Title
Create new category
Edit page index title
Edit category
Edit link
Advanced Search
In this document, we showcase some of the diverse threat hunting capabilities available in the advanced search feature.
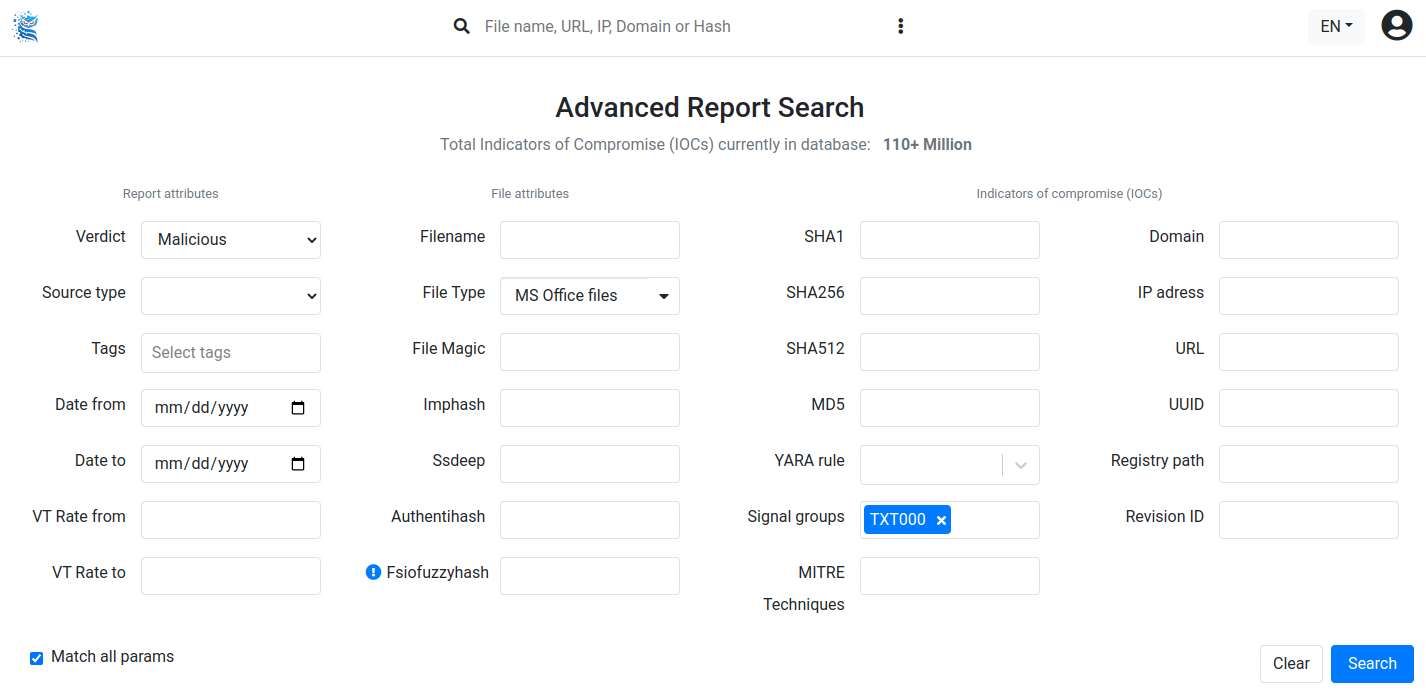
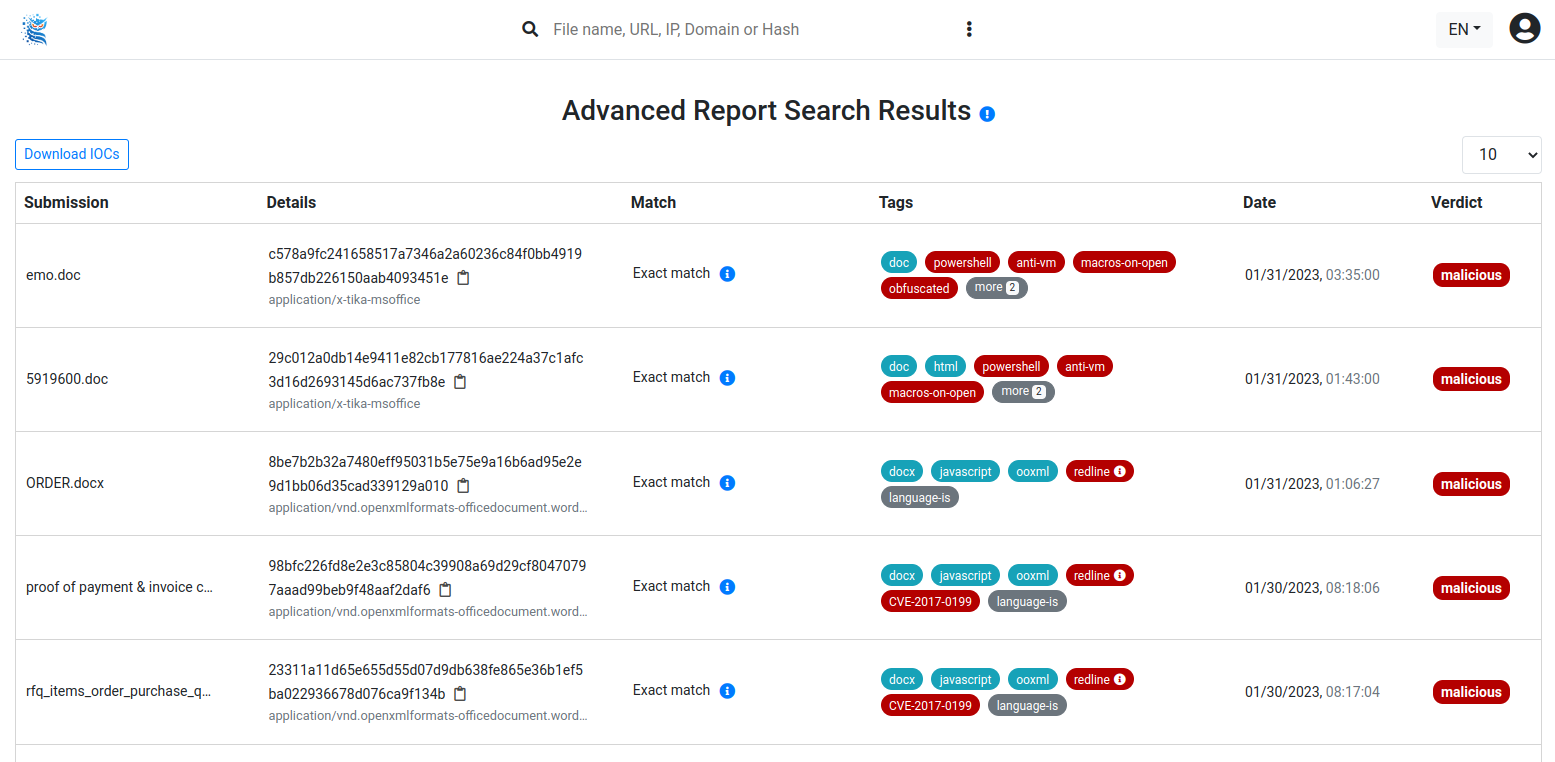
Examples
Note: Since the search can take time, opening the serach examples also takes time too.
Malicious Documents
Office Files with Foreign Language and Active Content: report exampe, search example
Office Files using default Symmetric Key Encryption: report example, search example
Office Files utilizing the EMBED.Equation exploit: report example, search example
Office Files with Auto-Execution and Process Spawns: report example, search example
Phishing PDFs: report example, search example
Suspicious Executables
Packed PE files with process hollowing capabilities: report example, search example
PE file with a RDTSC timing instruction: report example, search example
Unusual File Types
Malicious Windows Shortcut Files spawning rundll: report example, search example
Malicious files delivered via VHD image files: report example, search example
Mobile Threats
Malicious APKs: report example, search example
APKs reading the device ID (IMEI): report example, search example
Malicious Web Threats
E-Mails containing macro-enabled attachments: report example, search example
Phishing URLs: report example, search example
Additional Resources
Threat FeedAPI
See the "Technical Datasheet" for a complete list of features: https://docs.opswat.com/filescan/datasheet/technical-datasheet

