Title
Create new category
Edit page index title
Edit category
Edit link
Server profiles
Overview
MetaDefender Cloud Email Security is surrounded by different services that together can provide the email processing capabilities.
Such services are:
- SMTP services to where MetaDefender Cloud Email Security can forward emails when processing is completed;
- MetaDefender Managed File Transfer instances to where MetaDefender Cloud Email Security can upload attachments, for details see Integrations/Integration with MetaDefender Vault.
MetaDefender Cloud Email Security uses the concept of server profiles to integrate to these services.
The server profile is an abstract representation of one or more physical server bundled into a single unit.
Using this abstraction the same server may be reused at several points of the application, potentially with different actual settings. The abstraction can also provide failover or load balancing capabilities in certain cases.
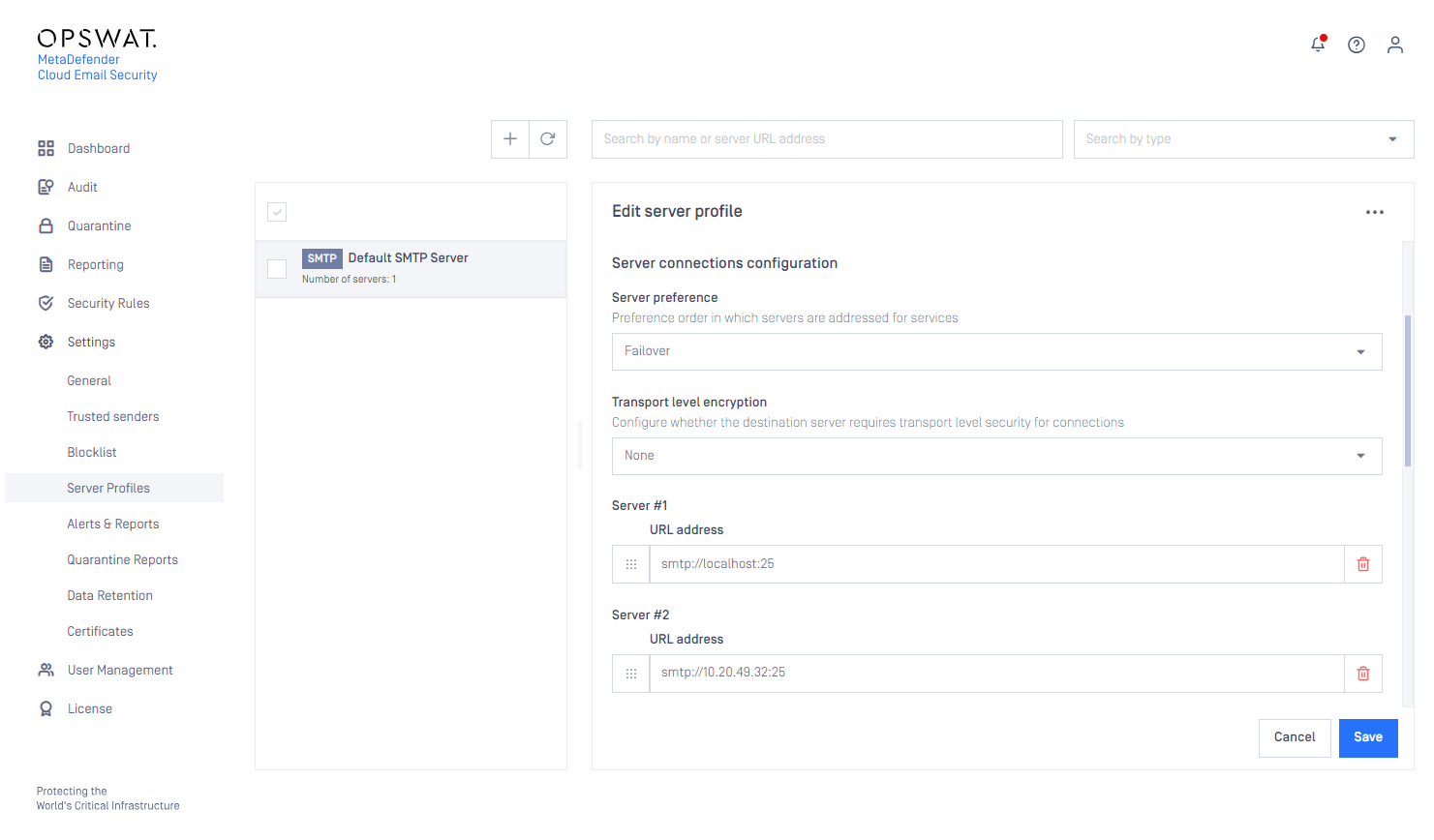
Example
In the image below we show an SMTP type server profile. This profile contains two actual SMTP servers that are utilized in a Failover fashion (the first is the preferred one, but if that fails, then the second is attempted).
