Title
Create new category
Edit page index title
Edit category
Edit link
Web & Phishing
#1 Brand Spoofing Detector
Detection Spotlight:
- Brand Spoofing Detector: By rendering suspicious websites and subjecting them to our advanced machine learning engine we're capable of identifying nearly 300 brands. In the example provided below, you can witness a website masquerading as a streaming company known as Netflix. Our solution excels in comparing the site's content to the genuine URL, swiftly identifying such fraudulent attempts to safeguard your digital assets and personal information. Learn more about this feature by clicking here.
- AI-driven analysis: We have an AI-driven solution analyzing the network traffic, structural and textual content of the rendered page. The verdict of the joint model outcome can be seen after 'ML Web Threat Model'.
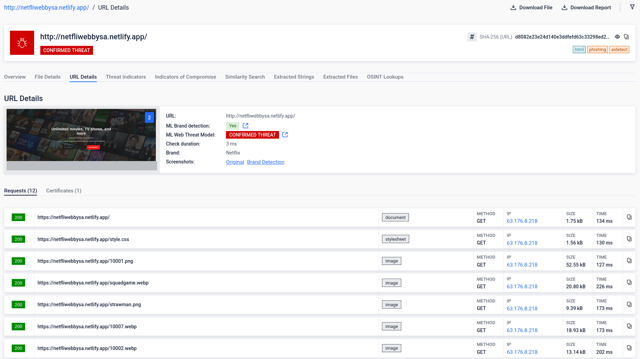
#2 URL Reputation Predictor
Detection Spotlight:
The URL Reputation Predictor model provides a new layer of defense by effectively detecting suspicious URLs, offering a robust means to identify and mitigate threats posed by malicious links. It leverages a dataset containing hundreds of thousands of URLs, meticulously labeled as either no threat or malicious by reputable vendors, to assess the feasibility of accurately detecting suspicious URLs through machine learning techniques.
It is important to note that this feature is particularly useful in air-gapped environments where online reputation lookups are not available.
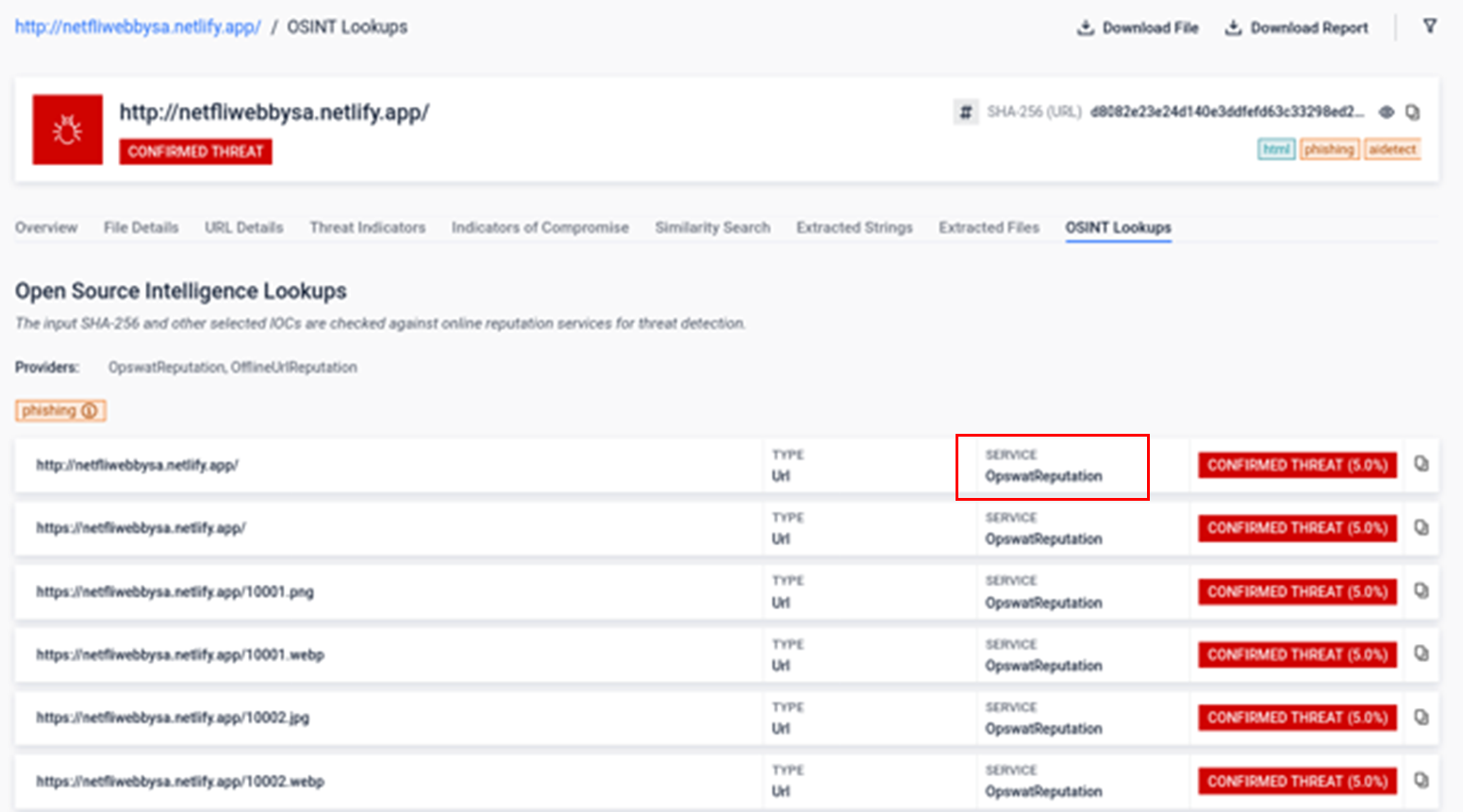
Learn more about the URL Reputation Predictor in Offline Mode by clicking here.
