Title
Create new category
Edit page index title
Edit category
Edit link
Version 5.7.4
| Release date | Scope |
|---|---|
| October 7th, 2024 | MetaDefender Email Gateway Security 5.7.4 focuses on usability improvements and bug fixes. |
New & improved
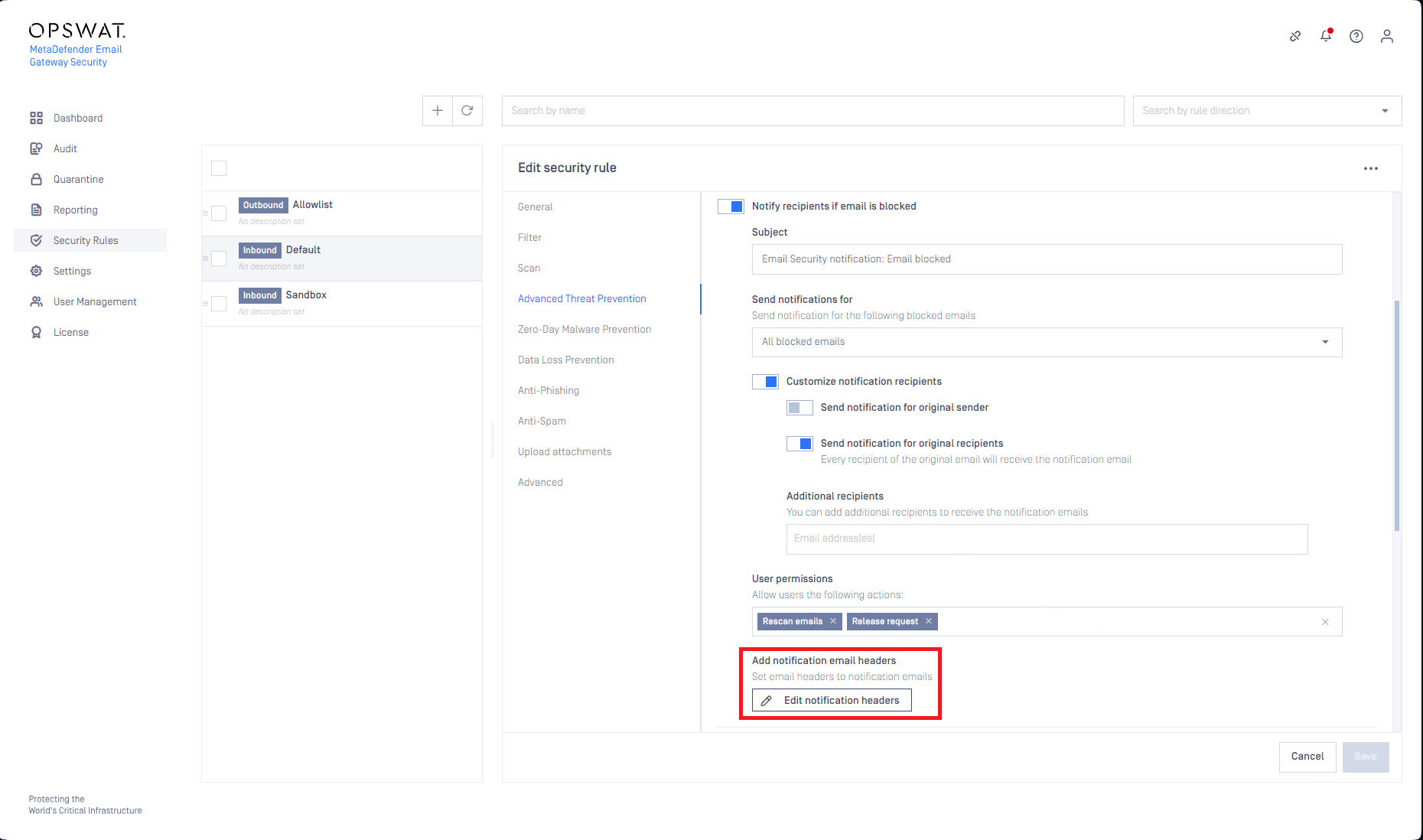
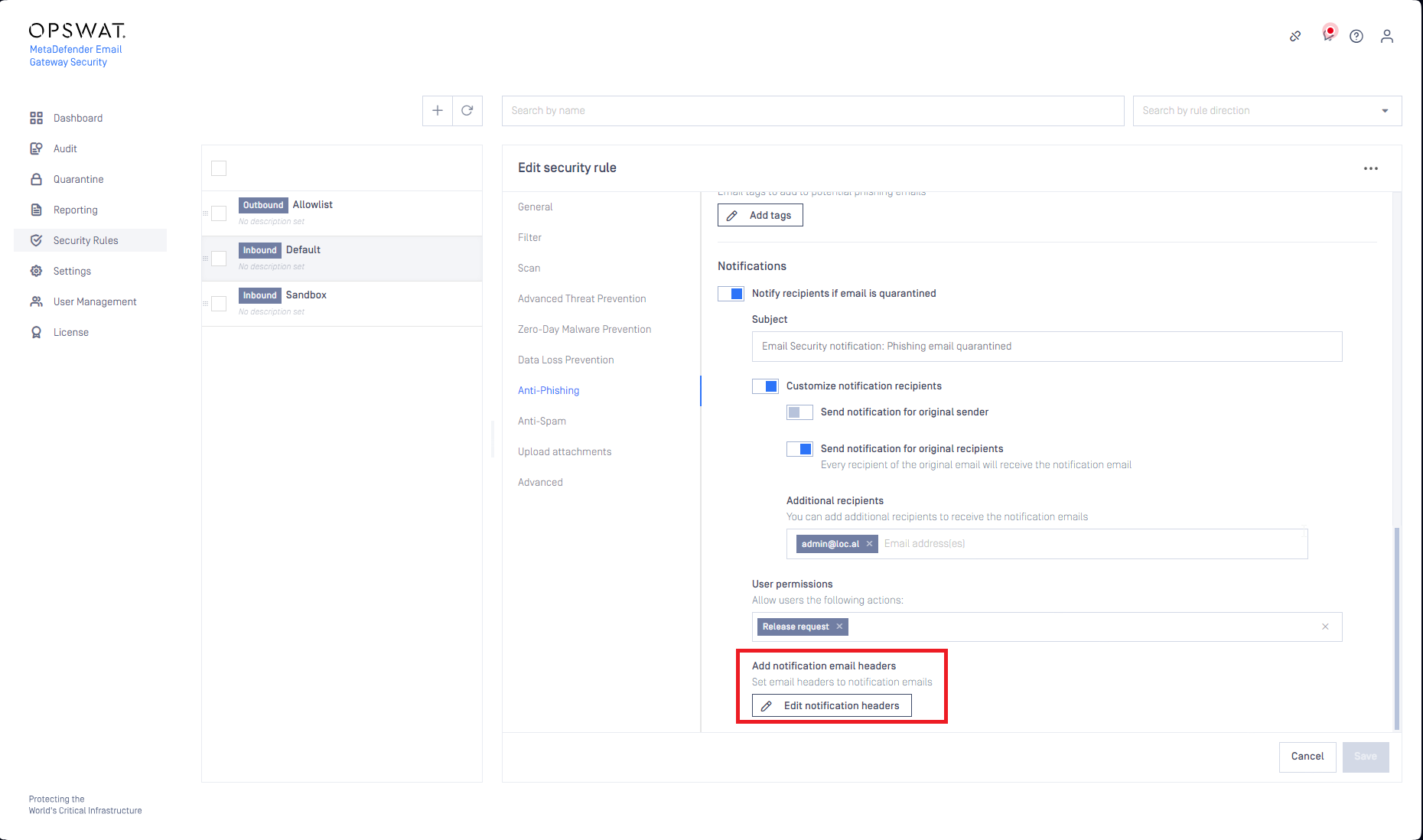
Custom headers to notification emails
It is now supported to add custom headers (X-headers) to notification emails in each use-case where notification emails are supported (Advanced Threat Prevention, Anti-spam, Anti-phishing).