This server profile can be used in any of the security rules as the SMTP relay server profile (see Configuration/Policy).
Sensitive data
Certain server profiles require sensitive information to be configured for the server profile to work correctly.
| Server profile type | Sensitive data |
|---|---|
| SMTP server | Password |
| MetaDefender Managed File Transfer | MetaDefender Managed File Transfer apikey |
As long as TLS is not configured for the web management console, sensitive information above is sent clear-text over the network.
For details see Configuration/Transport Layer Security.
As long as TLS is not configured between MetaDefender Cloud Email Security and the server providing the service of the server profile, sensitive information above is sent clear-text over the network.
For details about configuring TLS between MetaDefender Cloud Email Security and server profile servers see section Transport layer security schemes.
Server specifications
Servers must be specified using URI syntax. Multiple server specification may be added to an SMTP or MetaDefender Core type server profile. At least one server specification must exist in a server profile.
Only the following URI components are used:
[scheme]://[host]:[port]/[path]| URI component | Supporting server profile type | Example | Defaults | |
|---|---|---|---|---|
| scheme | All | smtp://10.0.0.10:25 | SMTP | smtp, smtps |
| host | All | http://10.0.0.10 | N/A | |
| port | All | http://10.0.0.10:**25** | SMTP | 25 |
| port | All | http:// 10.0.0.10:8010/vault_rest | MetaDefender Managed File Transfer | 8010 |
| path | MetaDefender Managed File Transfer | http://10.0.0.10:25/**vault_rest** | MetaDefender Managed File Transfer | /vault_rest |
Server profile examples
The following list contains examples for each server profile type with reasonable defaults (all use 127.0.0.1 as host).
| Server profile type | URI |
|---|---|
| SMTP | smtp://127.0.0.1:25 |
| MetaDefender Managed File Transfer | http://127.0.0.1:8010/vault_rest |
Transport layer security schemes
To configure TLS between MetaDefender Cloud Email Security and the server providing the service of the server profile, the following schemes must be used:
| Server profile type | TLS scheme |
|---|---|
| SMTP server | smtps |
| MetaDefender Core | https |
| MetaDefender Vault | https |
For TLS to work properly, it must be configured on the server profile server.
- SMTP server: seek for guidance at the vendor of your SMTP server
- MetaDefender Managed File Transfer: https://onlinehelp.opswat.com/vault/Enable_HTTPS.html
Server preference
Actual server in SMTP type server profiles can be set to a preference order in which servers are addressed for services.
Failover
High availability order; first successfully addressed server in the list will do the service.
Always start with the first server URL in list defined in the server profile.
Fail over to the next server in the list, if the actual server fails.
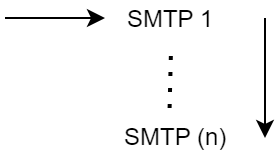
The order of the servers can be set by drag and drop using the ⋮ icon in front of the server specification.
Round robin
Load balancing order; next successfully addressed server in the list will do the service.
