Title
Create new category
Edit page index title
Edit category
Edit link
Version 5.7.1
| Release date | Scope |
|---|---|
| Mar 6th, 2024 | MetaDefender Email Gateway Security 5.7.1 focuses on new features, improvements and more. |
New & improved
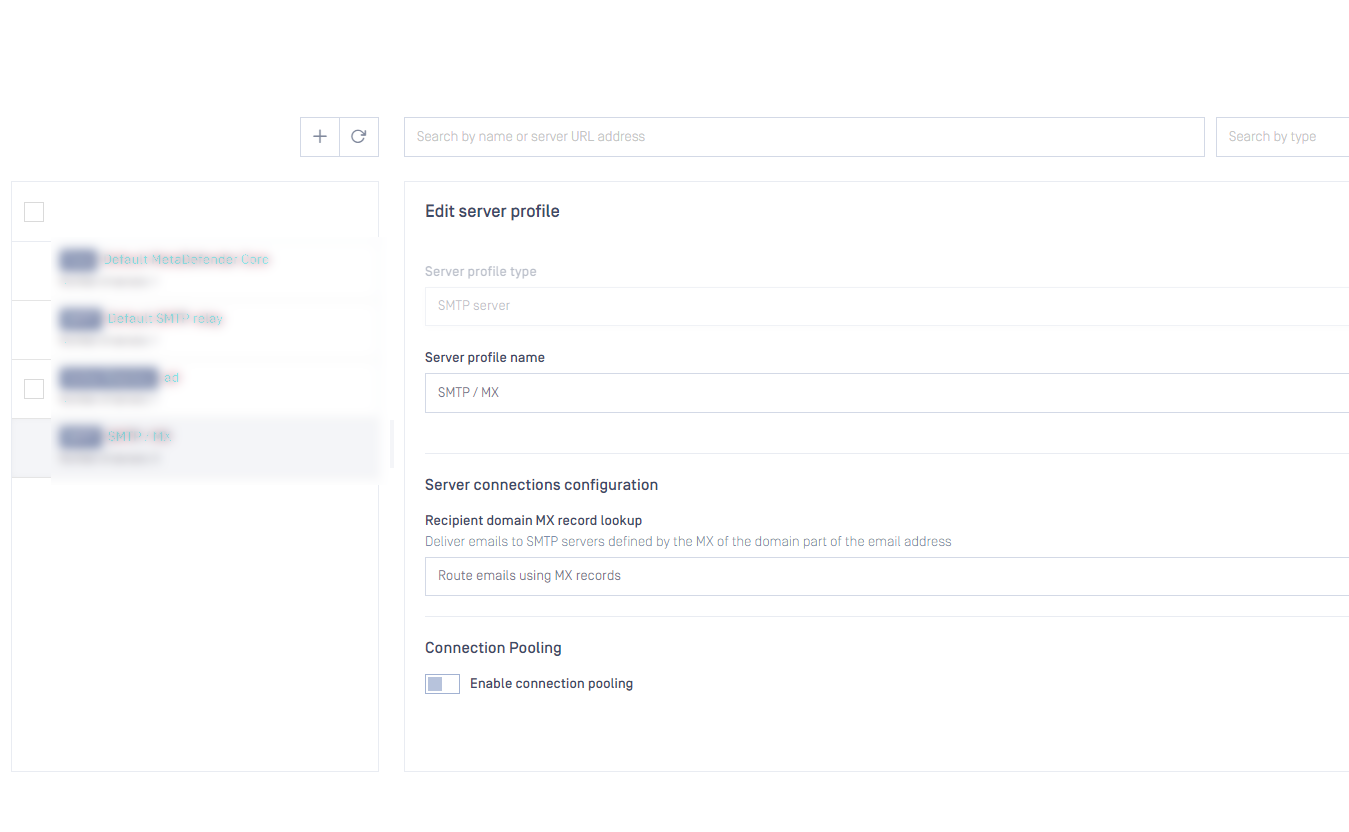
MX Record lookup support
It is now possible to configure SMTP server profiles to use DNS and lookup MX records when delivering emails. This allows easier handling of outbound email processing.
