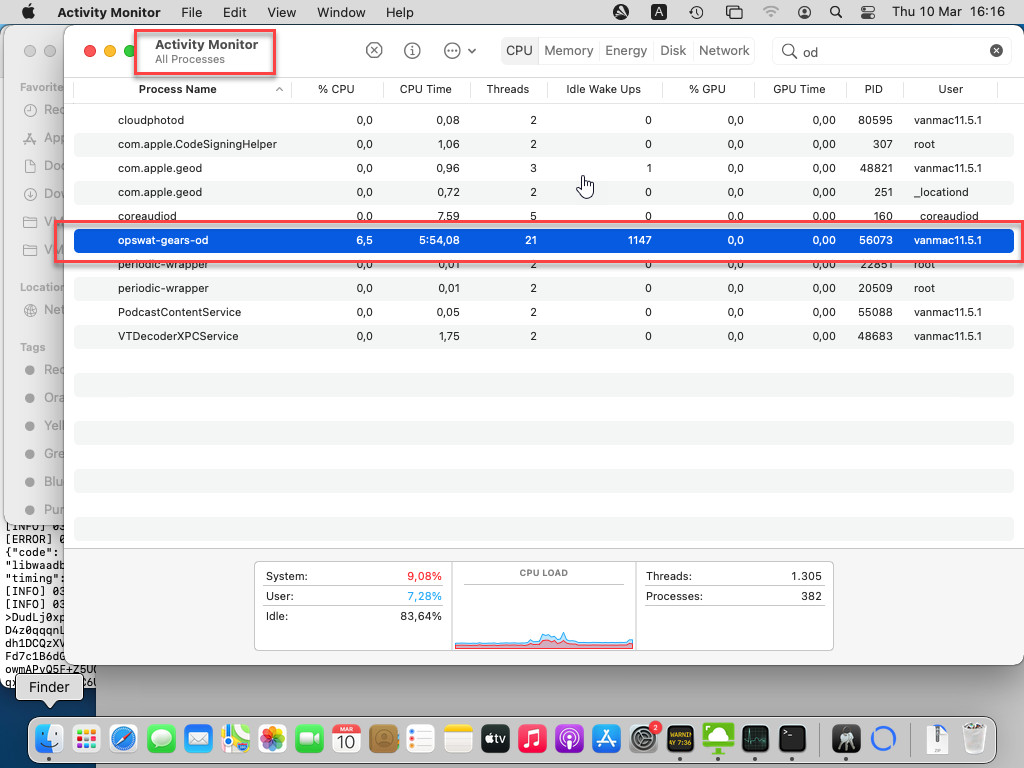
If failed:
- Add execute permission chmod +x opswat-gears-od
- Try run opswat-gears-od
- Check Path To Executable on Endpoint Compliance Check Provider Settings (UAG setting)
For Windows:
Check at Task manager for process OnDemand when connecting to Horizon Client
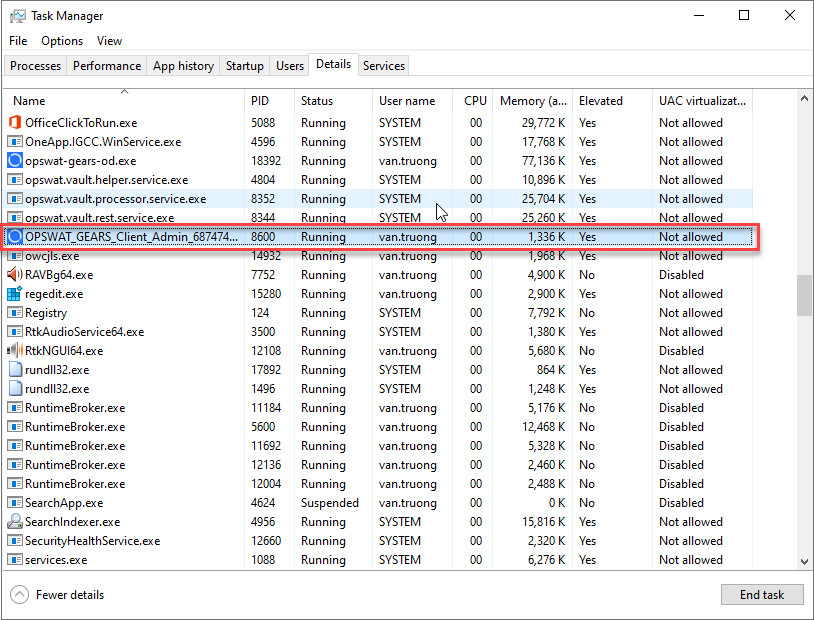
If failed:
- Try run opswat-gears-od
- Check Path To Executable on Endpoint Compliance Check Provider Settings (UAG setting)