Do a Round Robin selection of the SMTP URLs defined in the SMTP inventory:
- For the first delivery use SMTP 1
- If previous delivery used SMTP 1 then use SMTP 2 now,
- ...,
- If previous delivery used SMTP k then use SMTP k+1 now,
- ...,
- If previous delivery used SMTP n then use SMTP 1 now
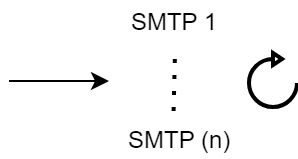
Instead of a real Round Robin selection, the initial server is selected in a random fashion currently:
Do a random selection of the SMTP URLs defined in the SMTP inventory.
Fail over to the next SMTP in the list, if the actual SMTP fails. Start over the selection at the end of the list and continue until the starting entry is reached.
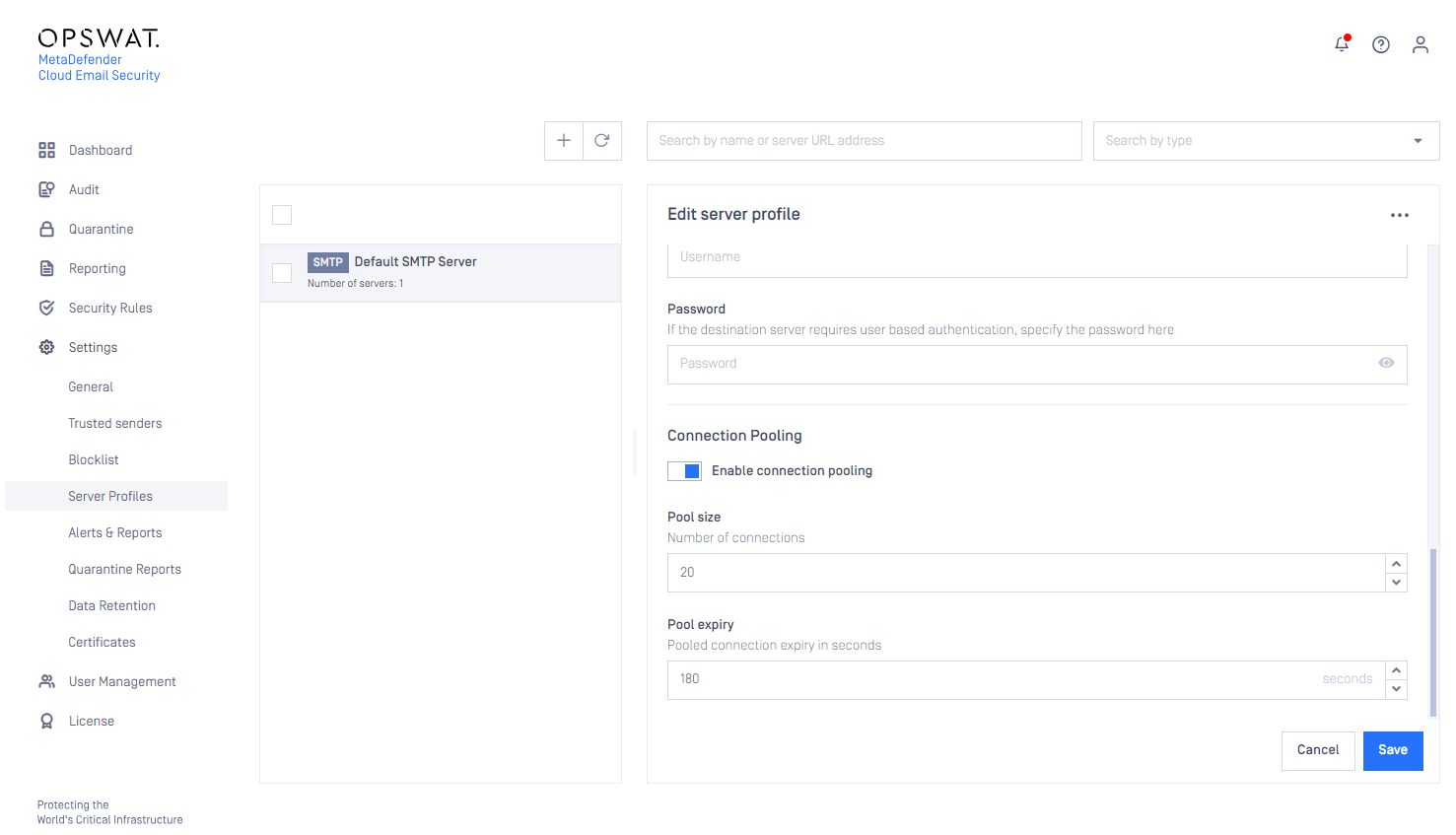
SMTP server connection pooling
To improve performance, MetaDefender Cloud Email Security can cache and reuse connections towards SMTP relays.
