Overview MetaDefender Sandbox API Reference Release Notes
Getting Started
Deployment & Usage
Support
Release Notes
3.0.0
Search this version
Release Notes
Release Notes
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Release Notes for v1.9.1
Copy Markdown
Open in ChatGPT
Open in Claude
Date: 22 November, 2023
This version is not suitable for a clean installation due to breaking changes introduced in Docker 25. Please use version 1.9.2 or later for clean installations!
Added:
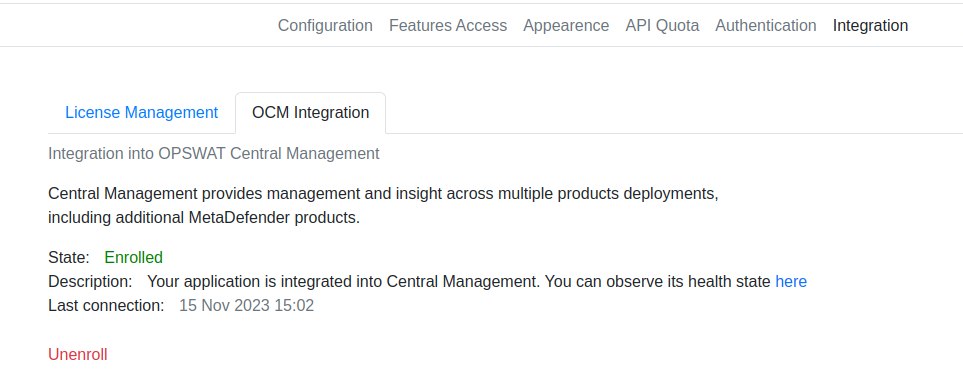
- Integrated OPSWAT Central Management (OCM) into the Web UI: OCM Registration
- Automatic email notifications with the original email sender when scanning .eml files: Email Notifications
- Detected and flagged .exe suffixes in URLs to highlight potential downloads of PEs
- Displayed additional Crypto Wallet Indicators of Compromise (IOCs) in scan reports
- Displayed the product's current version in the Web UI footer
- Showcased top malware families in the Trends page
- Identified clickable and non-clickable URLs from documents
- Implemented disassembly of relevant functions in 64-bit executables
- Implemented a parser for .ics files (vCalendar), including the extraction of attached files
- Extended support for JavaScript emulation in Adobe PDF files
- Enabled threat indicator monitoring and statistics support
- Enabled support for all file types when generating an executive summary using OpenAI’s GPT large language model (LLM): ChatGPT (Executive Summary)
Changed:
- Revamped the processing of threat indicators and the methodology behind verdict calculations
- Augmented documentation and introduced an automated system check to verify the utilization of CPUs with AVX support. Technical Requirements
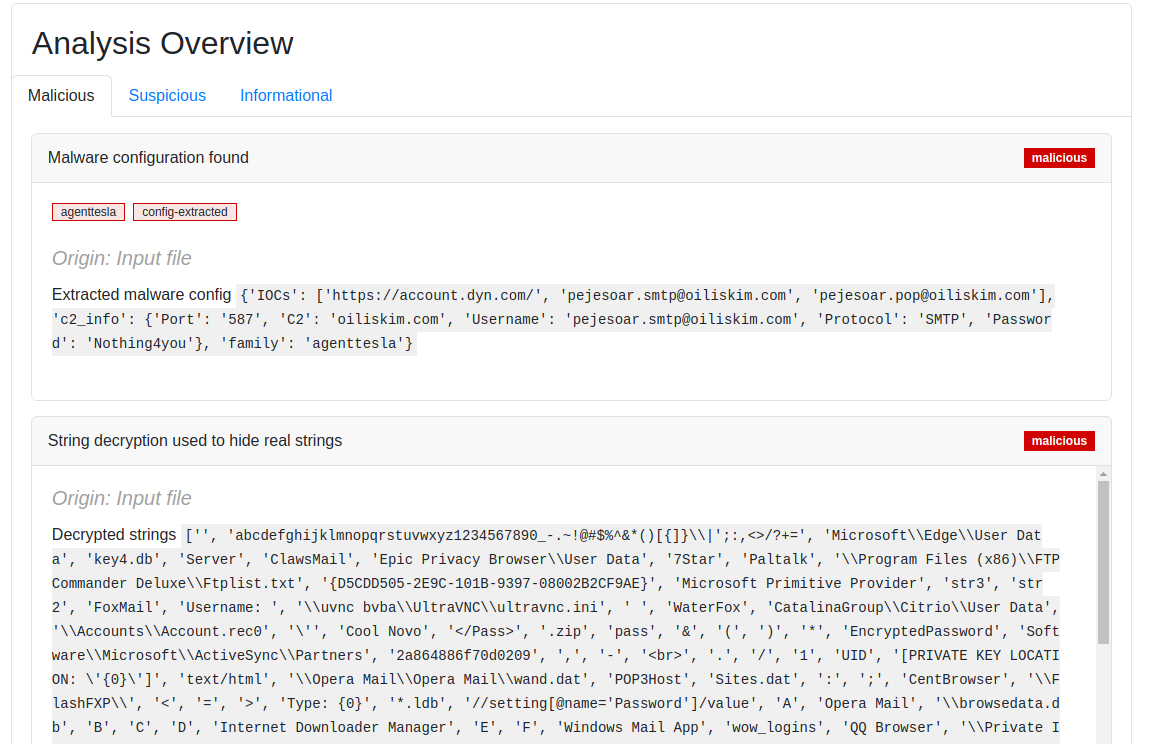
- Expanded malware configuration extractors to encompass the latest and most pertinent threats
- Implemented the generation of randomized internal passwords for fsBroker and fsTransform components during the installation process
- Upgraded the detection capabilities to more effectively identify malicious office documents
- Improved the extraction process for Crypto Wallets to ensure a more comprehensive and accurate output
- Fine-tuned the extraction of overlay elements in PDF files for increased precision
- Strengthened the system's capability to handle malformed Microsoft Office documents
- Enhanced heuristic domain identification to minimize false positives
- Improved the identification and parsing of VBA content within PDF files
- Enhanced memory management within the scan engine to boost overall efficiency
- Improved parsing for .NET executables for more accurate analysis
- Enhanced parsing for YARA rules to achieve greater precision in matching
- Improved the reporting mechanism for identifying and handling invalid signatures during certificate validation
- Elevated the capabilities of VBA and PowerShell emulation for heightened security measures
- Incorporated confidence values in phishing detections, influencing the final verdict for URL rendering
- Updated the "Download IOCs" button to selectively download items solely from the current page
- Refreshed the internal FSIO fuzzy hash blocklist to encompass emerging threat clusters
Fixed:
- Enhanced Application Security measures
- Improved health check functionality in scan job queues, automatically restarting when required
- Eliminated weak third-party YARA rules to prevent False Positives
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Release Notes for v1.9.0See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet
Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