SOC log level
A new logging level (SOC) has been introduced to easier parse or export data to 3rd party aggregators, such as Syslog etc. The new logging level includes the following entries:
| Event | Log identifier | Variables |
|---|---|---|
| Email received | email.receive | email_id, __ip_address, sender, recipients, subject, processing_id, message_id |
| Email refused | email.refuse | ip_address, sender, recipient, response |
| Email scanned | email.scan | email_id_,_ sender, recipients, subject, processing id, message_id, classifications, scan_result, anti_spam_result, rule_name, scan_result_details, scan_result_urls |
| Email completed | email.complete | email_id, sender, recipients, subject, processing id, message_id, classifications, status |
| Email quarantined | email.quarantine | email_id, sender, recipients, subject, processing id, message_id, classifications |
| Email retrying | email.retry | email_id sender, recipients, subject, processing id, message_id, classifications, retry_count, next_retry |
| Email failed | email.failure | email_id, sender, recipients, subject, processing id, message_id, classifications |
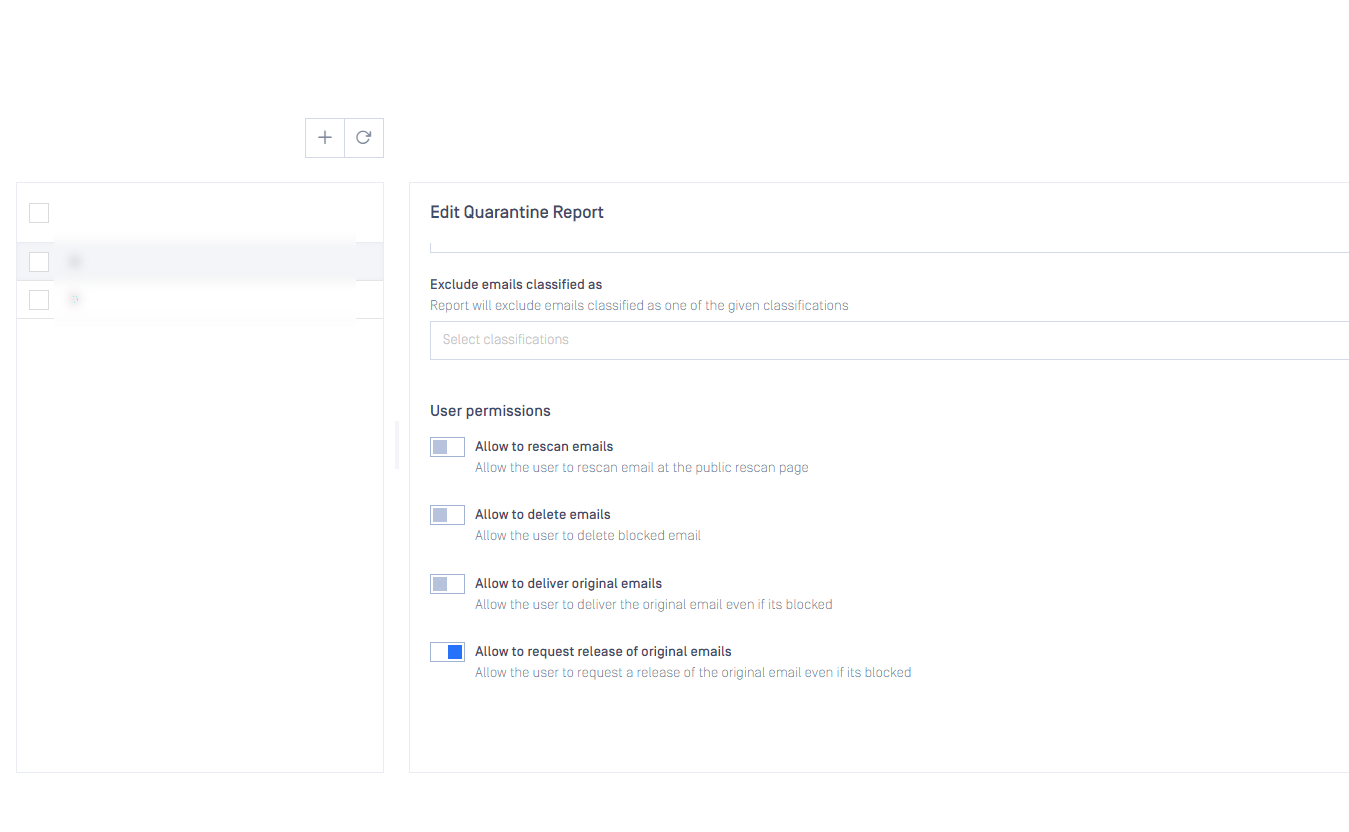
Request release action
It is now possible to configure quarantine reports to include a 'Request Release of original emails' action. This action will assign a 'Release requested' classification to emails. An administrator quarantine report can then be configured to aggregate a list of emails requested for release by end users.
