Title
Create new category
Edit page index title
Edit category
Edit link
Supported packers for unpacking
Our engine can unpack a wide range of packers, including both specific and generic ones. This is important because packers are often used by malware to evade detection. By unpacking them we can analyze it and identify any threats embedded.
Specifically supported packers:
- ASPack
- FSG
- MEW
- MPRESS
- PEtite
- UPX
- YZPack
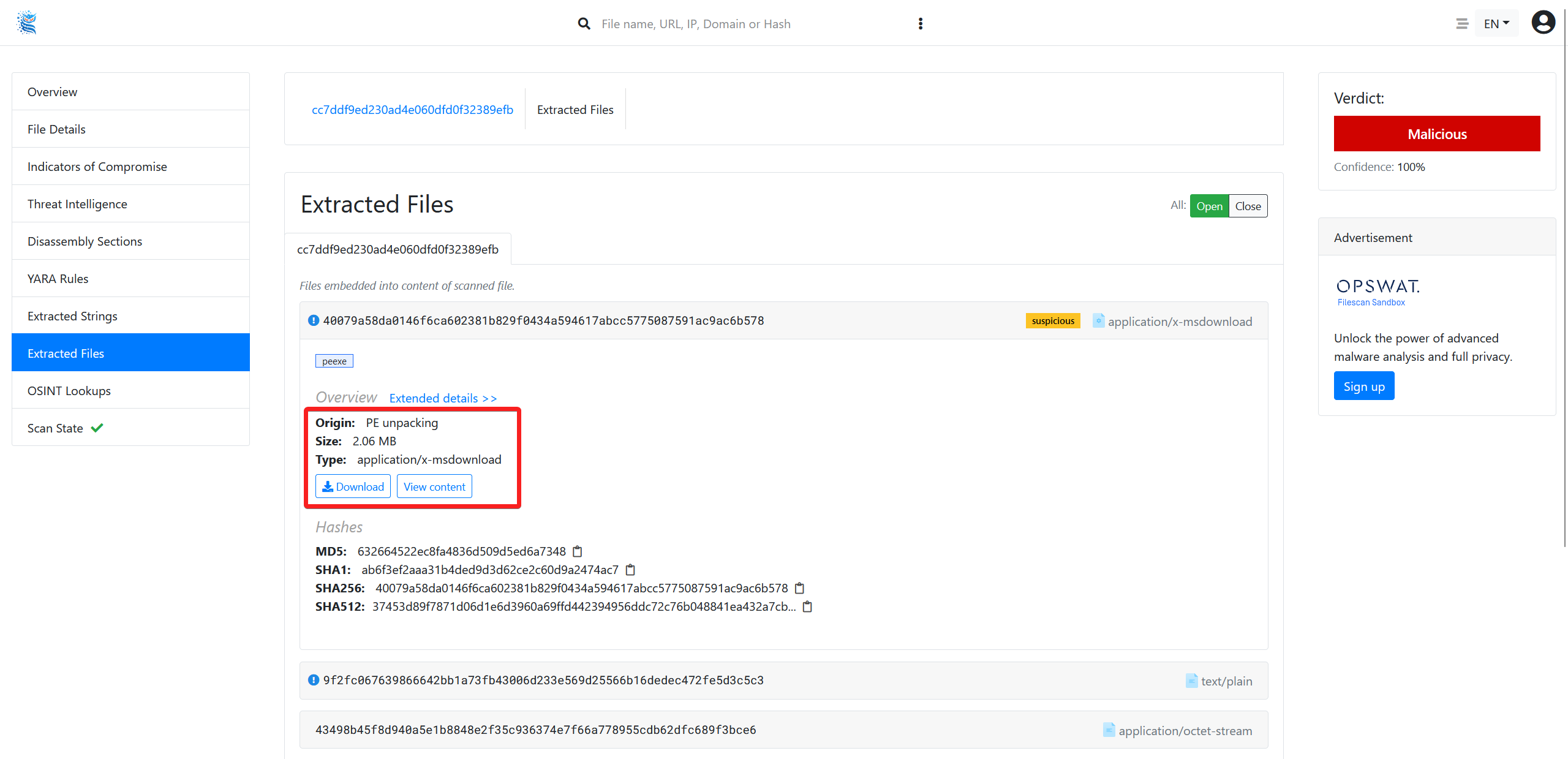
On the following link you can find the sample from the screenshot below:
The following screenshot from the linked analysis shows the unpacked PE is available to be downloaded.
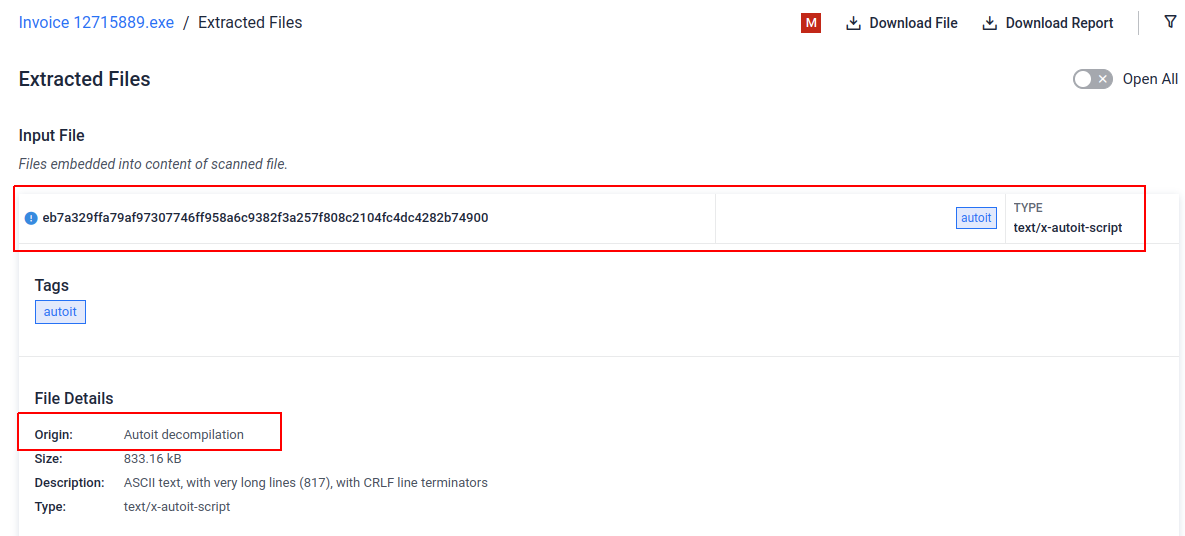
Additionally, we also support extraction and decompilation of scripting code that has be wrapped as an executable. This technique is commonly found in malware and can be effective to deviate the focus of the analysis from the relevant payload. Hence we detect, extract, and decompile such implementation in order to be able to focus on the relevant payload.
Supported compiled scripting languages:
- PyInstaller
- Py2Exe
- Nuitka
- AutoIT
- JPHP
On the following link you can find the sample from the screenshot below:
See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet

