Title
Create new category
Edit page index title
Edit category
Edit link
Peripheral Media Protection
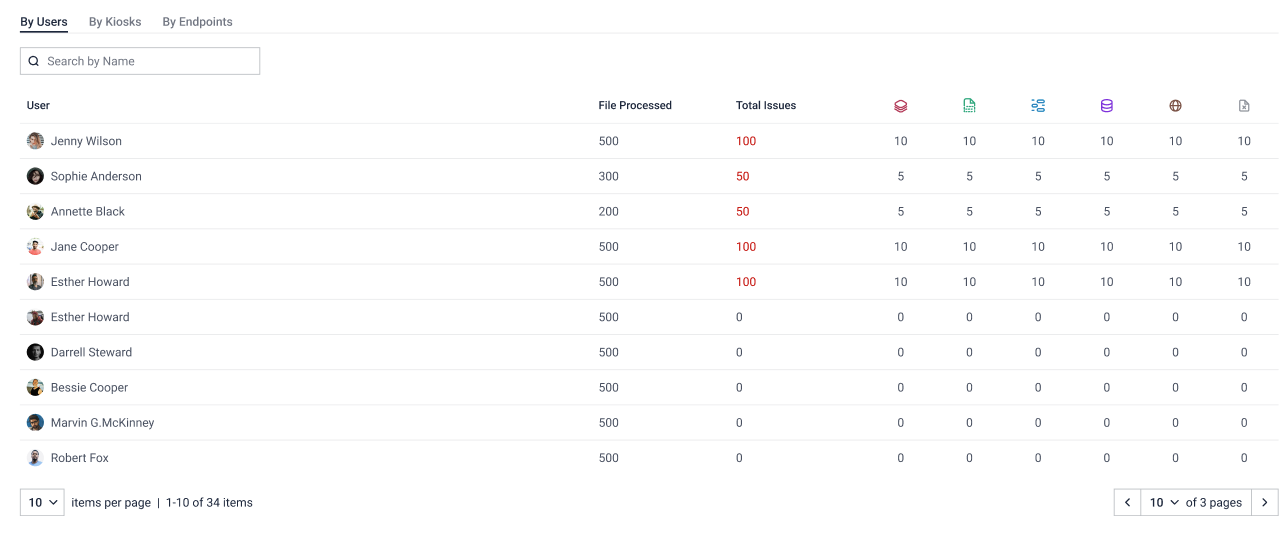
The Peripheral Media Protection Dashboard offers a detailed overview of the current security status and activities related to peripheral media protection. It showcases key metrics such as the number of active and out-of-date kiosks, monitored and unmonitored endpoints, and the outcomes of recent scan sessions. Additionally, it provides detailed threat detection statistics, including zero-day and COO detections, and categorizes protection activities by users and devices: Kiosks and endpoints. This information is essential for assessing the effectiveness of security measures and identifying areas that need attention.
You can access the dashboard from the left navigation menu by going to Dashboard > Peripheral Media Protection
This page serves as a central hub for monitoring and managing the security status of peripheral media and endpoints. Here's how to use it effectively
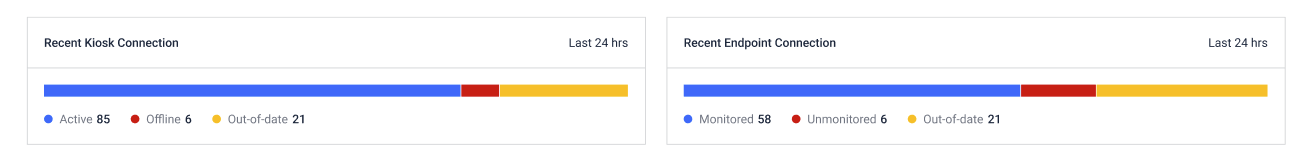
Connection status
- Recent Kiosk Connection: Shows the connection status of kiosks over the last 24 hours. Verify the status of kiosks to determine which ones are active, offline, or out-of-date
- Recent Endpoint Connection: Displays the connection status of endpoints over the last 24 hours, including monitored, unmonitored, and out-of-date endpoints.
This section is essential for ensuring that all kiosks and endpoints are adequately secured and up to date.
Data in other charts and tables on this dashboard is aggregated from Kiosks and Endpoints in specific groups and timeframe above those charts and tables.