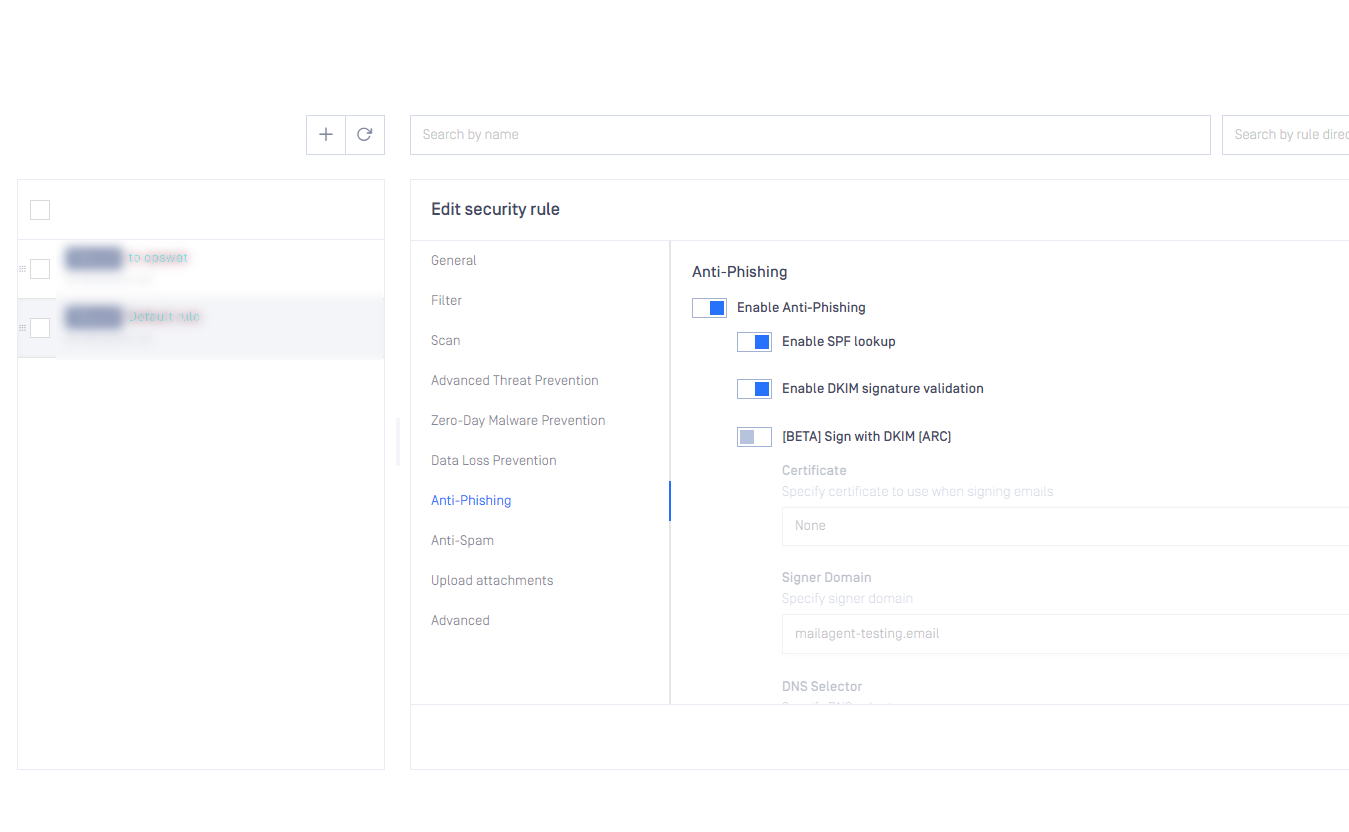
Enable/Disable DKIM & SPF in Security rule
It is now possible to control if DKIM and/or SPF record validation should be a part of the Anti-Phishing checks for specific security rules.
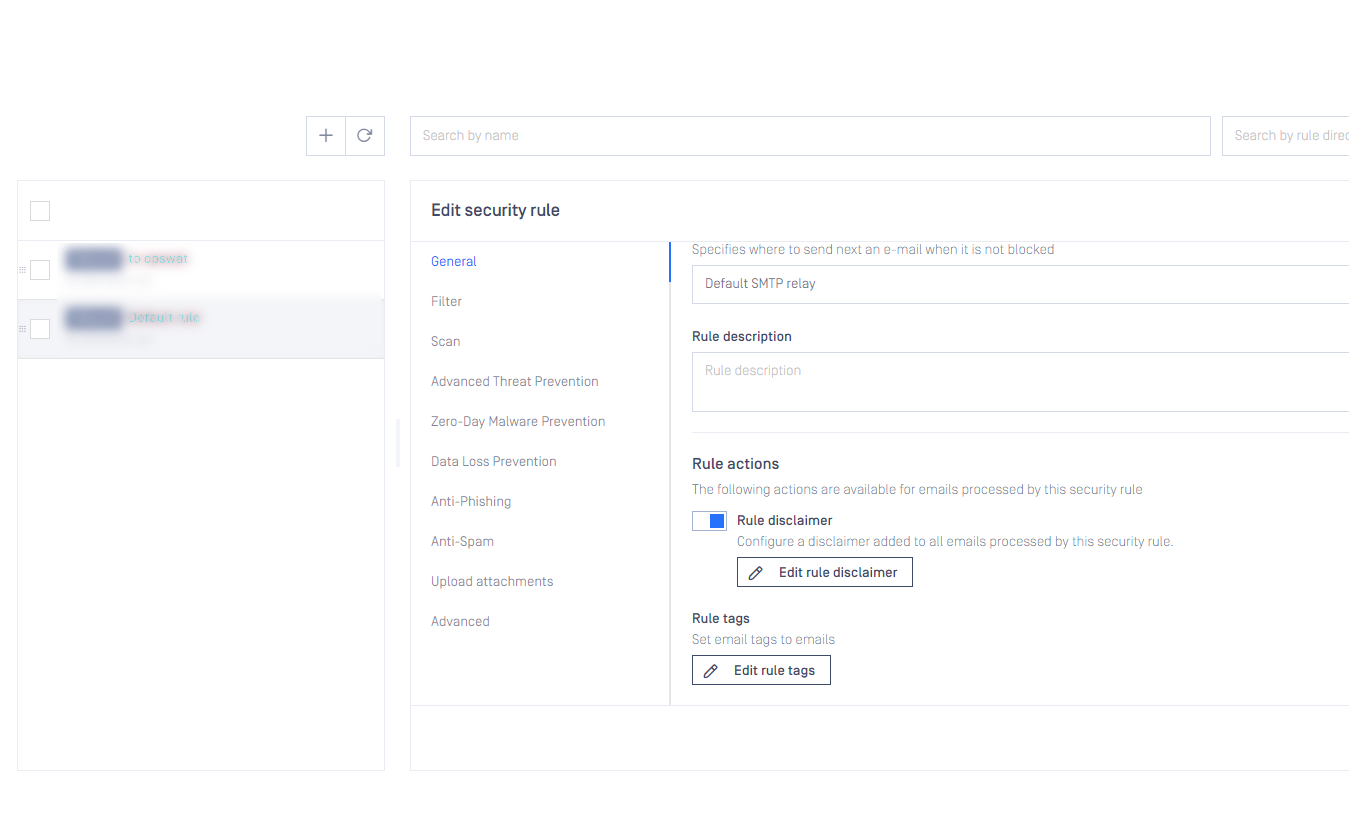
Rule disclaimer
It is now possible to configure a disclaimer added to every email processed by a specific rule, regardless of scan/sanitization results.
Other
Unicode support in Tag values
It is now possible to provide multi-byte characters as tag values. The length restriction is also increased to 30 characters.
Sanitization details variable
It is now possible to insert information about the sanitization actions performed on the email into a disclaimer. In any disclaimer, add the %[]sanitization_details[]% variable.
Test email/file1.doc: custom XML [removed],macro [removed], image [sanitized]
Test email/[body].txt: (No sanitization details available)
Test email/[body].htm: image [sanitized]
New Classification field variable
A new field variable %[]email_classifications[]% is now available for use in disclaimers and/or headers. For a list of available classifications, see Email classifications.
SANITIZED, NO_THREAT_DETECTED, URL_REWRITE
Field variable support in header values
Field variables can now also be used in header values. This allows inserting of dynamic data, such as sender, recipient, email classifications etc. into custom X-headers. For a list of available field variables, see Disclaimer variables
DLP redaction support for email headers
MetaDefender Email Gateway Security now also supports DLP redaction of Received & X-Originating-IP headers to, for example, redact IP addresses.
Bug fixes
Active Directory unavailable causes SMTP server failure
Stability improvements has been made to the product to better handle scenarios when a configured Active Directory server is not available.
When an Active Directory server profile is configured in MetaDefender Email Gateway Security it becomes an integral part of user/email address verification and rule selection. If the Active Directory service is not available and security rule selection cannot be performed on the product side, email recipients can be rejected with a 450 SMTP response.
Unable to search for emails when sender is postmaster (<>)
An issue in MetaDefender Email Gateway Security filtering prevented filtering for emails with postmaster as sender.
UUEncoded email corruption
An issue could cause corruption to UUEncoded emails after processing by MetaDefender Email Gateway Security.
SMTP server failure when using TLS certificates with PKCS#1 key
MetaDefender Email Gateway Security's SMTP server could fail when configuring a TLS certificate with a PKCS#1 private key.
SMTP server memory leak
An memory leak was identified in the MetaDefender Email Gateway Security's SMTP server that could eventually cause the process or the whole system to fail.
Temporary certificate store file build-up
When configuring TLS, S/MIME or DKIM certificates/private keys in the product, it could cause excessive creation of temporary files in the operating system crypto folder (C:\ProgramData\Microsoft\Crypto).
Safe URL redirect option enabled after upgrade
Due to the re-location of the Safe URL redirect option in the security rule option, it could incorrectly become enabled after a product upgrade.
Safe URL link corruption
In certain cases links processed by the Safe URL redirect engine could become invalid and not redirect to the correct endpoint URL.