#3 Google DKIM Replay Attack Detection
Detection Spotlight:
Email authentication mechanisms like SPF, DKIM, and DMARC are essential, but sophisticated attackers can sometimes bypass them. This example showcases a scenario where an email, despite being authentically signed by Google and passing standard checks, was identified as malicious by MetaDefender Aether.
MetaDefender Aether detected several anomalies along with other indicators:
- DKIM Boundary Violation: Identified content added beyond the scope of the DKIM signature.
- Obfuscation Techniques: Detected excessive whitespace used to hide malicious intent.
- Phishing Patterns: Recognized urgent calls-to-action characteristic of phishing attempts.
- Header Analysis: Flagged anomalies in email headers associated with OAuth application abuse.
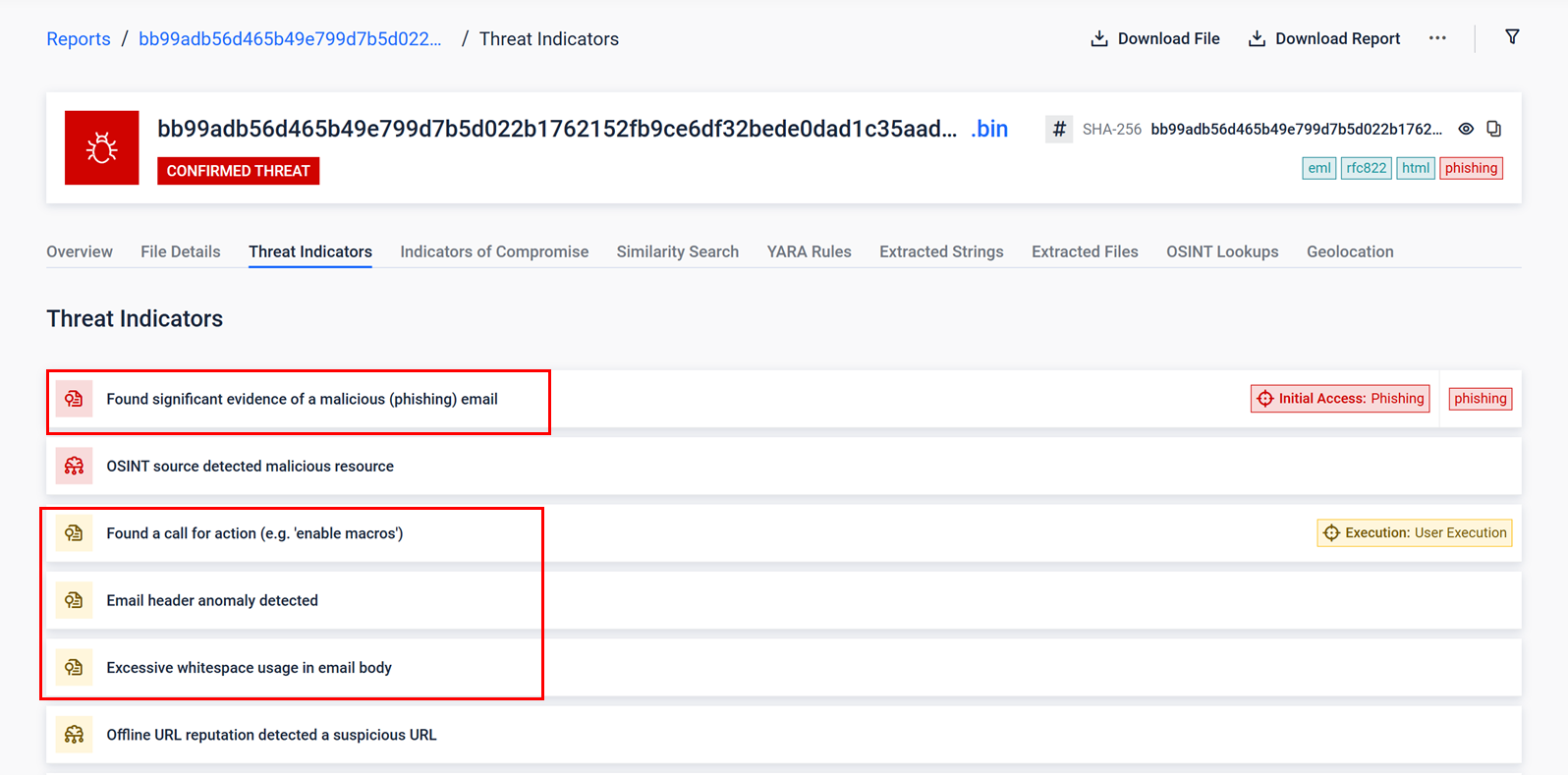
Advanced threat indicator detections for the phishing email
#4 ClickFix, a trending social engineering technique
Detection Spotlight:
ClickFix is an emerging web-based threat that leverages social engineering to silently trick users into executing malicious commands. Unlike traditional phishing, ClickFix operates through deceptive UX elements and clipboard manipulation rather than file downloads or credential theft.
The ClickFix website presents a fake reCAPTCHA or "bot protection" screen to appear legitimate. The user is then asked to verify themselves—often through a harmless-looking interaction—while, in the background, obfuscated JavaScript code silently runs. This script dynamically decodes a malicious command and copies it directly to the system clipboard. Next, the user is presented with misleading instructions and guide to execute the malware, unaware of the danger.
ClickFix highlights how simple web techniques, combined with user deception, can effectively bypass traditional security layers—making sandbox analysis critical for uncovering stealthy, low-footprint attacks like this one.
MetaDefender Aether analyses this threat end-to-end. The sandbox begins by rendering the malicious URL and applying phishing detection models to identify suspicious content. It then extracts and emulates the JavaScript, simulating user actions to reach the critical moment when the clipboard is modified. Once the hidden command is captured, it is emulated, allowing the sandbox to fully trace the malicious execution flow. This not only exposes the clipboard-based tactic but also reveals the payload’s behavior and infection chain.
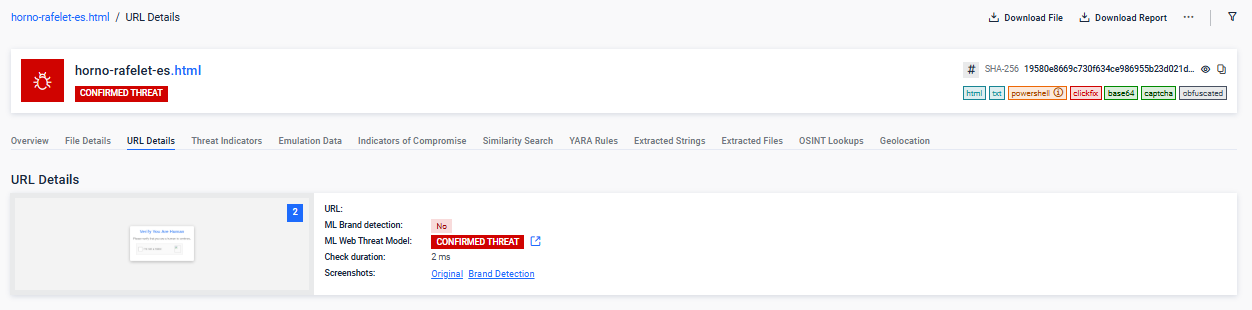
URL Rendering & Phishing detected by ML model.