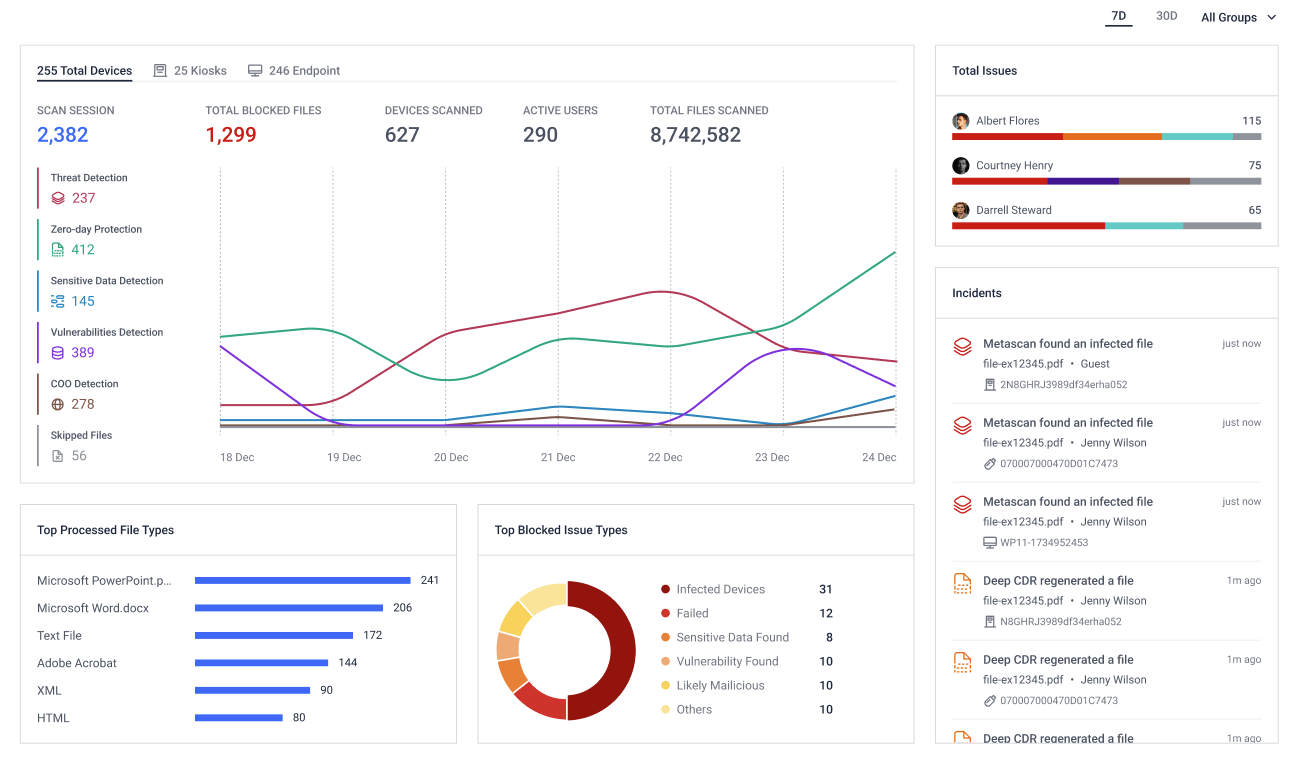
Peripheral Media Protection overview
By regularly reviewing this dashboard and chart, you can maintain a clear understanding of your security posture, quickly identify any vulnerabilities, and take necessary actions to ensure all devices and endpoints are secure and safe from threats.
- Scan session: The number of scan sessions that performed from all/specific groups of Kiosks and Endpoints
- Total Blocked Files: The number of files that have been blocked during scans.
- Devices Scanned: The number of devices that have been scanned.
- Active Users: The total number of users who have conducted scanning sessions.
- Total Files Scanned: The number of files that have been processed during scans.
- Total Issues: Displaying users with the most security issues.
- Incidents: This section displays the most recent issues detected across all devices.
- Top Processed File Types: provides a visual representation of the number of times different file types have been processed by the system
- Top Blocked Issue Types: display a visual overview of the various types of issues that have been blocked by the system
Detection Activities
Categorizes protection activities by users, kiosks, and endpoints, providing insights into where and what threats were being detected.