Title
Create new category
Edit page index title
Edit category
Edit link
Overview
Threat Intelligence Engine
The primary purpose of Threat Intelligence is to detect known threats by correlating against established intelligence indicators, including known malicious file hashes, IP addresses, domains, and URLs. In addition to detection, the engine enriches analysis results by providing contextual intelligence and metadata, enabling better‑informed security decisions and faster incident response.
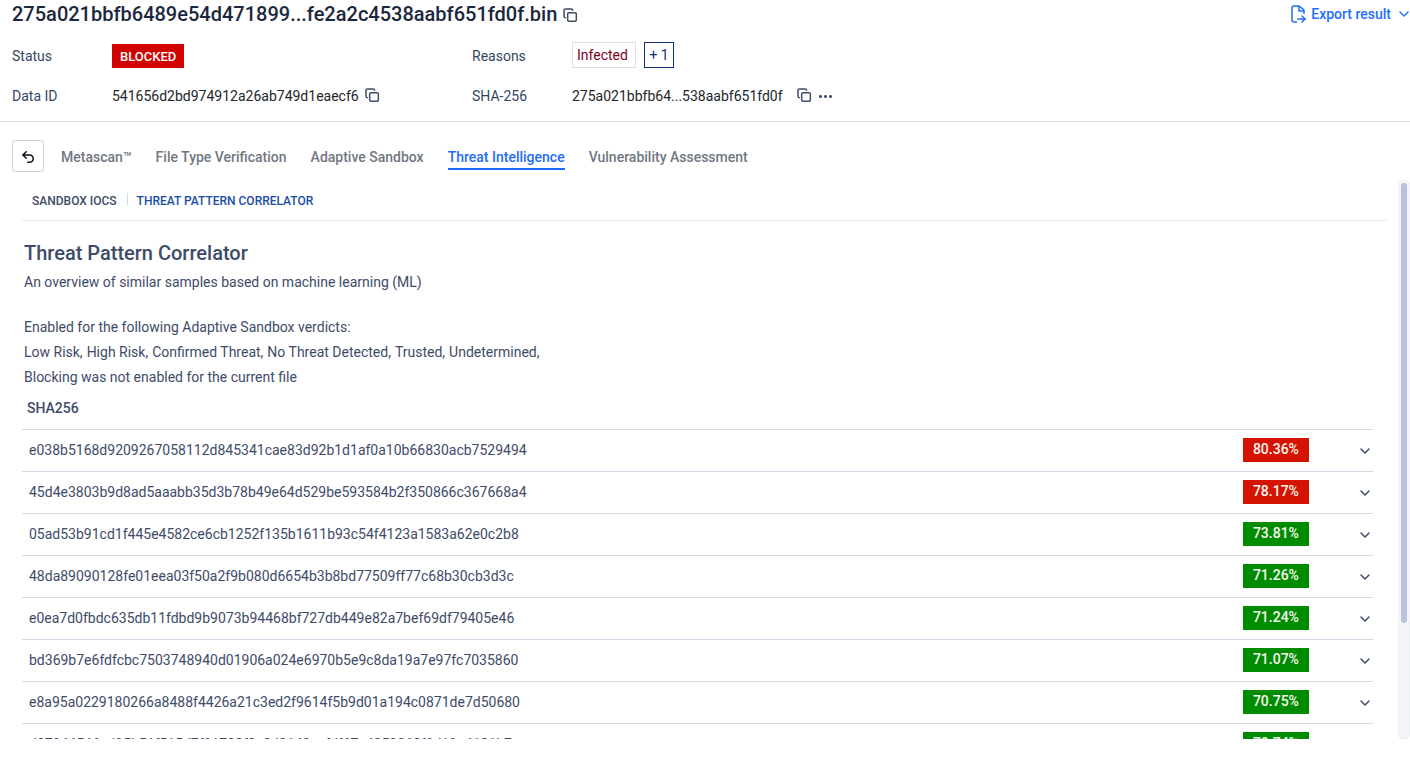
Threat Pattern Correlator, is designed to identify and assess unknown and emerging threats by correlating them with known malicious activity. Instead of relying solely on direct signatures or known indicators, the engine analyzes behavioral and structural characteristics to uncover similarities with established malware families, attack tactics, infrastructure, and threat campaigns.
By leveraging machine learning techniques, Threat Pattern Correlator enables the detection of zero‑day and previously unseen files by matching them to patterns derived from already known threats. This correlator‑based approach extends protection beyond traditional signature‑based detection
Most features require Aether license to function. Learn more: MetaDefender Aether
Adaptive Sandbox must be installed and enabled for the Threat Intelligence Engine to operate correctly.
Displaying engine results
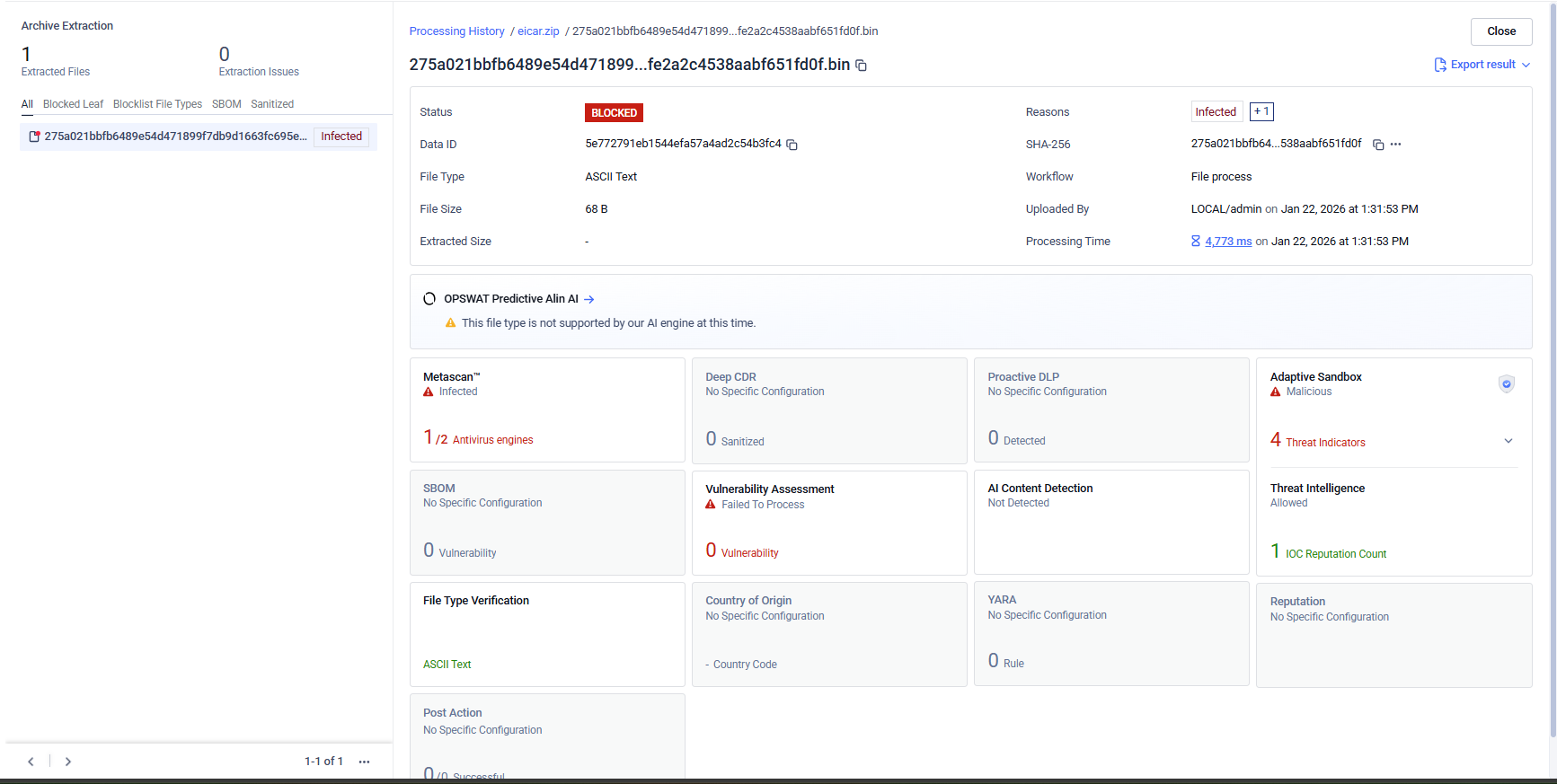
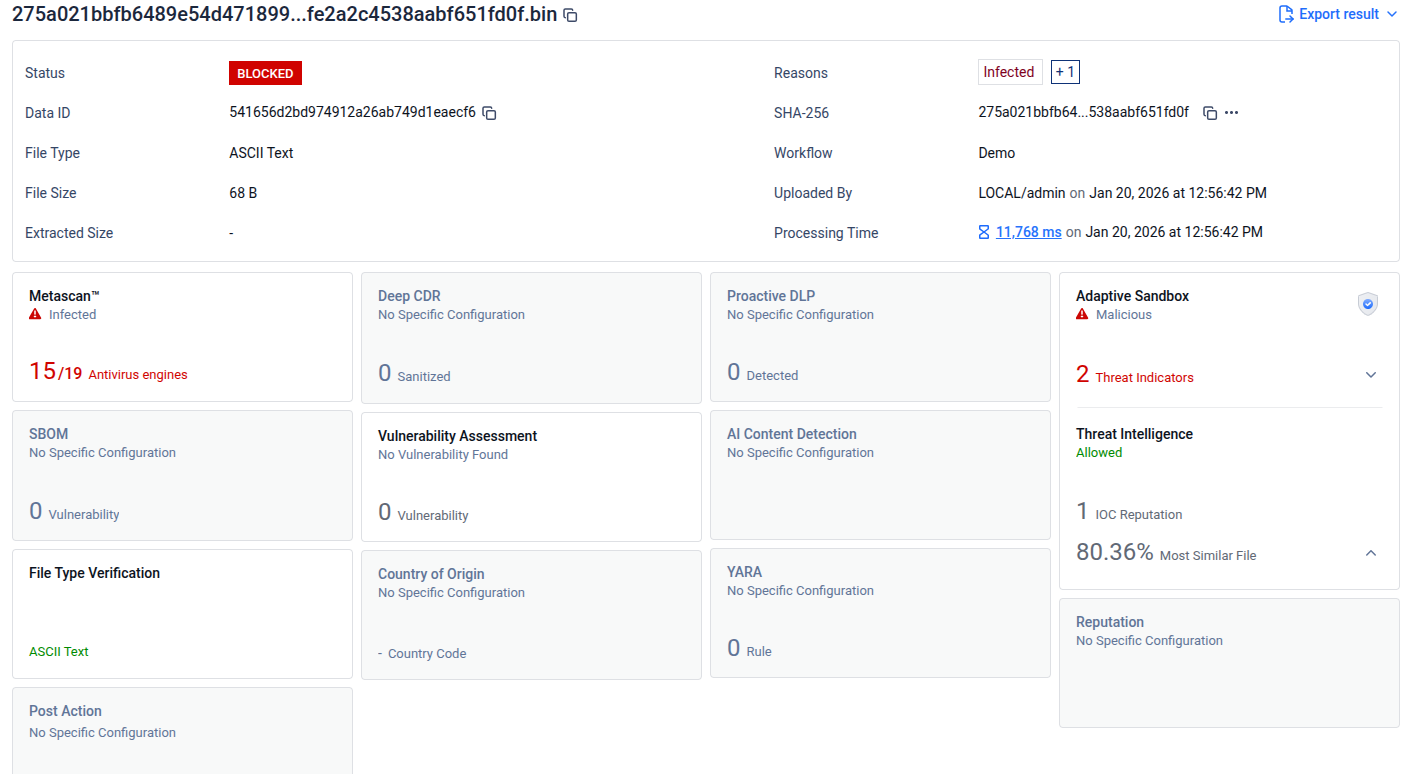
IoC (Indicators of Compromise) Reputation: When Threat Intelligence is enabled, the engine correlates sandbox‑generated IoCs with reputation sources and shows how many of those IoCs have reputation data.