With custom headers administrators can customize the handling of emails delivered by Email Gateway Security at later steps in the email processing flow (e.g. external quarantining, etc.).
For details see Advanced Threat Prevention, Anti-phishing and anti-spam and Additional email headers.
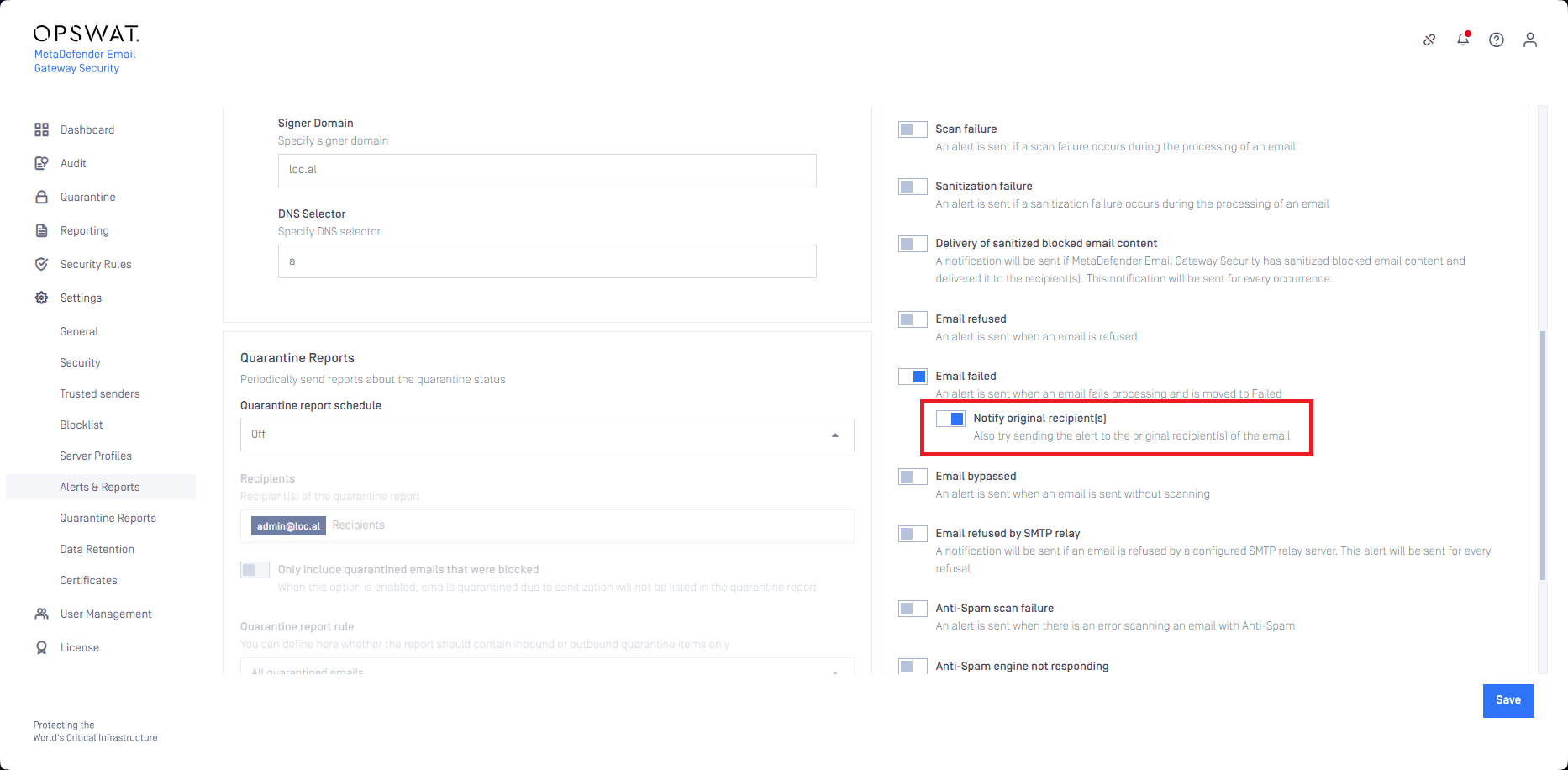
Notify the end user when email failed
Email Gateway Security can now be configured to send an alert to the original recipient of the email when