At the end of the processing of an email, MetaDefender Cloud Email Security forwards the processed email to the next hop –that is usually the mail server for inbound emails– via SMTP. This next hop is configured in the rule matching the email, under Security Rules / rule / GENERAL / SMTP relay server profile (see Configuration/Policy). The value must be an SMTP type server profile configured under Settings > Server Profiles.
When an email is forwarded to the relay, an SMTP handshake must happen while a TCP connection must be established. This is a time-consuming, resource-intensive task that can slow the email processing down, especially under a heavy load.
To contain the time loss caused by establishing SMTP connections, MetaDefender Cloud Email Security can reuse already established connections, these are kept in the connection pool.
- If the pool is empty, and a new SMTP connection is needed, then the connection gets established.
- If the pool is not full yet, and the communication completes over an SMTP connection, then this connection is placed into the pool for later reuse.
- If an SMTP connection is needed, and there is an idle connection in the pool, then it is taken from the pool and reused for this connection.
- If the pool is full, and the communication completes over an SMTP connection, then this connection is disconnected.
- If a connection in the pool has not been reused for the configured time, then it gets disconnected.
The following options are available:
| Option | Default | Min | Max | Description |
|---|---|---|---|---|
| Enable connection pooling | Off | N/A | N/A | Enable or disable SMTP connection pooling. |
| Pool size | 20 | 1 | 999 | Maximum number of SMTP connections kept in the pool for reuse purposes. |
| Pool expiry | 180 | 1 | 60 000 | If the pooled SMTP connection has not been used for the time window configured here, then it gets disconnected. |
Please note, that most SMTP servers limit the number of parallel inbound SMTP connections. This must be taken into consideration when configuring connection pooling in MetaDefender Cloud Email Security.
For details about limitations on number of connections in case of the Microsoft Exchange Server, see https://docs.microsoft.com/en-us/exchange/mail-flow/message-rate-limits.
Property validation
Some of the server profile properties have cross-dependencies and as so must match.
| Server profile type | Server specifications (URI) allowed schemes |
|---|---|
| SMTP | smtp |
| SMTP | smtps |
| MetaDefender Managed File Transfer | http |
| MetaDefender Managed File Transfer | https |
| Server specifications (URI) scheme | Transport level encryption allowed values |
|---|---|
| smtp | None |
| smtp | StartTLS optional |
| smtp | StartTLS required |
| smtps | Irrelevant If smtps scheme is specified then the SMTP connection is established over TLS irrelevant of the setting of Transport level encryption. |
| http | N/A |
| https | N/A If https or scheme is specified then the HTTP connection is established over TLS. |
Testing the configuration
Clicking the SAVE button the connection will be tested first. The test consists of two steps:
- Syntactical validation of the values
- Connection test
If the test fails, then the server profile can not be added.
Syntactical validation
The correctness of the provided values is validated:
- Server profile name must be unique
- The URI address values must conform with the URI syntax with the restriction listed at section Server specifications
- Cross dependencies must match (see the Property validation section)
Connection test
If the syntactical validation pass, then each server specification is tested for a successful connection.
Limitations
Currently the connection is tested without using TLS (when configured at all).