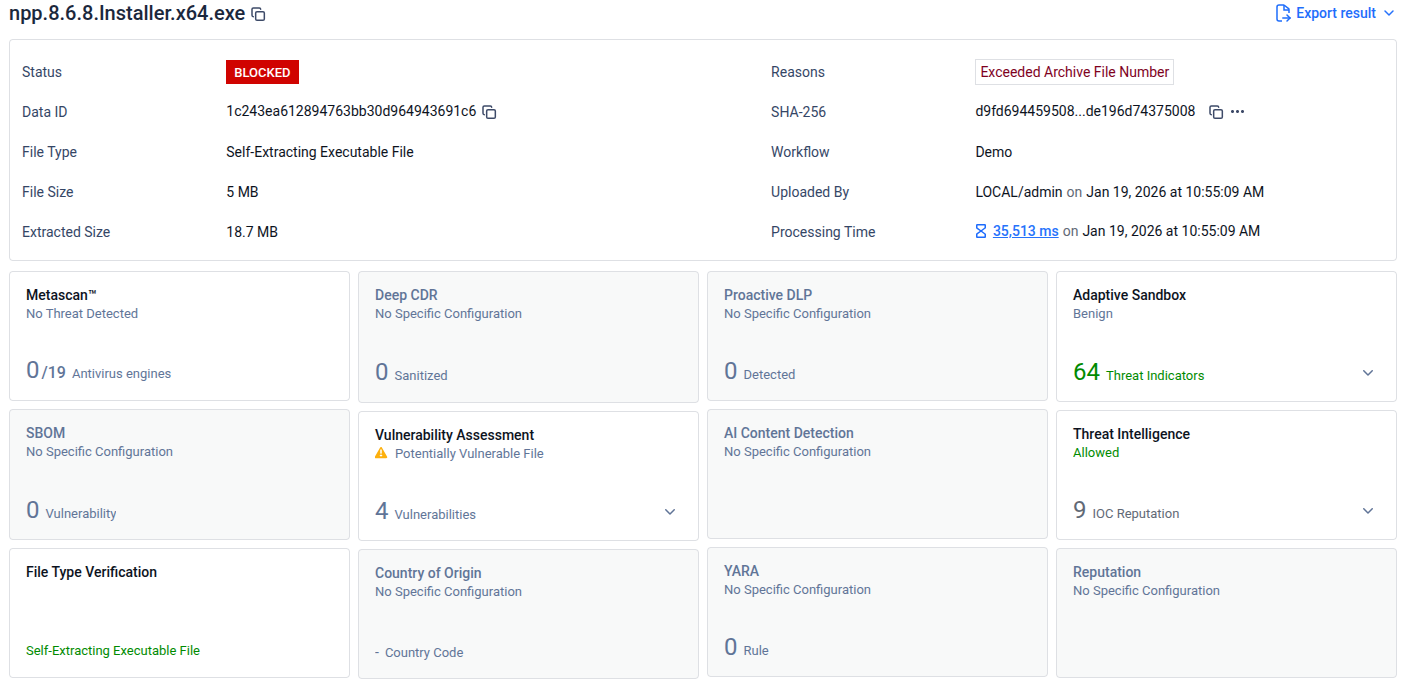
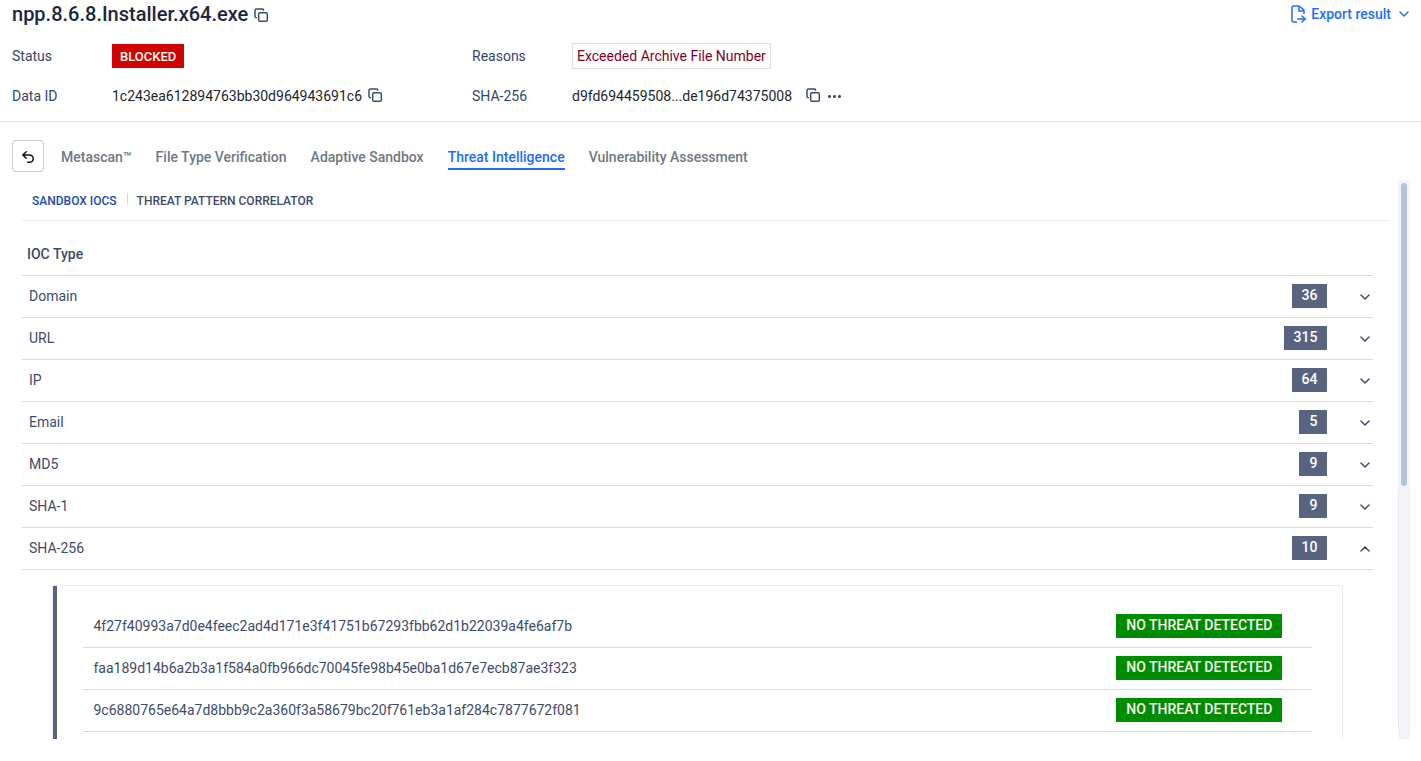
Threat Pattern Correlator (Blocking Disabled): Enabling Threat Pattern Correlator allows the Threat Intelligence Engine to analyze file fingerprints and identify similar files, while operating in a non‑blocking mode.
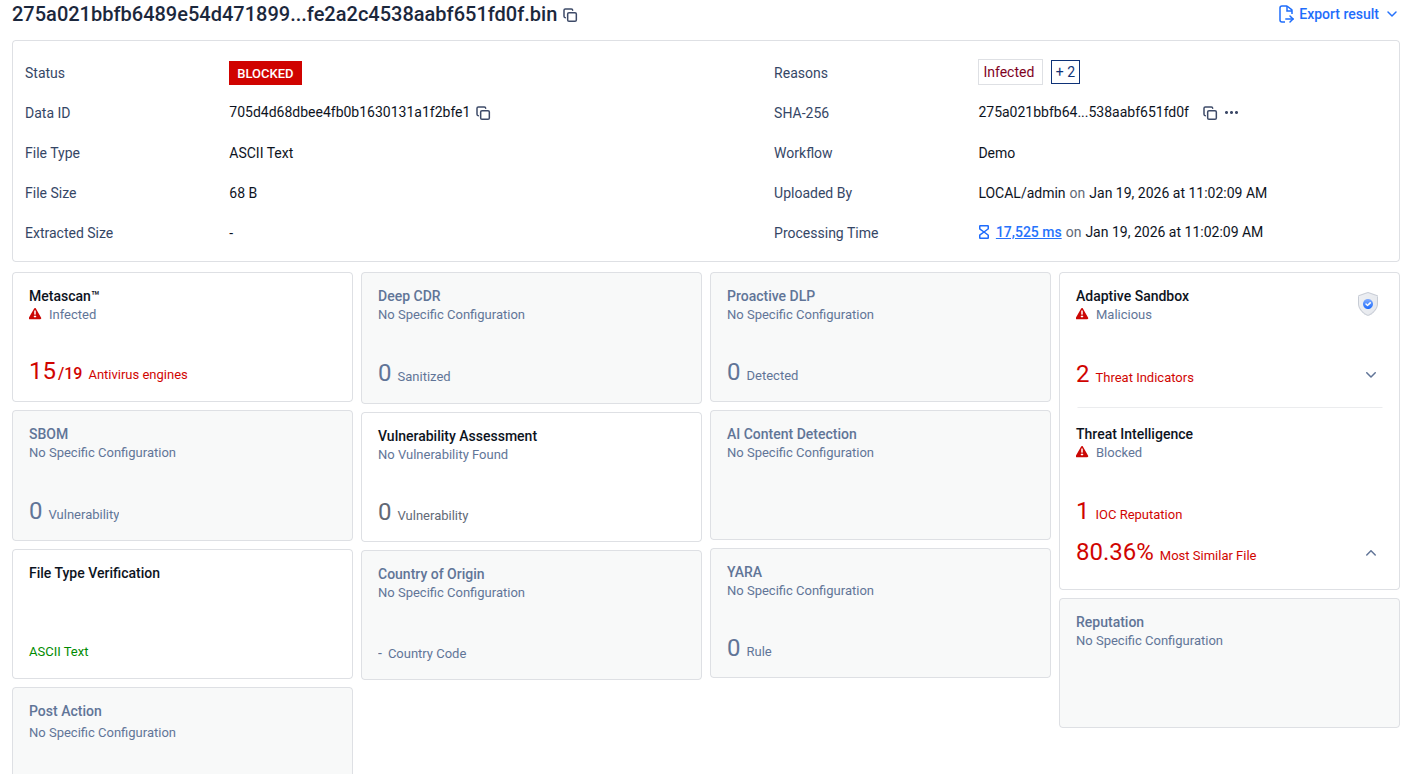
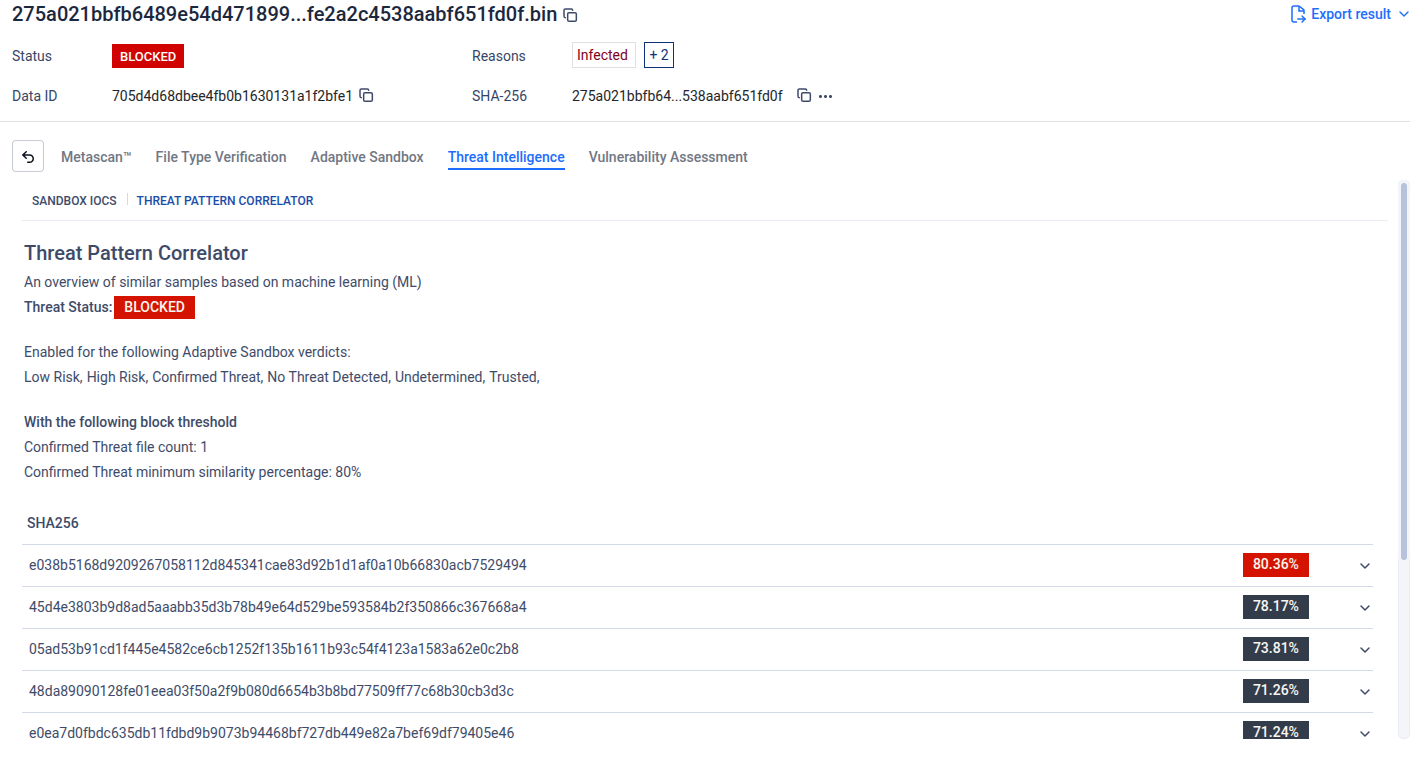
Threat Pattern Correlator (Blocking Enabled): Enabling Threat Pattern Detection allows the Threat Intelligence Engine to analyze file fingerprints, identify similar files, and automatically block those that match known threat patterns.