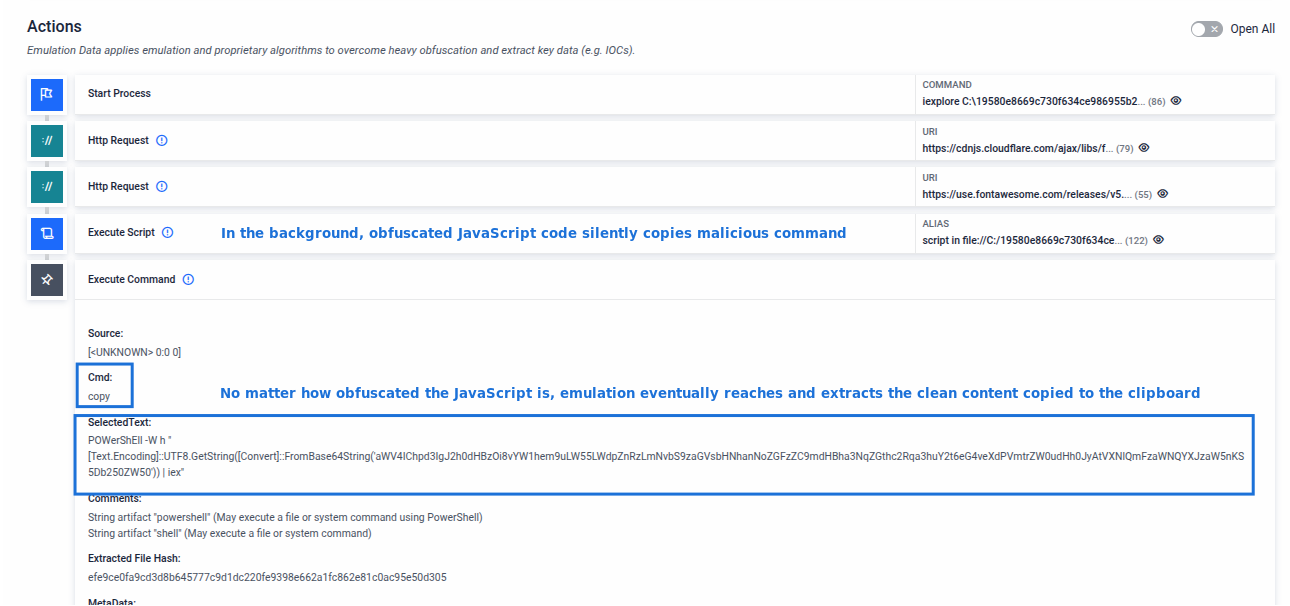
Emulation of ClickFix JavaScript code that reveals malicious copied command to the clipboard.
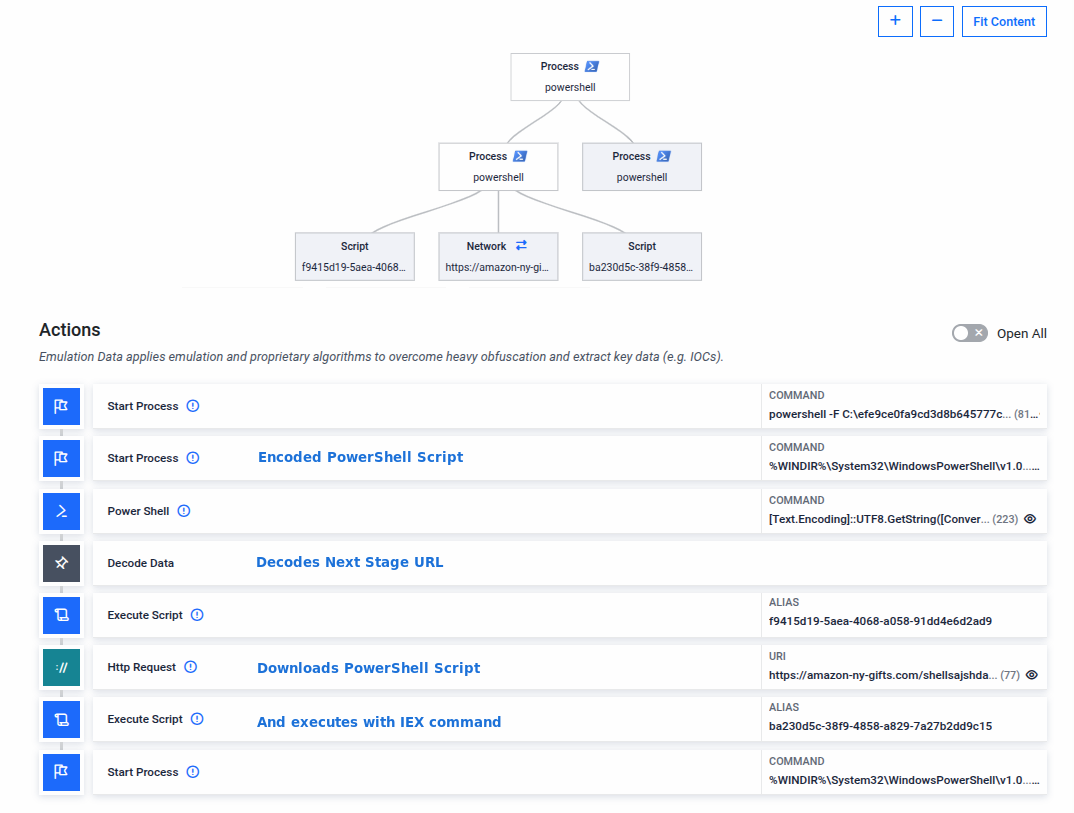
Emulation of PowerShell code copied silently in the clipboard. (Extracted files)
See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet

