Cloud Deployment
v5.16.0
Search this version
Cloud Deployment
Cloud Deployment
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Single EC2
Copy Markdown
Open in ChatGPT
Open in Claude
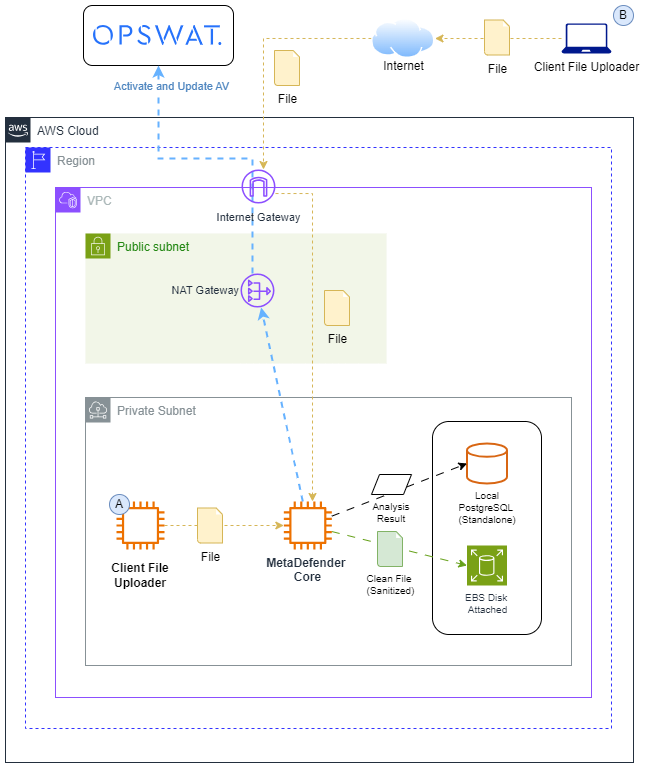
The single instance deployment is only recommended for small or test environments that do not need high availability. This deployment consist of a AWS EC2 instance using the MetaDefender Core AMI published in the marketplace that includes a Standalone MetaDefender Core where the PostgreSQL database is deployed in the same instance than MetaDefender Core.
Diagram
Orange flows
- A: From a private subnet, client is getting the files and uploading them to MetaDefender Core using the private IP
- B: From Internet, client is outside the VPC and is sending files to MetaDefender Core using the public IP
Blue flows
- MetaDefender Core get activated and updates the modules installed on it after activation
This diagram show the standalone database option where the analysis results are stored.
Resources Inventory
Access Management
| Service Type | Resource Name | Description |
|---|---|---|
| IAM Role | LambdaAccessRole | Role for Lambdas |
| IAM Role | LambdaExecutionRole | Role with Policy for logging |
| IAM Instance Profile | LambdaInstanceProfile | IAM InstanceProfile that is attached to the EC2 instance |
| IAM Policy | lambdaaccess | Policy attached to LambdaAccessRole for allowing all lambda and and events actions. |
| AWS Lambda Permissions | PermissionForEventsToInvokeLambda | Lambda Permission needed to invoke the DeactivateLambda function |
Networking
| Service Type | Resource Name | Description |
|---|---|---|
| VPC | <VPC Name> (parameter) | Desired Virtual Private Cloud |
| Subnet | terraform-${var.ENV_NAME}/SubnetPublicX | Desired Public Subnet |
| Subnet | terraform-${var.ENV_NAME}/SubnetPrivateX | Desired PrivateSubnet |
| Internet Gateway | terraform-${var.ENV_NAME}/InternetGateway | Internet Gateway for VPC |
| Elastic IP | terraform-${var.ENV_NAME}/NATIP | Public IP for NAT Gateway |
| NAT Gateway | terraform-${var.ENV_NAME}/NATGateway | NAT Gateway to give access to internet from private subnet |
| Route Table | terraform-${var.ENV_NAME}/PublicRouteTable | Route Table for Public Subnet |
| Route Table | terraform-${var.ENV_NAME}/PrivateRouteTable | Route Table for Private Subnet |
Security
| Service Type | Resource Name | Description |
|---|---|---|
| Security Group | MetaDefenderSecurityGroup | Generated security group to allow traffic to MetaDefender REST API. |
Compute
| Service Type | Resource Name | Description |
|---|---|---|
| EC2 Instance | ${var.ENV__NAME}-${var.APP_ _NAME}-instance | Instance to run MetaDefender Core AMI |
| Launch Template | ${var.APP_NAME}-template | Launch Template for MetaDefender Instance |
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Autoscaling EC2Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