the email ends up to be failed (e.g. fails to scan, fails to sanitize, etc.) to process.
This way recipients can be alerted that there is an email destined to them that is withhold by Email Gateway Security.
For details see the Email failed entry in Alerts.
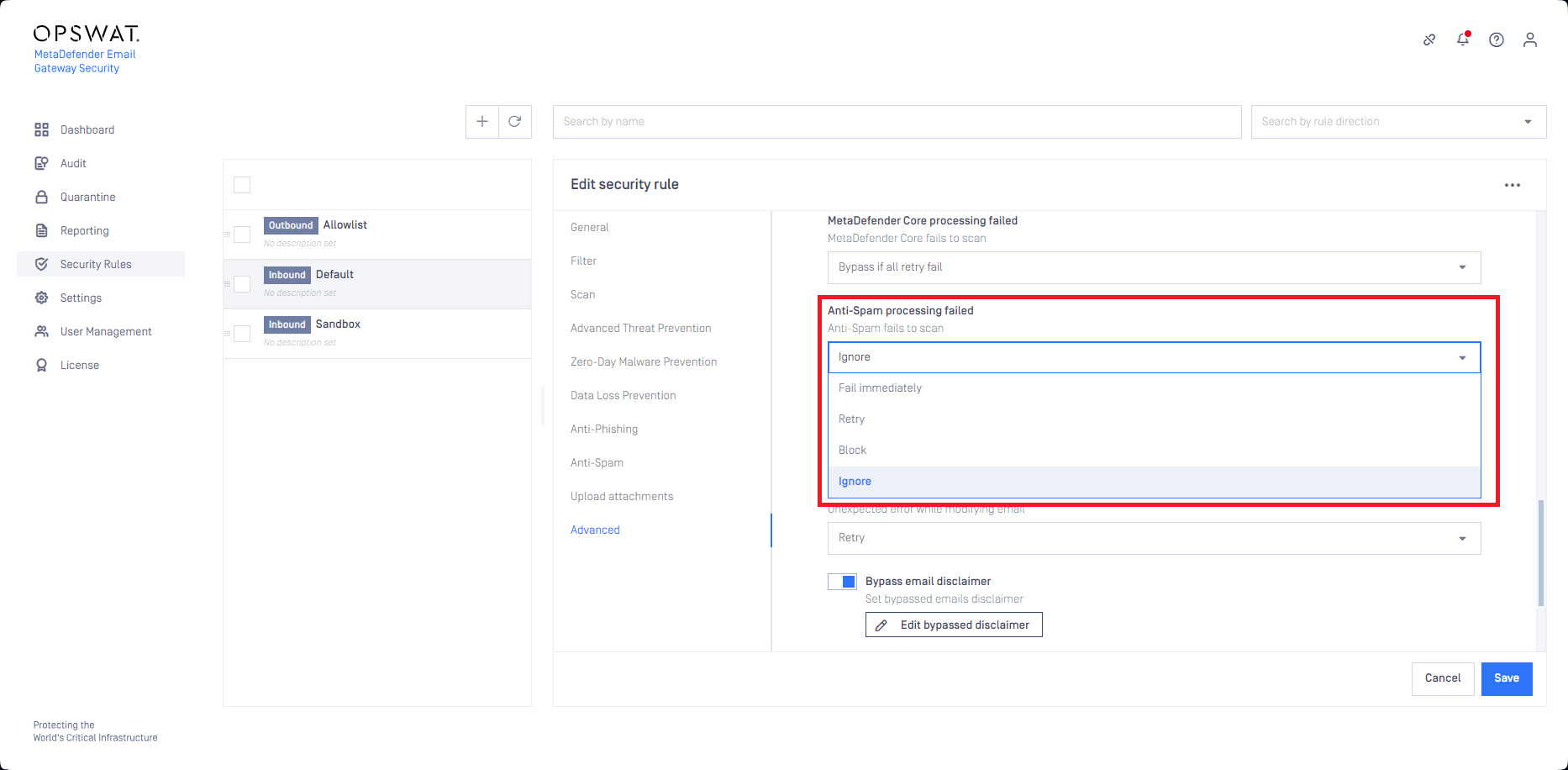
Anti-spam engine failure retry settings
The Anti-spam engine failure cases are now handled by the standard retry mechanism. The standard error handling can be customized for each security rule under the Advanced options.