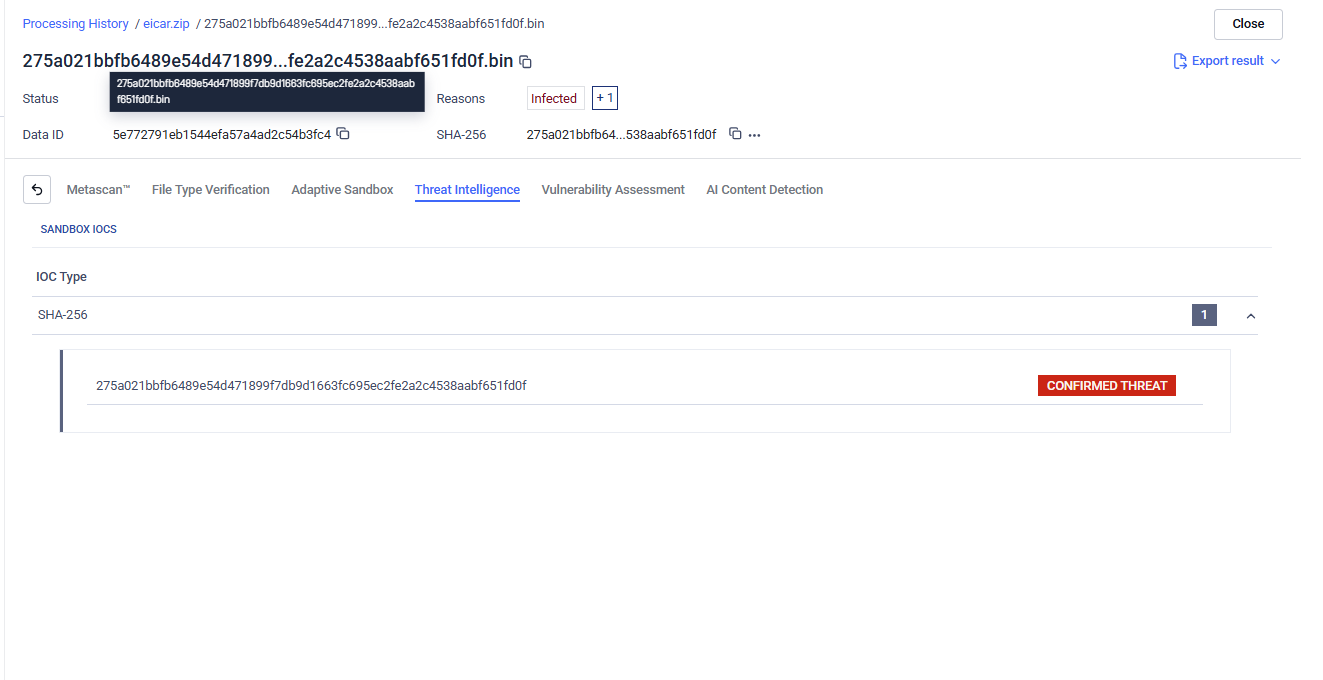
In some cases, a Threat Intelligence result may include an Indicator of Compromise (IoC) classified as “Confirmed Threat,” while the overall verdict is shown as Allowed.
This behavior is expected. IoCs are not evaluated in isolation; instead, they are factored into the final verdict generated by Adaptive Sandbox as part of a broader contextual analysis. The sandbox assesses execution behavior, runtime characteristics, and other environmental indicators to determine the overall risk level of the analyzed file.
As a result, the presence of a “Confirmed Threat” IoC alone may not be sufficient to classify the sample as malicious from a sandbox perspective, and the verdict may remain Allowed.
It is important to note that the Threat Intelligence engine blocks files only when the Threat Pattern Correlator is enabled. Without this feature, Threat Intelligence findings— including Confirmed Threat IoCs—do not directly enforce blocking decisions and are used for correlation and analysis purposes only.