For details see Retry and the Override settings section in Advanced.
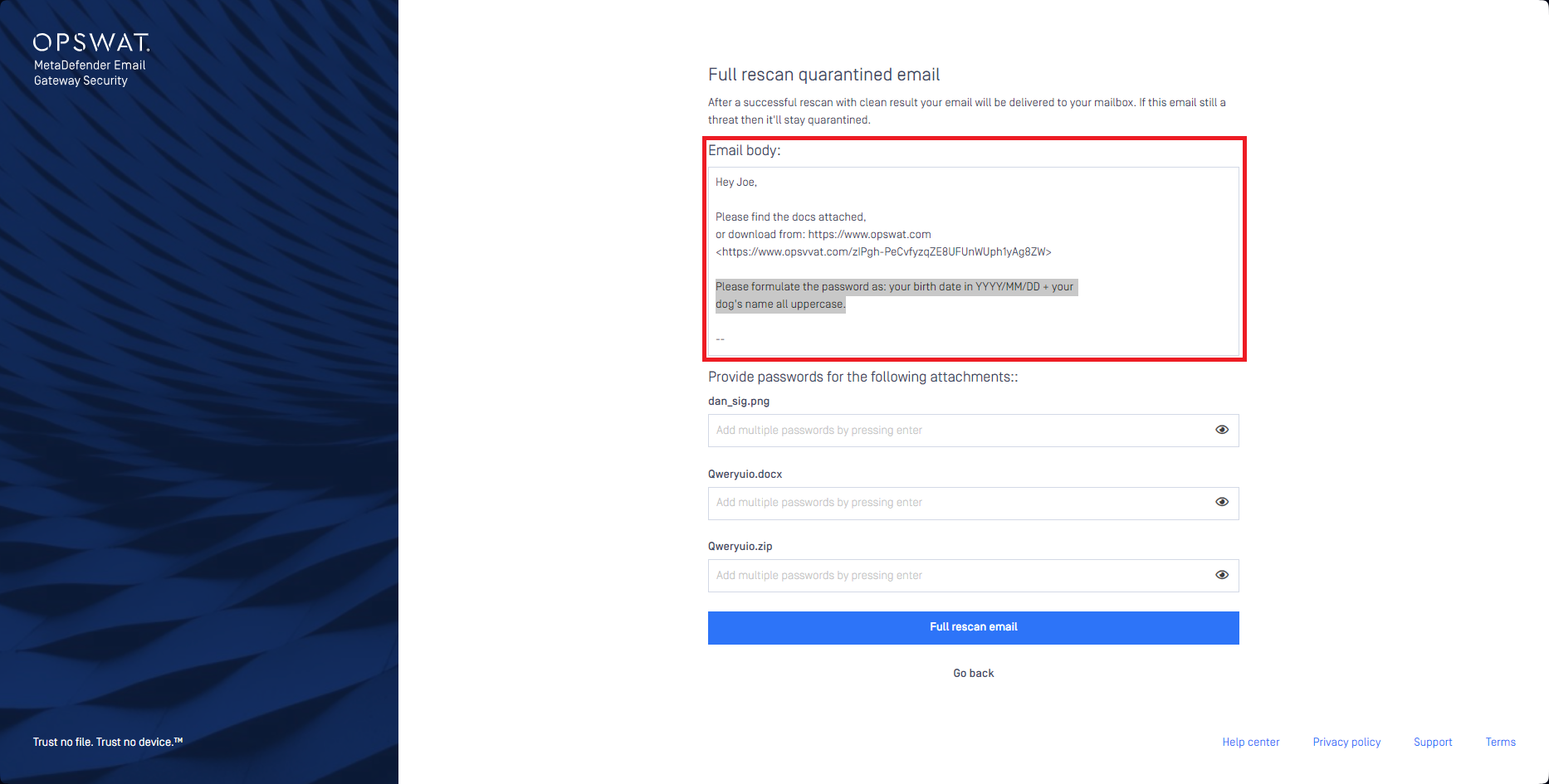
View email body for encrypted attachments
Email Gateway Security can now display the email body in the rescan page for encrypted attachments. The idea behind this feature is that sometimes it is the email body that contains the instructions how the password needs to be formulated.
For details see the Encrypted attachments section in Advanced Threat Prevention.
Reverse DNS lookup on sending IP address
Anti-phishing checks can now include a reverse DNS lookup of the sending IP address, besides the SPF and DKIM checks.
In case the sending IP address does not belong to a domain (any domain), the email can be classified as Possible Phishing or Phishing based on the settings.
For details see the domain_lookup_level entry in Registry configuration / Internal.
Customize behavior for SPF & DKIM results
It is now configurable what SPF and DKIM results are treated as Known Phishing, Possible Phishing or benign_._ Previously Fail and Soft fail SPF results and Invalid DKIM result were hardwired as Known Phishing (everything else as benign), which is still the default.
For details see the dkim_phishing_verdicts, dkim_possible_phishing_verdicts, spf_phishing_verdictsand spf_possible_phishing_verdicts entries in Registry configuration / Internal.
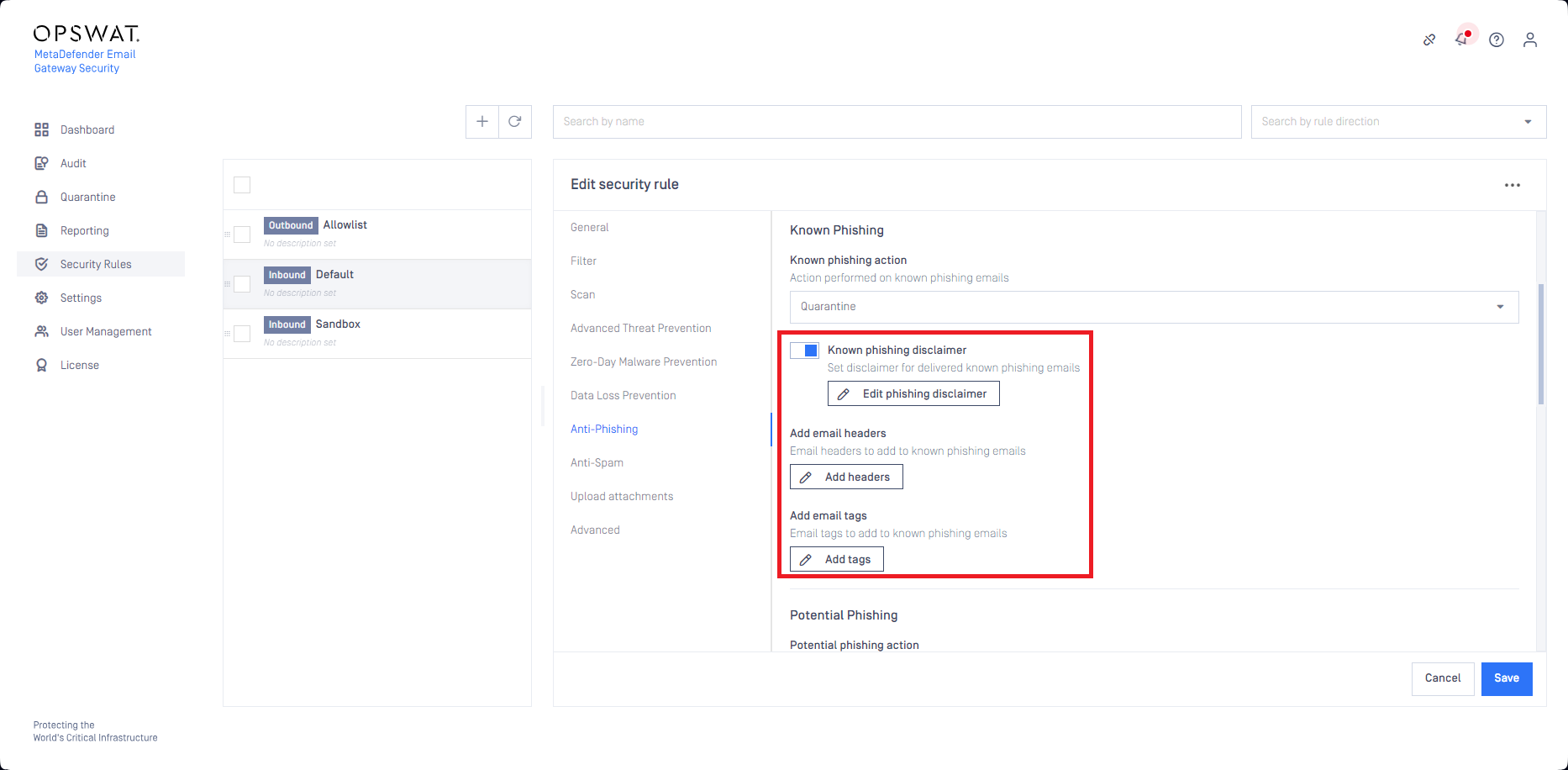
(Potential) spam and phishing disclaimers
Disclaimers are now supported for known and potential spam and phishing emails when such an email finally gets delivered either because the spam or phishing action is set to deliver for the email or the email got quarantined and delivered by a rescan.
For details see the Disclaimers section in Anti-phishing and anti-spam.
Anti-spam and anti-phishing defaults
For new installations, defaults of anti-spam and anti-phishing settings have been tuned to provide
- better visibility into emails that were blocked and quarantined,
- lower rate of false (positive or negative) spam or phishing detections.
The new defaults are:
Anti-phishing
Probability level: 6
Known Phishing
Known phishing action: Quarantine
Add email tags: Phishing
Notify recipients if email is quarantined: enabled
- User permissions: Release request
Known phishing disclaimer: enabled
Potential phishing
Potential phishing action: Deliver
Add email tags: Potential_phishing
- Add to subject: enabled
Possible phishing disclaimer: enabled
Anti-spam
Probability level: 7
Classify marketing/bulk email as possible spam: enabled
Known spam
Known spam action: quarantine
Add email tags: Spam
Notify recipients if email is quarantined: enabled
- User permissions: Anti-malware rescan
Known spam disclaimer: enabled
Potential spam
- Potential spam action: deliver
- Add email tags: Potential_spam
- Add to subject: enabled
New Quarantine view created
- Name: Phishing release request
- Classification filters:
- Phishing
- Release requested
The following quarantine reports preconfigured:
Report name & Subject: Phishing release requested - daily digest
- Report type: admin
- Recipients: the admin email address configured in the wizard
- Reporting frequency: daily
- Include emails classified as: Phishing, Release requested
Report name & Subject: Phishing - hourly digest
- Report type: user
- Reporting frequency: hourly
- Include emails classified as: Phishing
- Exclude emails classified as: Malware detected, Malicious behavior
- User permissions: Request release
Report name & Subject: Spam - hourly digest
- Report type: user
- Reporting frequency: hourly
- Include emails classified as: Spam
- Exclude emails classified as: Malware detected, Malicious behavior
- User permissions: Rescan, Anti-malware rescan, Request release
Existing systems that get upgraded to Email Gateway Security 5.7.4 from an earlier version are not affected by this change, those will keep the exiting configuration.
Spam & phishing disclaimers for rescan
Disclaimers are now supported for known and potential spam and phishing emails when such an email finally gets delivered because the email got quarantined and delivered by a rescan. The idea behind this behavior is that this way recipients can be alerted about the potential risks in spam and phishing emails even after being delivered by a rescan.
For details see the Disclaimers section in Anti-phishing and anti-spam.
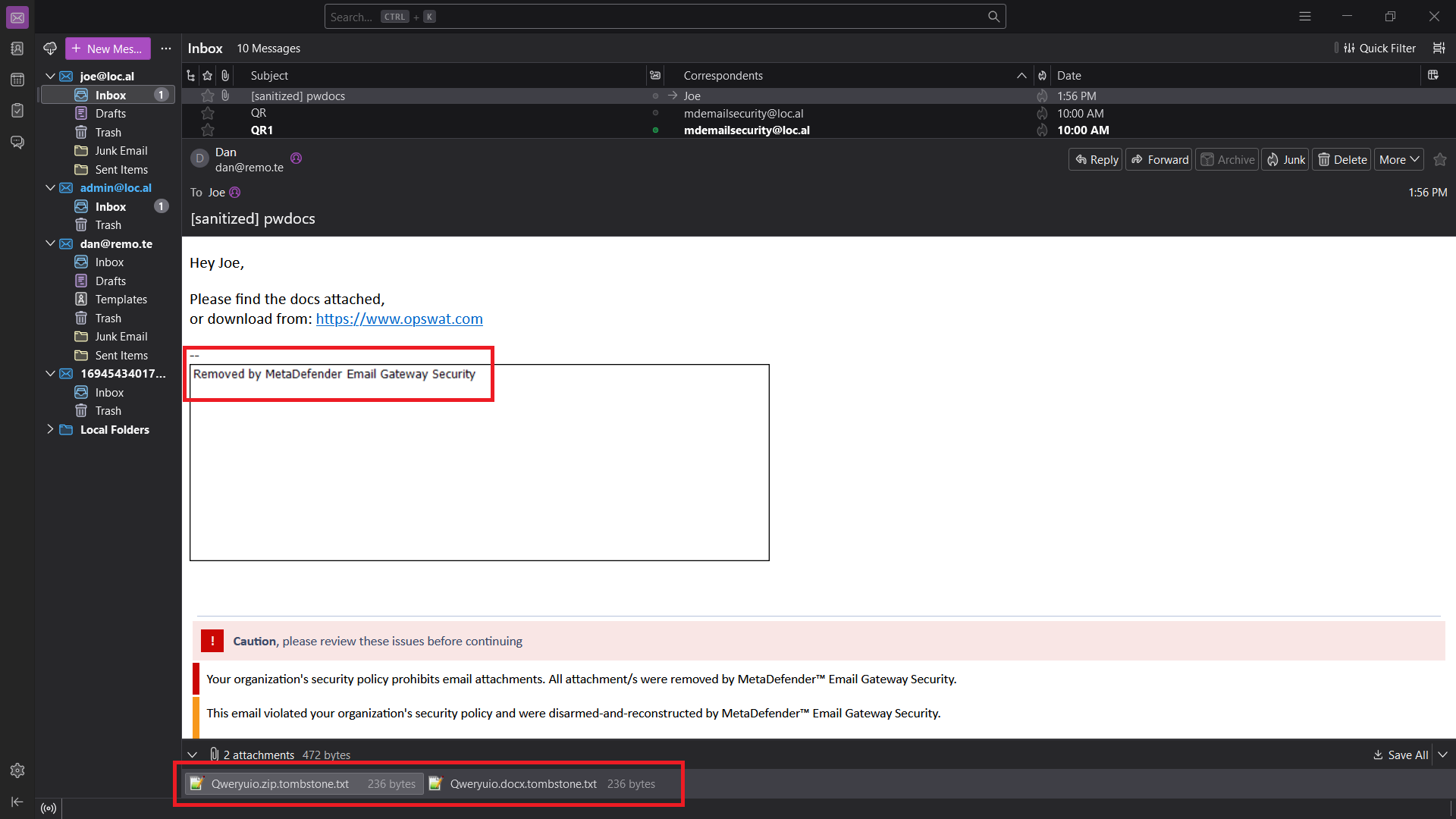
Replace blocked files with tombstones
For every use-case where Email Gateway Security might remove attachments, namely when in a security rule
- Handling of the email is set to Delete blocked contents or
- Remove attachments is enabled
it is now supported to replace the removed attachment (both inline and regular attachments) with tombstone files.
For details see the Tombstone files section in Advanced Threat Prevention.
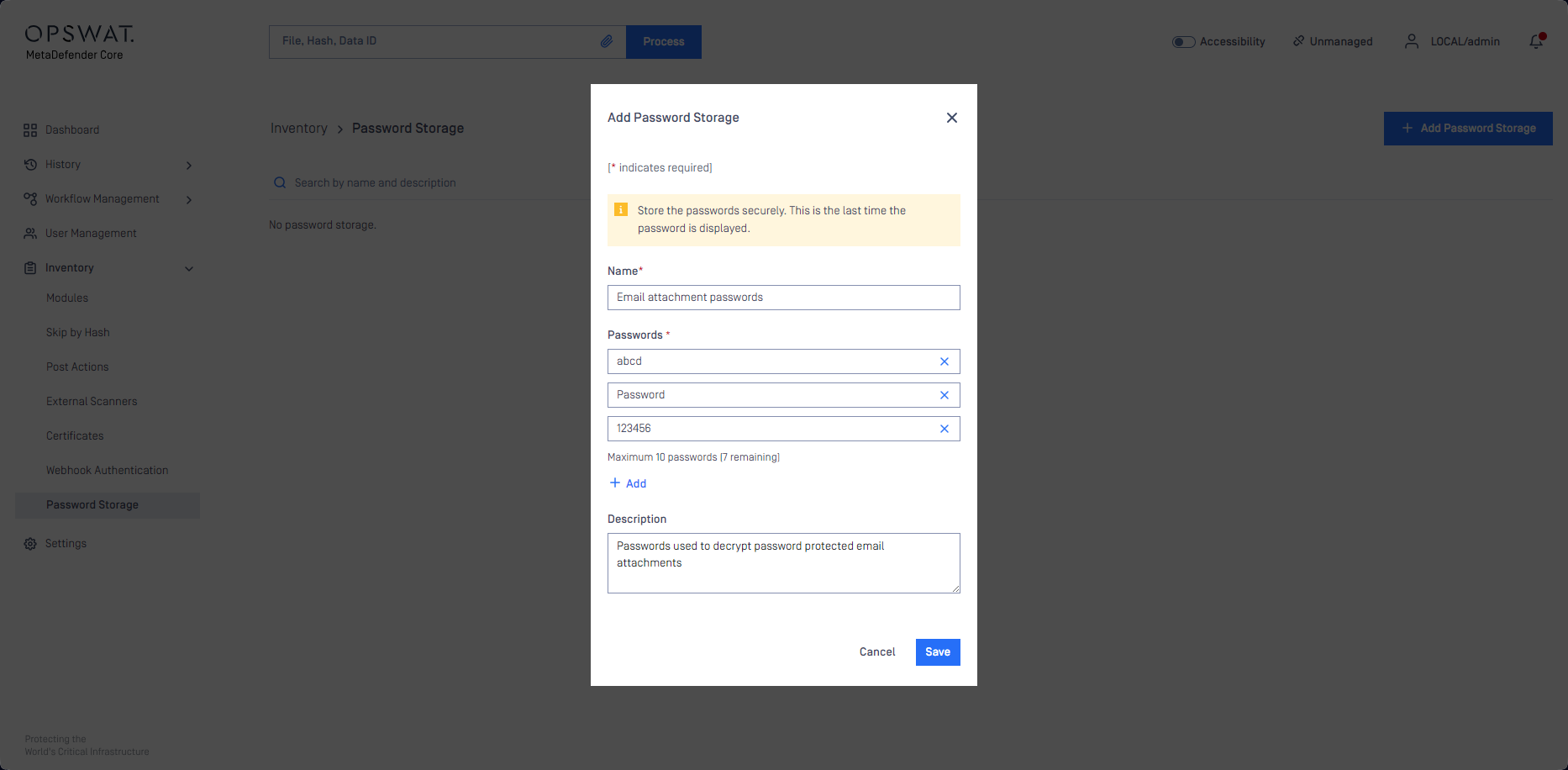
Password storage
From MetaDefender Core version 5.12.0, password storage is supported in Core workflows. When Email Gateway Security is integrated to Core using a workflow where password storage is configured, then Core will attempt to decrypt encrypted attachments using the passwords configured in the Core workflow. This way encrypted attachments may be processed automatically without the need to extract the password from the email body or to request the password from the recipient.
For details see the Password storage subsection in the Encrypted attachments section in Advanced Threat Prevention.
Bug fixes
Remove 0 byte attachments
Email gateway security now removes even 0 bytes attachments when Remove attachments is enabled for the security rule.
Filename and password box
For certain TNEF (winmail.dat) encoded emails that contained encrypted attachments, the rescan page did not present the file name label and the password box due to character conversion errors.
Outbound resending loop
Outbound emails using MX record lookup ended up in endless Resending loop and fork when emails were destined to recipients in multiple domains.
Core workflows did not load
After upgrading from certain previous versions to MetaDefender Email Gateway Security 5.7.3, workflows of MetaDefender Core type server profiles did not load on the GUI resulting in never ending load of the workflow dropdown.
Errata
This section contains significant information discovered after the release.
SMTP server URI parsing error in Chromium browsers
With Chrome 130 (2024-10-15) in the V8 JavaScript engine, Chromium based browsers changed the URI parsing (Chrome 130 | Release notes | Chrome for Developers).
This change breaks Email Gateway Security’s SMTP server URI parsing in SMTP type server profiles. As a consequence it is not possible to add or modify SMTP servers of the SMTP type server profiles in the latest version of some Chromium browsers.
Even with correct URIs entered, the input field returns the error This field must contain a valid port number.
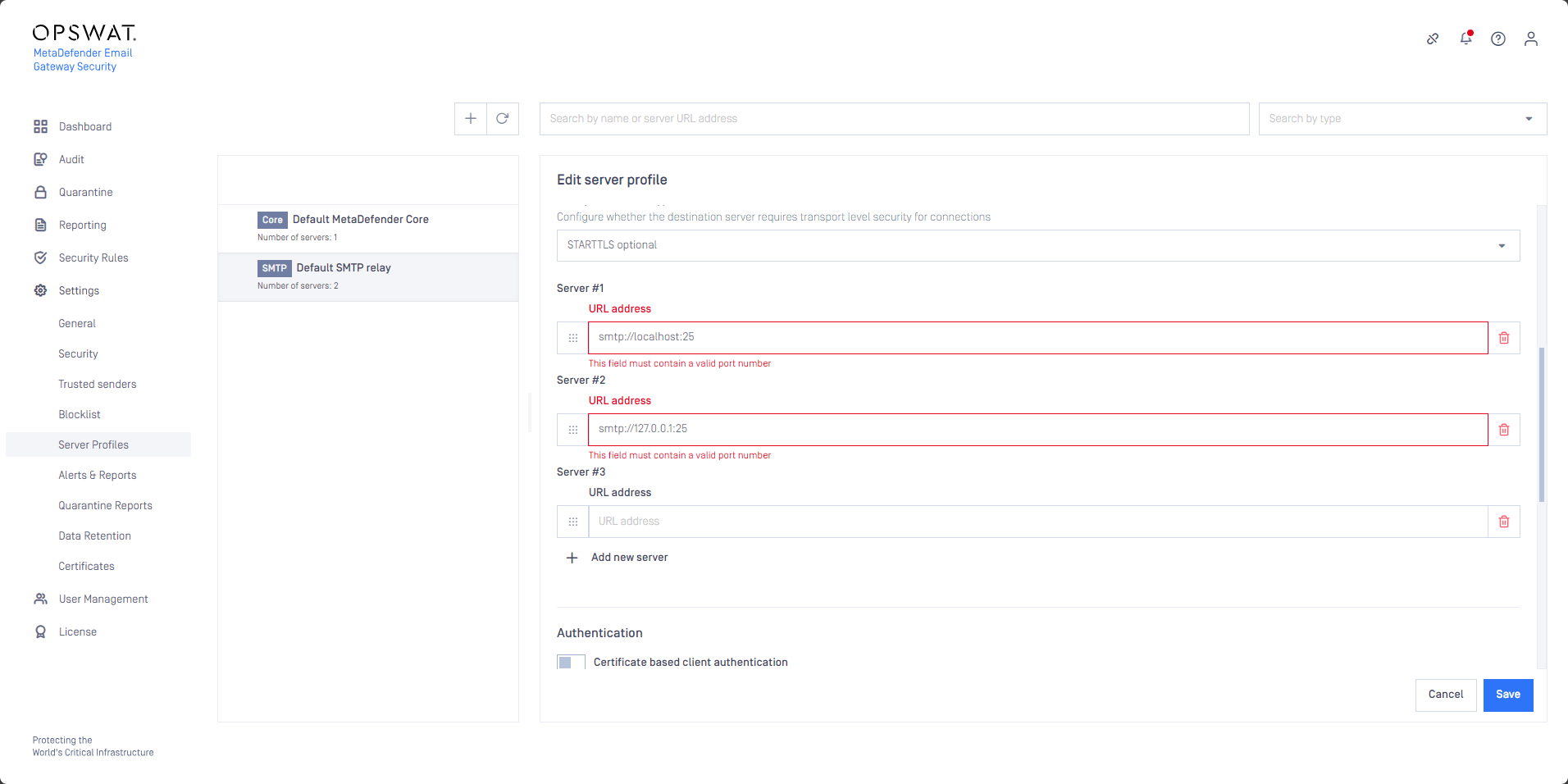
The issue has not been experienced with the latest version of some Chromium based browsers (Opera 114.0.5282.102) yet. It is, however, expected that other Chromium based browsers will apply Chrome changes soon (e.g. Microsoft Edge 130.0.2849.46 already has them).
Previous versions of Email Gateway Security (5.7.3 and earlier) are affected, too.
Workaround
Use a non-Chromium (e.g. Safari, Mozilla Firefox, LibreWolf, etc.) browser.

